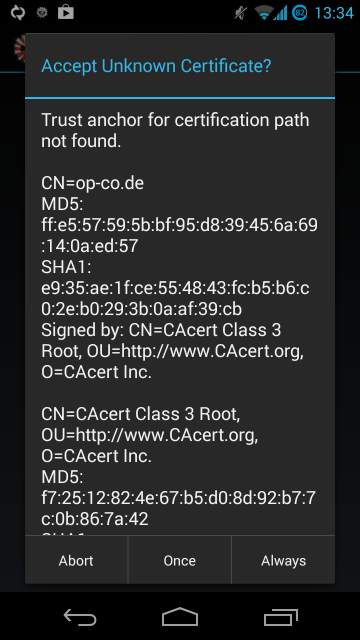
MemorizingTrustManager (MTM) is a project to enable smarter and more secure use of SSL on Android. If it encounters an unknown SSL certificate, it asks the user whether to accept the certificate once, permanently or to abort the connection. This is a step in preventing man-in-the-middle attacks by blindly accepting any invalid, self-signed and/or expired certificates.
MTM is aimed at providing seamless integration into your Android application, and the source code is available under the MIT license.
MemorizingTrustManager is in production use in the yaxim XMPP client. It is usable and easy to integrate, though it does not yet support hostname validation (the Java API makes it hard to integrate).
MTM is easy to integrate into your own application. Follow these steps or have
a look into the demo application in the example directory.
Download the MTM source from GitHub, or add it as a git submodule:
# plain download:
git clone https://github.com/ge0rg/MemorizingTrustManager
# submodule:
git submodule add https://github.com/ge0rg/MemorizingTrustManager
Then add a library project dependency to default.properties:
android.library.reference.1=MemorizingTrustManager
Edit your AndroidManifest.xml and add the MTM activity line right before the
end of your closing </application> tag.
...
<activity android:name="de.duenndns.ssl.MemorizingActivity" />
</application>
</manifest>
Hooking MemorizingTrustmanager in HTTPS connections:
// register MemorizingTrustManager for HTTPS
SSLContext sc = SSLContext.getInstance("TLS");
sc.init(null, MemorizingTrustManager.getInstanceList(this), new java.security.SecureRandom());
HttpsURLConnection.setDefaultSSLSocketFactory(sc.getSocketFactory());
Or, for aSmack you can use setCustomSSLContext():
org.jivesoftware.smack.ConnectionConfiguration connectionConfiguration = …
SSLContext sc = SSLContext.getInstance("TLS");
sc.init(null, MemorizingTrustManager.getInstanceList(application), new java.security.SecureRandom());
connectionConfiguration.setCustomSSLContext(sc);
MemorizingTrustManager is not the only one out there.
NetCipher is an Android library made by the Guardian Project to improve network security for mobile apps. It comes with a StrongTrustManager to do more thorough certificate checks, an independent Root CA store, and code to easily route your traffic through the Tor network using Orbot.
AndroidPinning is another Android library, written by Moxie Marlinspike to allow pinning of server certificates, improving security against government-scale MitM attacks. Use this if your app is made to communicate with a specific server!