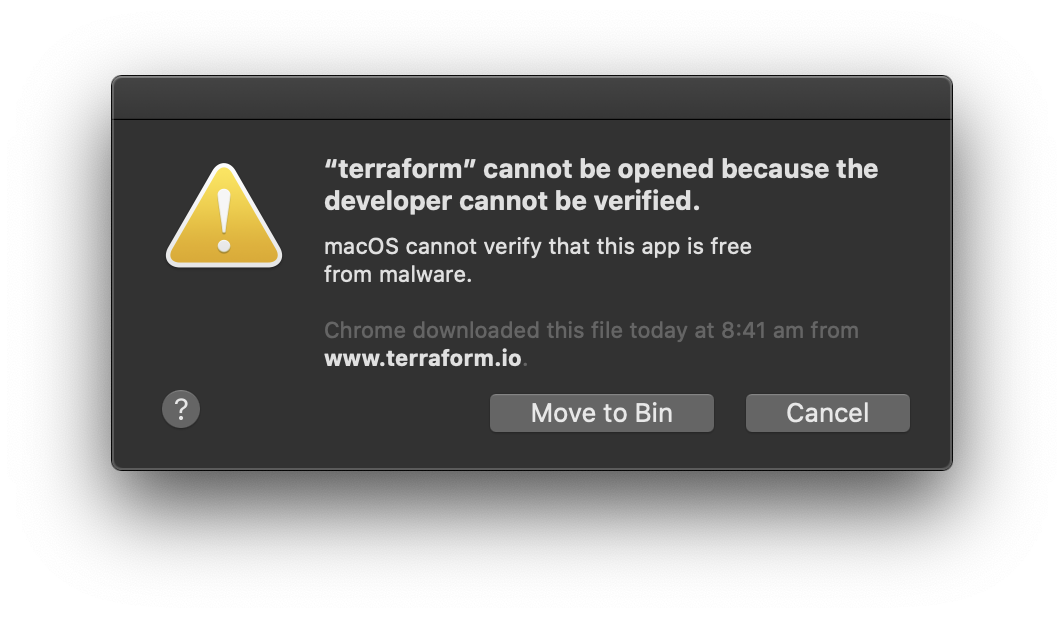
macOS Catalina error: “terraform” cannot be opened because the developer cannot be verified.
rouralberto opened this issue · 39 comments
Apparently, the workaround is quite painful:
- In the Finder on your Mac, locate the app you want to open.
- Control-click the app icon, then choose Open from the shortcut menu.
- Click Open.
The app is saved as an exception to your security settings, and you can open it in the future by double-clicking it or from cli, just as you can with any authorised app.
Hi @roura356a! Thanks for reporting this.
Indeed the new version of MacOS is stricter about running software you've downloaded that isn't signed with an Apple developer key. Terraform distributions are signed with a HashiCorp key with signatures distributed out of band on releases.hashicorp.com, but MacOS Catalina is requiring participation in Apple's developer program specifically, and Terraform is currently not built to support that.
Thank you for sharing your workaround. We're looking into the best way to proceed here to see if we can make this work better.
sudo spctl --master-disable to allow apps downloaded from Anywhere
sudo spctl --master-disableto allow apps downloaded from Anywhere
@EmpireJones Is there a way to do it for a specific app only?
Another simpler way is to go to System Preferences -> Security & Privacy -> General and enable any blocked app from Allow apps downloaded from pane at the bottom of the window.
@aprofromindia agreed, just like it always worked in Mac OS when you had security settings. Whenever an app is blocked. You just have to allow them there.
Removing existing terraform executable and installing it with brew install terraform solved the problem for me.
Another simpler way is to go to System Preferences -> Security & Privacy -> General and enable any blocked app from Allow apps downloaded from pane at the bottom of the window.
This does not appear to be available in Catalina.
- In the Finder on your Mac, locate the app you want to open.
- Control-click the app icon, then choose Open from the shortcut menu.
- Click Open.
The app is saved as an exception to your security settings, and you can open it in the future by double-clicking it or from cli, just as you can any authorised app.
This does work.
This is affecting all HashiCorp binaries on Catalina. We are looking into the macOS notarizing process to no longer require these work-arounds on Catalina. We will provide an update when we learn more about this.
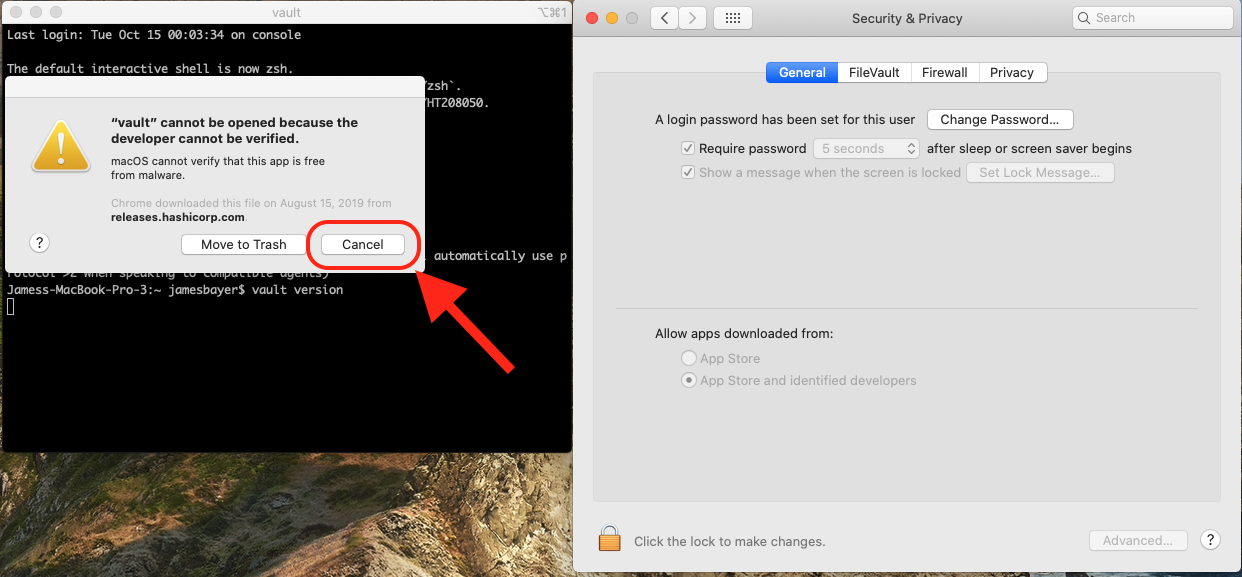
Here is the process I used to run the existing binaries on Catalina that does not require control-click. First I open the "Security & Privacy" control panel from System Preferences.
- Attempt to run the binary after upgrading to Catalina. It will fail. Click cancel instead of moving it to the trash. You should see
Killed: 9as output in the terminal.
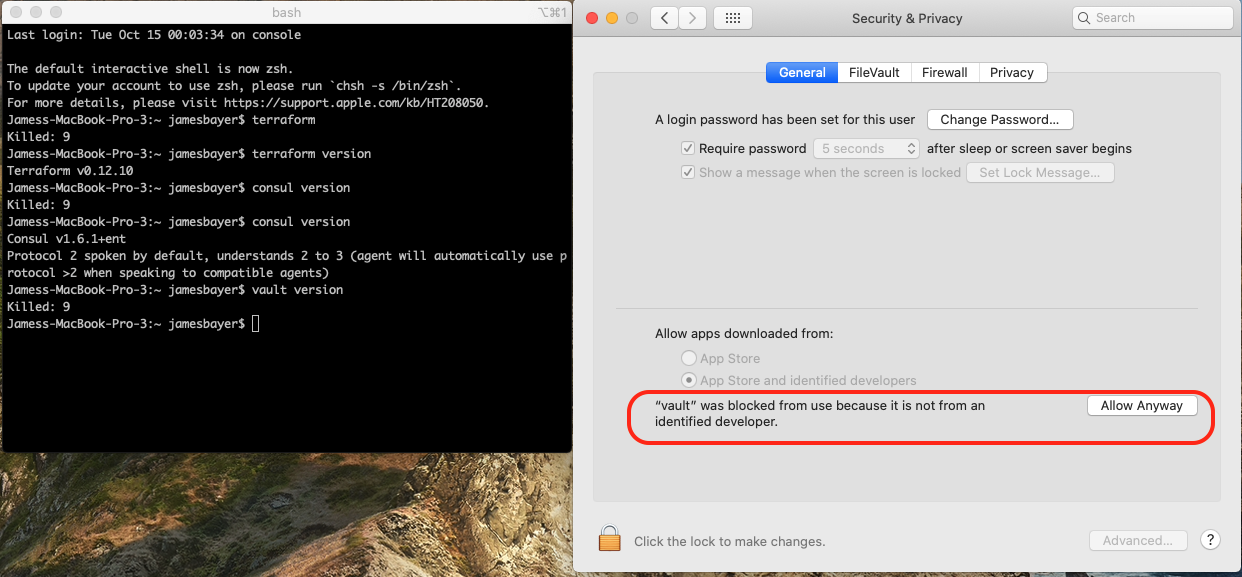
- The "Security & Privacy" panel, "General" tab is updated to reflect that the binary was recently prevented from running. I clicked "Allow Anyway".
- Attempt to run the binary again. This time a different prompt is shown and you are able to select "Open". After clicking open, the binary should run as you expect.
Had a similar issue with racket so that supports the idea that this issue is macOS Catalina specific.
The simple answer that @roura356a shared worked for me (just locate file > right click > open).
Good to know there are other workarounds too.
“racket” cannot be opened because the developer cannot be verified.
Thanks for the wonderful and generally applicable workarounds!
Same issue with 0.12.12
Argh! Same with latest Java (version 13.0.1)
The only solution that worked for me is to delete the com.apple.quarantine extended attribute from the downloaded directory of the app. For example this command solved the issue with GraalVM:
xattr -d com.apple.quarantine /Library/Java/JavaVirtualMachines/graalvm-ce-19.2.1
I've learned a bit more about this. The com.apple.quarantine metadata attribute is set on files by applications like browsers that download files over the network. It is possible to remove the com.apple.quarantine metadata attribute with a user that has permission to do it. Additionally there are some other alternatives mentioned by MITRE that avoid the attribute being set on files.
Apps loaded onto the system from USB flash drive, optical disk, external hard drive, or even from a drive shared over the local network won’t set this flag.
The same thing happens to me, but with a link on a browser, so I cannot right click for the open option. Does anyone know how to solve it in this case?
@anhdungle93 are you able to run this command wherever your terraform binary is located instead of /path/to/terraform?
xattr -d com.apple.quarantine /path/to/terraform
downloading with wget instead of chrome solved the problem for me.
I'm having the same problem with my cvx installation for Matlab, but when I run my code, it calls hundreds of separate programs, that all independently are denied permission. Does anybody know how to allow a folder of apps?
If you use the -r flag, this will run recursively:
xattr -r -d com.apple.quarantine /path/to/dir
If you use the
-rflag, this will run recursively:
xattr -r -d com.apple.quarantine /path/to/dir
This works, thanks a lot.
@roura356a It is worked, pretty cool! thx.
Hi all! Good news! HashiCorp release engineering has been working hard on getting a process build for OS X Catalina release notarization. We're planning on using this process for the upcoming Terraform 0.12.18 release, which is tentatively scheduled for Wednesday December 11th.
Before then, we'd appreciate your help confirming that our signed binaries work in your environment. We've built an 0.12.18 pre-release solely for the sake of verifying that Catalina code notarization is working. I do not recommend using this build for production use - it's just for the sake of validating that we've added Apple notarization to the release process correctly.
Here's the output of codesign on the terraform binary in that attached zip:
codesign -dv --verbose=4 terraform 127 ↵ 956 10:19:50
Executable=/Users/danieldreier/Downloads/terraform
Identifier=terraform
Format=Mach-O thin (x86_64)
CodeDirectory v=20500 size=442581 flags=0x10000(runtime) hashes=13825+2 location=embedded
VersionPlatform=1
VersionMin=657664
VersionSDK=657664
Hash type=sha256 size=32
CandidateCDHash sha1=a9b11c0f3308e0688cc869ba91292987a477c7fb
CandidateCDHash sha256=a057f871b185c90cce79436afc7ed55769c8ef90
Hash choices=sha1,sha256
Page size=4096
CDHash=a057f871b185c90cce79436afc7ed55769c8ef90
Signature size=9060
Authority=Developer ID Application: Hashicorp, Inc. (D38WU7D763)
Authority=Developer ID Certification Authority
Authority=Apple Root CA
Timestamp=Dec 5, 2019 at 7:41:22 AM
Info.plist=not bound
TeamIdentifier=D38WU7D763
Runtime Version=10.9.0
Sealed Resources=none
Internal requirements count=1 size=172
If you care about this issue, please download that zip, run it on your Catalina OS X machine, and let us know here if you run into notarization issues. If we don't get any negative feedback here, we'll move forward and start notarizing future terraform releases starting on 0.12.18.
And, again, when you're done please do not use this as 0.12.18 - throw it away when you're done and don't install it permanently.
I downloaded 0.12.18 pre-release and tried getting it to run on my MacOS w/Catalina and I still get no response. I did update my XCode Tools before this so that I can get the Developer Tools icon to show up in the Security & Privacy dialog in the Privacy window based on the post above. I also clicked Agree to allow the terraform app to run even though it is an application purchased through the App Store.
So after doing all the above, I open a new terminal window and navigate to the downloaded terraform app (already unzipped) and try to run it and it just hangs; no response. I voted down the post above indicating my issue with the terraform cli is not fixed with this release. I kinda need to get this working, I would have to have to roll back just to use terraform.
I downloaded 0.12.18 pre-release and tried getting it to run on my MacOS w/Catalina and I still get no response. I did update my XCode Tools before this so that I can get the Developer Tools icon to show up in the Security & Privacy dialog in the Privacy window based on the post above. I also clicked Agree to allow the terraform app to run even though it is an application purchased through the App Store.
So after doing all the above, I open a new terminal window and navigate to the downloaded terraform app (already unzipped) and try to run it and it just hangs; no response. I voted down the post above indicating my issue with the terraform cli is not fixed with this release. I kinda need to get this working, I would have to have to roll back just to use terraform.
Sorry you're still having issues with this. Do you have time for a screenshare so we can help sort this out? You can reach me at mdegges@hashicorp.com.
Edit:
Below are the steps you can use to test the 0.12.18 pre-release binary
- Navigate to https://github.com/hashicorp/terraform/files/3928438/terraform-v0.12.18-prerelease-catalina-signed__darwin_amd64.zip in a browser to download the zipfile
- Run
open /path/to/terraform-v0.12.18-prerelease-catalina-signed__darwin_amd64.zipin your terminal. The terraform binary will now be available for use - Run
/path/to/terraformin your terminal to view the available commands - Test out a command, e.g.
/path/to/terraform/versionto view the version
Update: I uninstalled all the versions of terraform and reinstalled it using Brew and it installed this version: https://homebrew.bintray.com/bottles/terraform-0.12.17.catalina.bottle.tar.gz
And it worked perfectly.
Below are the steps you can use to test the 0.12.18 pre-release binary
- Navigate to https://github.com/hashicorp/terraform/files/3928438/terraform-v0.12.18-prerelease-catalina-signed__darwin_amd64.zip in a browser to download the zipfile
- Run
open /path/to/terraform-v0.12.18-prerelease-catalina-signed__darwin_amd64.zipin your terminal. The terraform binary will now be available for use- Run
/path/to/terraformin your terminal to view the available commands- Test out a command, e.g.
/path/to/terraform/versionto view the version
Followed these steps and received no prompt. Everything worked as expected.
@danieldreier When can we expect this pre-release to become an actual release? The notarization process seems to works fine. Is it possible to make a release with this ASAP?
@sanspace We're planning a release this week! We know people are eager to have this 😄
brrew install terraform should be the easiest way for latest installation.
Terraform 0.12.18 has been released with a notarized binary for OS X 10.15+: https://github.com/hashicorp/terraform/releases/tag/v0.12.18
A huge thanks to the community for your help and patience.
From the changelog:
NOTES:
-
cli: Our darwin releases for this version and up will be signed and notarized according to Apple's requirements.
Prior to this release, MacOS 10.15+ users attemping to run our software reported seeing the error: "'terraform' cannot be opened because the developer cannot be verified." This error affected all MacOS 10.15+ users who downloaded our software directly via web browsers, and was caused by changes to Apple's third-party software requirements.
Our recommended approach to install and interact with the Terraform CLI can be found here.
MacOS 10.15+ users should plan to upgrade to 0.12.18+.
This is really awesome. Sorry for commenting a closed issue, but @pkolyvas - does this apply to providers as well, or is only Terraform core signed...? The reason I'm asking is, the providers seem to be executing as different binaries. Some security software on Windows/Macs tend to block terraform - and not having signed binaries has been a painful issue also on those before, hence the question.
The reason I'm asking is, the providers seem to be executing as different binaries. Some security software on Windows/Macs tend to block terraform - and not having signed binaries has been a painful issue also on those before, hence the question.
Are you running into any errors trying to use the providers with the latest terraform core release? Testing with the AWS and GCP providers on my end doesn't reveal any errors, but we're happy to help troubleshoot if you can send over repro steps.
Are you running into any errors trying to use the providers with the latest terraform core release? Testing with the AWS and GCP providers on my end doesn't reveal any errors, but we're happy to help troubleshoot if you can send over repro steps.
I need to test this with our company's IT support to see how this works or not. Let's see... What I've understood is, it is the provider binary (AWS as an example) which would communicate with AWS APIs. hence I think the provider binary should also be signed so it could be whitelisted.
@iiro my understanding of the way MacOS new protections work is that specified MacOS programs (such as web browsers like Chrome, Safari, Firefox) will add file system extended attributes like com.apple.quarantine that denote that files were downloaded from the internet if the files are not notarized. So if you download the AWS Provider directly from a browser directly, I believe you would need the file notarized or explicitly enable it to work.
However, the typical terraform workflow the standard terraform binary that is signed will download the providers and does not add the file system extended attributes for the provider binaries that it downloads. That's why I think this worked in @mdeggies example.
Friendly reminder that this is a closed issue and will be locked eventually -- any new issues should be reported as such (but it seems like what has followed has generally been discussion).
Please open a new issue for any existing, or emergent, issues related to this, but the original issue is closed.
Another simpler way is to go to System Preferences -> Security & Privacy -> General and enable any blocked app from Allow apps downloaded from pane at the bottom of the window.
Good one...
Most of the new apps get blocked after upgrade. You can see the terraform is blocked when you open Security and Privacy and then allow it. Instead of allow of them as told by some people.
I'm going to lock this issue because it has been closed for 30 days ⏳. This helps our maintainers find and focus on the active issues.
If you have found a problem that seems similar to this, please open a new issue and complete the issue template so we can capture all the details necessary to investigate further.