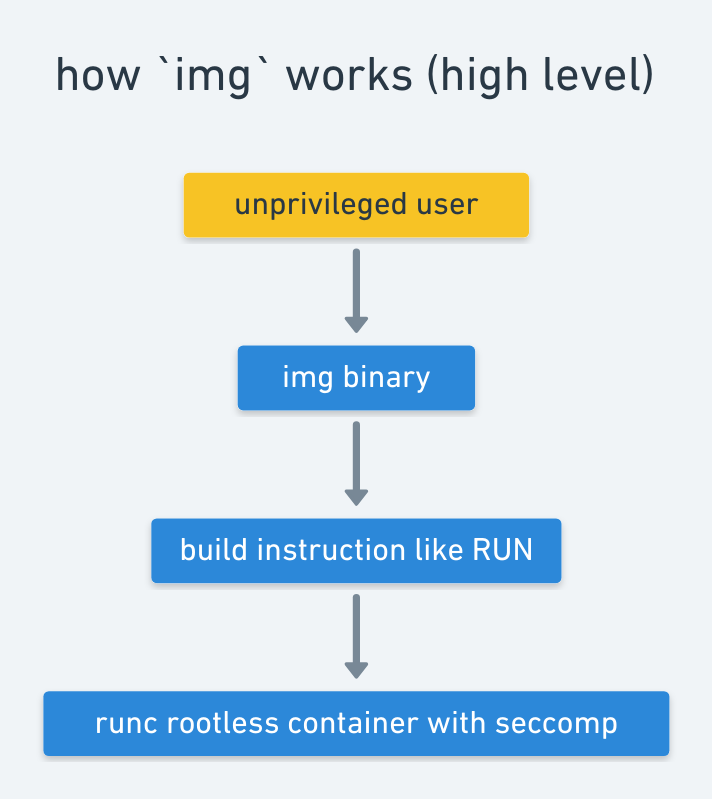
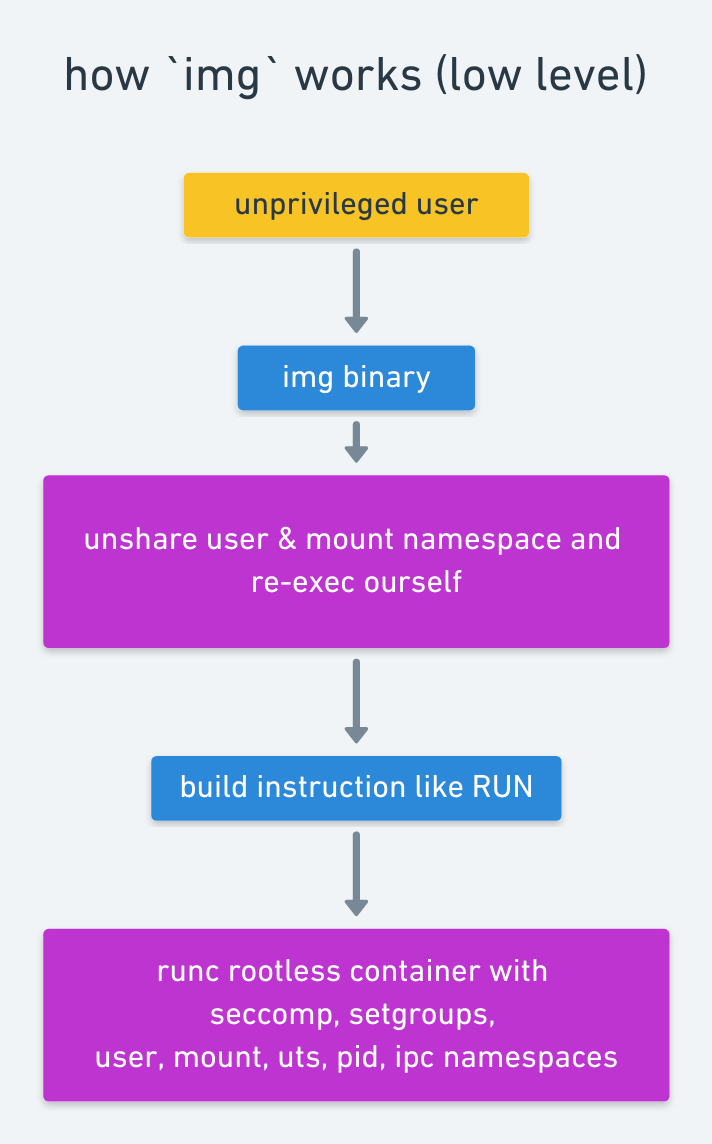
Standalone, daemon-less, unprivileged Dockerfile and OCI compatible container image builder.
img is more cache-efficient than Docker and can also execute multiple build stages concurrently,
as it internally uses BuildKit's DAG solver.
The commands/UX are the same as docker {build,push,pull,login} so all you
have to do is replace docker with img in your scripts, command line, and/or life.
This a glorified cli tool built on top of buildkit. The goal of this project is to be able to build container images as an unprivileged user.
Running unprivileged allows companies who use LDAP and other login mechanisms
to use img without needing root. This is very important in HPC environments
and academia as well.
Currently this works out of the box on a Linux machine if you install via
the directions covered in installing from binaries. This
installation will ensure you have the correct version of img and also runc.
The ultimate goal is to also have this work inside a container. There are patches being made to container runtimes and Kubernetes to make this possible. For the on-going work toward getting patches into container runtimes and Kubernetes, see:
The patches for runc has been merged into the upstream since ecd55a4135e0a26de884ce436442914f945b1e76 (May 30, 2018).
The upstream BuildKit can also run in rootless mode since 65b526438b86a17cf35042011051ce15c8bfb92a (June 1, 2018).
You might also be interested in reading:
Table of Contents
You need to have newuidmap installed.
On Ubuntu, newuidmap is provided by the uidmap package.
runc will be installed on start from an embedded binary if it is not already
available locally.
NOTE: These steps work only for Linux. Compile and run in a container (explained below) if you're on Windows or MacOS.
- linux amd64
# Install latest img binary
$ sudo curl -L https://github.com/genuinetools/img/releases/download/v0.4.1/img-linux-amd64 -o /usr/local/bin/img
# Verify the sha256sum
$ export SHASUM=$(curl -L https://github.com/genuinetools/img/releases/download/v0.4.1/img-linux-amd64.sha256 | awk '{ print $1 }')
$ if [ "$SHASUM" != "$(shasum -a 256 /usr/local/bin/img | awk '{ print $1 }')" ]; then echo "sha256sum mismatch!"; fi
$ sudo chmod a+x /usr/local/bin/img
$ echo "img installed!"$ go get github.com/genuinetools/img$ mkdir -p $GOPATH/src/github.com/genuinetools
$ git clone https://github.com/genuinetools/img $GOPATH/src/github.com/genuinetools/img
$ cd !$
$ make
$ sudo make installThere is an AUR build.
sudo pacman -S imgThere is an ebuild.
$ sudo emerge -a app-emulation/img$ docker run --rm -it \
--name img \
--volume $(pwd):/home/user/src:ro \ # for the build context and dockerfile, can be read-only since we won't modify it
--workdir /home/user/src \ # set the builder working directory
--volume "${HOME}/.docker:/root/.docker:ro" \ # for credentials to push to docker hub or a registry
--cap-add SETGID \ # so we can set groups
--cap-add SETUID \ # so we can map users in a user namespace
--security-opt apparmor=unconfined \ # turn off apparmor so we can mount unprivileged
--security-opt seccomp=unconfined \ # turn off seccomp because it blocks new user namespaces
r.j3ss.co/img build -t user/myimage .$ img -h
Usage: img <command>
Commands:
build Build an image from a Dockerfile.
du Show image disk usage.
ls List images and digests.
login Log in to a Docker registry.
pull Pull an image or a repository from a registry.
push Push an image or a repository to a registry.
rm Remove one or more images.
save Save an image to a tar archive (streamed to STDOUT by default).
tag Create a tag TARGET_IMAGE that refers to SOURCE_IMAGE.
version Show the version information.$ img build -h
Usage: img build [OPTIONS] PATH
Build an image from a Dockerfile.
Flags:
-backend backend for snapshots ([auto native overlayfs]) (default: auto)
-build-arg Set build-time variables (default: [])
-d enable debug logging (default: false)
-f Name of the Dockerfile (Default is 'PATH/Dockerfile') (default: <none>)
-state directory to hold the global state (default: /tmp/img)
-t Name and optionally a tag in the 'name:tag' format (default: <none>)
-target Set the target build stage to build (default: <none>)Use just like you would docker build.
$ img build -t jess/img .
Building jess/img
Setting up the rootfs... this may take a bit.
RUN [/bin/sh -c apk add --no-cache ca-certificates]
--->
fetch http://dl-cdn.alpinelinux.org/alpine/v3.7/main/x86_64/APKINDEX.tar.gz
fetch http://dl-cdn.alpinelinux.org/alpine/v3.7/community/x86_64/APKINDEX.tar.gz
OK: 5 MiB in 12 packages
<--- 5e433zdbh8eosea0u9b70axb3 0 <nil>
RUN [copy /src-0 /dest/go/src/github.com/genuinetools/img]
--->
<--- rqku3imaivvjpgl676se1gupc 0 <nil>
RUN [/bin/sh -c set -x && apk add --no-cache --virtual .build-deps bash git gcc libc-dev libgcc libseccomp-dev linux-headers make && cd /go/src/github.com/genuinetools/img && make static && mv img /usr/bin/img && mkdir -p /go/src/github.com/opencontainers && git clone https://github.com/opencontainers/runc /go/src/github.com/opencontainers/runc && cd /go/src/github.com/opencontainers/runc && make static BUILDTAGS="seccomp" EXTRA_FLAGS="-buildmode pie" EXTRA_LDFLAGS="-extldflags \\\"-fno-PIC -static\\\"" && mv runc /usr/bin/runc && apk del .build-deps && rm -rf /go && echo "Build complete."]
--->
+ apk add --no-cache --virtual .build-deps bash git gcc libc-dev libgcc libseccomp-dev linux-headers make
fetch http://dl-cdn.alpinelinux.org/alpine/v3.7/main/x86_64/APKINDEX.tar.gz
fetch http://dl-cdn.alpinelinux.org/alpine/v3.7/community/x86_64/APKINDEX.tar.gz
(1/28) Installing pkgconf (1.3.10-r0)
(2/28) Installing ncurses-terminfo-base (6.0_p20171125-r0)
(3/28) Installing ncurses-terminfo (6.0_p20171125-r0)
(4/28) Installing ncurses-libs (6.0_p20171125-r0)
(5/28) Installing readline (7.0.003-r0)
(6/28) Installing bash (4.4.19-r1)
....
....
RUN [copy /src-0/certs /dest/etc/ssl/certs]
--->
<--- 6ljir2x800w6deqlradhw0dy2 0 <nil>
Successfully built jess/img$ img ls -h
Usage: img ls [OPTIONS]
List images and digests.
Flags:
-backend backend for snapshots ([auto native overlayfs]) (default: auto)
-d enable debug logging (default: false)
-f Filter output based on conditions provided (default: [])
-state directory to hold the global state (default: /tmp/img)$ img ls
NAME SIZE CREATED AT UPDATED AT DIGEST
jess/img:latest 1.534KiB 9 seconds ago 9 seconds ago sha256:27d862ac32022946d61afbb91ddfc6a1fa2341a78a0da11ff9595a85f651d51e
jess/thing:latest 591B 30 minutes ago 30 minutes ago sha256:d664b4e9b9cd8b3067e122ef68180e95dd4494fd4cb01d05632b6e77ce19118eIf you need to use self-signed certs with your registry, see Using Self-Signed Certs with a Registry.
$ img pull -h
Usage: img pull [OPTIONS] NAME[:TAG|@DIGEST]
Pull an image or a repository from a registry.
Flags:
-backend backend for snapshots ([auto native overlayfs]) (default: auto)
-d enable debug logging (default: false)
-state directory to hold the global state (default: /tmp/img)$ img pull r.j3ss.co/stress
Pulling r.j3ss.co/stress:latest...
Snapshot ref: sha256:2bb7a0a5f074ffe898b1ef64b3761e7f5062c3bdfe9947960e6db48a998ae1d6
Size: 365.9KiBIf you need to use self-signed certs with your registry, see Using Self-Signed Certs with a Registry.
$ img push -h
Usage: img push [OPTIONS] NAME[:TAG]
Push an image or a repository to a registry.
Flags:
-backend backend for snapshots ([auto native overlayfs]) (default: auto)
-d enable debug logging (default: false)
-insecure-registry Push to insecure registry (default: false)
-state directory to hold the global state (default: /tmp/img)$ img push jess/thing
Pushing jess/thing:latest...
Successfully pushed jess/thing:latest$ img tag -h
Usage: img tag SOURCE_IMAGE[:TAG] TARGET_IMAGE[:TAG]
Create a tag TARGET_IMAGE that refers to SOURCE_IMAGE.
Flags:
-backend backend for snapshots ([auto native overlayfs]) (default: auto)
-d enable debug logging (default: false)
-state directory to hold the global state (default: /tmp/img)$ img tag jess/thing jess/otherthing
Successfully tagged jess/thing as jess/otherthing$ img save -h
Usage: img save [OPTIONS] IMAGE [IMAGE...]
Save an image to a tar archive (streamed to STDOUT by default).
Flags:
-backend backend for snapshots ([auto native overlayfs]) (default: auto)
-d enable debug logging (default: false)
-o Write to a file, instead of STDOUT (default: <none>)
-state directory to hold the global state (default: /tmp/img)$ img save jess/thing | docker load
6c3d70c8619c: Loading layer [==================================================>] 9.927MB/9.927MB
7e336c441b5e: Loading layer [==================================================>] 5.287MB/5.287MB
533fecff21a8: Loading layer [==================================================>] 2.56MB/2.56MB
3db7019eac28: Loading layer [==================================================>] 1.679kB/1.679kB
Loaded image: jess/thingUsage: img rm [OPTIONS] IMAGE [IMAGE...]
Remove one or more images.
Flags:
-backend backend for snapshots ([auto native overlayfs]) (default: auto)
-d enable debug logging (default: false)
-state directory to hold the global state (default: /tmp/img)$ img du -h
Usage: img du [OPTIONS]
Show image disk usage.
Flags:
-backend backend for snapshots ([auto native overlayfs]) (default: auto)
-d enable debug logging (default: false)
-f Filter output based on conditions provided (snapshot ID supported) (default: <none>)
-state directory to hold the global state (default: /tmp/img)$ img du
ID RECLAIMABLE SIZE DESCRIPTION
sha256:d9a48086f223d28a838263a6c04705c8009fab1dd67cc82c0ee821545de3bf7c true 911.8KiB pulled from docker.io/tonistiigi/copy@sha256:476e0a67a1e4650c6adaf213269a2913deb7c52cbc77f954026f769d51e1a14e
7ia86xm2e4hzn2u947iqh9ph2 true 203.2MiB mount /dest from exec copy /src-0 /dest/go/src/github.com/genuinetools/img
...
sha256:9f131fba0383a6aaf25ecd78bd5f37003e41a4385d7f38c3b0cde352ad7676da true 958.6KiB pulled from docker.io/library/golang:alpine@sha256:a0045fbb52a7ef318937e84cf7ad3301b4d2ba6cecc2d01804f428a1e39d1dfc
sha256:c4151b5a5de5b7e272b2b6a3a4518c980d6e7f580f39c85370330a1bff5821f1 true 472.3KiB pulled from docker.io/tonistiigi/copy@sha256:476e0a67a1e4650c6adaf213269a2913deb7c52cbc77f954026f769d51e1a14e
sha256:ae4ecac23119cc920f9e44847334815d32bdf82f6678069d8a8be103c1ee2891 true 148.9MiB pulled from docker.io/library/debian:buster@sha256:a7789365b226786a0cb9e0f142c515f9f2ede7164a6f6be4a1dc4bfe19d5ec9c
bkrjrzv3nvp7lvzd5cw9vzut7* true 4.879KiB local source for dockerfile
sha256:db193011cbfc238d622d65c4099750758df83d74571e8d7498392b17df381207 true 467.2MiB pulled from docker.io/library/golang:alpine@sha256:a0045fbb52a7ef318937e84cf7ad3301b4d2ba6cecc2d01804f428a1e39d1dfc
wn4m5i5swdcjvt1ud5bvtr75h* true 4.204KiB local source for dockerfile
Reclaimable: 1.08GiB
Total: 1.08GiBIf you need to use self-signed certs with your registry, see Using Self-Signed Certs with a Registry.
$ img login -h
Usage: img login [OPTIONS] [SERVER]
Log in to a Docker registry.
If no server is specified, the default (https://index.docker.io/v1/) is used.
Flags:
-backend backend for snapshots ([auto native overlayfs]) (default: auto)
-d enable debug logging (default: false)
-p Password (default: <none>)
-password-stdin Take the password from stdin (default: false)
-state directory to hold the global state (default: /tmp/img)
-u Username (default: <none>)We do not allow users to pass all the custom certificate flags on commands because it is unnecessarily messy and can be handled through Linux itself. Which we believe is a better user experience than having to pass three different flags just to communicate with a registry using self-signed or private certificates.
Below are instructions on adding a self-signed or private certificate to your trusted ca-certificates on Linux.
Make sure you have the package ca-certificates installed.
Copy the public half of your CA certificate (the one user to sign the CSR) into the CA certificate directory (as root):
$ cp cacert.pem /usr/share/ca-certificatesRebuild the directory with your certificate included, run as root:
# On debian, this will bring up a menu.
# Select the ask option, scroll to the certificate you are adding,
# mark it for inclusion, and select ok.
$ dpkg-reconfigure ca-certificates
# On other distros...
$ update-ca-certificatesTo mount a filesystem without root accsess, img automatically invokes
newuidmap(1)/newgidmap(1)
SUID binaries to prepare SUBUIDs/SUBGIDs, which is typically required by apt.
Make sure you have sufficient entries (typically >=65536) in your
/etc/subuid and /etc/subgid.
The auto backend is resolved into either native or overlayfs, depending on
the availability of overlayfs on the system.
The native backends creates image layers by simply copying files.
copy_file_range(2) is used when available.
You can also use overlayfs
backend, but that requires a kernel patch from Ubuntu to be unprivileged,
see #22.
Please do! This is a new project and can use some love <3. Check out the issues.
The local directories are mostly re-implementations of buildkit interfaces to
be unprivileged.
A lot of this is based on the work of moby/buildkit. Thanks @tonistiigi and @AkihiroSuda!