sgCheckup is a tool to scan your AWS Security Groups for a combination of open ports and attached Network Interfaces. The goal is to find anything listening on a port that you wouldn't consider safe. In addition to generating reports for security groups, sgCheckup can generate and run nmap to get specifics.
Security Groups are an important line of defense for your infrastructure, but as you make changes, it's easy to forget to revert some quick fix that was made to get something working. Having a view into what ports are open and what's listening can help you prioritize locking down access. Using nmap to pinpoint specifics as well as fingerprint the open ports further aides with context in locking down security groups.
- AWS Credentials (
~/.aws/,AWS_*environment variables, metadata server, etc.) - Docker
- If running from source, go version >= go1.15
- Download the latest release:
Linux:
curl -Lo sgCheckup https://github.com/goldfiglabs/sgCheckup/releases/latest/download/sgCheckup_linux
chmod a+x ./sgCheckup
OSX x86:
curl -Lo sgCheckup https://github.com/goldfiglabs/sgCheckup/releases/latest/download/sgCheckup_darwin_amd64
chmod a+x ./sgCheckup
OSX M1/arm:
curl -Lo sgCheckup https://github.com/goldfiglabs/sgCheckup/releases/latest/download/sgCheckup_darwin_arm64
chmod a+x ./sgCheckup
- Run from source:
git clone https://github.com/goldfiglabs/sgCheckup.git cd sgCheckup go run main.go
Run ./sgCheckup and view the reports generated in output/.
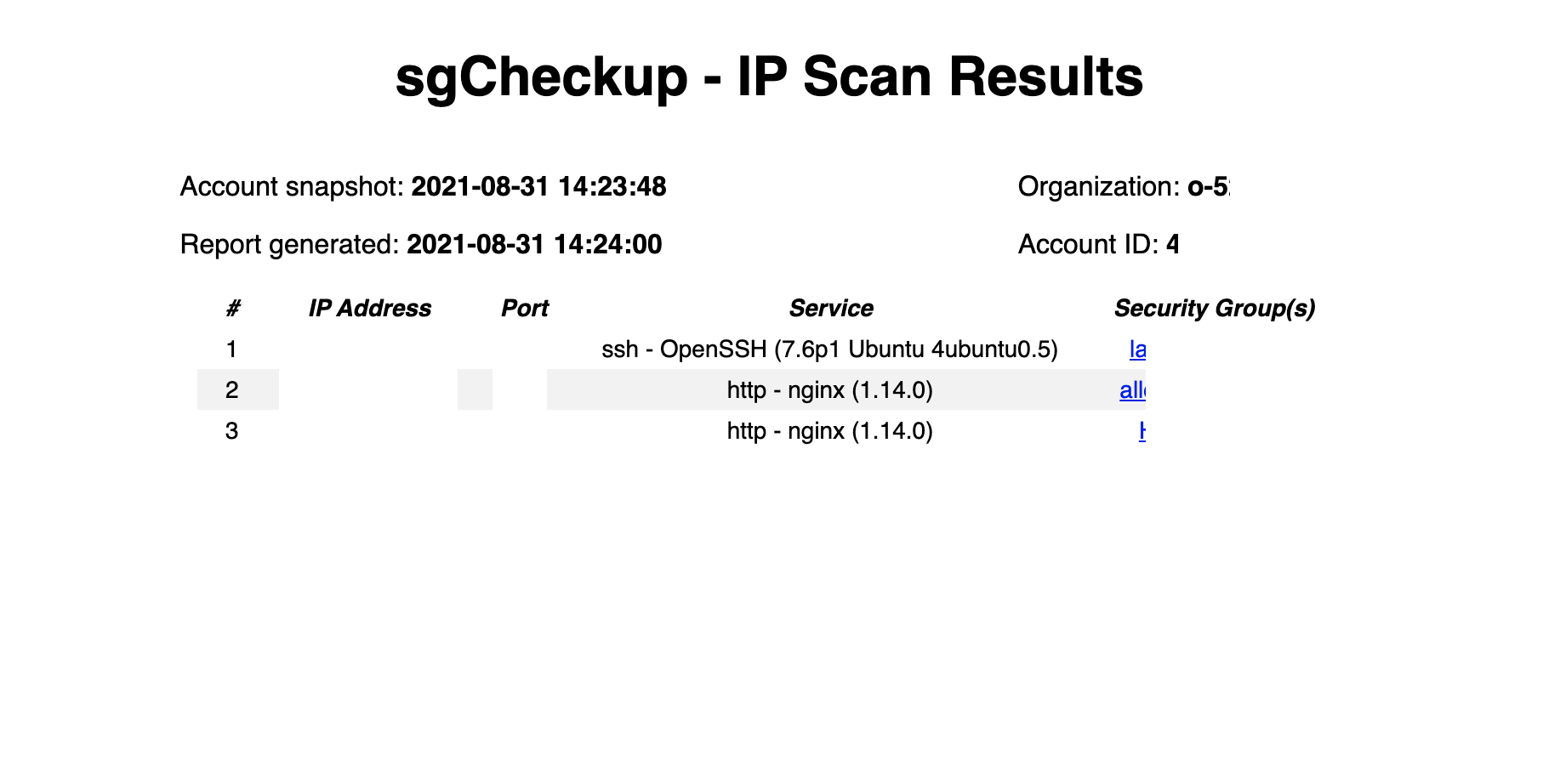
nmap results are in output/nmap/ with a summary cross-referencing security groups found in nmap.html:
sgCheckup uses goldfiglabs/introspector to snapshot the Security Groups and Network Interfaces from your AWS Account into a Postgres database. sgCheckup then runs SQL queries to look for Security Groups with open ports and attached Network Interfaces. This list is then used to configure running nmap against the targeted list of IPs and ports. The output of nmap is used to determine if a) anything is listening and b) what software is listening on open ports.
-
2 HTML and CSV reports are provided: one each organized by Security Group, and one each organized by IP/Port combination.
-
By default, sgCheckup considers ports 22, 80, and 443 to be open intentionally. You can use the flag
-safePorts <comma-separated port list>to override this behavior according to your own policies. Use--safe-ports ""to mark all ports unsafe. -
You can skip the nmap phase with
-skip-nmap. You will still get the report focused on Security Groups, but not the report based on open IP/Port combinations.
Copyright (c) 2021 Gold Fig Labs Inc.
This Source Code Form is subject to the terms of the Mozilla Public License, v.2.0. If a copy of the MPL was not distributed with this file, You can obtain one at http://mozilla.org/MPL/2.0/.