Remote upload embedded payload from image using EOF to Discord users machines through cache.
Depending on how NodeJS and Discord's cache system works, you could potentially make this a full remote code execution exploit.
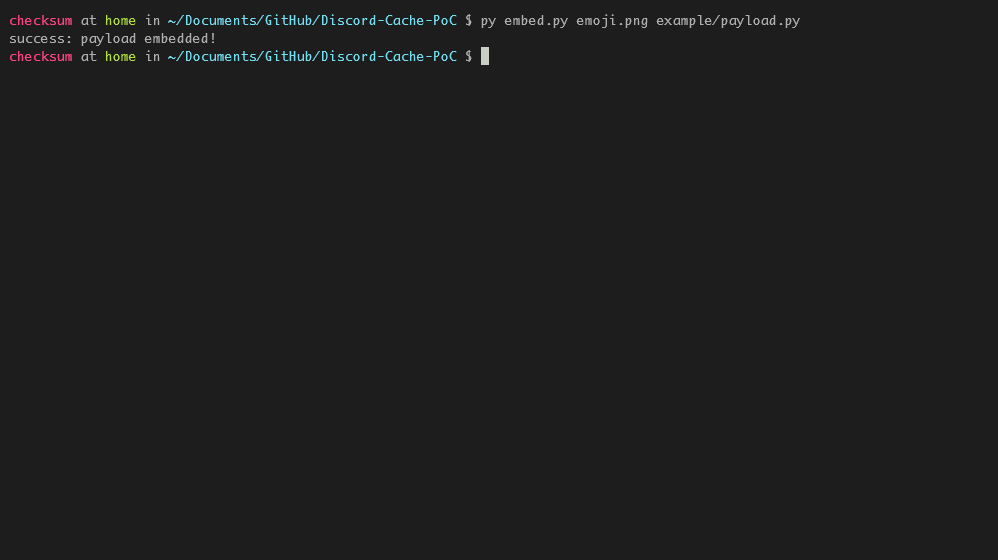
Embed payload to an image that's less than 256 kb of size:
python3 embed.py <image> <python payload>
For this proof-of-concept, my payload is:
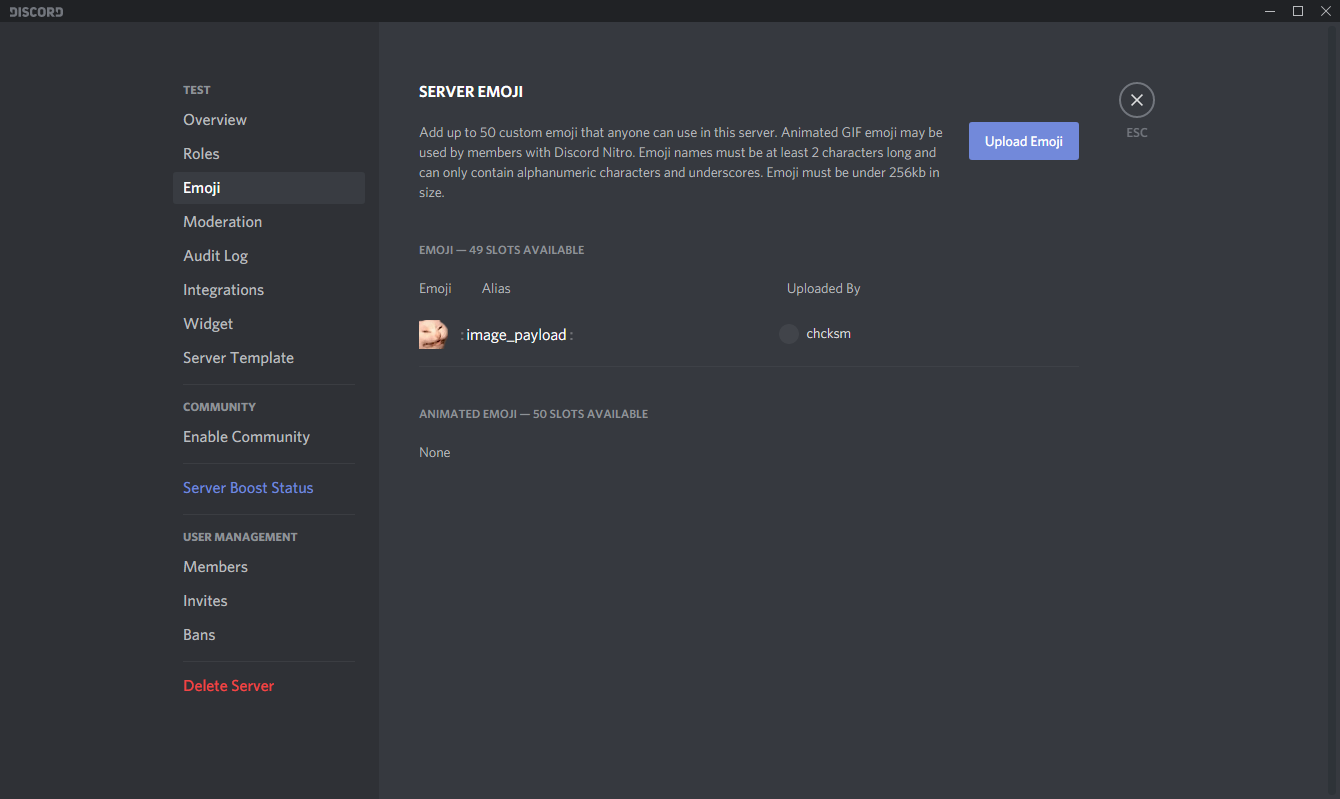
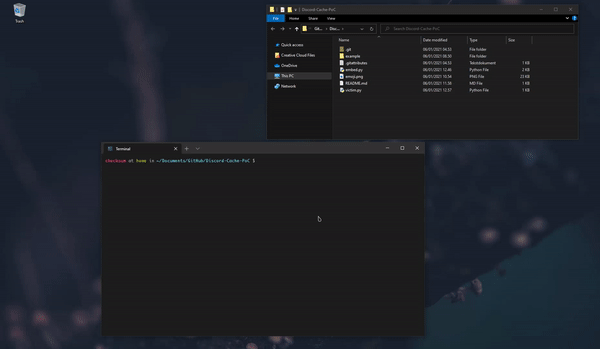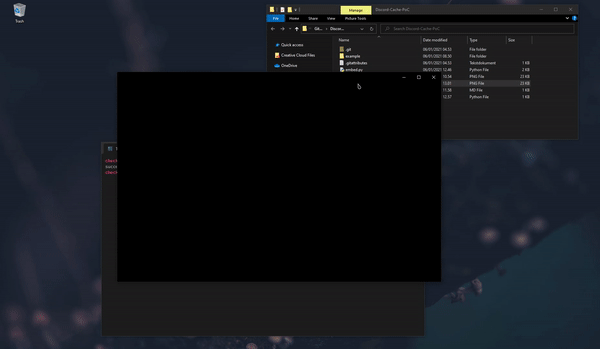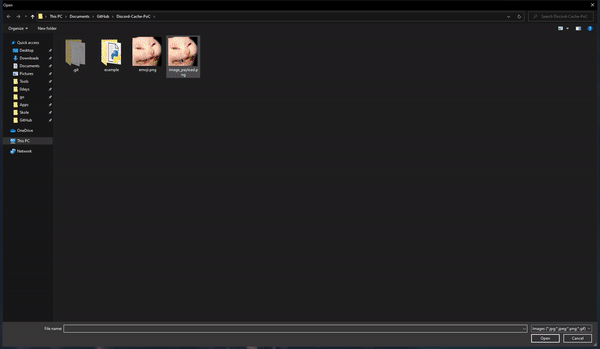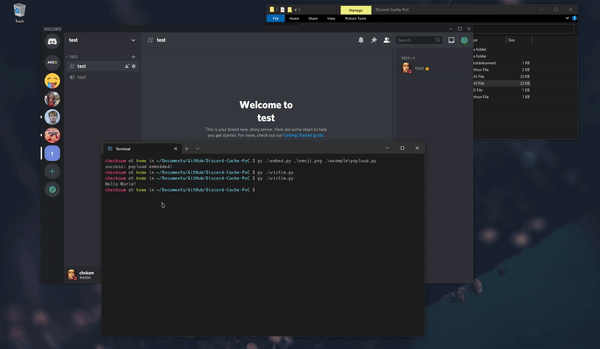
print('Hello World!')Upload the image with the embedded payload to a Discord server as an emoji.
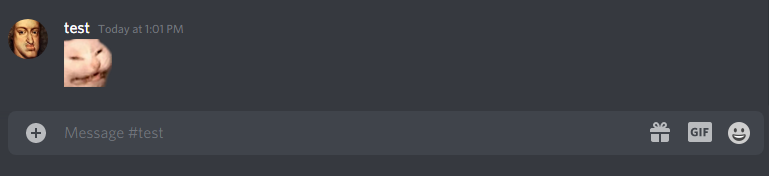
Send the emoji in a text channel. Any member that displays that emoji will automatically download it with the embedded payload to cache.
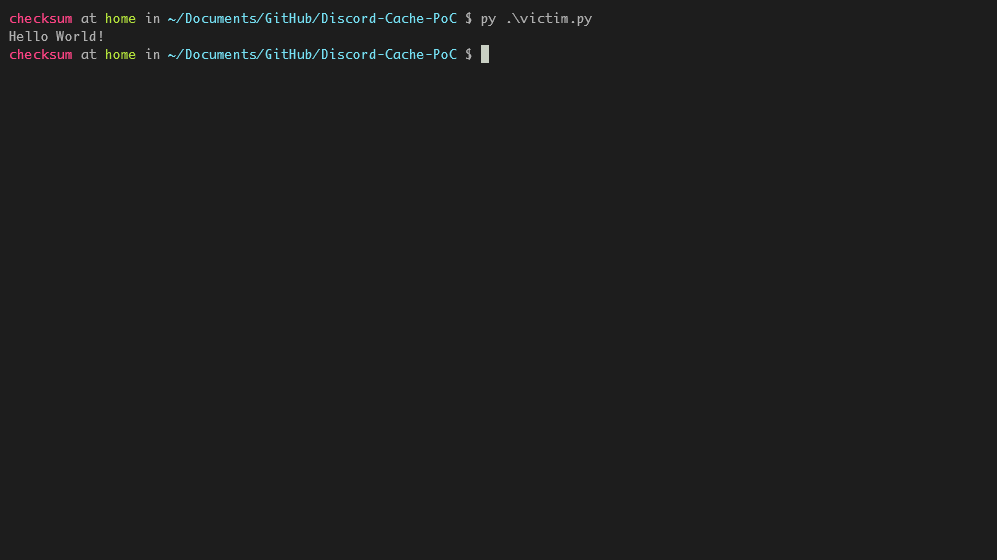
To actually execute the embedded payload, you'd have to make victim run a script like victim.py. The script will find and execute the embedded payload from the image in cache.
The same trick can be done with profile avatars.
cs:
Have fun triggering AVs :p