WhatsTrapp is a tool for analyzing and dumping WhatsApp accounts.
- Node.js >= 8.0
- Yarn
- Docker
- Docker Compose
Clone the repository:
$ git clone git@github.com:Wicker25/whatstrapp.git
$ cd whatstrapp/
Install all the dependencies for the project:
$ yarn
Create the Elasticsearch and Kibana's containers:
$ docker-compose pull
Start the Elasticsearch and Kibana's containers with:
$ docker-compose up
Launch the WhatsTrapp server with:
$ yarn start
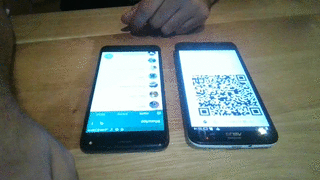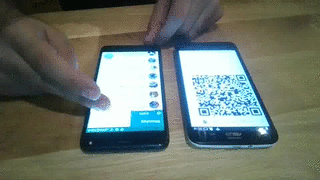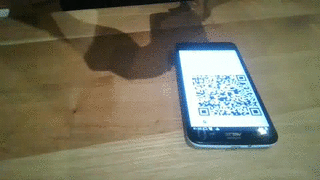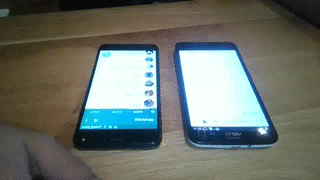
Then open your browser at http://127.0.0.1:8025/ and wait until the QR code has been loaded.
Launch the target's WhatsApp and, from the main menu, select "WhatsApp Web".
Finally, take a picture of the QR code and enjoy it!
Launch Kibana by opening your browser at http://127.0.0.1:5601/.
Set the Index Pattern as wt-* and click on "Create" (the pattern is valid only after you collected some data!).
Now you can open the Discover page and visualize the collected data.
The WhatsTrapp's architecture consists of a Puppeteer, Puppets, and Clients:
- The Puppeteer launches the browser instance by using Google Puppeteer and injects a Puppet into it;
- The Puppet is a JavaScript that performs actions in the WhatsApp Web page;
- The Client is the user interface used by the attacker for performing the hack.
All of the components communicate with each other via WebSocket.