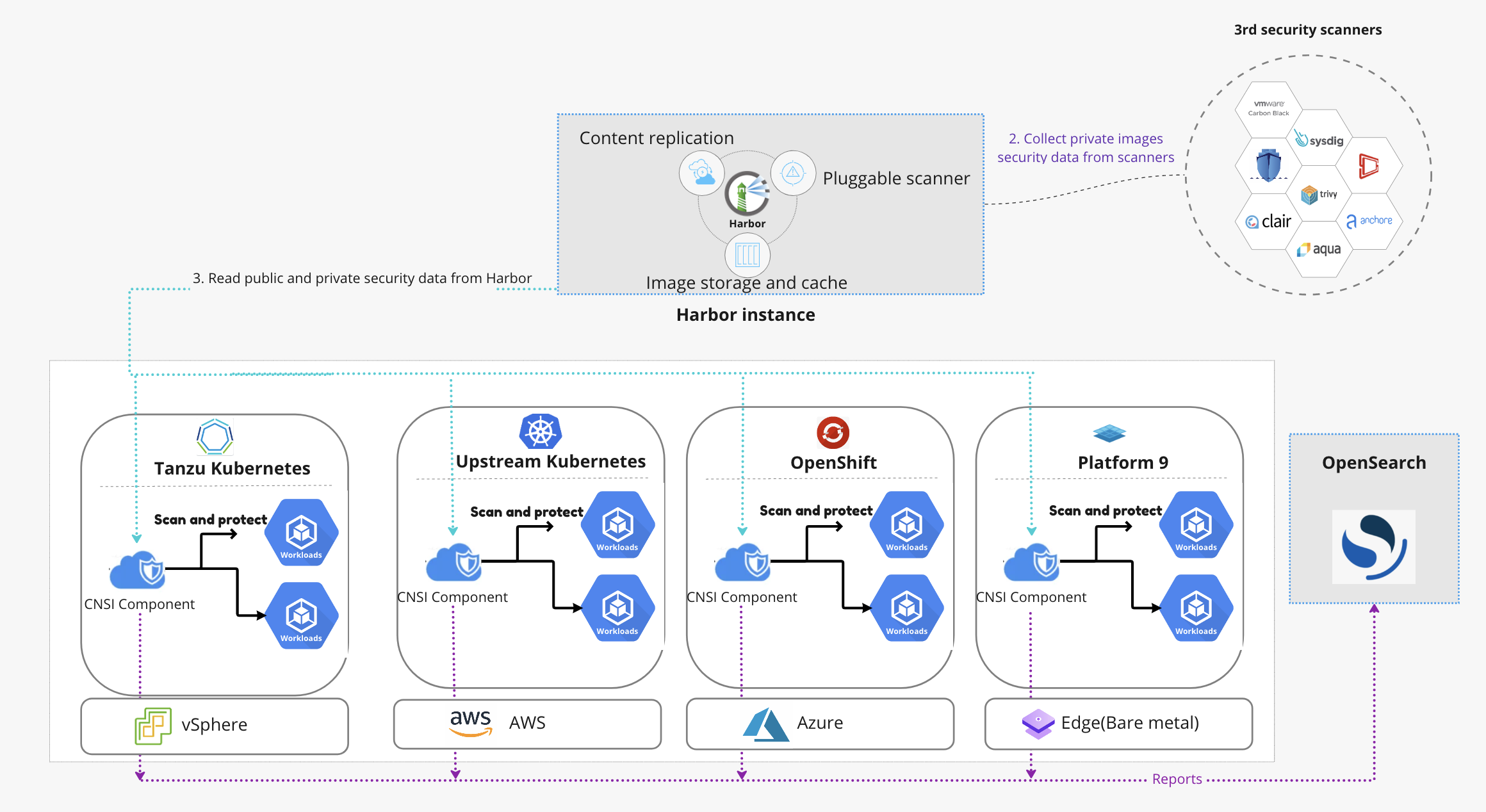
Cloud Native Security Inspector is an open source cloud native runtime security tool. It allows end users to assess the security posture of Kubernetes clusters at runtime. This project will add dynamic scanning giving Security Auditors greater awareness and control of running workloads.
- View overall security posture of applications in runtime
- Policy-based scanning management
- Revise baseline policies as needed and prevent redeploying workloads sourced from vulnerable images
- Quarantine non-secure workloads
- Review and filter the assessment reports
- Send the historical assessment reports to OpenSearch or ElasticSearch
Cloud Native Security Inspector consists of the following 3 components:
- The Controller Manager
- The Portal
- Scanners
In regard to scanners, currently we support 3 different kinds of scanners:
Harbor provides static analysis of vulnerabilities in images through the open source projects Trivy. In CNSI, this capability is used to perform dynamic security application testing (DAST).
Kubebench scanner mainly cares about the underlying Kubernetes cluster. It checks whether Kubernetes is deployed securely by running the checks documented in the CIS Kubernetes Benchmark.
The Risk scanner fetches the CVSS vectors from the image vulnerability report, then reports scored-risks it observed in the vector.
Video Demo - Demo for Cloud Native Security Inspector features
- Ubuntu Linux as the operating system of the installation machine
- Kubernetes 1.24
- Harbor 2.5.0+ is deployed and vulnerability scanning in Harbor is configured properly.
- kubectl and docker commands are ready to use.
Follow the instructions below to deploy the Cloud Native Security Inspector. There are two deployment options:
- Using pre-built images
- Building images from scratch
Using the following command to clone the source code:
$ git clone https://github.com/vmware-tanzu/cloud-native-security-inspector.gitUse the following commands to deploy the Cloud Native Security Inspector and other related components, and make sure the Kubernetes cluster has an Internet connection.
$ cd cloud-native-security-inspector
$ ./deploy.sh installInstead of using the pre-built images, users can also choose to build the images from source. Optionally, after the images are built, they can be pushed to a registry service. (either Harbor or DockerHub). Use the following command to clone the source code:
$ git clone https://github.com/vmware/cloud-native-security-inspector.gitBefore building the images, please ensure you have installed and configured the golang SDK correctly. To install the golang SDK, please familiarize yourself with the Golang documentation.
Use the following commands to compile the source code and build the docker images. After that, the images are generated and pushed to registry, then deployed.
$ cd cloud-native-security-inspector
$ ./deploy.sh install --build-sourceAfter the installation is completed either via Option 1 or Option 2, use the following command to see if all the components have been started successfully in Kubernetes.
# Verify the manager and portal
kubectl get deployment -n cnsi-system
NAME READY UP-TO-DATE AVAILABLE AGE
cloud-native-security-inspector-portal 1/1 1 1 93m
cnsi-controller-manager 1/1 1 1 93m
# Verify other resource of portal deployment
$ kubectl get serviceaccount -n cnsi-system cloud-native-security-inspector-portal-serviceaccount
NAME SECRETS AGE
cloud-native-security-inspector-portal-serviceaccount 0 166m
$ kubectl get clusterRole -n cnsi-system cloud-native-security-inspector-portal-role
NAME CREATED AT
cloud-native-security-inspector-portal-role 2022-08-10T06:33:01Z
$ kubectl get clusterrolebinding -n cnsi-system cloud-native-security-inspector-portal-rolebinding
NAME ROLE AGE
cloud-native-security-inspector-portal-rolebinding ClusterRole/cloud-native-security-inspector-portal-role 130m
$ kubectl get svc -n cnsi-system cloud-native-security-inspector-portal-service
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
cloud-native-security-inspector-portal-service NodePort 10.98.232.35 <none> 3800:32541/TCP 44h- Refer to the Tutorial for a quick guidance.
- Refer to the User Guide for more details on how to use Cloud Native Security Inspector.
To uninstall Cloud Native Security Inspector, use the following command:
$ ./deploy.sh uninstall For more details, please refer to the User Guide.
Email: narrows@vmware.com
Cloud Native Security Inspector is available under the Apache 2 license.