| Services | platforms | author | level | client | service | endpoint |
|---|---|---|---|---|---|---|
active-directory |
Android |
danieldobalian |
100 |
Android Mobile App |
Microsoft Graph |
AAD V2 |
| Getting Started | Library | API Reference | Support |
|---|
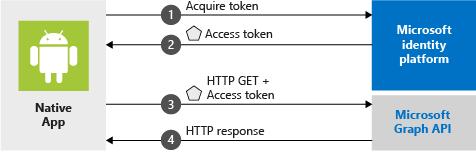
The MSAL Android preview gives your app the ability to begin using the Microsoft identity platform by supporting Microsoft Azure Active Directory and Microsoft Accounts in a converged experience using industry standard OAuth2 and OpenID Connect. This sample demonstrates all the normal lifecycles your application should experience, including:
- Get a token for the Microsoft Graph
- Device-wide SSO and Conditional Access suport through the Auth Broker
- Refresh tokens automatically
- Call the Microsoft Graph
- Sign out the user
This app is a multi-tenant app meaning it can be used by any Azure AD tenant or Microsoft Account. It demonstrates how a developer can build apps to connect with enterprise users and access their Azure + O365 data via the Microsoft Graph. During the auth flow, end users will be required to sign in and consent to the permissions of the application, and in some cases may require an admin to consent to the app. The majority of the logic in this sample shows how to auth an end user and make a basic call to the Microsoft Graph.
// Initialize your app with MSAL
PublicClientApplication pApp = new PublicClientApplication(
this.getApplicationContext(),
R.raw.auth_config);
// Perform authentication requests
pApp.acquireToken(getActivity(), SCOPES, getAuthInteractiveCallback());
// ...
// Get tokens to call APIs like the Microsoft Graph
authenticationResult.getAccessToken();To begin registering your app, begin at the Azure portal
To create an app,
-
Click
New Registration. -
Name your app, select the audience you're targeting, and click
Register.- This sample is focused on
Accounts in any organization and personal Microsoft accounts, but can be modified to support any audience. - Do not register a Redirect URI.
- This sample is focused on
-
Click
Authentication>Add Platform>Android.- Enter the Package Name from your Android studio project.
- Generate a Signature Hash. Refer to the portal for instructions.
-
Hit the
Configuredbutton. Store the MSAL Configuration for the next steps.
-
Clone the code.
git clone https://github.com/Azure-Samples/active-directory-android-native-v2 -
Open Android Studio, and select open an existing Android Studio project. Find the cloned project and open it.
-
Configure the sample code in
auth_config.JSONandAndroidManifest.xml.- Copy and paste the MSAL Configuration JSON from the Azure portal into
auth_config.JSON. - Inside the
AndroidManifest.xml, replaceandroid:hostandandroid:pathwith the same info registered above.auth_config.JSONcontains this information as a reference inside theredirect_urifield.- The Signature Hash should NOT be URL encoded in the
AndroidManifest.xml.
- Copy and paste the MSAL Configuration JSON from the Azure portal into
-
Select Build > Clean Project.
-
Select Run > Run 'app'.
We use Stack Overflow with the community to provide support. We highly recommend you ask your questions on Stack Overflow first and browse existing issues to see if someone has asked your question before.
If you find and bug or have a feature request, please raise the issue on GitHub Issues.
To provide a recommendation, visit our User Voice page.
We enthusiastically welcome contributions and feedback. You can clone the repo and start contributing now. Read our Contribution Guide for more information.
This project has adopted the Microsoft Open Source Code of Conduct. For more information see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.
This library controls how users sign-in and access services. We recommend you always take the latest version of our library in your app when possible. We use semantic versioning so you can control the risk associated with updating your app. As an example, always downloading the latest minor version number (e.g. x.y.x) ensures you get the latest security and feature enhanements but our API surface remains the same. You can always see the latest version and release notes under the Releases tab of GitHub.
If you find a security issue with our libraries or services please report it to secure@microsoft.com with as much detail as possible. Your submission may be eligible for a bounty through the Microsoft Bounty program. Please do not post security issues to GitHub Issues or any other public site. We will contact you shortly upon receiving the information. We encourage you to get notifications of when security incidents occur by visiting this page and subscribing to Security Advisory Alerts.