APKKiller is a method to bypass android application integrity and signature check. APKKiller uses JNI Reflection also using some trick and hack to bypass hidden API restrictions.
When an android application is loaded, it stores various information regarding current running Application like App Name, Package Name, Signature, APK Path, etc. You can't access those information normal way, but with Reflection you access, read and write new data to those internal classes & fields.
These informations are stored in a class like AppBindData, LoadedApk, ApplicationInfo, etc.
APKKiller changes data on those classes to spoof current application information such APK Path, APK Signatures, APK Installer Information, etc. APKKiller is not guaranteed to work on all apps/games, but it is guaranteed to bypass majorities of application security system.
- Get the target app original Signature using APKSignReader
- Change apk_signatures in
APKKiller.husing the resuslt of APKSignReader - Build the APKKiller Project to APK
- Decompile both APKKiller APK and Target APK
- Copy smali from
com/kuro(APKKiller smali) to the Target App smali - Copy libs from APKKiller APK to Target APK (Make sure only copy same ABIs as the Target App, for example if Target App has only armeabi-v7a, then you should only copy armeabi-v7a)
- Locate Target App entry point in the smali, you can do this by taking a look at
AndroidManifest.xml - Call
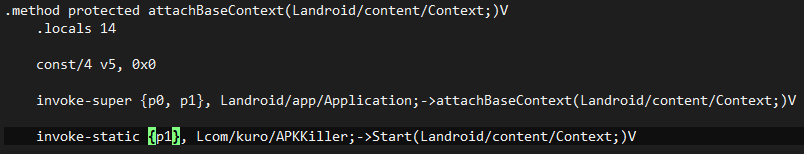
Startfunction on the target appattachBaseContext(Application) oronCreate(Activity) [Preferrably attachBaseContext]
For example:
attachBaseContext
onCreate
- Copy Target original APK file to
<decompile_target_app_dir>/assets/original.apk - Compile Target App and test it!