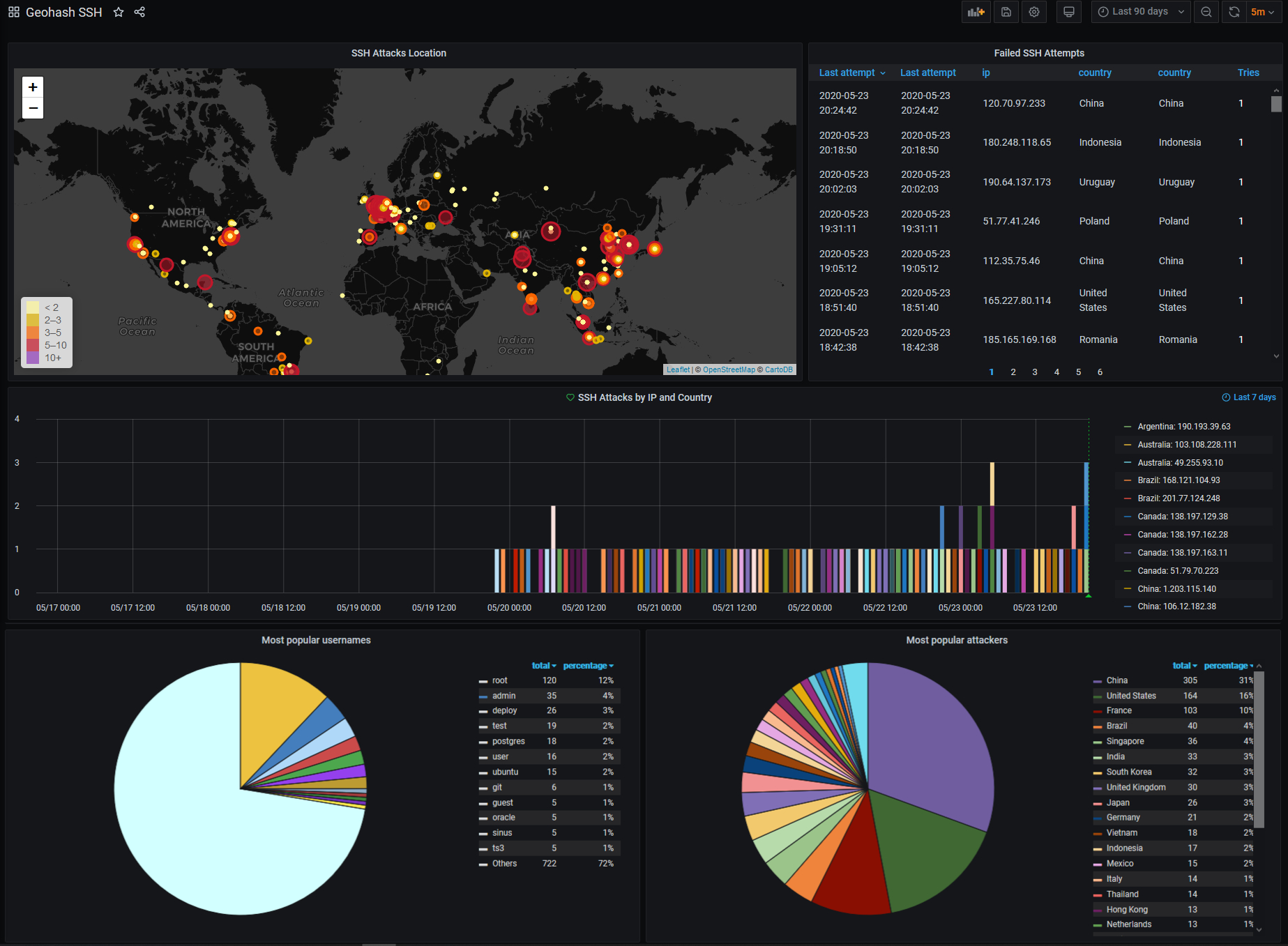
Visualize bruteforce SSH attacker's location in real time
Multiarch supported linux/amd64,linux/arm/v7,linux/arm64 for Raspberry Pis 😄
Thanks to Schkn for its original post https://devconnected.com/geolocating-ssh-hackers-in-real-time/
Preview
Grafana dashboard id : 12323
docker run -e INFLUX_HOST=myinfluxdb.com -e INFLUX_DB=geoloc -p 7070:7070 acouvreur/ssh-log-to-influx
Prerequisites
- Docker
- Rsyslog
- An InfluxDB instance (or use docker-compose.standalone.yml)
- A Grafana instance (or use docker-compose.standalone.yml)
Getting started
With a bundled InfluxDB and Grafana
docker-compose -f docker-compose.standalone.yml up
With an external InfluxDB
INFLUX_PROTOCOLoptional default: http Protocol to use, http or https.INFLUX_HOSTInflux (FQDN) host to connect to.INFLUX_PORToptional default: 8086 Influx port to connect to.INFLUX_USERoptional default: root Username for connecting to the database.INFLUX_PWDoptional default: root Password for connecting to the database.INFLUX_DBDatabase to operate on.
Note: You can use the Docker network FQDN if you put the service in the same Docker network as your InfluxDB instance. INFLUX_HOST will be influx if your service name is influx.
docker-compose up -d
Test the TCP server
docker-compose -f docker-compose.standalone.yml upnetcat localhost 7070orncat localhost 7070with Git bash for Windows- type:
Failed password for username from 206.253.167.10 port 11111 ssh2 - Data should be parsed and added
Rsyslog configuration
Add this under /etc/rsyslog.conf to forward ssh auth failures to local server :
I have 'PasswordAuthentication' activated
template(name="OnlyMsg" type="string" string="%msg:::drop-last-lf%\n")
if $programname == 'sshd' then {
if $msg startswith ' Failed' then {
action(type="omfwd" target="127.0.0.1" port="7070" protocol="tcp" template="OnlyMsg")
}
}
I have 'PubkeyAuthentication' activated
template(name="OnlyMsg" type="string" string="%msg:::drop-last-lf%\n")
if $programname == 'sshd' then {
if $msg startswith ' Invalid' then {
action(type="omfwd" target="127.0.0.1" port="7070" protocol="tcp" template="OnlyMsg")
} else if $msg startswith ' Disconnected from authenticating' then {
action(type="omfwd" target="127.0.0.1" port="7070" protocol="tcp" template="OnlyMsg")
}
}
Debug configuration
- If you want to skip certificate validation, set
NODE_TLS_REJECT_UNAUTHORIZEDto 0, but don't do this without understanding the implications. DEBUG_LEVEL: level of logging in log4js, default is "info".