Sentinel Threat Intelligence Upload Toolkit
The Sentinel TI Upload Toolkit contains a number of PowerShell functions and scripts to import Threat Intelligence IOCs into Microsoft Sentinel using the upload indicators API. For more details also see Reference the upload indicators API (Preview) to import threat intelligence to Microsoft Sentinel
- Initially I started with just a few scripts while learning and trying to better understand the STIX indicator format specification and the Request Body for the API.
- Provide a quick automated process to load custom TI into Microsoft Sentinel
- Use Azure Automation account as an alternative to Azure Logic Apps
- Comparisson and content review of various Open Source TI Feeds
Author: AlexVerboon
The Sentinel Threat Intelligence Upload Toolkit PowerShell Module includes the following fuctions:
| Function | Description |
|---|---|
| ConvertTo-STIXJson | Converts a collection of IOCs (Indicators of Compromise) into STIX JSON format. |
| Get-IOCDomainNamesContent | Retrieves domain names from a specified URL (TXT files) |
| Get-IOCIPContent | Retrieves IP Addresses from a specified URL (TXT files) |
| Get-IOCIPRawContent | Retrieves IP Addresses from a specified URL (TXT files) |
| Get-IOCUrlContent | Retrieves Urls from a specified URL (TXT files) |
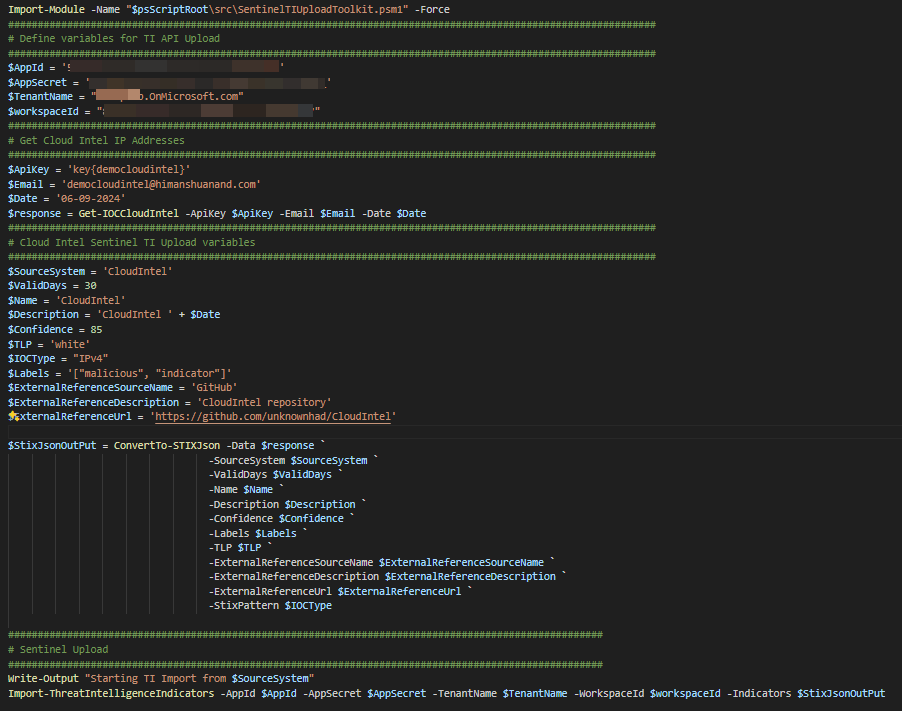
| Import-ThreatIntelligenceIndicators | Import threat intelligence indicators to Microsoft Sentinel using the Threat Intelligence upload API. Using client credentials for authentication and authorization |
| Import-ThreatIntelligenceIndicators_MI | Import threat intelligence indicators to Microsoft Sentinel using the Threat Intelligence upload API. Using system managed identity for authentication and authorization |
| Script | Description |
|---|---|
| Import-Blocklist-Bots.ps1 | Import Blocklist.de Bots IOC |
| Import-CloudIntel.ps1 | Import CloudIntel IOC |
| Import-DigitalSide-Threat-Intel.ps1 | Import DigitalSide IOCs |
| Import-OpenPhish.ps1 | Import OpenPhish IOcs |
| Import-Abuse-Botnet C2 IP Blacklist | Import SSL blacklist Abuse.ch |
| Import-TorExitNodes | Import Tor Exit Nodes |
| Import-TorAllNodes | Import Tor All Nodes |
| Script | Description |
|---|---|
| AA-Import-CloudIntelFeed.ps1 | Import CloudIntel IOC |
| AA-Import-TorExitNodes.ps1 | Import Tor Exit Nodes IOC |
| AA-Import-TorAllNodes.ps1 | Import Tor Exit Nodes IOC |
- Register a Microsoft Entra application and record its application ID.
- Generate and record a client secret for your Microsoft Entra application.
- Assign your Microsoft Entra application the Microsoft Sentinel contributor role or equivalent.
- Install the Threat Intelligence upload indicators API data connector in Microsoft Sentinel (optional) Microsoft documentation
- Within the Import-Scripts folder update the indiidual ps1 scripts.
- Run the PowerShell Script
- Create an Automation Account in Azure
- Assign the system managed identity for the Automation Account Microsoft Sentinel contributor role or equivalent.
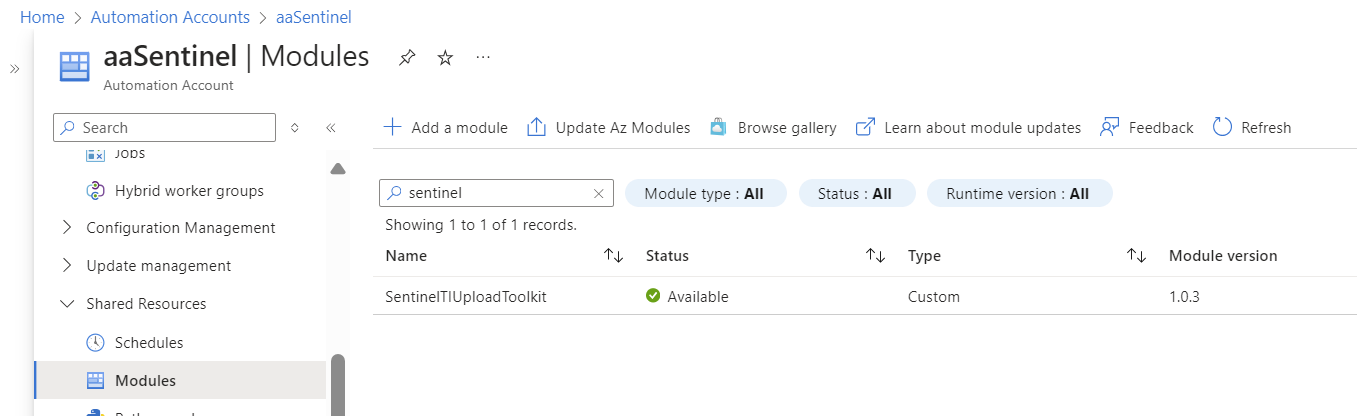
- Import the SentinelTIUploadToolkit PowerShell Module into the Azure Automation Account Modules
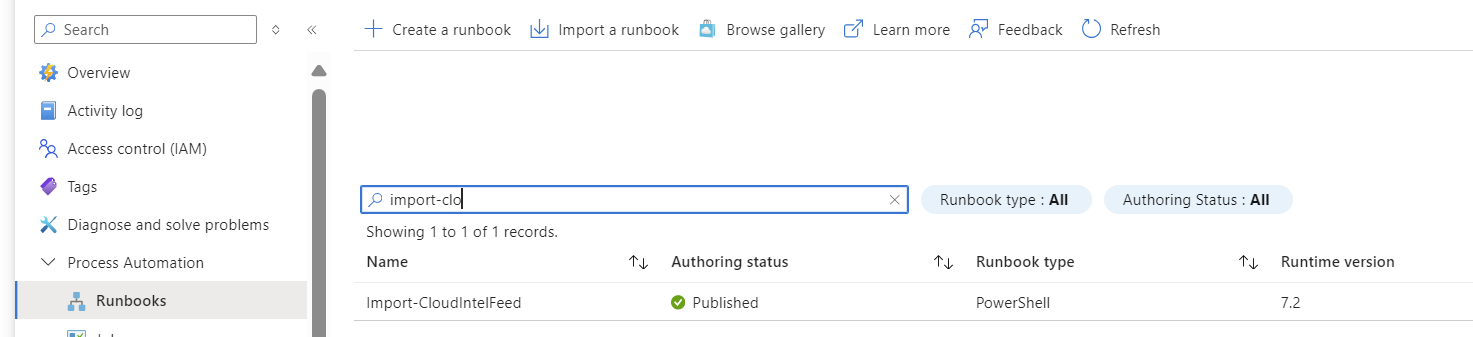
- Create a Runbook for example "Import-CloudIntelFeed" and paste the code from AA-Import-CloudINtelFeed
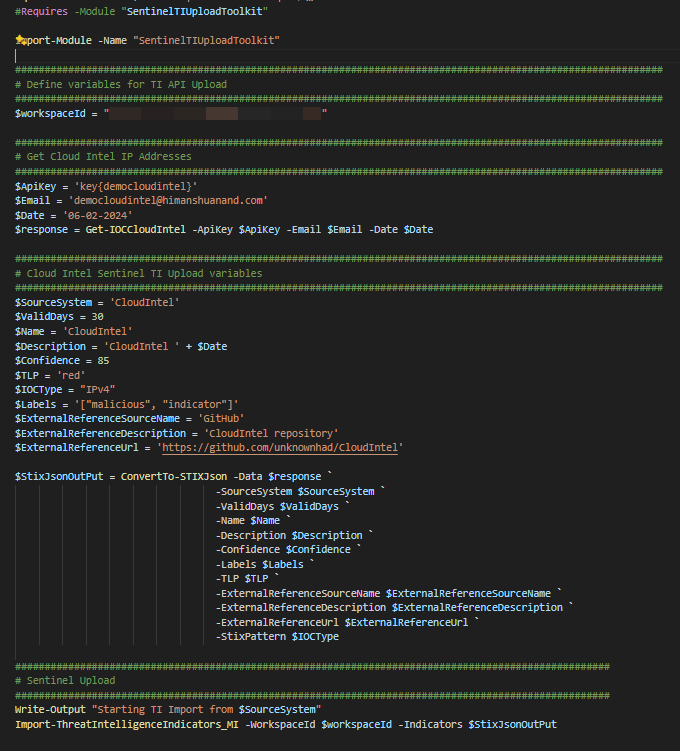
- Update the workspaceid variable and update other variables as per your needs
- Start the Runbook
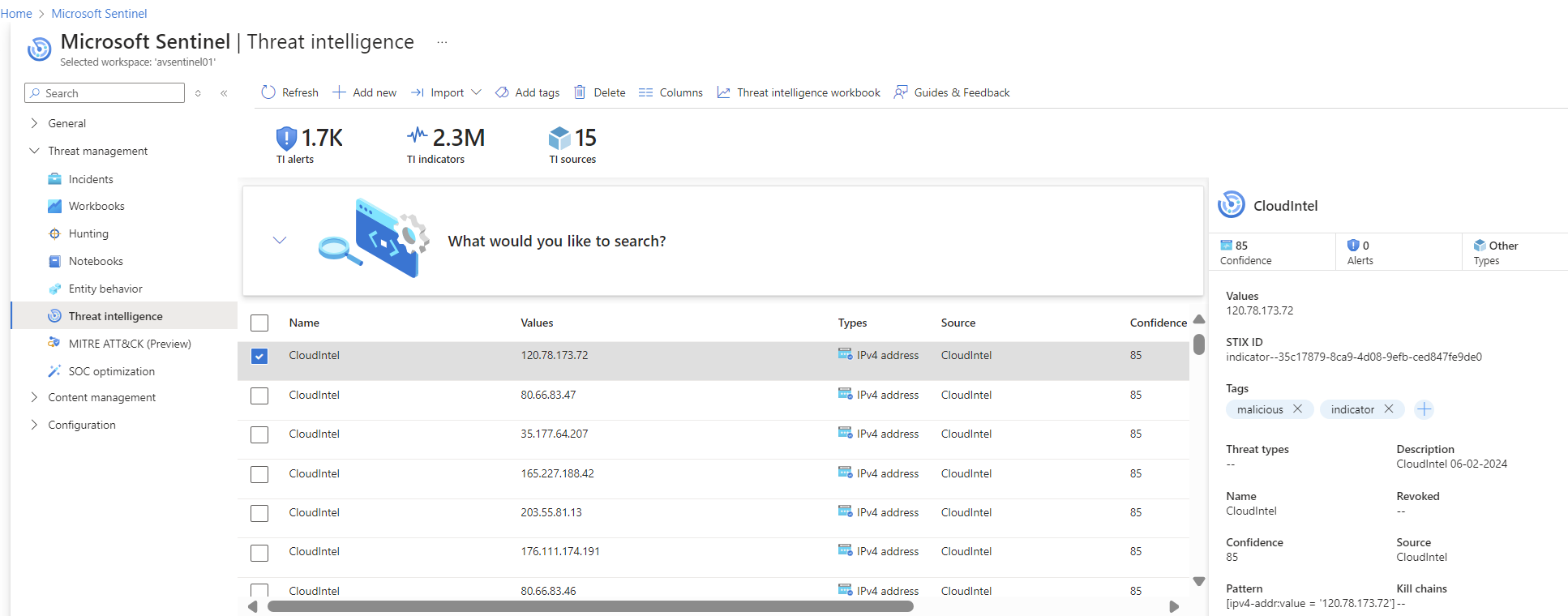
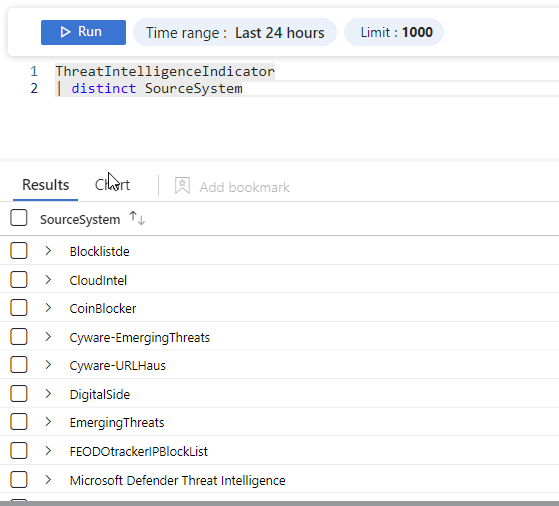
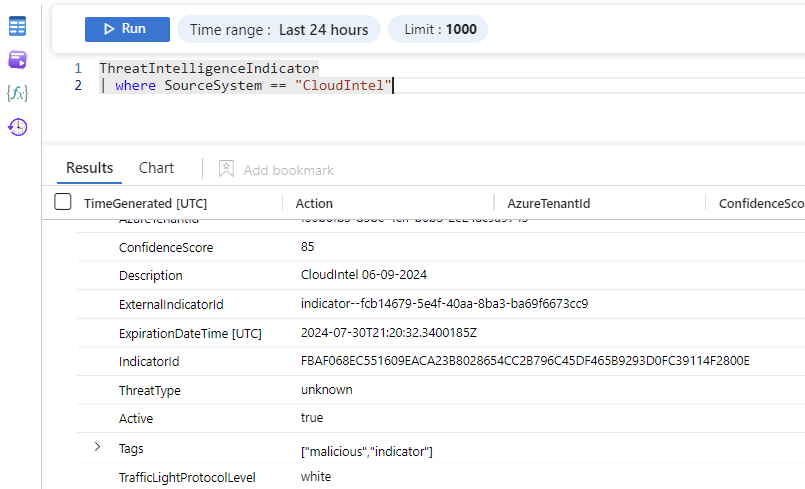
When all works as expected you see the imported TI appear in the Microsoft Sentinel portal and Log Analytics workspace.
- BertJanCyber for maintaining the Open Source Threat Intel Feeds list
- Fabian Bader, it's been a while since I created a PowerShell module, so used one of his as a reference.
- Add Automation Account variables to avoid hardcoded worskpaceid
- Add tutorial for creating new TI feed import scripts
- Create scripts to retrieve content from CSV files
- Create a Schedule for Automation Account Runbooks so that imports happen at the right time
- Add more examples for importing md5 hashes and email IOCs
- Automate PowerShell module ZIP file creation and upload to PowerShell Gallery
- Update Endpoint to https://sentinelus.azure-api.net/{workspaceId}/threatintelligenceindicators:upload (Currently in Preview)