🔗 https://identity.ic0.app • 📜 Specification
―
📚 Forum • 🚑 Report an Issue • 📞 Discord
Internet Identity is an authentication service for the Internet Computer. It is the authentication system that allows hundreds of thousands of users to log in to Dapps like Distrikt, DSCVR and more.
Internet Identity is:
- Simple: It uses some of the WebAuthn API to allow users to register and authenticate without passwords, using TouchID, FaceID, Windows Hello, and more.
- Flexible: Integrating Internet Identity in a Dapp (or even Web 2 app) is as simple as opening the Internet Identity's HTTP interface, https://identity.ic0.app, in a new tab. No need to interact with the canister smart contract directly.
- Secure: Different identities are issued for each app a user authenticates to and cannot be linked back to the user.
For more information, see What is Internet Identity? on internetcomputer.org.
This section gives an overview of Internet Identity's architecture, instructions on how to build the Wasm module (canister), and finally pointers for integrating Internet Identity in your own applications.
Use the Internet Identity canister in your local dfx project by adding the following code snippet to your dfx.json file:
{
"canisters": {
"internet_identity": {
"type": "custom",
"candid": "https://github.com/dfinity/internet-identity/releases/download/release-2024-03-01/internet_identity.did",
"wasm": "https://github.com/dfinity/internet-identity/releases/download/release-2024-03-01/internet_identity_dev.wasm.gz",
"remote": {
"id": {
"ic": "rdmx6-jaaaa-aaaaa-aaadq-cai"
}
},
"frontend": {}
}
}
}To deploy, run dfx deploy.
To access Internet Identity or configure it for your dapp, use one of the following URLs:
- Chrome, Firefox:
http://<canister_id>.localhost:4943 - Safari:
http://localhost:4943?canisterId=<canister_id>
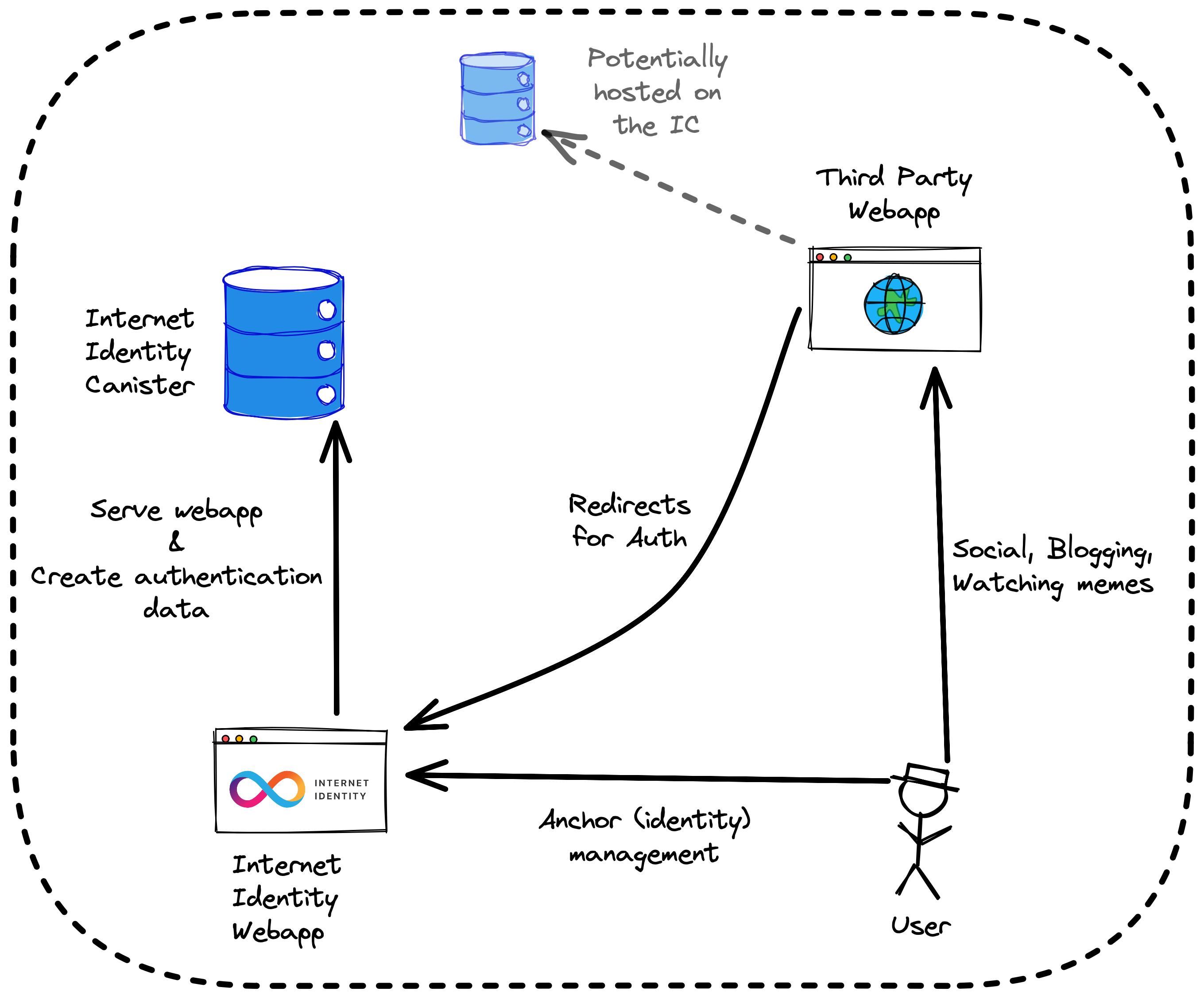
Internet Identity is an authentication service for the Internet Computer. All programs on the Internet Computer are Wasm modules, or canisters (canister smart contracts).
Internet Identity runs as a single canister which both serves the frontend application code, and handles the requests sent by the frontend application code.
💡 The canister (backend) interface is specified by the internet_identity.did candid interface. The (backend) canister code is located in
src/internet_identity, and the frontend application code (served by the canister through thehttp_requestmethod) is located insrc/frontend.
The Internet Identity authentication service works indirectly by issuing "delegations" on the user's behalf; basically attestations signed with some private cryptographic material owned by the user. The private cryptographic material never leaves the user's device. The Internet Identity frontend application uses the WebAuthn API to first create the private cryptographic material, and then the WebAuthn API is used again to sign delegations.
For information on how Internet Identity works in more detail, please refer to the following:
- Internet Identity presentation 📼, streamed during the Genesis Event
- Internet Identity Specification, the official Internet Identity Specification
To get the canister (Wasm module) for Internet Identity, you can either download a release from the releases page, or build the code yourself. The simplest way to build the code yourself is to use Docker and the docker-build script:
$ ./scripts/docker-buildThe Dockerfile specifies build instructions for Internet Identity. Building the Dockerfile will result in a scratch container that contains the Wasm module at /internet_identity.wasm.gz.
💡 The build can be customized with build features.
We recommend using the docker-build script. It simplifies the usage of build features and extracts the Wasm module from the final scratch container.
💡 You can find instructions for building the code without Docker in the HACKING document.
The using-dev-build demo shows a documented example project that integrates Internet Identity. For more, please refer to the Client Authentication Protocol section of the Internet Identity Specification to integration Internet Identity in your app from scratch. For a just-add-water approach using the agent-js library (also used by using-dev-build), check out Kyle Peacock's blogpost.
If you're interested in the infrastructure of how to get the Internet Identity canister and how to test it within your app, check out using-dev-build, which uses the Internet Identity development canister.
The Internet Identity build can be customized to include features that are useful when developing and testing. We provide pre-built flavors of Internet Identity that include different sets of features.
These options can be used both when building with docker and
without docker. The features are enabled by setting the corresponding
environment variable to 1. Any other string, as well as not setting the
environment variable, will disable the feature.
For instance:
$ II_FETCH_ROOT_KEY=1 dfx build
$ II_DUMMY_CAPTCHA=1 II_DUMMY_AUTH=1 ./scripts/docker-buildThe features are described below:
| Environment variable | Description |
|---|---|
II_FETCH_ROOT_KEY |
When enabled, this instructs the frontend code to fetch the "root key" from the replica. The Internet Computer (https://ic0.app) uses a private key to sign responses. This private key not being available locally, the (local) replica generates its own. This option effectively tells the Internet Identity frontend to fetch the public key from the replica it connects to. When this option is not enabled, the Internet Identity frontend code will use the (hard coded) public key of the Internet Computer. |
II_DUMMY_CAPTCHA |
When enabled, the CAPTCHA challenge (sent by the canister code to the frontend code) is always the known string "a". This is useful for automated testing. |
II_DUMMY_AUTH |
When enabled, the frontend code will use a known, stable private key for registering anchors and authenticating. This means that all anchors will have the same public key(s). In particular this bypasses the WebAuthn flows (TouchID, Windows Hello, etc), which simplifies automated testing. |
II_INSECURE_REQUESTS |
When enabled, the 'upgrade-insecure-requests' directive is removed from the content security policy in order to allow local development with Safari. |
We offer some pre-built Wasm modules that contain flavors, i.e. sets of features targeting a particular use case. Flavors can be downloaded from the table below for the latest release or from the release page for a particular release.
| Flavor | Description | |
|---|---|---|
| Production | This is the production build deployed to https://identity.ic0.app. Includes none of the build features. | 💾 |
| Test | This flavor is used by Internet Identity's test suite. It fully supports authentication but uses a known CAPTCHA value for test automation. Includes the following features:
|
💾 |
| Development | This flavor contains a version of Internet Identity that effectively performs no checks. It can be useful for external developers who want to integrate Internet Identity in their project and care about the general Internet Identity authentication flow, without wanting to deal with authentication and, in particular, WebAuthentication. Includes the following features:
See the using-dev-build project for an example on how to use this flavor. |
💾 |
Internet Identity requires data in stable memory to have a specific layout in order to be upgradeable. The layout has been changed multiple times in the past. This is why II stable memory is versioned and each version of II is only compatible to some stable memory versions.
If on upgrade II traps with the message stable memory layout version ... is no longer supported then the stable memory layout has changed and is no longer compatible.
The easiest way to address this is to reinstall the canister (thus wiping stable memory). A canister can be reinstalled by executing dfx deploy <canister> --mode reinstall.
We're here to help! Here are some ways you can reach out for help if you get stuck:
- Internet Identity Bug Tracker: Create a new ticket if you encounter a bug using Internet Identity, or if an issue arises when you try to build the code.
- DFINITY Forum: The forum is a great place to look for information and to ask for help.
- Support: Create a support request if you'd like to keep things private.
- Internet Identity Specification, the official Internet Identity Specification
- Integration with Internet Identity by Kyle Peacock
- What is Internet Identity? on internetcomputer.org
- Internet Identity presentation 📼 on YouTube, streamed during the Genesis Event
- Excalidraw, used to make diagrams