Android App Which Shows Details about CWA Exposures (Requires Root)
© 2020 Michael Huebler and other contributors. This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details.
There are 3 options:
- Download from https://play.google.com/store/apps/details?id=org.tosl.warnappcompanion
- Write a short review
- Download the latest released APK from the Assets at https://github.com/mh-/corona-warn-companion-android/releases
- Install via
adbtool and USB cable:adb install corona-warn-companion-github-release.apk
git clode https://github.com/mh-/corona-warn-companion-android.git- In Android Studio, select a 'flavor':
githubis the normal version, called "Corona-Warn-Companion".playstoreis a version that was renamed to "Warn-App-Companion" because of the Play Store requirements for COVID-19 apps; this is not a category 1 or 2 app and must therefore not use COVID-19 related terms in its Play Store listing. - Build the
debugbuild variant, and install it on your device. Thereleasebuild variant will probably build out-of-the box only on macOS because of the way how the keystore for app signing is accessed.
This app helps you to better understand warnings of the official Corona-Warn-App.
ATTENTION: FOR FULL FUNCTIONALITY, THE APP REQUIRES ROOT PERMISSIONS. Without root permissions, the app cannot access your risk encounters, and only three features are available: 1. Test how many diagnosis keys can be downloaded from the server; 2. Use RaMBLE data; 3. Demo Mode.
- The app reads the Rolling Proximity IDs recorded by your device from the Exposure Notifications database (this is only possible with root permissions, which is why the official Corona-Warn-App cannot display these details).
 Alternatively, the app can also read a database exported from RaMBLE (does not need root permissions).
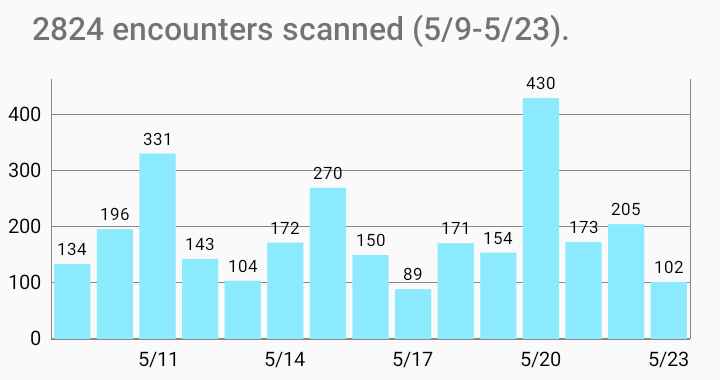
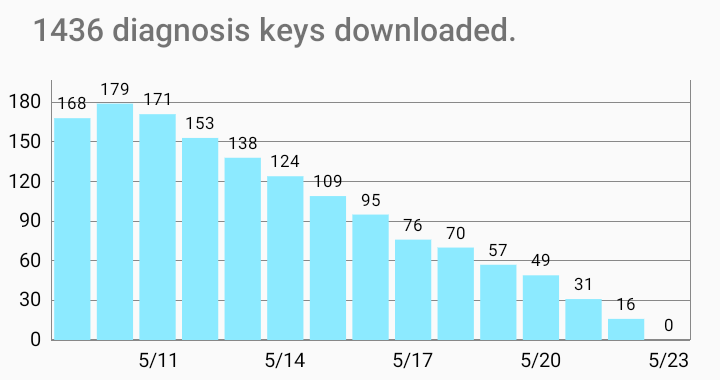
Alternatively, the app can also read a database exported from RaMBLE (does not need root permissions). - The app downloads the Diagnosis Keys from the official Corona-Warn-Server. It downloads the keys published daily for the last few days, and the keys published every hour for today. Therefore, different information than in the official Corona-Warn-App might be displayed.
Only keys for the days found in step 1 are shown and counted.
- The app compares both in order to find matches (risk encounters).
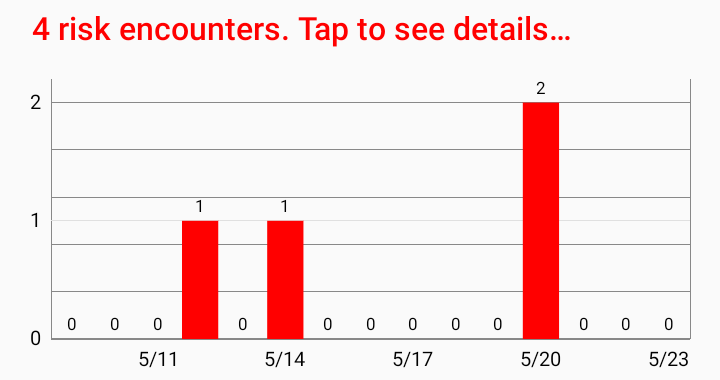
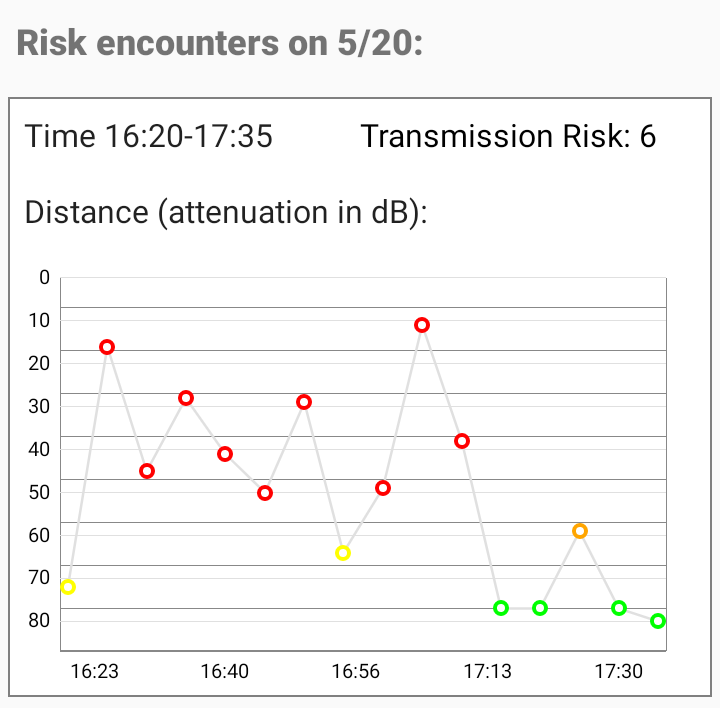
If risk encounters are found, it shows the details: At which times and with which radio attenuation (roughly corresponds to the distance) did the encounters take place, and what level of transmission risk did the encounters have.
Note that 1 means a low and 8 means a high transmission risk.
- The app does not process any personal data.
- The app only accesses the internet for the purpose 2 (see above), i.e. it only downloads data from the official Corona-Warn-Server and does not send any data to other servers.
- The app does not show any advertising.
Note: This app has only been tested on a few devices so far, so it is possible that it will not work and/or show incorrect results.
The source code of the app is published at https://github.com/mh-/corona-warn-companion-android, so you can check the source code, build the app yourself, and you are also welcome to contribute to improvements.
In RaMBLE mode, the app will not read the Exposure Notification database, but instead read the most recent RaMBLE database export stored in the Download folder.
Note that the Exposure Notifications database contains calibrated_rssi (see here).
RaMBLE however stores only raw_rssi, which means that the colors shown on the details screen are probably different from the case when the app reads the Exposure Notifications database.
- The app is used for private purposes only, it is not used for any business purposes.
- The app is not a "hacking tool". It only reads data from the memory of your own device, which is stored there without additional encryption.