This is a helper script providing an easy-to-use command line interface to support login and retrieve AWS temporary credentials for multiple roles of different accounts with saml2aws.
All notable changes to this project will be documented in CHANGELOG.
- Python - support Python 3.10, 3.11, 3.12.
- CodeQL is enabled in this repository.
- Dependabot is enabled for auto dependency updates.
- Gitleaks and TruffleHog are enabled in this GitHub Actions workflow for detecting and preventing hardcoded secrets.
- Snyk is enabled for vulnerability scanning and auto pull-request.
$ awslogin --help
Usage: awslogin [OPTIONS] COMMAND [ARGS]...
Get credentials for multiple accounts with saml2aws
Options:
-l, --shortlisted TEXT Show only roles with the given keyword(s);
e.g. -l keyword1 -l keyword2...
-s, --pre-select TEXT Pre-select roles with the given keyword(s);
e.g. -s keyword1 -s keyword2...
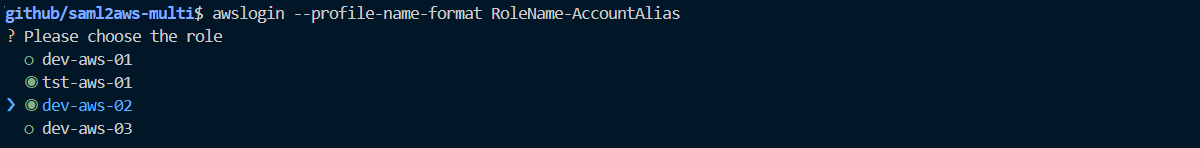
-n, --profile-name-format [RoleName|RoleName-AccountAlias]
Set the profile name format. [default:
RoleName]
-r, --refresh-cached-roles Re-retrieve the roles associated to the
username and password you providedand save
the roles into <home>/.saml2aws-
multi/aws_login_roles.csv. [default: False]
-t, --session-duration TEXT Set the session duration in seconds,
-d, --debug Enable debug mode. [default: False]
--help Show this message and exit.
Commands:
chained List chained role profiles specified in ~/.aws/config
switch Switch default profile
whoami Who am I?
-
When you run
awsloginthe first time, the script retrieves the roles associated to the username and password you provided, then saves the roles to<user_home>/.saml2aws-multi/aws_login_roles.csv, such that the script does not need to calllist_rolesevery time you runawslogin.For example, if you have role ARNs like:
RoleArn, AccountAlias arn:aws:iam::123456789012:role/aws-01-dev, aws-01 arn:aws:iam::123456789012:role/aws-01-tst, aws-01 arn:aws:iam::213456789012:role/aws-02-dev, aws-02 arn:aws:iam::313456789012:role/aws-03-dev, aws-03Then, the profile names will look like

To refresh the content of
aws_login_roles.csv, just runawslogin --refresh-cached-roles -
When you run
awslogin, the script pre-selects the options you selected last time. -
Use
--pre-selector-sto pre-select option by keyword(s).awslogin -s dev -s tst -
Use
--shortlistedor-lto show the list of roles having profile name matching the given keyword(s).awslogin -l dev -l tst -
To change your
defaultprofile in<user_home>/.aws/credentials, runawslogin switch -
If you have roles in different accounts with the same role names, you can use
--profile-name-format RoleName-AccountAlias, such that the profile names will include both role name and account alias. Alternatively, you can also changeDEFAULT_PROFILE_NAME_FORMATin the code toRoleName-AccountAlias.For example, if you have role ARNs like:
RoleArn, AccountAlias arn:aws:iam::123456789012:role/dev, aws-01 arn:aws:iam::123456789012:role/tst, aws-01 arn:aws:iam::213456789012:role/dev, aws-02 arn:aws:iam::313456789012:role/dev, aws-03
-
Install saml2aws. See also install-saml2aws.sh for Linux, or Install-saml2aws.ps1 for Windows.
-
Create
saml2awsconfig file (~/.saml2aws) by runningsaml2aws configure. -
Build and run
# Create and activate a new virtual env (optional)
virtualenv env
. env/bin/activate # (or env\Scripts\activate on Windows)
# Install and run
pip install -e .
awslogin --help
pip install -r requirements-build.txt
tox -r