This is a middleware for Gin framework.
It uses jwt-go to provide a jwt authentication middleware. It provides additional handler functions to provide the login api that will generate the token and an additional refresh handler that can be used to refresh tokens.
Simple HS256 JWT token brute force cracker. Effective only to crack JWT tokens with weak secrets. Recommendation: Use strong long secrets or RS256 tokens. See the jwt-cracker repository.
Download and install using go module:
export GO111MODULE=on
go get github.com/appleboy/gin-jwt/v2Import it in your code:
import "github.com/appleboy/gin-jwt/v2"Download and install without using go module:
go get github.com/appleboy/gin-jwtImport it in your code:
import "github.com/appleboy/gin-jwt"Please see the example file and you can use ExtractClaims to fetch user data.
package main
import (
"log"
"net/http"
"os"
"time"
jwt "github.com/appleboy/gin-jwt/v2"
"github.com/gin-gonic/gin"
)
type login struct {
Username string `form:"username" json:"username" binding:"required"`
Password string `form:"password" json:"password" binding:"required"`
}
var identityKey = "id"
func helloHandler(c *gin.Context) {
claims := jwt.ExtractClaims(c)
user, _ := c.Get(identityKey)
c.JSON(200, gin.H{
"userID": claims[identityKey],
"userName": user.(*User).UserName,
"text": "Hello World.",
})
}
// User demo
type User struct {
UserName string
FirstName string
LastName string
}
func main() {
port := os.Getenv("PORT")
r := gin.New()
r.Use(gin.Logger())
r.Use(gin.Recovery())
if port == "" {
port = "8000"
}
// the jwt middleware
authMiddleware, err := jwt.New(&jwt.GinJWTMiddleware{
Realm: "test zone",
Key: []byte("secret key"),
Timeout: time.Hour,
MaxRefresh: time.Hour,
IdentityKey: identityKey,
PayloadFunc: func(data interface{}) jwt.MapClaims {
if v, ok := data.(*User); ok {
return jwt.MapClaims{
identityKey: v.UserName,
}
}
return jwt.MapClaims{}
},
IdentityHandler: func(c *gin.Context) interface{} {
claims := jwt.ExtractClaims(c)
return &User{
UserName: claims[identityKey].(string),
}
},
Authenticator: func(c *gin.Context) (interface{}, error) {
var loginVals login
if err := c.ShouldBind(&loginVals); err != nil {
return "", jwt.ErrMissingLoginValues
}
userID := loginVals.Username
password := loginVals.Password
if (userID == "admin" && password == "admin") || (userID == "test" && password == "test") {
return &User{
UserName: userID,
LastName: "Bo-Yi",
FirstName: "Wu",
}, nil
}
return nil, jwt.ErrFailedAuthentication
},
Authorizator: func(data interface{}, c *gin.Context) bool {
if v, ok := data.(*User); ok && v.UserName == "admin" {
return true
}
return false
},
Unauthorized: func(c *gin.Context, code int, message string) {
c.JSON(code, gin.H{
"code": code,
"message": message,
})
},
// TokenLookup is a string in the form of "<source>:<name>" that is used
// to extract token from the request.
// Optional. Default value "header:Authorization".
// Possible values:
// - "header:<name>"
// - "query:<name>"
// - "cookie:<name>"
// - "param:<name>"
TokenLookup: "header: Authorization, query: token, cookie: jwt",
// TokenLookup: "query:token",
// TokenLookup: "cookie:token",
// TokenHeadName is a string in the header. Default value is "Bearer"
TokenHeadName: "Bearer",
// TimeFunc provides the current time. You can override it to use another time value. This is useful for testing or if your server uses a different time zone than your tokens.
TimeFunc: time.Now,
})
if err != nil {
log.Fatal("JWT Error:" + err.Error())
}
// When you use jwt.New(), the function is already automatically called for checking,
// which means you don't need to call it again.
errInit := authMiddleware.MiddlewareInit()
if errInit != nil {
log.Fatal("authMiddleware.MiddlewareInit() Error:" + errInit.Error())
}
r.POST("/login", authMiddleware.LoginHandler)
r.NoRoute(authMiddleware.MiddlewareFunc(), func(c *gin.Context) {
claims := jwt.ExtractClaims(c)
log.Printf("NoRoute claims: %#v\n", claims)
c.JSON(404, gin.H{"code": "PAGE_NOT_FOUND", "message": "Page not found"})
})
auth := r.Group("/auth")
// Refresh time can be longer than token timeout
auth.GET("/refresh_token", authMiddleware.RefreshHandler)
auth.Use(authMiddleware.MiddlewareFunc())
{
auth.GET("/hello", helloHandler)
}
if err := http.ListenAndServe(":"+port, r); err != nil {
log.Fatal(err)
}
}Please run _example/server.go file and listen 8000 port.
go run _example/server.goDownload and install httpie CLI HTTP client.
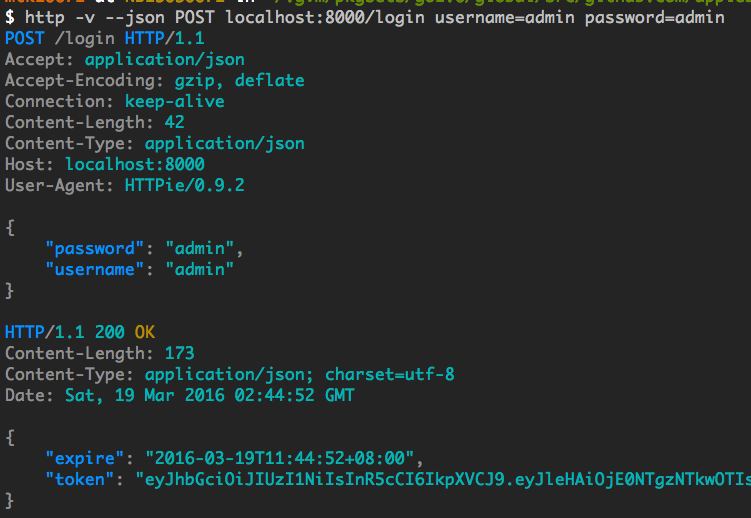
http -v --json POST localhost:8000/login username=admin password=adminOutput screenshot
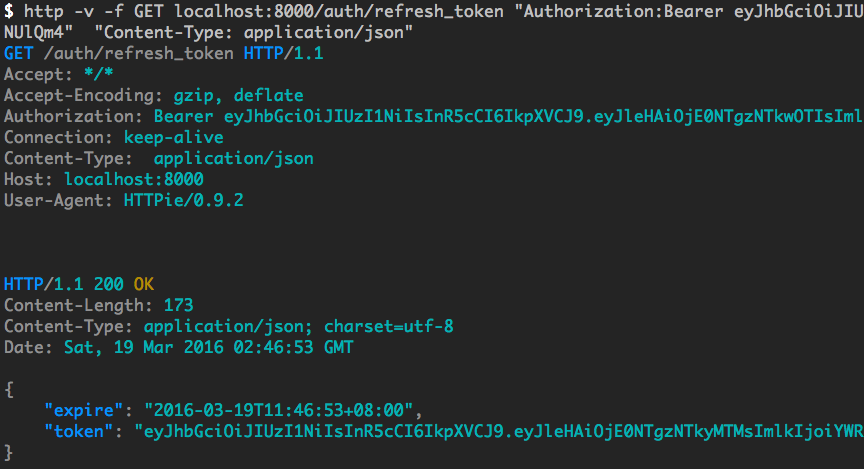
http -v -f GET localhost:8000/auth/refresh_token "Authorization:Bearer xxxxxxxxx" "Content-Type: application/json"Output screenshot
Please login as admin and password as admin
http -f GET localhost:8000/auth/hello "Authorization:Bearer xxxxxxxxx" "Content-Type: application/json"Response message 200 OK:
HTTP/1.1 200 OK
Content-Length: 24
Content-Type: application/json; charset=utf-8
Date: Sat, 19 Mar 2016 03:02:57 GMT
{
"text": "Hello World.",
"userID": "admin"
}Please login as test and password as test
http -f GET localhost:8000/auth/hello "Authorization:Bearer xxxxxxxxx" "Content-Type: application/json"Response message 403 Forbidden:
HTTP/1.1 403 Forbidden
Content-Length: 62
Content-Type: application/json; charset=utf-8
Date: Sat, 19 Mar 2016 03:05:40 GMT
Www-Authenticate: JWT realm=test zone
{
"code": 403,
"message": "You don't have permission to access."
}Use these options for setting the JWT in a cookie. See the Mozilla documentation for more information on these options.
SendCookie: true,
SecureCookie: false, //non HTTPS dev environments
CookieHTTPOnly: true, // JS can't modify
CookieDomain: "localhost:8080",
CookieName: "token", // default jwt
TokenLookup: "cookie:token",
CookieSameSite: http.SameSiteDefaultMode, //SameSiteDefaultMode, SameSiteLaxMode, SameSiteStrictMode, SameSiteNoneMode-
PROVIDED:
LoginHandlerThis is a provided function to be called on any login endpoint, which will trigger the flow described below.
-
REQUIRED:
AuthenticatorThis function should verify the user credentials given the gin context (i.e. password matches hashed password for a given user email, and any other authentication logic). Then the authenticator should return a struct or map that contains the user data that will be embedded in the jwt token. This might be something like an account id, role, is_verified, etc. After having successfully authenticated, the data returned from the authenticator is passed in as a parameter into thePayloadFunc, which is used to embed the user identifiers mentioned above into the jwt token. If an error is returned, theUnauthorizedfunction is used (explained below). -
OPTIONAL:
PayloadFuncThis function is called after having successfully authenticated (logged in). It should take whatever was returned from
Authenticatorand convert it intoMapClaims(i.e. map[string]interface{}). A typical use case of this function is for whenAuthenticatorreturns a struct which holds the user identifiers, and that struct needs to be converted into a map.MapClaimsshould include one element that is [IdentityKey(default is "identity"): some_user_identity]. The elements ofMapClaimsreturned inPayloadFuncwill be embedded within the jwt token (as token claims). When users pass in their token on subsequent requests, you can get these claims back by usingExtractClaims. -
OPTIONAL:
LoginResponseAfter having successfully authenticated with
Authenticator, created the jwt token using the identifiers from map returned fromPayloadFunc, and set it as a cookie ifSendCookieis enabled, this function is called. It is used to handle any post-login logic. This might look something like using the gin context to return a JSON of the token back to the user.
-
PROVIDED:
MiddlewareFuncThis is gin middleware that should be used within any endpoints that require the jwt token to be present. This middleware will parse the request headers for the token if it exists, and check that the jwt token is valid (not expired, correct signature). Then it will call
IdentityHandlerfollowed byAuthorizator. IfAuthorizatorpasses and all of the previous token validity checks passed, the middleware will continue the request. If any of these checks fail, theUnauthorizedfunction is used (explained below). -
OPTIONAL:
IdentityHandlerThe default of this function is likely sufficient for your needs. The purpose of this function is to fetch the user identity from claims embedded within the jwt token, and pass this identity value to
Authorizator. This function assummes [IdentityKey: some_user_identity] is one of the attributes embedded within the claims of the jwt token (determined byPayloadFunc). -
OPTIONAL:
AuthorizatorGiven the user identity value (
dataparameter) and the gin context, this function should check if the user is authorized to be reaching this endpoint (on the endpoints where theMiddlewareFuncapplies). This function should likely useExtractClaimsto check if the user has the sufficient permissions to reach this endpoint, as opposed to hitting the database on every request. This function should return true if the user is authorized to continue through with the request, or false if they are not authorized (whereUnauthorizedwill be called).
-
PROVIDED:
LogoutHandlerThis is a provided function to be called on any logout endpoint, which will clear any cookies if
SendCookieis set, and then callLogoutResponse. -
OPTIONAL:
LogoutResponseThis should likely just return back to the user the http status code, if logout was successful or not.
-
PROVIDED:
RefreshHandler:This is a provided function to be called on any refresh token endpoint. If the token passed in is was issued within the
MaxRefreshTimetime frame, then this handler will create/set a new token similar to theLoginHandler, and pass this token intoRefreshResponse -
OPTIONAL:
RefreshResponse:This should likely return a JSON of the token back to the user, similar to
LoginResponse
-
OPTIONAL
Unauthorized:On any error logging in, authorizing the user, or when there was no token or a invalid token passed in with the request, the following will happen. The gin context will be aborted depending on
DisabledAbort, thenHTTPStatusMessageFuncis called which by default converts the error into a string. Finally theUnauthorizedfunction will be called. This function should likely return a JSON containing the http error code and error message to the user.