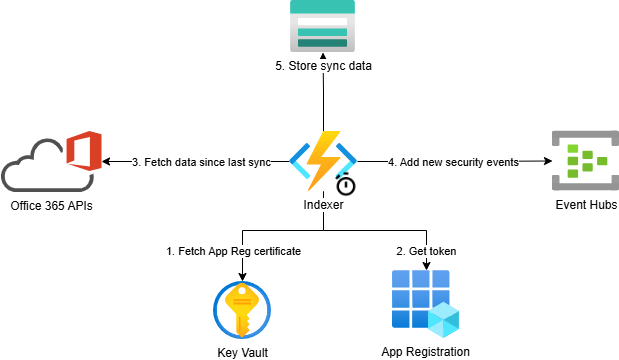
Fetch O365 audit logs and Exchange message traces and publish them to Event Hubs.
Audit logs are fetched from the Office 365 Management Activity API using a Function App, whereas Exchange message traces are fetched Using Office 365 Reporting web service.
This POC relies on the following services:
- Azure Functions: pulling data from data sources (APIs) every 5 minutes (configurable) and adding these events to Event Hubs
- Event Hubs: This is where all security events will be added. You can use a separate hub for each event type or share one event hub for all events.
- Blob storage: Persist the state of succcessful last data synchronizations to enable fetching new data only and be able to retry failed fetch operations.
- App registration: The Application which we will be using to access the reporting APIs of Office 365.
- Key Vault: Ehere we will store the PEM certificate to authenticate the app.
- Azure Monitor: We will rely on Application Insights and Log Analytics to observe the system, understand how the POC is behaving and locate potential issues.
You need an Azure subscription for deploying all project resources like Event Hubs, Azure Functions, and other backing resources.
You need to have enough permissions to:
- deploy resources like the Contributor role on the subscription or resource group)
- assign RBAC roles like the User Access Administrator or Role Based Access Control Administrator role
If you want to deploy the POC within a VNET, then please make sure that:
- You have access to the VNET so that you can deploy the Function App code. Alternatively, please ensure that a CI/CD pipeline is available for deploying the code of the Function App while using VNETs.
- You can download the npm dependencies defined in package-lock.json (directly from npmjs.org or via a proxy) so that you can package and deploy the Function App code.
You can specify a proxy to use for all data fetching requests (o365 audit logs + exchange message traces) using the environment variables APP_PROXY_URI and APP_PROXY_TOKEN (optional).
APP_PROXY_URI:
The expected format for APP_PROXY_URI is https://proxy:port.
APP_PROXY_TOKEN:
The expected format for APP_PROXY_TOKEN (optional) is the same type of content for the Authorization header.
For example, you can use Bearer xxxx or Basic <base64-encoded-credentials>.
Ensure that you have the following tools installed:
Use azd to provision resources:
azd auth login
azd provisionThis will create all required resources in Azure.
Create a PEM certificate and add it to the deployed instance of Azure Key Vault.
You can follow this guide for creating a certificate in Azure Key Vault.
Important
The Certificate must be in the PEM format
You can download a copy of this certificate in the CER format for the next step.
Important
Download the certificate in the CER format so that you can import it in the App Registration
The POC relies on an App registration to access the APIs of Office 365.
The App registration must have access to both Office 365 Management Activity API and Office 365 Reporting web service.
To do this, please create an App Registration on Entra ID by following this guide.
In addition to the permissions for Office 365 Management Activity API described in the guide above, you will also need to do the following steps to grant the App Registration access to the Office 365 Reporting web service:
- Update the
API Permissionsof the App Registratyion and assign it the roleReportingWebService.Read.All. To do this, you should go to Entra ID, then selectManage > App registrations, then click on your App Registration and selectManage > API Permissions, then click onAdd permission, select the tabAPIs my organization uses, locate and click onOffice 365 Exchange Online, and thenApplication permissions, and lastly selectReportingWebService.Read.All. - Assign the role
Security Readerto the App Registration. To do this, you should go to Entra ID, then selectRoles and administrators, then locate and click onSecurity Reader. Finally, click onAdd assignments, thenSelect member(s), and select the App Registration.
Once the App Registration is granted access to both O365 APIs, you will now need to update the App Registration to allow authentication using the PEM certificate that you created before.
Go to the App Registration, then click on the blade menu Certificates & secrets then click on Upload certificate, and finally import the downloaded CER certificate and save changes.
Now that the Function App and its dependencies are deployed, we need to update the App Settings of the Function App.
Please check the App Settings of the Function App and make sure all settings look good, you can do this by navigating to the Function App, then selecting the blade menu Settings, then clicking on Environment variables.
Make sure the field ENTRA_APP_CLIENT_ID is set to the Cliend ID of the App registration.
You will also need to update the value of ENTRA_APP_CLIENT_CERTIFICATE_NAME and set it to the name of the certificate which you have previously added to the App Registration.
Use azd deploy to deploy the code of Function App to Azure.
The deployment may take 1 or 2 minutes, but once that is done, the timer function gets triggered you should start getting new O365 audit events in Event Hubs.