This is a Microsoft Sysinternals Sysmon configuration repository, set up modular for easier maintenance and generation of specific configs.
NOTICE; Sysmon 8.02 is not compatible with this configuration, it will cause severe blind spots in your logging. Please use Sysmon 8.0 or 8.0.4
NOTICE; Sysmon 9.0x is not supported in the generate script yet. There is a manually generated configuration HERE.
Note: I do recommend using a minimal number of configurations within your environment for multiple obvious reasons, like; maintenance, output equality, manageability and so on.
Big credit goes out to SwiftOnSecurity for laying a great foundation and making this repo possible! sysmonconfig-export.xml.
Equally a huge shoutout to Roberto Rodriguez for his amazing work on the ThreatHunter-Playbook and his contribution to the community on his blog.
Final thanks to Matt Graeber for his PowerShell Modules, without them, this project would not have worked as well.
Pull requests / issue tickets and new additions will be greatly appreciated!
I started a series of blog posts covering this repo;
- Endpoint detection Superpowers on the cheap - part1 - MITRE ATT&CK, Sysmon and my modular configuration
- Endpoint detection Superpowers on the cheap — part 2 — Deploy and Maintain
- Endpoint detection Superpowers on the cheap — part 3 — Sysmon Tampering
Following this blogpost Sysmon 8.0, a leap forward in event annotation I've been working on updating the configuration modules to schemaversion 4.1 as well as adding the MITRE annotation fields. Eventually I deviated a little bit from my blogpost and went with the OSSEM field naming; technique_id and technique_name
I strive to map all configurations to the ATT&CK framework whenever Sysmon is able to detect it.
A current ATT&CK navigator export of all linked configurations is found here and can be viewed here
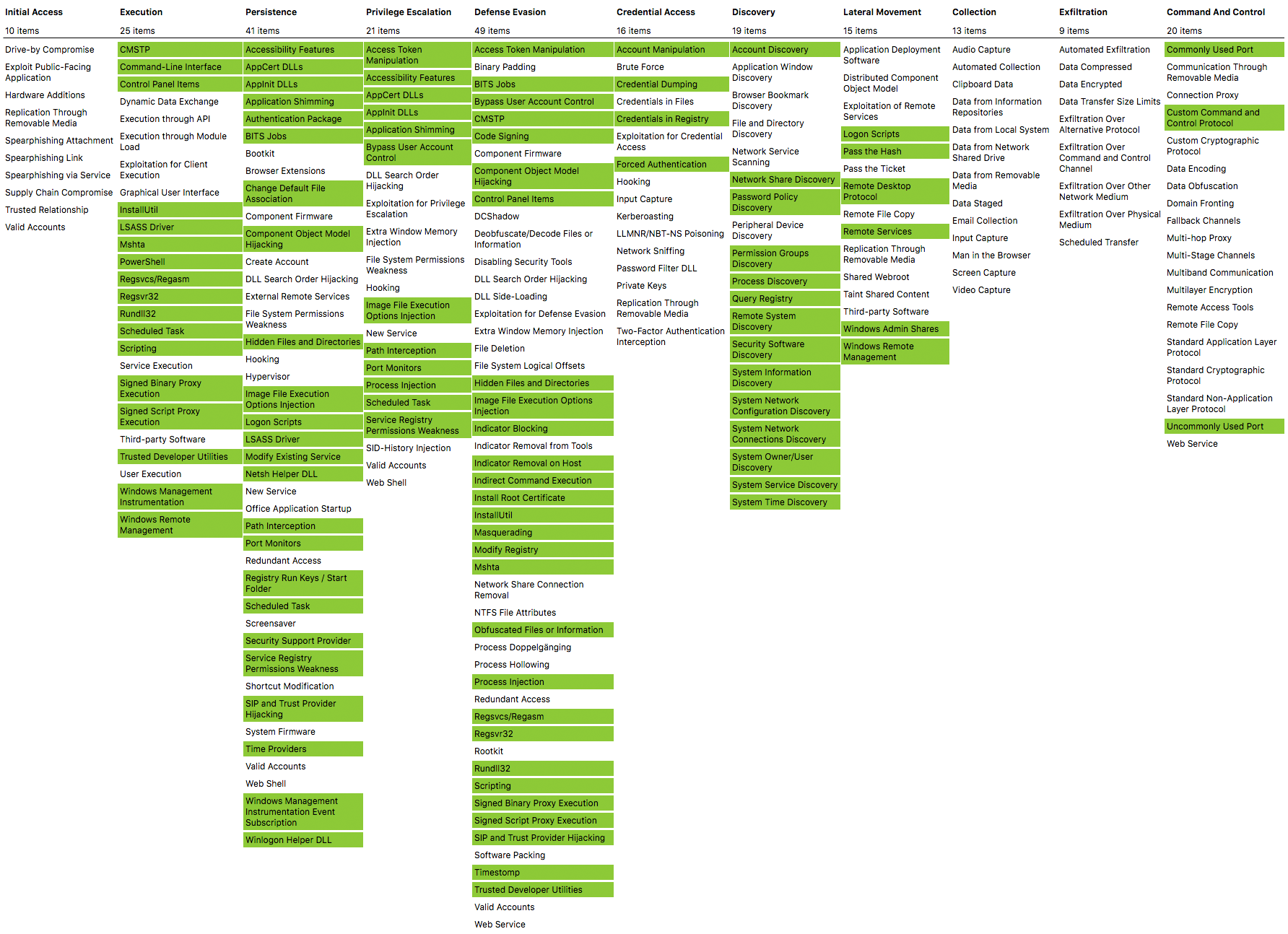
I highly recommend looking at the configs before implementing them in your production environment. This enables you to have as actionable logging as possible and as litte noise as possible.
Install the PowerShell modules from PSSysmonTools
git clone https://github.com/olafhartong/PSSysmonTools.git
cd PSSysmonTools
Import-Module .\PSSysmonTools.psm1
You will need to install and observe the results of the configuration in your own environment before deploying it widely. For example, you will need to exclude actions of your antivirus, which will otherwise likely fill up your logs with useless information.
git clone https://github.com/olafhartong/sysmon-modular.git
cd sysmon modular
.\Generate-Sysmon-Config.ps1
Optionally you can omit the comments from the merged config with the “-ExcludeMergeComments” switch.
You might see an error like ; Merge-SysmonXMLConfiguration : The schema version of C:\Temp\sysmon-modular-master\sysmonconfig.xml () does not match that of the reference configuration: The error is due to the validator. When executing the oneliner the sysmonconfig.xml is created but it is still empty at that time. Therefore it is not a valid config at that time, the file is filled with data at the end of the generation phase. You can safely ignore it.
You can test your config if it's schema compliant
Test-SysmonConfiguration .\sysmonconfig.xml
This repository also was made available within SysmonShell a great tool by Nader Shalabi
Run with administrator rights
sysmon.exe -accepteula -i sysmonconfig.xml
Run with administrator rights
sysmon.exe -c sysmonconfig.xml
- Link more indicators to Mitre ATT&CK techniques.
- Add / Improve comments
- Extend, extend, extend.



