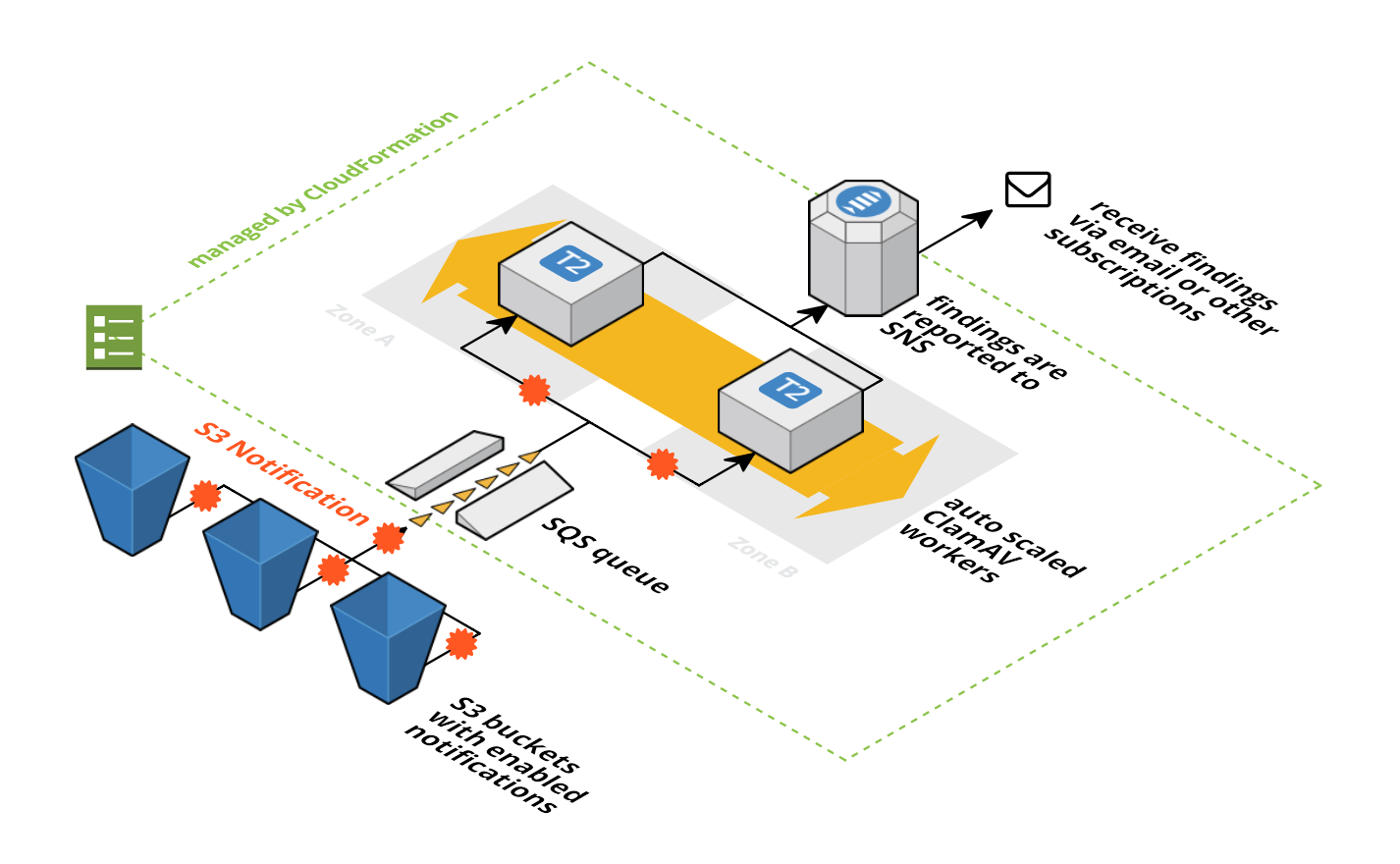
Antivirus for S3 buckets. You can connect as many buckets as you like by using S3 Event Notifications
- Uses ClamAV to scan newly added files on S3 buckets
- Automatically updates ClamAV db every 3 hours
- Scale EC2 instance workers to distribute workload
A picture is worth a thousand words:
- S3 VirusScan uses a SQS queue to decouple scan jobs from the ClamAV workers. Each S3 bucket can fire events to that SQS queue in case of new objects. This feature of S3 is called S3 Event Notifications.
- The SQS queue is consumed by a fleet of EC2 instances running in an Auto Scaling Group. If the number of outstanding scan jobs reaches a treshold a new ClamAV worker is automatically added. If the queue is mostly empty workers are removed.
- The ClamAV workers run a simple ruby script that executes the clamscan command. In the background the virus db is updated every three hours.
- If
clamscanfinds a virus the file is directly deleted (you can configure that) and a SNS notification is published.
Create a CloudFormation stack based on template.json.
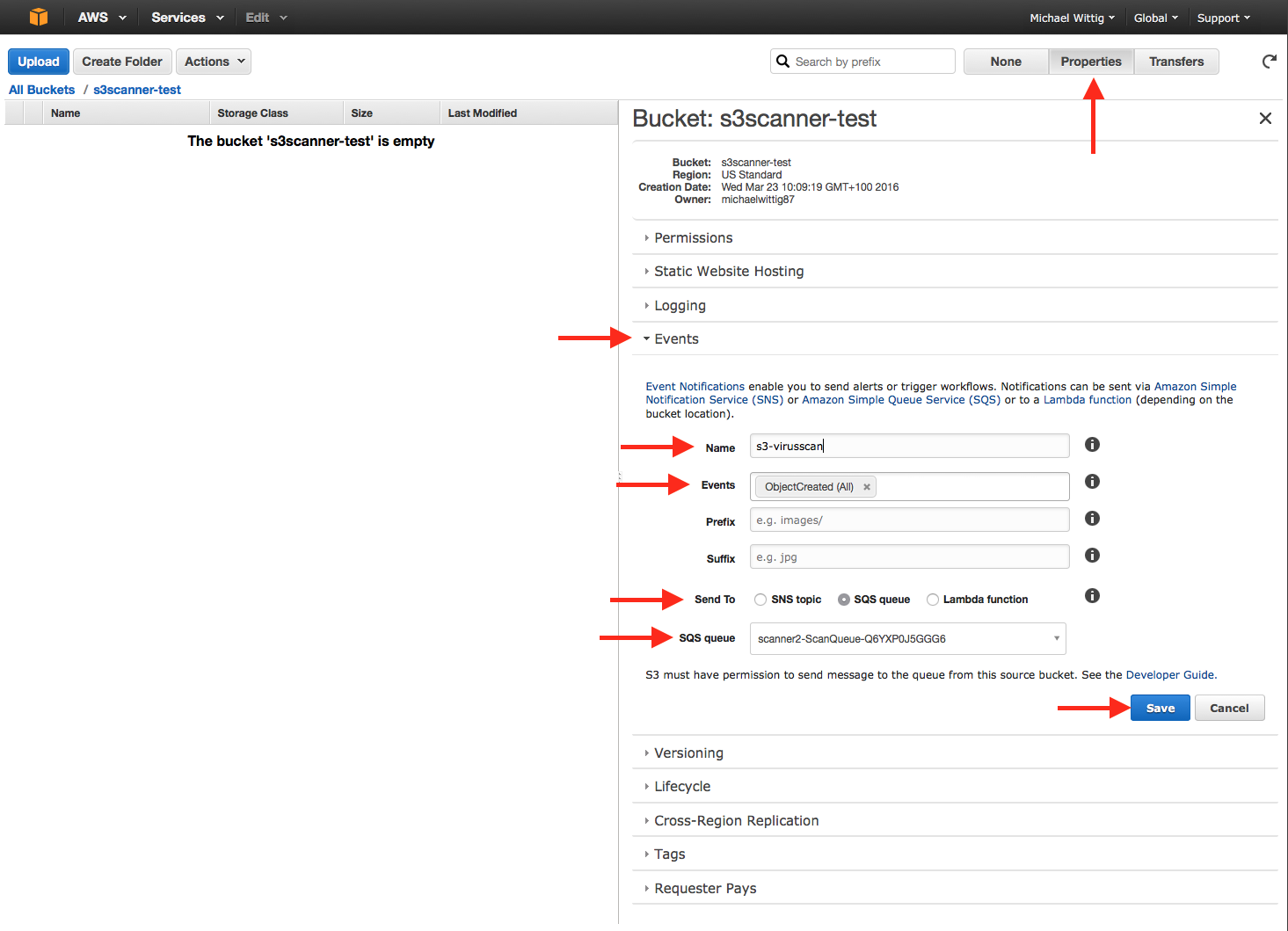
Configure the buckets you want to connect to S3 VirusScan as shown in the next figure:
Make sure you select the -ScanQueue- NOT the -ScanQueueDLQ-!
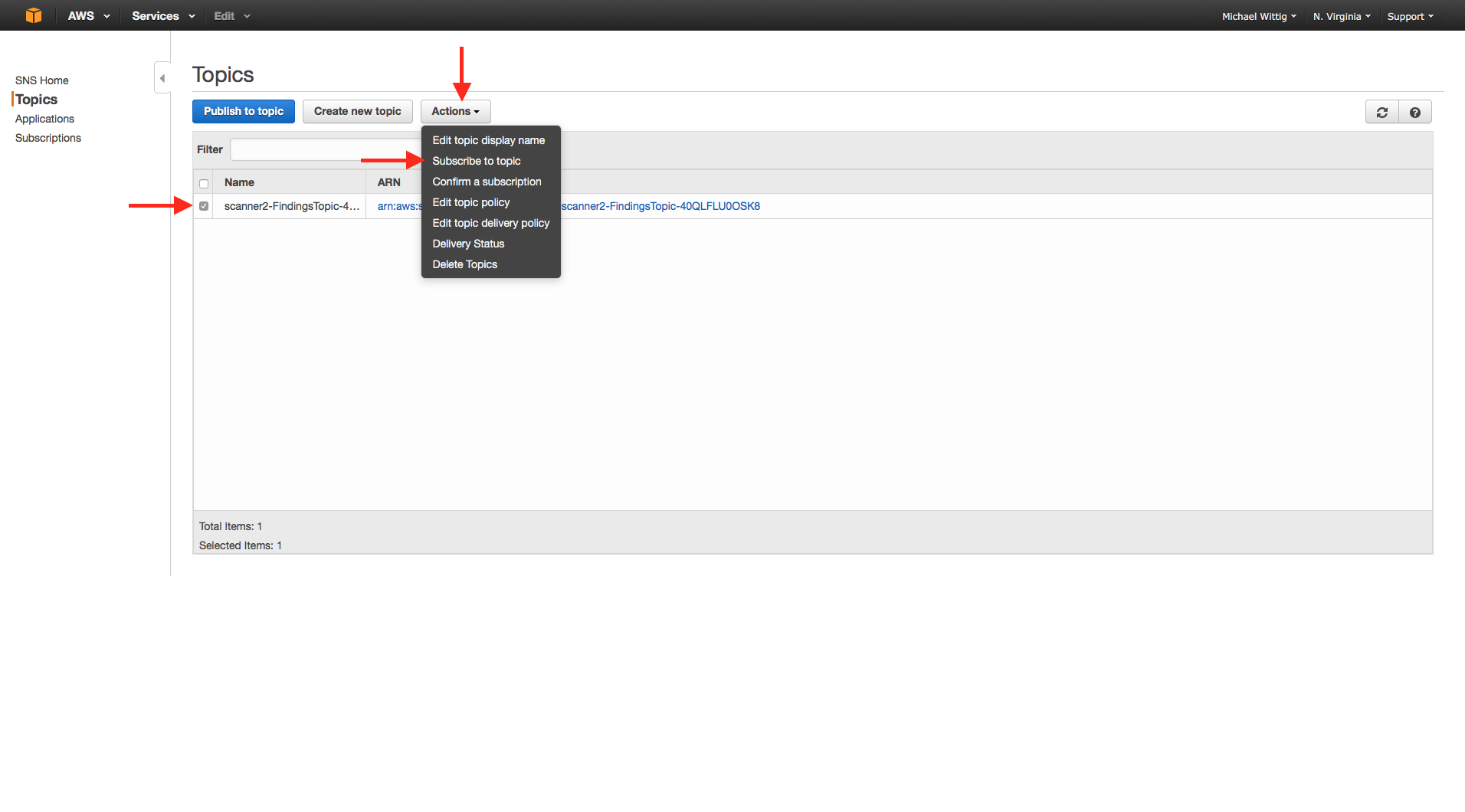
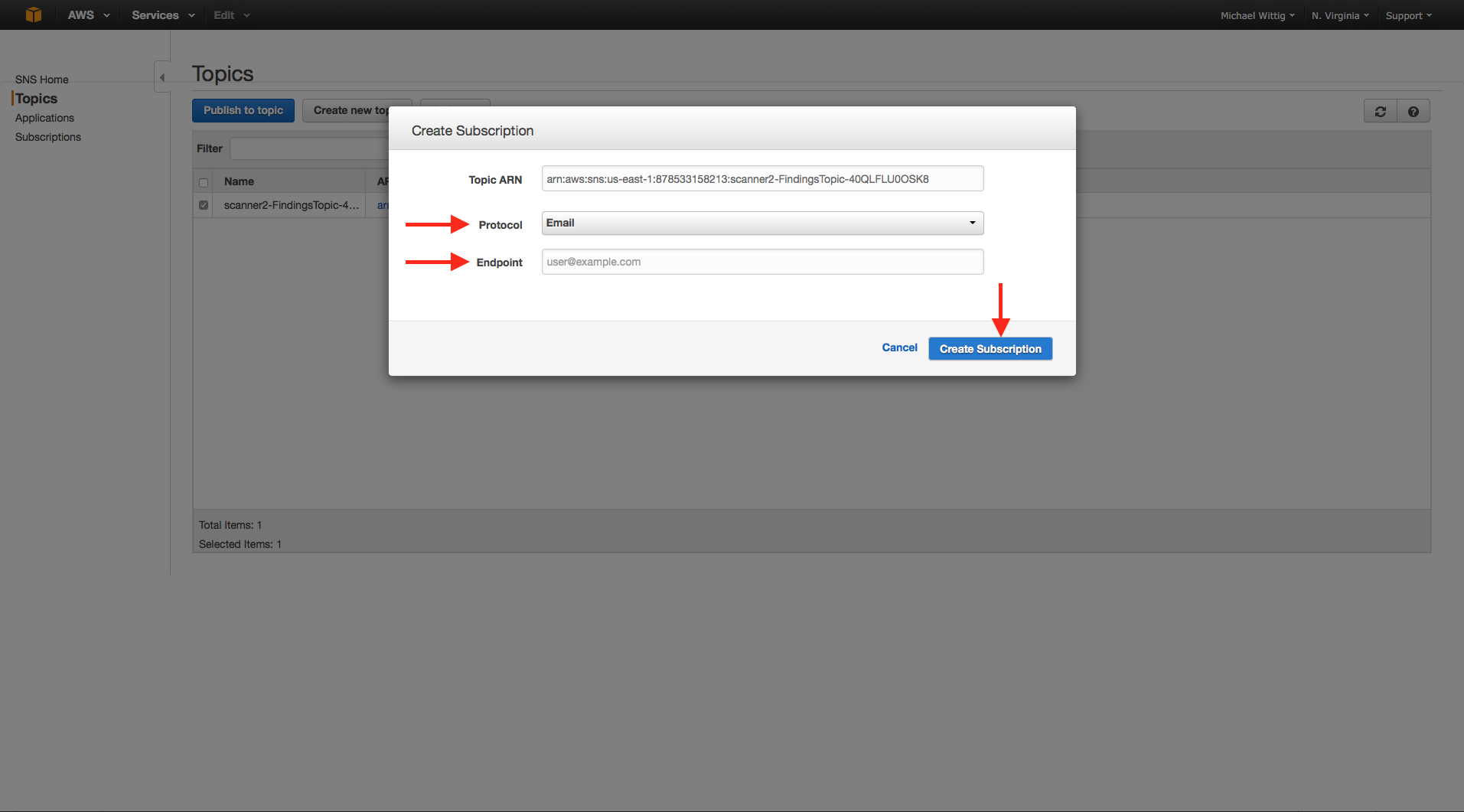
If you like to receive emails if a virus was found you must subscribe to the SNS topic as sown in the next two figures:
You will receive a confirmation email.
Create a EICAR Standard Anti-Virus Test File with the following content:
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
and upload that file to your S3 bucket.
- Support versioned S3 buckets
- An initial scan may also be useful. This could be implemented with a Lambda function that pushes every key to SQS.