Envoy jwt filter example
Example app using envoy jwt filter
Demo
- Download and install Docker Desktop
- Run
docker compose up
$ docker compose up- Go to login page
- Use
adminfor username and1234for password - Boom! You're authenticated
How it works
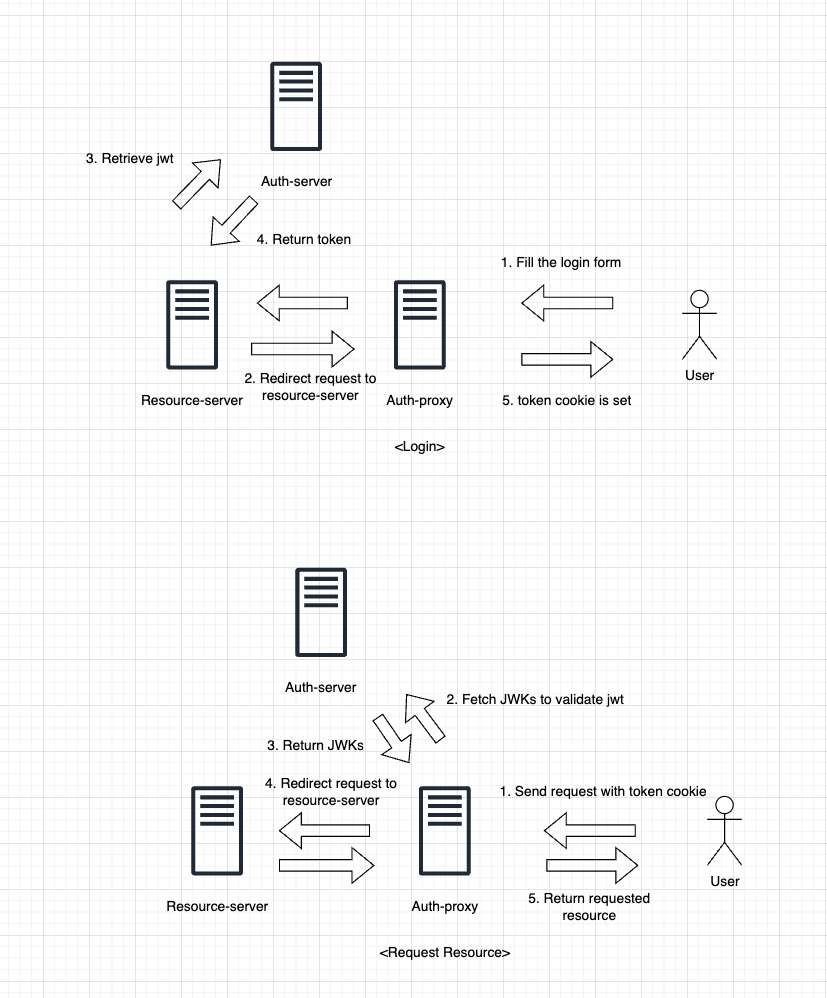
There are three components in this demo.
- auth-proxy
- auth-server
- resource-server
Auth-proxy uses envoy jwt filter to authenticate request, and it works as a reverse proxy for resource-server.
Auth-server provides two endpoints, one for getting JWTs and one for getting JWKs. Auth-proxy makes use of JWK endpoint to get public key for jwt verification.
Resource-server provides resources for end users or other services.
Below is a diagram explaining each user scenarios.
RBAC
There are two kind of roles in this example, admin and user.
If you log in using an admin account (username = admin, password = 1234), you'll be successfully redirected to private page.
However, if you use a user account (username = user-1234, password = 1234), you'll be redirected to "RBAC: access denied" page.
This can be accomplished using Envoy's rbac filter.