A Companion Demo for the CI/CD with Docker and Kubernetes Book
Run it in your workstation
$ docker-compose up --build
$ curl -w "\n" -X PUT -d "firstName=al&lastName=pacino" 127.0.0.1:3000/person
$ curl -w "\n" 127.0.0.1:3000/allCI/CD Pipelines
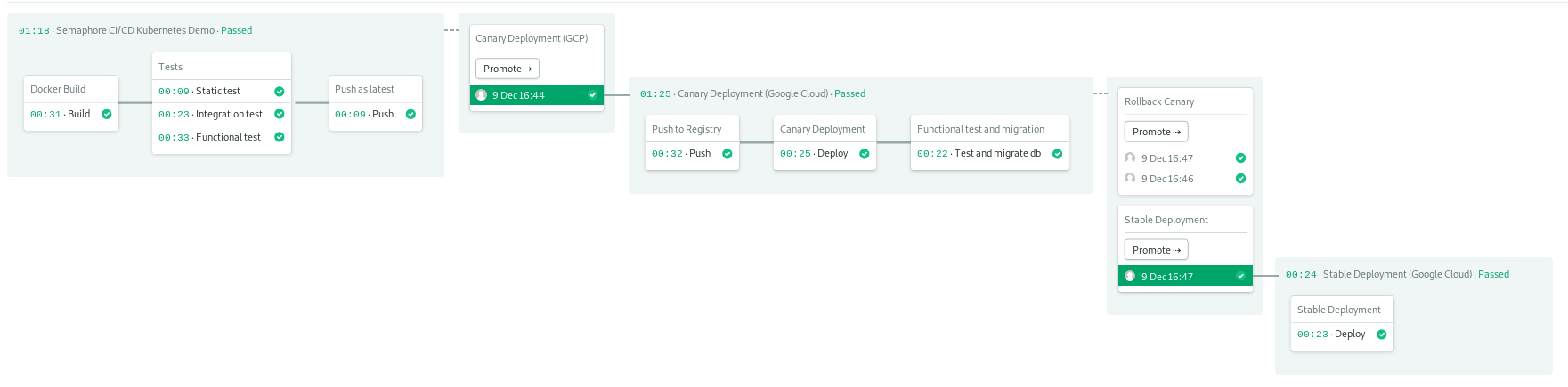
The CI/CD workflow is as follows:
- Build docker image w/cache.
- Run tests inside docker images.
- Push image to docker registry.
- Perform canary deployment.
- Run functional test and migration in canary deployment.
- One-click production/stable deployment.
Configure Semaphore
- Fork this repository
- Clone it to your machine
- Sign up for Semaphore and install sem cli.
- Add the project to Semaphore:
$ sem initDeploy to the cloud
Cloud services required:
- Kubernetes Cluster (recommended 3 nodes) called
semaphore-demo-cicd-kubernetes - PostgreSQL Database in the same region and VPC as the cluster.
Open the relevant pipeline files at .semaphore and fill in the environment variables for the blocks.
Uncomment the desired promotion on .semaphore/semaphore.yml.
Create Secrets
Create DB connection secret:
$ sem create secret db-params \e
-e DB_USER=YOUR_DB_USERNAME \
-e DB_PASSWORD=YOUR_DB_PASSWORD \
-e DB_HOST=YOUR_DB_IP \
-e DB_PORT=YOUR_DB_PORT (5432) \
-e DB_SCHEMA=YOUR_DB_SCHEMA (postgres) \
-e DB_SSL=true|false (empty)Depending on the cloud provider, you’ll need to create different secrets.
AWS
- Create an IAM User with Administrator permissions. Create a secret with the access id and the Kubernetes kubeconfig file:
$ sem create secret aws-key \
-e AWS_ACCESS_KEY_ID=YOUR_AWS_ACCESS_ID \
-e AWS_SECRET_ACCESS_KEY=YOUR_AWS_SECRET_KEY \
-f YOUR_KUBECONFIG.yml:/home/semaphore/aws-key.ymlGoogle Cloud
- Create a project called
semaphore-demo-cicd-kubernetes - Create service account and generate a key file. Upload the file to Semaphore:
$ sem create secret gcp-key -f YOUR_KEY_FILE.json:/home/semaphore/gcp-key.jsonDigitalOcean
- Create a project called
semaphore-demo-cicd-kubernetesand set it as default. - Get your authentication API Token and create a secret for it:
$ sem create secret do-key -e DO_ACCESS_TOKEN=YOUR_DIGITALOCEAN_TOKEN-
Set the parameter in
db-paramssecret toDB_SSL=true -
Create a secret to store your DockerHub credentials:
$ sem create secret dockerhub \
-e DOCKER_USERNAME=YOUR_DOCKERHUB_USER \
-e DOCKRE_PASSWORD=YOUR_DOCKERHUB_PASSWORDLicense
Copyright (c) 2019 Rendered Text
Distributed under the MIT License. See the file LICENSE.md.