Red Team C2 Log Visualization
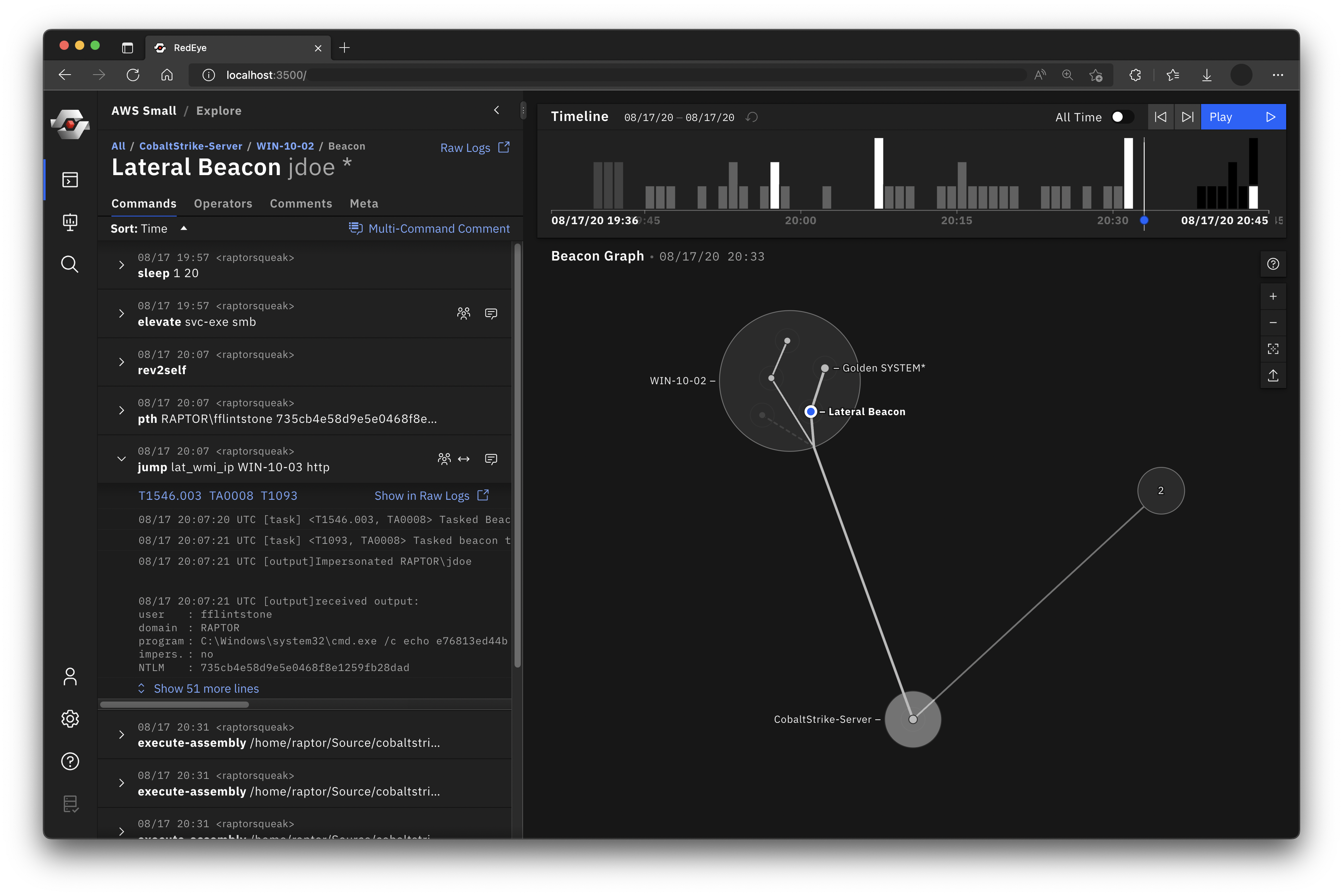
RedEye is an open-source analytic tool developed by CISA and DOE’s Pacific Northwest National Laboratory to assist Red Teams with visualizing and reporting command and control activities. This tool allows an operator to assess and display complex data, evaluate mitigation strategies, and enable effective decision making in response to a Red Team assessment. The tool parses logs, such as those from Cobalt Strike, and presents the data in an easily digestible format. The users can then tag and add comments to activities displayed within the tool. The operators can use the RedEye’s presentation mode to present findings and workflow to stakeholders.
RedEye can assist an operator to efficiently:
- Replay and demonstrate Red Team’s assessment activities as they occurred rather than manually pouring through thousands of lines of log text.
- Display and evaluate complex assessment data to enable effective decision making.
- Gain a clearer understanding of the attack path taken and the hosts compromised during a Red Team assessment or penetration test.
Follow along with the User Guide to learn about RedEye's feature set.
- Download the latest RedEye binaries for your OS* from the Releases page.
- Pick a mode and Run the server
- Red Team mode enables the full feature set: upload C2 logs, explore data, and create presentations. To start the server in Red Team mode, run the following in a terminal. You must provide a password to run in RedTeam mode.
AUTHENTICATION_PASSWORD=<your_password> ./RedEye --redTeam - Blue Team mode (default) enables a simplified, read-only UI for reviewing campaigns exported by a Red Team. To start the server in Blue Team mode. Double-click on the 'RedEye' executable or run
./RedEyefrom the command line.
- Red Team mode enables the full feature set: upload C2 logs, explore data, and create presentations. To start the server in Red Team mode, run the following in a terminal. You must provide a password to run in RedTeam mode.
- Use the web app in a browser at http://127.0.0.1:4000. The RedEye binary runs as a server in a terminal window and will automatically open the web app UI your default browser. You must close the terminal window to quit the RedEye server.
MacOS Issue - When running RedEye for the first time, you may get a "not verified" error. You must go to "System Preferences" > "Security & Privacy" > "General" and click "Open Anyway." More info on the apple support page.
RedEye has two modes that cover two stages of the Red Teaming process. Red Team mode allows importing C2 data, editing imported data, and making comments and presentations. After curating and annotating campaign data, Red Teams can export their campaign as a standalone .redeye file and hand it off to a Blue Team for reporting and remediation. Blue Team mode runs RedEye in a simplified read-only mode for viewing curated data exported by a Red Team.
Note: Both Red and Blue Team modes can be started from the same RedEye application binary.
The downloaded binary comes in two parts:
- The
RedEyeapplication binary - The
parsersfolder containing thecs-parserCobalt Strike log parser binary
There are three options to run RedEye in Red Team mode:
- Run the downloaded binary, passing in the
--redTeamand password options:AUTHENTICATION_PASSWORD=<your_password> ./RedEye --redTeam - Clone, install, and run the project directly (covered in the Local Build section).
- Docker Compose
- Clone the repo
- Update the environment variables in
docker-compose.yml. - Run:
docker-compose -f docker-compose.yml up -d redeye-core
The Blue Team mode is a simplified, read-only UI for displaying data that has been curated, annotated, and exported by a Red Team. This mode runs by default to make startup more simple for the Blue Team.
The Blue Team version can be run by double-clicking the 'RedEye' application binary. RedEye runs at http://127.0.0.1:4000 (by default) and will automatically open your default browser.
If a campaigns folder is located in the same directory as the RedEye application, RedEye will attempt to import any .redeye campaign files within. Campaign files can be exported in the Red Team mode.
To prepare a version for the Blue Team, follow these two steps:
- Copy the
RedEyeapplication binary to an empty folder. - Create a
campaignsfolder in the same directory and place the.redeyecampaign files you want to send inside.
Folder/
RedEye
campaigns/
Campaign-01.redeye
Campaign-02.redeye
.redeye files can also be uploaded in Blue Team mode via the "+ Add Campaign" dialog.
Type ./Redeye -h to view the options
-d, --developmentMode [boolean] put the database and server in development mode
-r, --redTeam [boolean] run the server in red team mode
-p, --port [number] the port the server should be exposed at
-t, --childProcesses [number] max # of child processes the parser can use
-h, --help display help for command
you can also configure the sever parameters in an .env file that sits next to the RedEye binary
AUTHENTICATION_PASSWORD=937038570
AUTHENTICATION_SECRET=supertopsecretdonttellanyone
DATABASE_MODE=DEV_PERSIST
SERVER_BLUE_TEAM=false
SERVER_PRODUCTION=false- Node.js >= v16
- Install yarn:
npm install -g yarn - Run:
yarn install// Installs all packages - Run either:
yarn release:allto build a binary for Linux, macOS, and Windowsyarn release:(mac|windows|linux).
- platform options:
- mac
- windows
- linux
Install Node.js >= v16 Install yarn globally via npm
npm install -g yarn
Install package dependencies
yarn install
Runs the project in development mode
yarn startIt is recommended to run the server and client in two separate terminals
yarn start:client...in another terminal
yarn start:serverto build a binary for Linux, macOS, and Windows
yarn release:allto build for a specific platform, replace all with the platform name
yarn release:(mac|windows|linux)- Linux
- Ubuntu 18 and newer
- Kali Linux 2020.1 and newer
- Others may be supported but are untested
- macOS
- El Capitan and newer
- Windows
- Windows 7 and newer ARM support is experimental