- What is vxlang?
- Download
- Software Protector
- Software Code obfuscation and virtualization
- Virtualization Preview
- Precautions
- Option
- Deploying the full version
- Latest Version
- TODO
- Special Thanks
VXLANG is a project designed to prevent reverse-engineering behaviors such as static or dynamic analysis, file tampering, and unauthorized access to memory by attackers.
The vxlang project currently targets x86-64 system and .Net binaries, native binary files for the Microsoft Windows operating system, including executables with the ".exe" extension, dynamic link library files with the ".dll" extension, and kernel driver files with the ".sys" extension. (The types of target binaries supported by vxlang will be expanded in future updates).
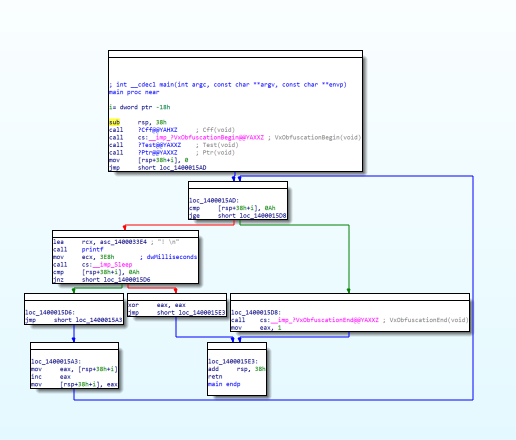
Executable compression refers to the process of compressing a file into an executable format. This type of compression helps to hide source code and file information, making access more difficult. Software protectors such as vxlang can provide increased security by tampering with files, obfuscating code, and performing dynamic analysis protection to prevent unauthorized access or tampering.
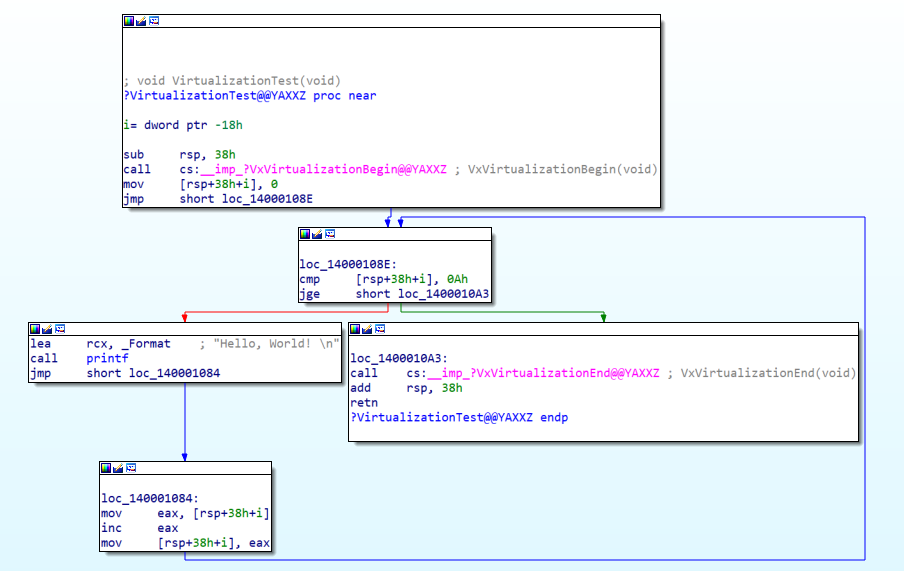
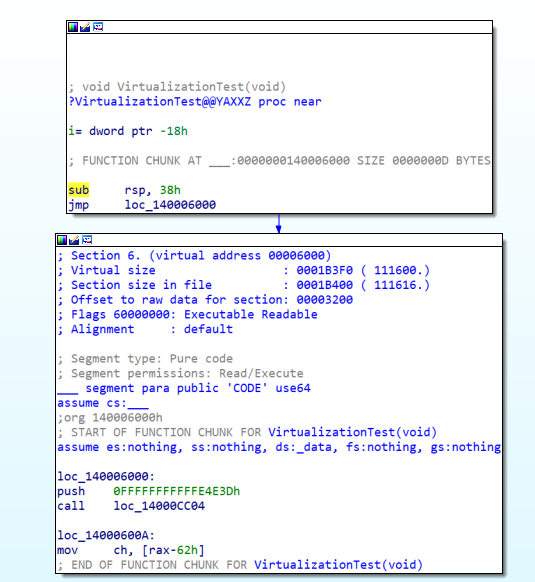
The software protector effectively blocks access to encryption and runtime states, however, it has a drawback in that it can expose the source code when the runtime state is dumped. To address this issue, code obfuscation is applied by adding dummy code or modulating the source code with similar code to the code exposed in the static or dynamic state. However, a more effective solution to protect the code is Code-Virtualization. Code virtualization represents real-world operational commands as virtual code, which can be executed on internal virtual machines. This approach provides a higher level of security compared to code obfuscation alone. vxlang offers these advanced obfuscation and virtualization services to ensure the protection of the code.
Optimization: Verify that VxVirtualizationBegin and VxVirtualizationEnd are in the same block.
If procedures are merged due to code optimization, problems may arise.switch-case: In the switch-case, when the branch movement is not an IMM value, it may be moved to the original position.Exception handling: Currently, the virtual CPU does not support exception handling.
--detect-debug: Checks to see if the process is debugging.--detect-patch: Checks if the process memory has been tampered with.--disable-packer: It doesn't use packers; it only virtualizes or obfuscates code.--opt-entry: Virtualize the program entry point.--add-on: Add an extension module (Add-on).
The beta version is free software, so if you request the full version via email, I will create a distribution file and respond to you.
- E-Mail: 0x999h@gmail.com
- The demo message box is removed.
- Support for specialized add-on modules.
- Support for virtual CPUs with specialized CPU contexts.
- Supports on/off for packer and engine code.
- Add-on development allows you to develop additional features.
- Anti-debugging and anti-tamper features are adjustable.
- Users can disable or control error messages.
- Free beta releases
- Fixed a bug that caused code obfuscation and virtualization to take a long time or crash.
- Added axion plugin.
- It plays an additional anti-tampering role, and will be updated.
- It is automatically applied in the demo version.
- You can include RAW data in your packing. This data can be requested and used by extension modules.
- A demo version is not available.
- Minor bug fixes
- Compiler and linker merged on a per-platform basis.
- Improved core structure.
- The link file and IL file have been removed.
0.9.7Packers and obfuscators are also modified on a per-platform basis.Obfuscation methods (e.g. control-flow-flattening, CFF) are added. Adds x86-64 assembler to the obfuscator, and updates it to make-
Befor
After
Task- Add ELF32/64 format for x86-64
- Add code obfuscation methods for x86-64
- Once the above steps are complete, add the ARM system for the ELF file format.
Thank you to everyone who helped with the development.