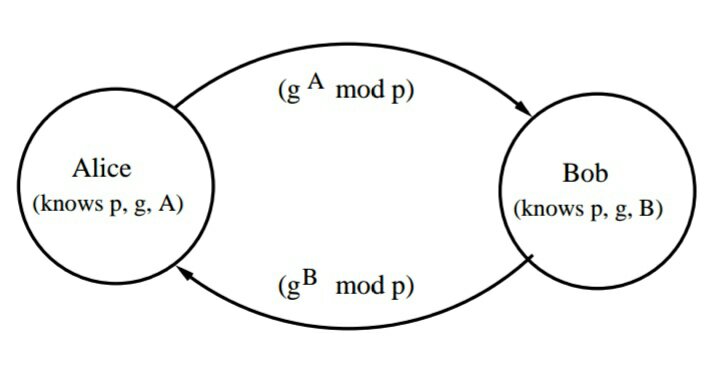
This project partially implements the HTTPS protocol using key exchange through Diffie Hellman and message simmetric encryption through AES.
Python 3.9.0
You can make use of the available Makefile targets to:
The following command installs all python dependencies on a virtual environment:
$ make install
checking for 'python3'...ok
Collecting antiorm==1.2.1
Using cached antiorm-1.2.1.tar.gz (171 kB)
Collecting cffi==1.15.0
...
Successfully installed PyYAML-6.0 antiorm-1.2.1 ...
The following command tests code behavior using unittest:
$ make test
checking for 'python3'...ok
....
-----------------------------------
Ran 4 tests in 0.050s
OK
The following command cleans the state kept on a SQLite database:
$ make clean
OK
This project is able to establish secure communication between two points A and B.
Notice that Diffie Hellman's point of failure is known (man-in-the-middle attack).
To achieve secure communication, first you need to exchange keys between two communication points, and then encrypt/decrypt the messages along the conversation.
To exchange keys, use mode exch.
First, you need to generate your own secret integer (a), which will be stored, and generate a public hexadecimal (A) to be exchanged with your receiver.
You can also receive a public hexadecimal (B) from your receiver, and generate a key (key), which also will be stored for further communication.
To achieve this goals, first you need to create a argument file (yaml) with a public prime number (p) and its generator (g):
p: "B10B8F96A080E01DDE92DE5EAE5D54EC52C99FBCFB06A3C\
69A6A9DCA52D23B616073E28675A23D189838EF1E2EE652C\
013ECB4AEA906112324975C3CD49B83BFACCBDD7D90C4BD7\
098488E9C219A73724EFFD6FAE5644738FAA31A4FF55BCCC\
0A151AF5F0DC8B4BD45BF37DF365C1A65E68CFDA76D4DA70\
8DF1FB2BC2E4A4371"
g: "A4D1CBD5C3FD34126765A442EFB99905F8104DD258AC507\
FD6406CFF14266D31266FEA1E5C41564B777E690F5504F21\
3160217B4B01B886A5E91547F9E2749F4D7FBD7D3B9A92EE\
1909D0D2263F80A76A6A24C087A091F531DBF0A0169B6A28\
AD662A4D18E73AFA32D779D5918D08BC8858F4DCEF97C2A2\
4855E6EEB22B3B2E5"Notice: the larger are 'p' and 'g' values, safer is the communication
The following command generates your private integer (a) and public hex (A):
$ ./run.sh mode exch --A --argfile args.yaml
A: 3d87e93b6227cf6361bd060b2bc68bff0b285390307a02d1fc02554e65dcac3d727ee62b6cd1b042c311f2960bcc7d7d9cc0d6a05bafbc687f6fcebc72d76cee0b154a1fca0d34154634e83a7e3fd42f5e4e576d3c5f4754ffd0e7a5543cca6c413545e6e95a6a848d58ed971c881e1b2a8887fac09b36b1f7e7b5cb52c6d804
Notice the usage of
--argfile <p_g_yaml_file_path>and--Aarguments
The following command generates the communication key (key), used to encrypt communication messages:
$ ./run.sh mode exch --argfile args.yaml --key 2D3811A7F1AC7A364DAAF2BE4A8F28A12E701FDB0B6E03660617C95A52A46CADCC3B309B928F74ACC2353CA652E26539A095A778FA7FC6A0B3AA76A1665E16DCCAFF58E451B184BA2B4A3CC16D3C2B376B3B6601CD0F98C811EEA3E4362616EA5EA83EA567936DD73B804398E55A08018CD21BE083A4F26490BAF3ED8CB70C13
key: 115eb4313a6f6e1e225b88dc6f630914
Notice the usage of
--argfile <p_g_yaml_file_path>and--keyarguments
Notice: The value passed for the
--keyargument must be generated by your receiver (B).
To exchange messages, use mode talk.
The AES simmetric encrtyption algorithm is used to encrypt and decrypt the messages exchanged.
To achieve the goal of encrypting and decrypting messages you have to execute the steps described at Exchange keys section.
The following command encrypts a plaintext message:
$ ./run.sh mode talk --send 'hello world!'
encrypted: 224ac30c8f66c5c7bfc5fa54c30ff4272ee9abb036680c8efe07b4519c21567c
Notice the usage of
--send <message>argument
The following command encrypts a plaintext inverted message:
$ ./run.sh mode talk --sendinv 'hello world!'
encrypted: 70340ecb967b22a711449be99e9e0d57cda64149c42ae3f0427f593baf3ae9e1
Notice the usage of
--sendinv <message>argument
The following command decrypts an encrypted message using this project:
$ ./run.sh mode talk --recv 224ac30c8f66c5c7bfc5fa54c30ff4272ee9abb036680c8efe07b4519c21567c
decrypted: hello world!
Notice the usage of
--recv <message>argument