Auto applying tags for AWS resources for a better activity and costs tracking.
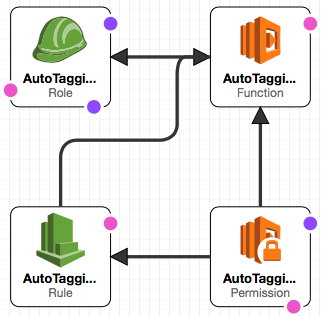
This project use a Lambda function to tag AWS resources by following this process:
- CloudTrail produces events
- These events are catch by an CloudWatch Event Rule
- The Rule trigger an Lambda function
- The function tags the resource depending on event source
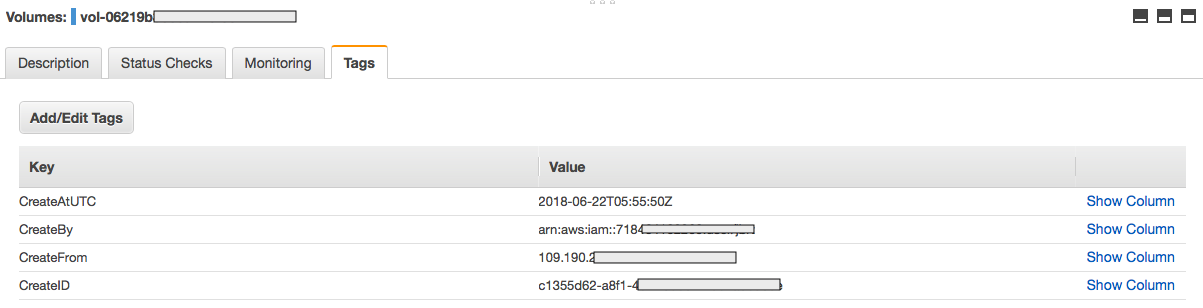
Here is an example of applied tags on a resource:
Current event supported:
- (EC2) RunInstances
- (EC2) CreateImage
- (EC2) CreateDhcpOptions
- (EC2) CreateNetworkAcl
- (EC2) CreateNetworkInterface
- (EC2) CreateRouteTable
- (EC2) CreateSecurityGroup
- (EC2) CreateSnapshot
- (EC2) CreateSubnet
- (EC2) CreateVolume
- (EC2) CreateVpc
- (EC2) CreateInternetGateway
- (DynamoDB) CreateTable
- (S3) CreateBucket
- (SQS) CreateQueue
Much more events will be added, see TODO section for more information. Work in progress.
Obviously, CloudTrail must be activated.
To deploy this solution you can use the CloudFormation template present in the "deployment" directory. This directory also contains a ZIP file containing the whole source code of this project.
If you want to delete this solution just destroy the CloudFormation stack.
You can also use Terraform to deploy this solution:
- Go in the deployment/terraform directory
- Set environment variables AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY with your credentials
- If it's the first time you use Terraform, do an
terraform initbefore go further - do an
terraform plan -var aws_region=YOUR_REGIONto preview the changes (the default region is eu-west-1) - do an
terraform apply -var aws_region=YOUR_REGIONto create the resources
If you want to delete this solution just do a terraform destroy.
The development is still ongoing. The next releases will add:
- support of more events and AWS services
- other deployment methods (Ansible probably)
- another stuff, who knows :-)
Pull requests are welcome.
To add the support of new events into the code, you have to do 5 things:
- Add the parsing of the new event in the right Python module (ex: events_ec2.py)
- Add the support of this new event in the factory module (factory.py)
- Update the CloudFormation template by adding this event in the CloudWatch Rule
- Write some unittests and put them into the file unittest-lambda.py (and add a sample in the directory event-samples)
- Update this page if needed :-)
This project is under GPL3 license.