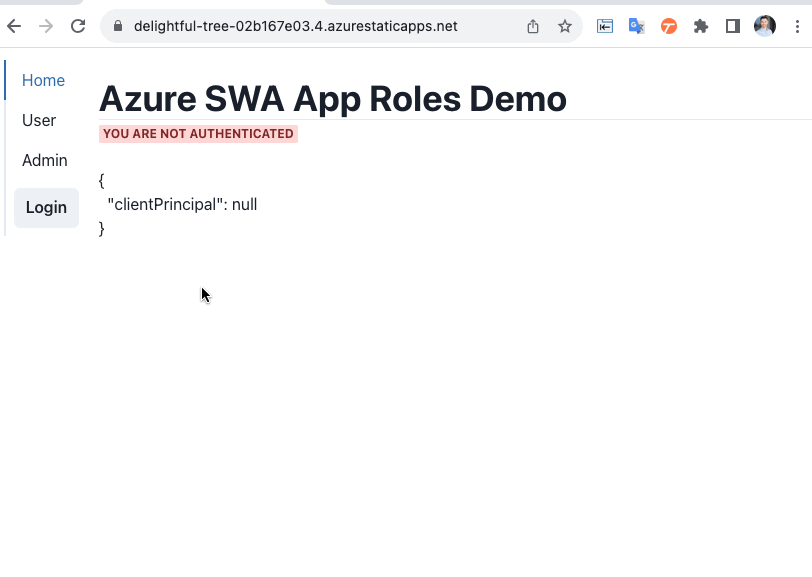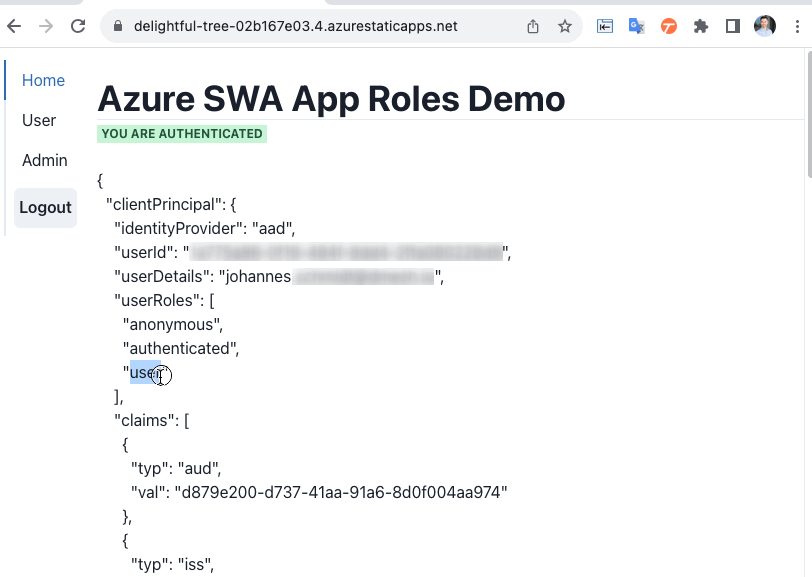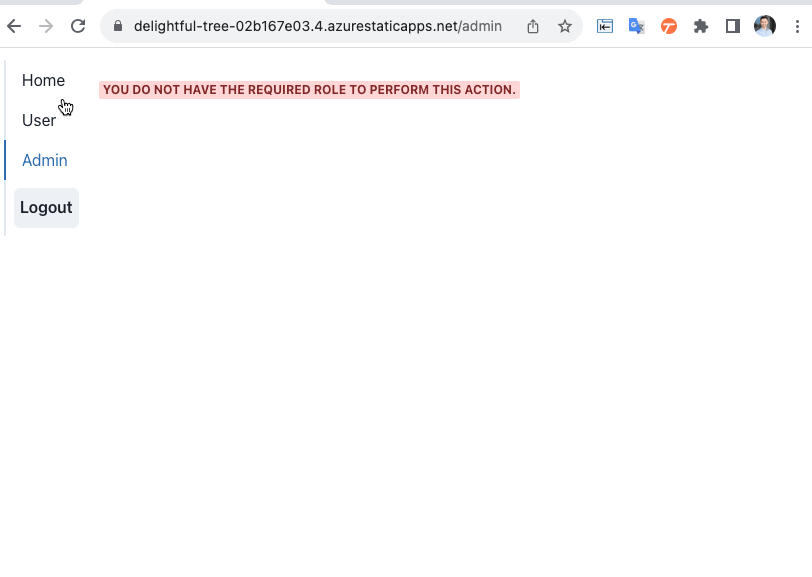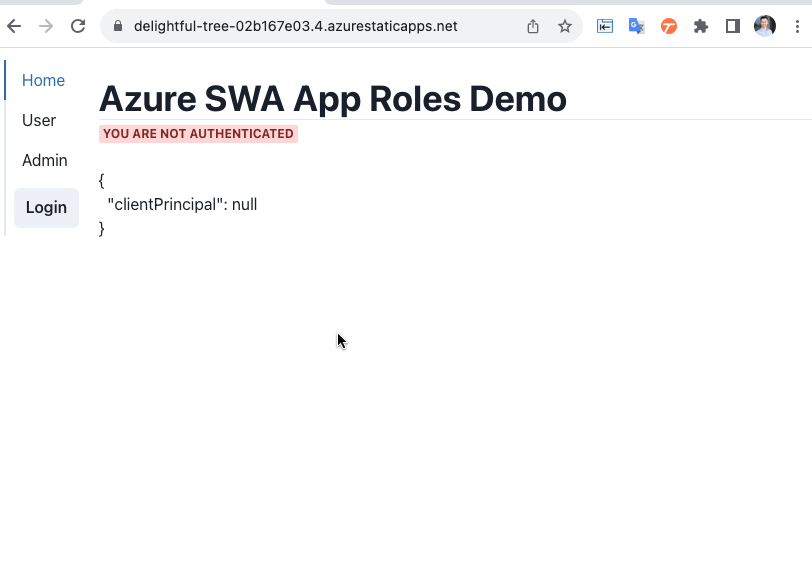
Build a secure web app with Azure SWA and Azure Active Directory App Roles
- Frontend: React
- Backend: Managed Azure Functions (Python)
- Authentication: Custom authentication provider with Azure AD
- Authorization: Role-based access control (RBAC) with Azure AD App Roles
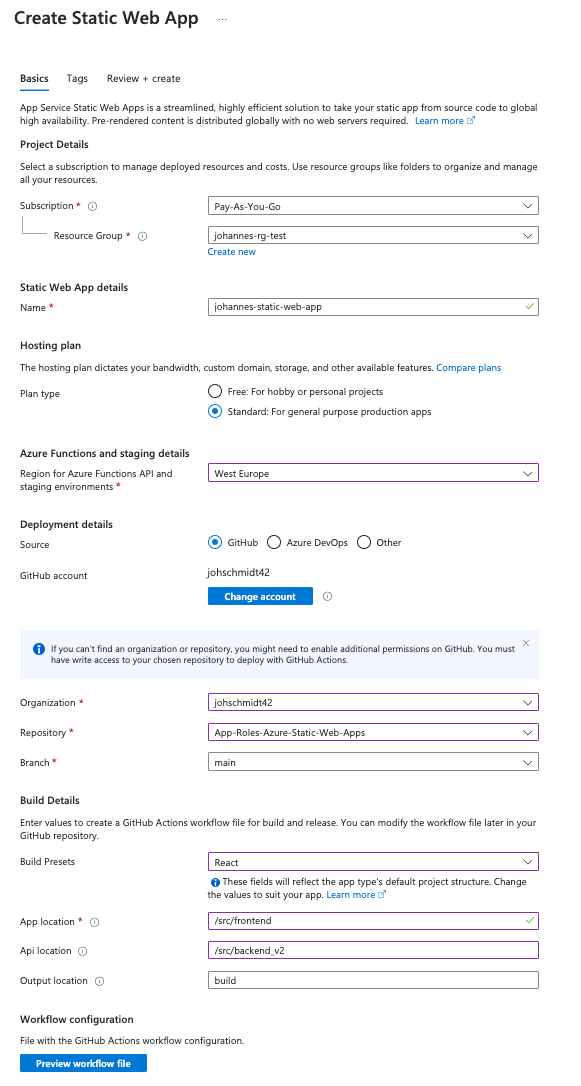
Create an Azure Static Web App.
Follow the steps in the blog post.
- Install terraform and cdktf cli, follow here
pip install -r requirements-infra.txt- run
cdktf provider add azure/azapifollowed bycdktf get. This is necessary as the azapi provider itself is not yet published to pypi and needs to be retrieved via the terraform binding mechanism ( see here for more information). For that, the cdktf-cli (installed by npm) and the cdktf python package need to have the same version - Create an azure service principal for infrastructure deployment
- Create a resource group in azure and grant the service principal contributor rights to it (the SP will be used by terraform and needs contributor rights for resource creation/management)
- Create a storage account and container within the resource group (this will be used as the remote backend for the terraform state)
- Create a PAT in GitHub. This allows Terraform to access your GitHub repository
- Run
cp .env-infra.example .env-infraand fill all the configuration of.env-infrawith data of steps from 3-6 - Deploy with
cdktf apply
You need to add two secrets to your GitHub repository:
Go to your GitHub repository -> Settings -> Secrets and Variables -> Actions and click on new repository secret. Name
it ARM_TENANT_ID and enter the tenant uuid here.
- backend_v1: v1 programming model
- backend_v2: v2 programming model
- backend_v2_fastapi: v2 programming model with FastAPI (currently not working, see this issue)