An Advanced Web Panel • Built on Xray Core
Disclaimer: This project is only for personal learning and communication, please do not use it for illegal purposes, please do not use it in a production environment
sudo ufw allow 80/tcp
sudo ufw allow 443/tcp
sudo certbot certonly --standalone -d domain.com
# Certificate is saved at: /etc/letsencrypt/live/domain.com/fullchain.pem
# Key is saved at: /etc/letsencrypt/live/domain.com/privkey.pem
sudo certbot renew --dry-runSo the final version of our docker-compose.yml will look something like this:
---
version: "3"
services:
3x-ui:
image: ghcr.io/mhsanaei/3x-ui:latest
container_name: 3x-ui
hostname: domain.com
volumes:
- $PWD/db/:/etc/x-ui/
- /etc/letsencrypt/:/etc/letsencrypt/:rw
environment:
XRAY_VMESS_AEAD_FORCED: "false"
tty: true
network_mode: host
restart: unless-stoppeddocker compose up -dAfter that you will be able to login to your panel with default credentials (admin/admin) on
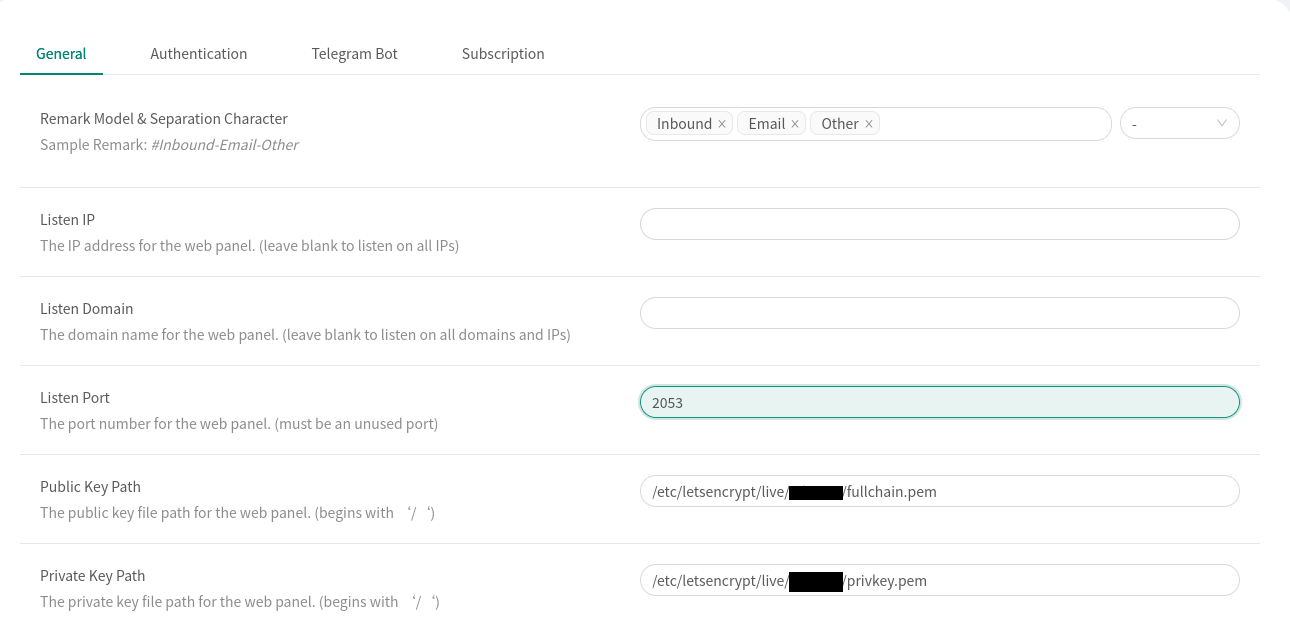
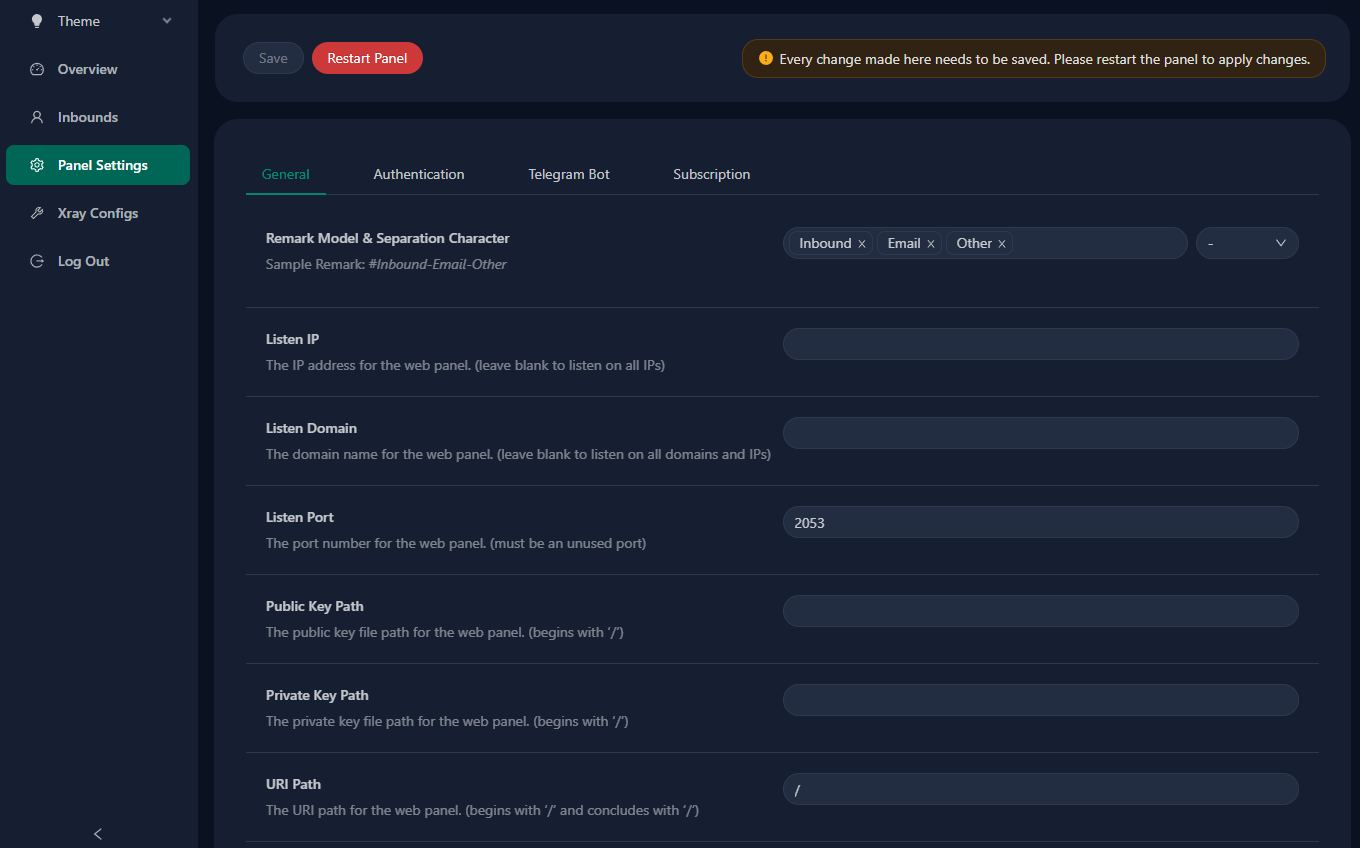
Navigate to Panel Settings and under the General tab we will add our SSL certificate paths:
publich key path: /etc/letsencrypt/live/domain.com/fullchain.pem
private key path: /etc/letsencrypt/live/domain.com/privkey.pemPress Save but do not restart the panel just yet. Instead head to Authentication and change your password (and username). Now you can save and restart the panel after which make sure to login using https://domain.com:2053.
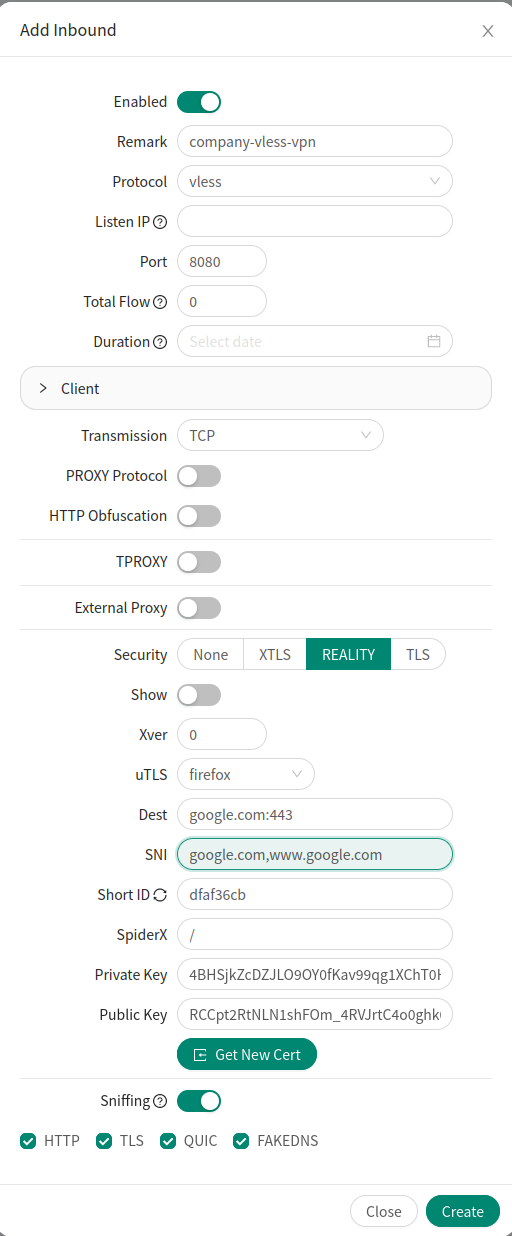
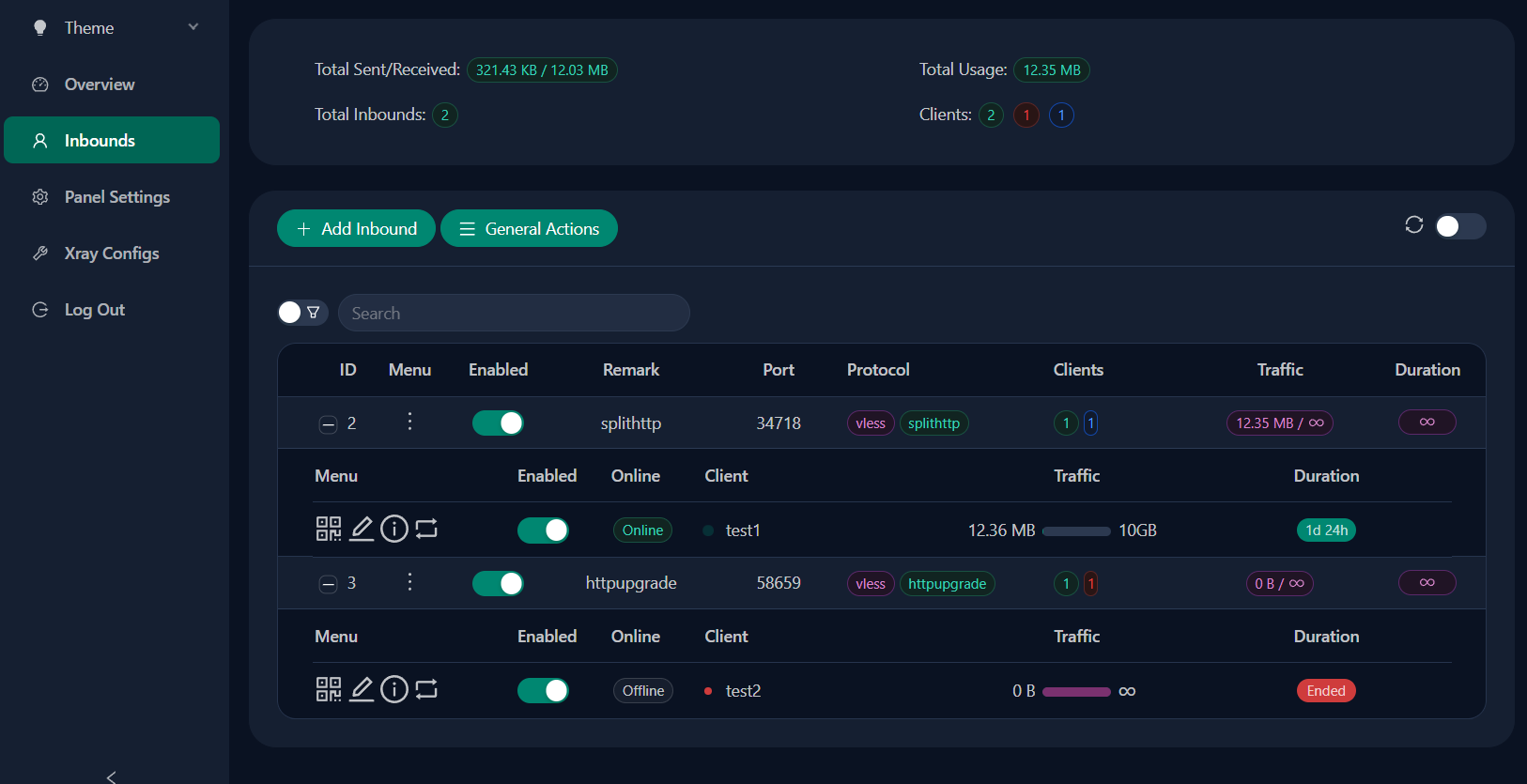
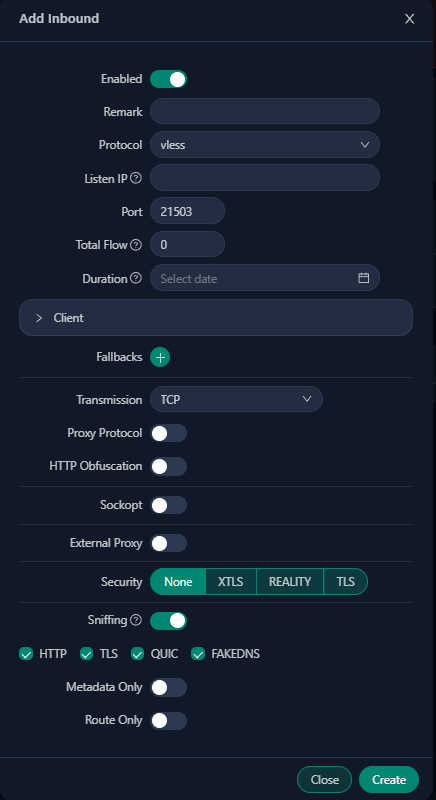
To setup a tunnel, head to Inbounds and click on Add Inbound button.
Do not yet touch the Client configuration, we will deal with it in the next step.
In the Remark field it is good to give the tunnel an appropriate name.
Choose a Port number. It is good idea to use some common web port, such as https 443. In my case it is already in use so I set my port to 8080.
For Security you should chose REALITY.
As uTLS you can chose any browser you like, in my case I use firefox.
In the Dest and SNI fields we will add the URLs that the traffic will pretend to be destining to.
Finally in the bottom click on Get New Cert button.
For all the other options you should use the defaults.
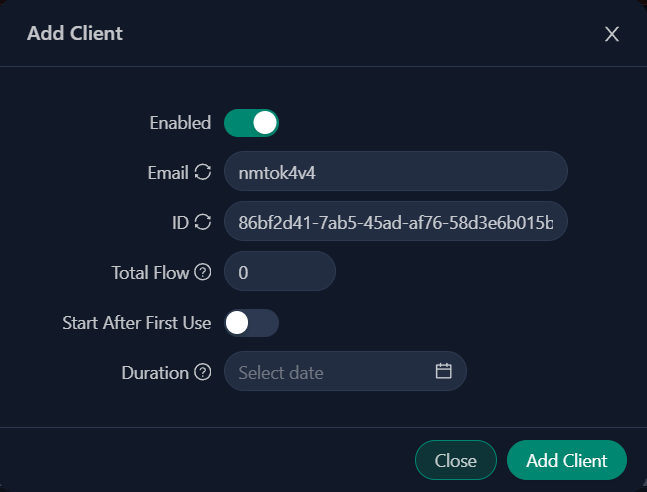
Now you can click open the Client section. You can see an auto-generated client. You can modify an Email field if you want or live it as is.
There is no need to modify additional fields if you do not want to limit the traffic quota etc for the user.
Now you can press Create to create your client.
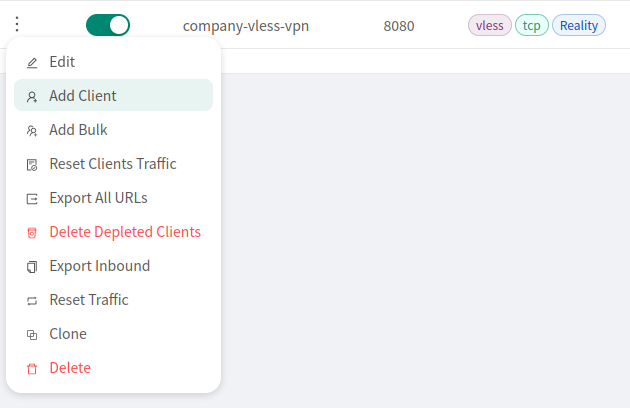
If you want to add additional users, you can do so by pressing the 3 dots next to the tunnel name and selecting Add Client option from the list:
sudo ufw allow 8080/tcpbash <(curl -Ls https://raw.githubusercontent.com/mhsanaei/3x-ui/master/install.sh)
To install your desired version, add the version to the end of the installation command. e.g., ver v2.3.11:
bash <(curl -Ls https://raw.githubusercontent.com/mhsanaei/3x-ui/master/install.sh) v2.3.11
Click for SSL Certificate details
To manage SSL certificates using ACME:
-
Ensure your domain is correctly resolved to the server.
-
Run the
x-uicommand in the terminal, then chooseSSL Certificate Management. -
You will be presented with the following options:
- Get SSL: Obtain SSL certificates.
- Revoke: Revoke existing SSL certificates.
- Force Renew: Force renewal of SSL certificates.
To install and use Certbot:
apt-get install certbot -y
certbot certonly --standalone --agree-tos --register-unsafely-without-email -d yourdomain.com
certbot renew --dry-runThe management script includes a built-in SSL certificate application for Cloudflare. To use this script to apply for a certificate, you need the following:
- Cloudflare registered email
- Cloudflare Global API Key
- The domain name must be resolved to the current server through Cloudflare
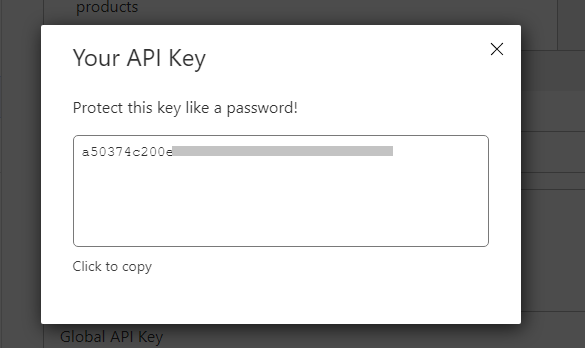
How to get the Cloudflare Global API Key:
- Run the
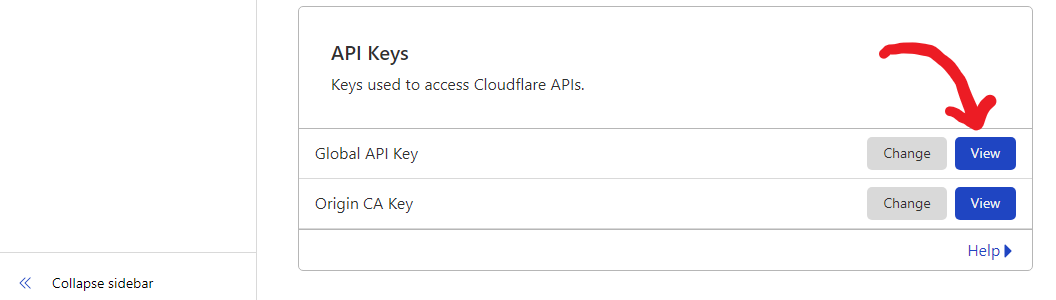
x-uicommand in the terminal, then chooseCloudflare SSL Certificate. - Visit the link: Cloudflare API Tokens.
- Click on "View Global API Key" (see the screenshot below):
- You may need to re-authenticate your account. After that, the API Key will be shown (see the screenshot below):
When using, just enter your domain name, email, and API KEY. The diagram is as follows:
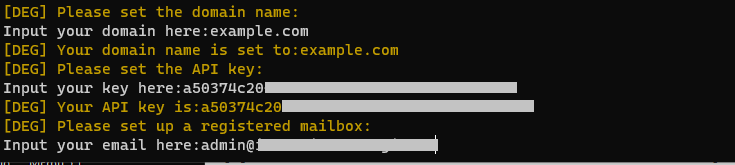
Click for manual install details
- To download the latest version of the compressed package directly to your server, run the following command:
ARCH=$(uname -m)
case "${ARCH}" in
x86_64 | x64 | amd64) XUI_ARCH="amd64" ;;
i*86 | x86) XUI_ARCH="386" ;;
armv8* | armv8 | arm64 | aarch64) XUI_ARCH="arm64" ;;
armv7* | armv7) XUI_ARCH="armv7" ;;
armv6* | armv6) XUI_ARCH="armv6" ;;
armv5* | armv5) XUI_ARCH="armv5" ;;
s390x) echo 's390x' ;;
*) XUI_ARCH="amd64" ;;
esac
wget https://github.com/MHSanaei/3x-ui/releases/latest/download/x-ui-linux-${XUI_ARCH}.tar.gz- Once the compressed package is downloaded, execute the following commands to install or upgrade x-ui:
ARCH=$(uname -m)
case "${ARCH}" in
x86_64 | x64 | amd64) XUI_ARCH="amd64" ;;
i*86 | x86) XUI_ARCH="386" ;;
armv8* | armv8 | arm64 | aarch64) XUI_ARCH="arm64" ;;
armv7* | armv7) XUI_ARCH="armv7" ;;
armv6* | armv6) XUI_ARCH="armv6" ;;
armv5* | armv5) XUI_ARCH="armv5" ;;
s390x) echo 's390x' ;;
*) XUI_ARCH="amd64" ;;
esac
cd /root/
rm -rf x-ui/ /usr/local/x-ui/ /usr/bin/x-ui
tar zxvf x-ui-linux-${XUI_ARCH}.tar.gz
chmod +x x-ui/x-ui x-ui/bin/xray-linux-* x-ui/x-ui.sh
cp x-ui/x-ui.sh /usr/bin/x-ui
cp -f x-ui/x-ui.service /etc/systemd/system/
mv x-ui/ /usr/local/
systemctl daemon-reload
systemctl enable x-ui
systemctl restart x-uiClick for Docker details
-
Install Docker:
bash <(curl -sSL https://get.docker.com) -
Clone the Project Repository:
git clone https://github.com/MHSanaei/3x-ui.git cd 3x-ui -
Start the Service:
docker compose up -d
OR
docker run -itd \ -e XRAY_VMESS_AEAD_FORCED=false \ -v $PWD/db/:/etc/x-ui/ \ -v $PWD/cert/:/root/cert/ \ --network=host \ --restart=unless-stopped \ --name 3x-ui \ ghcr.io/mhsanaei/3x-ui:latest
-
Update to the Latest Version:
cd 3x-ui docker compose down docker compose pull 3x-ui docker compose up -d -
Remove 3x-ui from Docker:
docker stop 3x-ui docker rm 3x-ui cd -- rm -r 3x-ui
- Ubuntu 20.04+
- Debian 11+
- CentOS 8+
- Fedora 36+
- Arch Linux
- Parch Linux
- Manjaro
- Armbian
- AlmaLinux 9+
- Rocky Linux 9+
- Oracle Linux 8+
- OpenSUSE Tubleweed
Click for Supported Architectures and devices details
Our platform offers compatibility with a diverse range of architectures and devices, ensuring flexibility across various computing environments. The following are key architectures that we support:
-
amd64: This prevalent architecture is the standard for personal computers and servers, accommodating most modern operating systems seamlessly.
-
x86 / i386: Widely adopted in desktop and laptop computers, this architecture enjoys broad support from numerous operating systems and applications, including but not limited to Windows, macOS, and Linux systems.
-
armv8 / arm64 / aarch64: Tailored for contemporary mobile and embedded devices, such as smartphones and tablets, this architecture is exemplified by devices like Raspberry Pi 4, Raspberry Pi 3, Raspberry Pi Zero 2/Zero 2 W, Orange Pi 3 LTS, and more.
-
armv7 / arm / arm32: Serving as the architecture for older mobile and embedded devices, it remains widely utilized in devices like Orange Pi Zero LTS, Orange Pi PC Plus, Raspberry Pi 2, among others.
-
armv6 / arm / arm32: Geared towards very old embedded devices, this architecture, while less prevalent, is still in use. Devices such as Raspberry Pi 1, Raspberry Pi Zero/Zero W, rely on this architecture.
-
armv5 / arm / arm32: An older architecture primarily associated with early embedded systems, it is less common today but may still be found in legacy devices like early Raspberry Pi versions and some older smartphones.
-
s390x: This architecture is commonly used in IBM mainframe computers and offers high performance and reliability for enterprise workloads.
- English
- Farsi
- Chinese
- Russian
- Vietnamese
- Spanish
- Indonesian
- Ukrainian
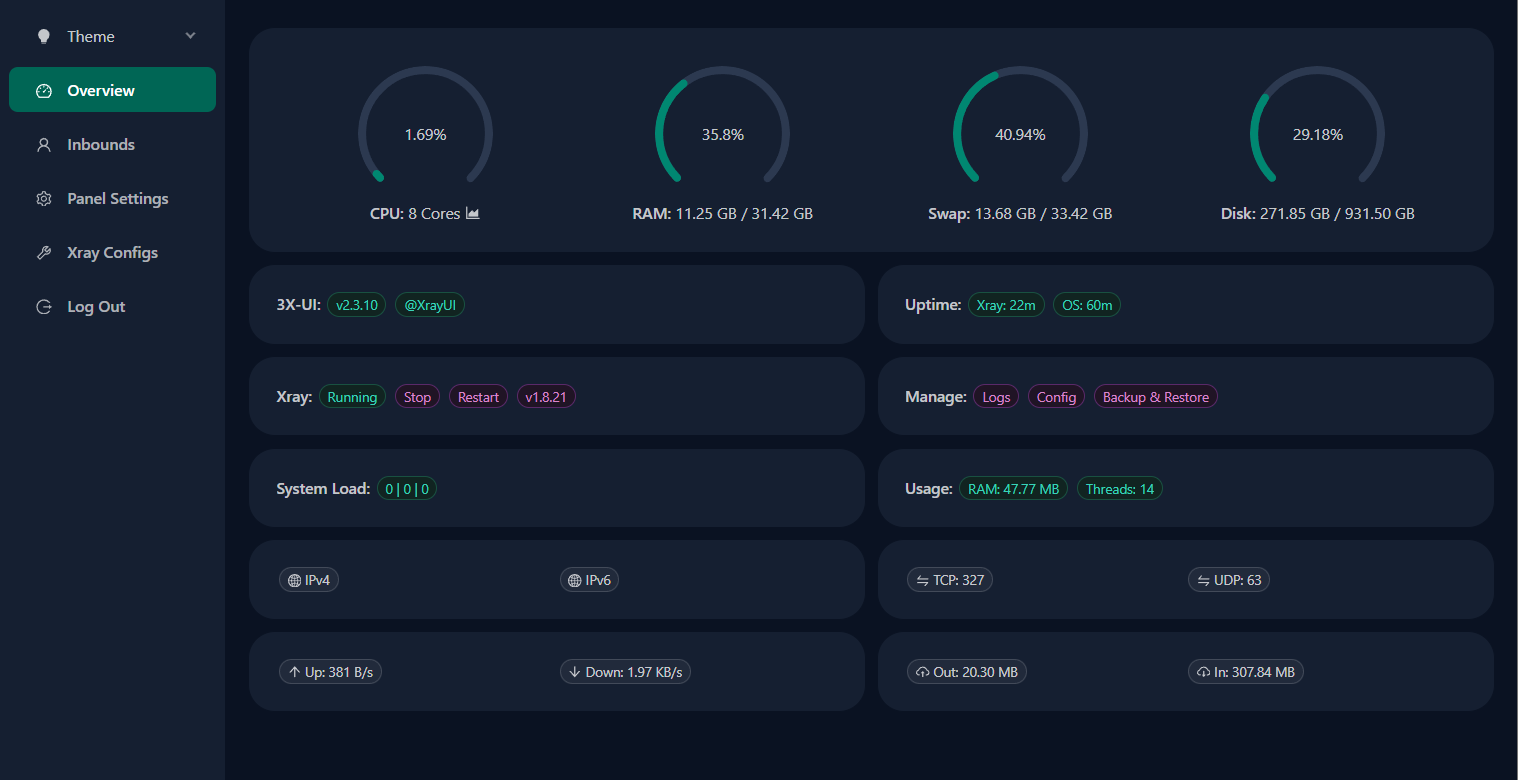
- System Status Monitoring
- Search within all inbounds and clients
- Dark/Light theme
- Supports multi-user and multi-protocol
- Supports protocols, including VMess, VLESS, Trojan, Shadowsocks, Dokodemo-door, Socks, HTTP, wireguard
- Supports XTLS native Protocols, including RPRX-Direct, Vision, REALITY
- Traffic statistics, traffic limit, expiration time limit
- Customizable Xray configuration templates
- Supports HTTPS access panel (self-provided domain name + SSL certificate)
- Supports One-Click SSL certificate application and automatic renewal
- For more advanced configuration items, please refer to the panel
- Fixes API routes (user setting will be created with API)
- Supports changing configs by different items provided in the panel.
- Supports export/import database from the panel
Click for default settings details
These will be generated randomly if you skip modifying them.
- Port: the default port for panel is
2053
You can conveniently perform database Backups and Restores directly from the panel.
- Database Path:
/etc/x-ui/x-ui.db
-
Reset Web Base Path:
- Open your terminal.
- Run the
x-uicommand. - Select the option to
Reset Web Base Path.
-
Generate or Customize Path:
- The path will be randomly generated, or you can enter a custom path.
-
View Current Settings:
- To view your current settings, use the
x-ui settingscommand in the terminal orView Current Settingsinx-ui
- To view your current settings, use the
- For enhanced security, use a long, random word in your URL structure.
Examples:
http://ip:port/*webbasepath*/panelhttp://domain:port/*webbasepath*/panel
Click for WARP configuration details
For versions v2.1.0 and later:
WARP is built-in, and no additional installation is required. Simply turn on the necessary configuration in the panel.
For versions before v2.1.0:
-
Run the
x-uicommand in the terminal, then chooseWARP Management. -
You will see the following options:
- Account Type (free, plus, team): Choose the appropriate account type.
- Enable/Disable WireProxy: Toggle WireProxy on or off.
- Uninstall WARP: Remove the WARP application.
-
Configure the settings as needed in the panel.
Click for IP limit details
Note: IP Limit won't work correctly when using IP Tunnel.
- For versions up to
v1.6.1:- The IP limit is built-in to the panel
For versions v1.7.0 and newer:
To enable the IP Limit functionality, you need to install fail2ban and its required files by following these steps:
-
Run the
x-uicommand in the terminal, then chooseIP Limit Management. -
You will see the following options:
- Change Ban Duration: Adjust the duration of bans.
- Unban Everyone: Lift all current bans.
- Check Logs: Review the logs.
- Fail2ban Status: Check the status of
fail2ban. - Restart Fail2ban: Restart the
fail2banservice. - Uninstall Fail2ban: Uninstall Fail2ban with configuration.
-
Add a path for the access log on the panel by setting
Xray Configs/log/Access logto./access.logthen save and restart xray.
-
For versions before
v2.1.3:-
You need to set the access log path manually in your Xray configuration:
"log": { "access": "./access.log", "dnsLog": false, "loglevel": "warning" },
-
-
For versions
v2.1.3and newer:- There is an option for configuring
access.logdirectly from the panel.
- There is an option for configuring
Click for Telegram bot details
The web panel supports daily traffic, panel login, database backup, system status, client info, and other notification and functions through the Telegram Bot. To use the bot, you need to set the bot-related parameters in the panel, including:
- Telegram Token
- Admin Chat ID(s)
- Notification Time (in cron syntax)
- Expiration Date Notification
- Traffic Cap Notification
- Database Backup
- CPU Load Notification
Reference syntax:
30 \* \* \* \* \*- Notify at the 30s of each point0 \*/10 \* \* \* \*- Notify at the first second of each 10 minutes@hourly- Hourly notification@daily- Daily notification (00:00 in the morning)@weekly- weekly notification@every 8h- Notify every 8 hours
- Report periodic
- Login notification
- CPU threshold notification
- Threshold for Expiration time and Traffic to report in advance
- Support client report menu if client's telegram username added to the user's configurations
- Support telegram traffic report searched with UUID (VMESS/VLESS) or Password (TROJAN) - anonymously
- Menu based bot
- Search client by email ( only admin )
- Check all inbounds
- Check server status
- Check depleted users
- Receive backup by request and in periodic reports
- Multi language bot
-
Start Botfather in your Telegram account:
-
Create a new Bot using /newbot command: It will ask you 2 questions, A name and a username for your bot. Note that the username has to end with the word "bot".
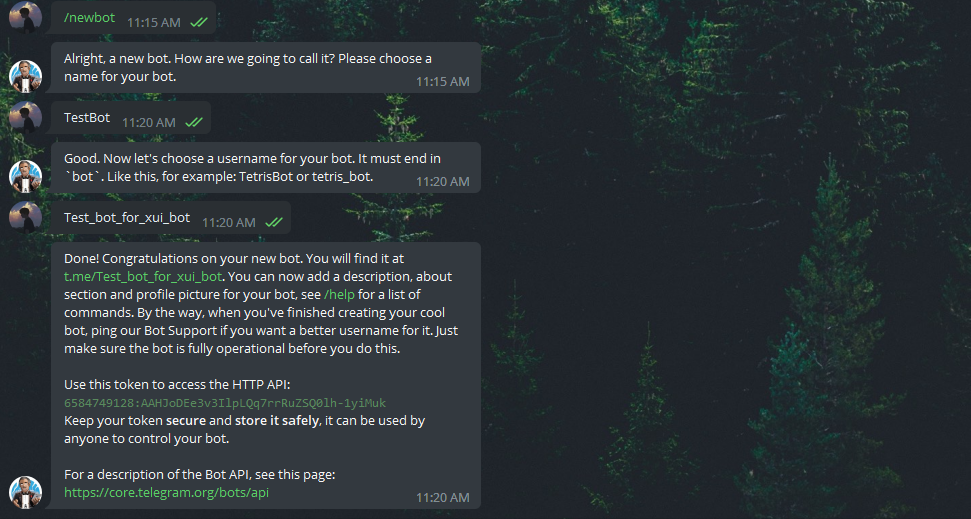
-
Start the bot you've just created. You can find the link to your bot here.
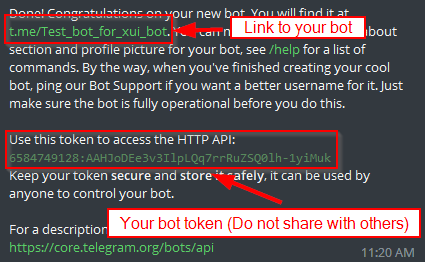
-
Enter your panel and config Telegram bot settings like below:
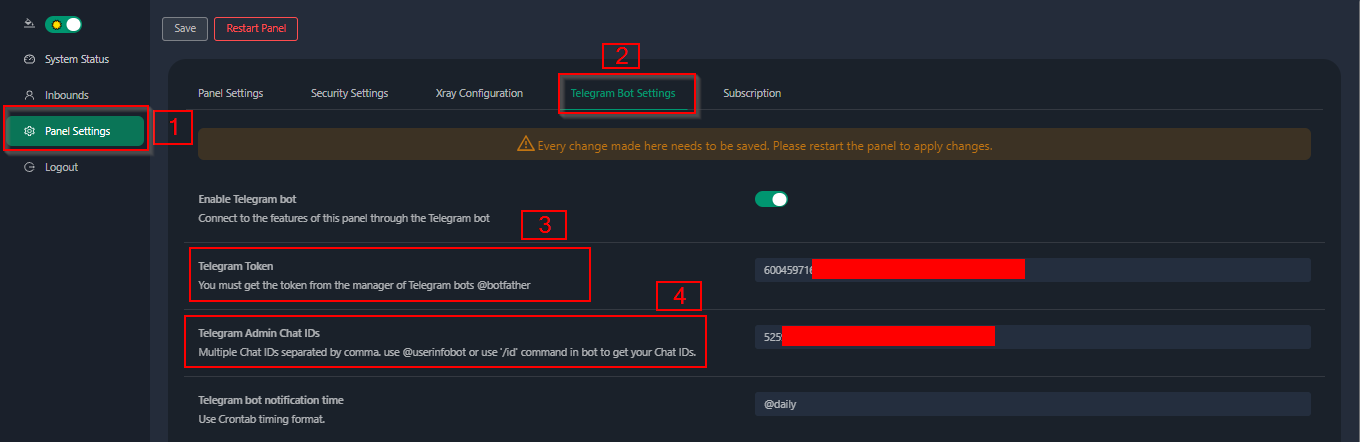
Enter your bot token in input field number 3. Enter the user ID in input field number 4. The Telegram accounts with this id will be the bot admin. (You can enter more than one, Just separate them with ,)
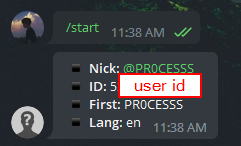
- How to get Telegram user ID? Use this bot, Start the bot and it will give you the Telegram user ID.
Click for API routes details
/loginwithPOSTuser data:{username: '', password: ''}for login/panel/api/inboundsbase for following actions:
| Method | Path | Action |
|---|---|---|
GET |
"/list" |
Get all inbounds |
GET |
"/get/:id" |
Get inbound with inbound.id |
GET |
"/getClientTraffics/:email" |
Get Client Traffics with email |
GET |
"/getClientTrafficsById/:id" |
Get client's traffic By ID |
GET |
"/createbackup" |
Telegram bot sends backup to admins |
POST |
"/add" |
Add inbound |
POST |
"/del/:id" |
Delete Inbound |
POST |
"/update/:id" |
Update Inbound |
POST |
"/clientIps/:email" |
Client Ip address |
POST |
"/clearClientIps/:email" |
Clear Client Ip address |
POST |
"/addClient" |
Add Client to inbound |
POST |
"/:id/delClient/:clientId" |
Delete Client by clientId* |
POST |
"/updateClient/:clientId" |
Update Client by clientId* |
POST |
"/:id/resetClientTraffic/:email" |
Reset Client's Traffic |
POST |
"/resetAllTraffics" |
Reset traffics of all inbounds |
POST |
"/resetAllClientTraffics/:id" |
Reset traffics of all clients in an inbound |
POST |
"/delDepletedClients/:id" |
Delete inbound depleted clients (-1: all) |
POST |
"/onlines" |
Get Online users ( list of emails ) |
*- The field clientId should be filled by:
-
client.idfor VMESS and VLESS -
client.passwordfor TROJAN -
client.emailfor Shadowsocks
Click for environment variables details
| Variable | Type | Default |
|---|---|---|
| XUI_LOG_LEVEL | "debug" | "info" | "warn" | "error" |
"info" |
| XUI_DEBUG | boolean |
false |
| XUI_BIN_FOLDER | string |
"bin" |
| XUI_DB_FOLDER | string |
"/etc/x-ui" |
| XUI_LOG_FOLDER | string |
"/var/log" |
Example:
XUI_BIN_FOLDER="bin" XUI_DB_FOLDER="/etc/x-ui" go build main.go- Iran v2ray rules (License: GPL-3.0): Enhanced v2ray/xray and v2ray/xray-clients routing rules with built-in Iranian domains and a focus on security and adblocking.
- Vietnam Adblock rules (License: GPL-3.0): A hosted domain hosted in Vietnam and blocklist with the most efficiency for Vietnamese.