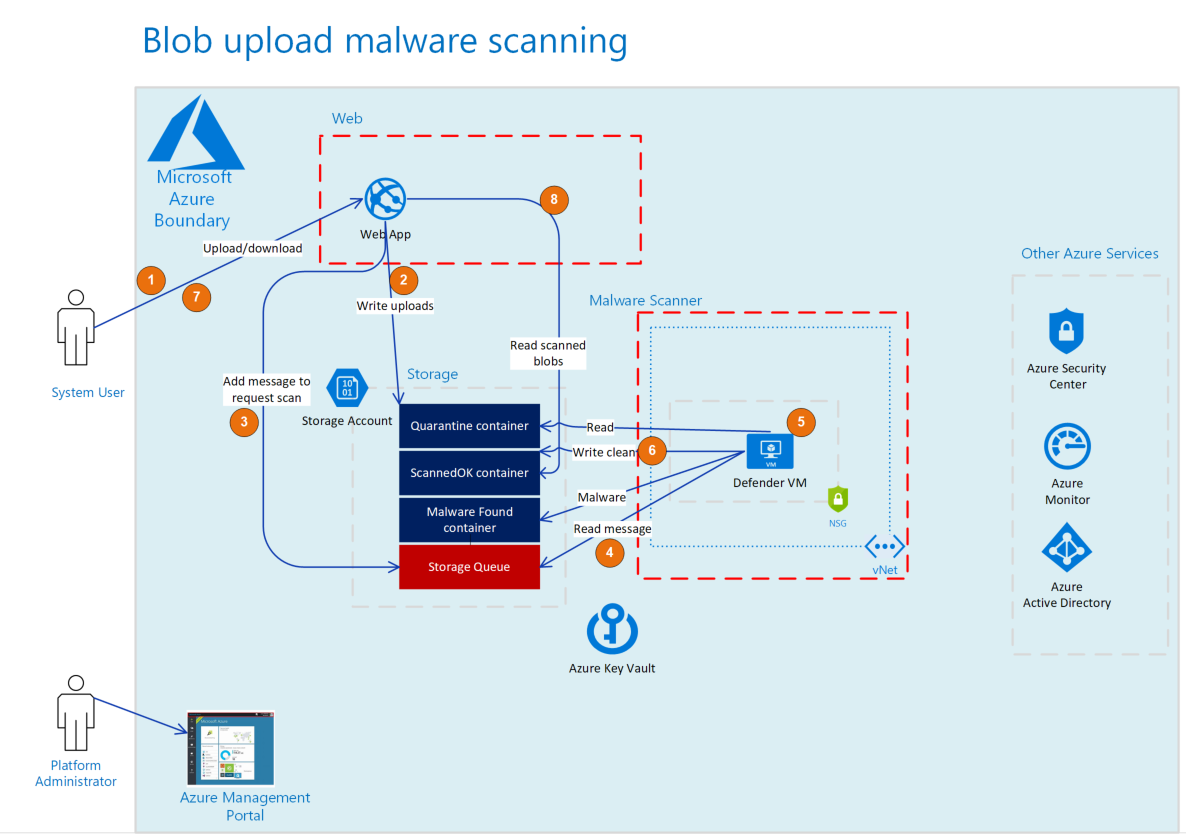
Users can upload files to Azure blob storage for others to download.
We don't want the files downloaded to contain Malware.
- User uploads a file to a web app
- Web app stores upload in container (named quarantine)
- Web app adds message to queue to request scan in Azure Storage Queue
- VM reads message and download file
- VM scans for malware
- A malware check is completed and either
- If malware is found the file is moved to a container (named malwarefound) and deletes from quarantine
- If file scan is OK then the file is moved to a container (named scannedok) and deletes from quarantine
- Users of the application request download to web app
- web app returns file from ScannedOK container
Note: VM uses Managed Identity and KeyVault Policy to connect to KeyVault and request queue connection string and SAS tokens enabling read/write from containers
Create
- Azure Storage account with 3 containers named quarantine, scannedok, malwarefound
- Virtual Machine (with system managed identity) ensure you add antimalware and exclude the scanpath such as d:\scan - suggest a size such as DS3v2 with with Accelerated Networking
- Azure KeyVault
- Add key vault policy to allow list, get secrets from KeyVault for VM managed identity
- Add secrets to keyvault (note case sensitive)
- BlobSasToken e.g. ?sv=2019-10-10&ss=b&srt=sco&sp=rwdlacx&se=2023-06-29T19:21:07Z&st=2020-06-29T11:21:07Z&spr=https&sig=7FFFFFFFFFFFFFAAAAAAAAAAAAA
- queueConnectionString e.g. DefaultEndpointsProtocol=https;AccountName=example;AccountKey=1oPsXDAAAAAopDjlRkkg==;EndpointSuffix=core.windows.net
- workQueue e.g. scanqueue
- Open the source code in visual studio, right click and select Publish to create a standalone EXE for windows, copy this onto the VM with the config file
- upload blob to quarantine container e.g. example.txt
- add a message with the filename of the blob e.g. example.txt to the queue using the Azure portal (note do not Encode the message body in Base64)