This is a work-in-progress remote support tool, designed to allow forwarding any tcp connection securely over the internet without having to set up port forwarding.
Currently, it can forward any tcp connection over a channel encrypted by TLSv1.2, with public key authentication, through certain types of NATs. It is still very rough around the edges. Symmetric NATs do not work without setting up port forwarding. See the wikipedia page on udp hole punching for more information.
-
Make sure you are not working from a corporate network. If you are, you will need to set up port forwarding, which is not currently supported.
-
Download and run the server application on a computer accessible to both of the clients, with port 40000 open.
-
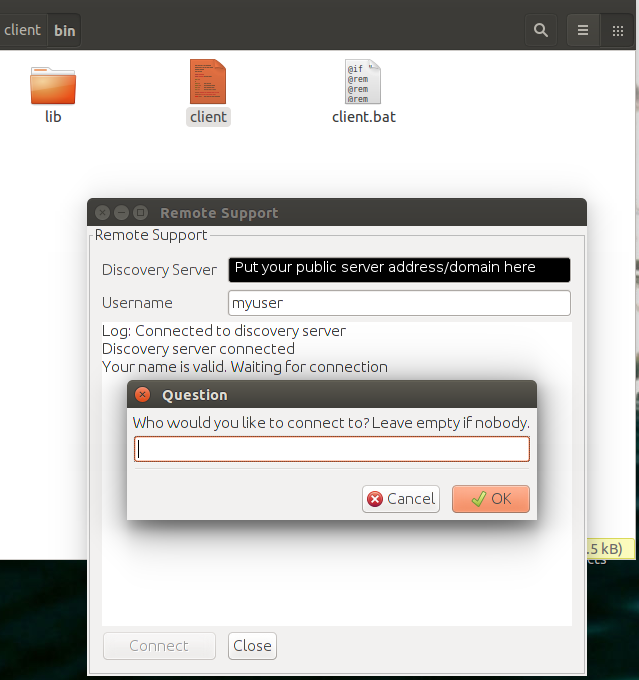
Download and run the client application by extracting the zip and launching the shell script (linux/mac) or the .bat file (windows). Enter the public ip address or domain for the discovery server you set up in part 2. The application will connect to this address on port 40000 to negotiate a connection with your partner, but no data from the tunnel will be sent to the discovery server once your connection is established.
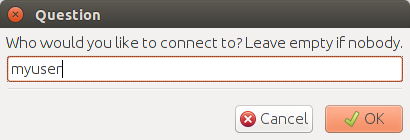
- Connect to your partner, or leave blank if your partner will connect to you
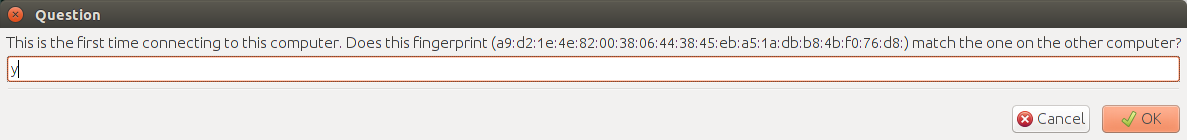
- Verify your X509 Certificate fingerprints
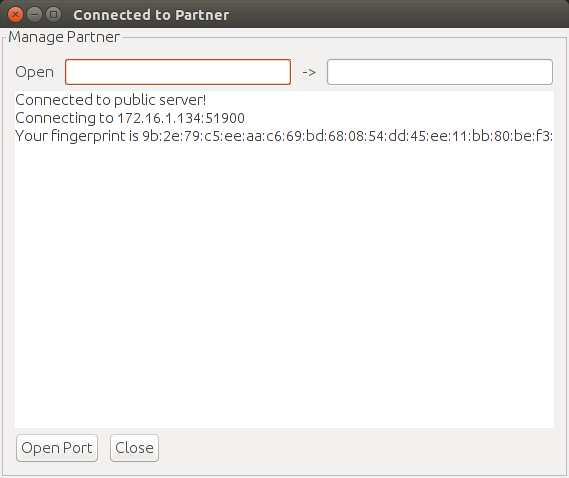
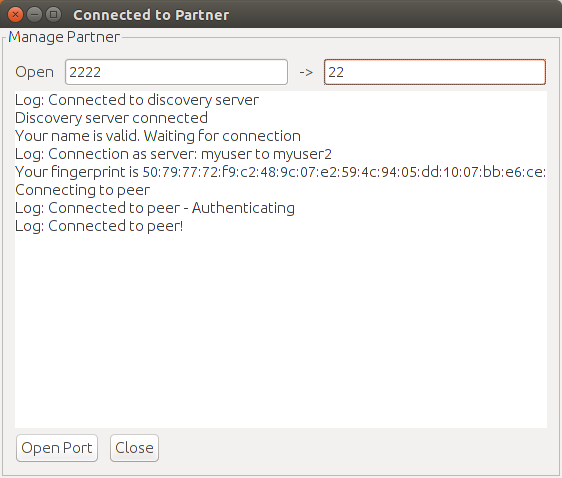
6)You are now connected. Enter a local port to be forwarded to a remote port. A single tcp connection on this port will be forwarded to the remote computer. Once the connection closes, you will have to re-open the port.
In the example above, to ssh in to the remote computer you would use ssh [remote-user]@localhost -p 2222 to connect to an ssh server on the remote machine on port 22.
It uses UDP hole punching to allow clients to connect through a network address translator. The server/ subproject must be running on a publicly accessible server, so that the clients can learn each other's public ip addresses. Each client then tries to connect directly to the other, attempting to re-use the port mapping from the public connection. This project uses Netty and Barchart UDT to provide a reliable stream over UDP, and BouncyCastle to provide encryption.
-
Fix bug where the client hangs when closing
-
Fix bug where close doesn't work when connecting to peer
-
Change close button text on public screen to cancel
-
Add persistent forwarded connections (i.e that reconnect when they close)
-
Clean up code
-
Make error handling more friendly, fix service closing exceptions
-
Add separate logs per service, error handling + separate ui panes per service
-
Make the ui more user friendly
-
Establish encrypted connection with public server, authenticate aliases
-
Ask the user to forward ports if udp hole punching doesn't work, and allow connecting directly to another user
-
Allow running as daemon, so you can enable unattended access
-
Launch vnc and ssh server remotely
-
Allow file uploading or other admin tasks directly