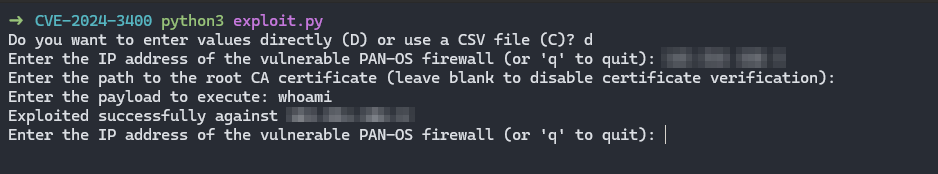
This script is a simple tool for exploiting vulnerable PAN-OS firewalls. It allows users to perform attacks against vulnerable PAN-OS firewalls by injecting custom payloads into them. The script can be run by entering values directly or by using a CSV file containing a list of targets.
- Make sure you have Python 3.x installed along with the required libraries.
- Download or clone this repository into your system.
- Open a terminal or command prompt and navigate to the directory where you have saved this repository.
- Run the script by executing the command
python3 exploit.py. - Choose option 'D' to enter values directly.
- Follow the prompts to input the firewall IP address, payload to be executed, and the path to the root CA certificate if required.
- Make sure you have Python 3.x installed along with the required libraries.
- Prepare a CSV file containing a list of targets you want to attack. The format should be three columns: firewall IP address, payload, and the path to the root CA certificate (optional).
- Save the CSV file to a location on your system.
- Download or clone this repository into your system.
- Open a terminal or command prompt and navigate to the directory where you have saved this repository.
- Run the script by executing the command
python3 exploit.py. - Choose option 'C' to use a CSV file.
- Enter the path to the CSV file when prompted.
- The script will read the CSV file, exploit each listed target, and print the results.
Make sure to use this tool responsibly and only for legitimate purposes. Misusing this tool to conduct unauthorized attacks is strictly prohibited.