Checkov is a static code analysis tool for infrastructure-as-code. It scans cloud infrastructure provisioned using Terraform, Cloudformation or Kubernetes and detects security and compliance misconfigurations.
Checkov also powers Bridgecrew, the developer-first platform that codifies and streamlines cloud security throughout the development lifecycle. Bridgecrew identifies, fixes, and prevents misconfigurations in cloud resources and infrastructure-as-code files.


Table of contents
Features
- 300+ built-in policies cover security and compliance best practices for AWS, Azure & Google Cloud.
- Scans Terraform, AWS CloudFormation and Kubernetes configuration files.
- Detects AWS credentials in EC2 Userdata, Lambda environment variables and Terrafrom providers
- Policies support evaluation of variables to their optional default value.
- Supports in-line suppression of accepted risks or false-positives to reduce recurring scan failures. Also supports global skip from using CLI.
- Output currently available as CLI, JSON or JUnit XML.
Screenshots
Scan results in CLI
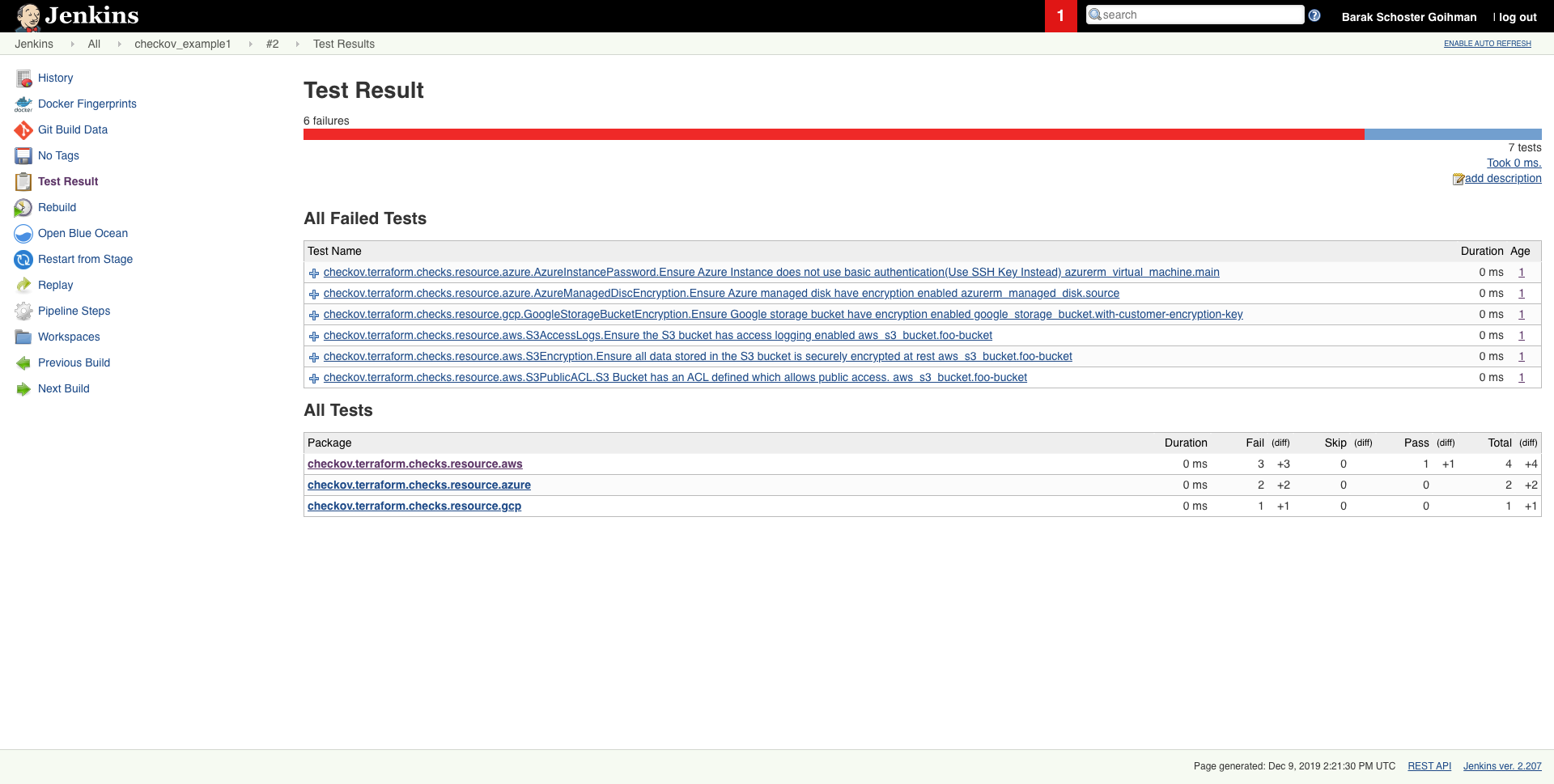
Scheduled scan result in Jenkins
Getting started
Installation
pip install checkovInstallation on Alpine:
pip3 install --upgrade pip && pip3 install --upgrade setuptools
pip3 install checkovor using homebrew (MacOS only)
brew tap bridgecrewio/checkov https://github.com/bridgecrewio/checkov
brew update
brew install checkovConfigure an input folder
checkov -d /user/path/to/iac/codeOr a specific file
checkov -f /user/tf/example.tfor
checkov -f /user/cloudformation/example.ymlScan result sample (CLI)
Passed Checks: 1, Failed Checks: 1, Suppressed Checks: 0
Check: "Ensure all data stored in the S3 bucket is securely encrypted at rest"
/main.tf:
Passed for resource: aws_s3_bucket.template_bucket
Check: "Ensure all data stored in the S3 bucket is securely encrypted at rest"
/../regionStack/main.tf:
Failed for resource: aws_s3_bucket.sls_deployment_bucket_name Start using Checkov by reading the Getting Started page.
Using Docker
docker pull bridgecrew/checkov
docker run -t -v /user/tf:/tf bridgecrew/checkov -d /tfSuppressing/Ignoring a check
Like any static-analysis tool it is limited by its analysis scope. For example, if a resource is managed manually, or using subsequent configuration management tooling, a suppression can be inserted as a simple code annotation.
Suppression comment format
To skip a check on a given Terraform definition block or CloudFormation resource, apply the following comment pattern inside it's scope:
checkov:skip=<check_id>:<suppression_comment>
<check_id>is one of the available check scanners<suppression_comment>is an optional suppression reason to be included in the output
Example
The following comment skip the CKV_AWS_20 check on the resource identified by foo-bucket, where the scan checks if an AWS S3 bucket is private.
In the example, the bucket is configured with a public read access; Adding the suppress comment would skip the appropriate check instead of the check to fail.
resource "aws_s3_bucket" "foo-bucket" {
region = var.region
#checkov:skip=CKV_AWS_20:The bucket is a public static content host
bucket = local.bucket_name
force_destroy = true
acl = "public-read"
}
The output would now contain a SKIPPED check result entry:
...
...
Check: "S3 Bucket has an ACL defined which allows public access."
SKIPPED for resource: aws_s3_bucket.foo-bucket
Suppress comment: The bucket is a public static content host
File: /example_skip_acl.tf:1-25
...To suppress checks in Kubernetes manifests, annotations are used with the following format:
checkov.io/skip#: <check_id>=<suppression_comment>
For example:
apiVersion: v1
kind: Pod
metadata:
name: mypod
annotations:
checkov.io/skip1: CKV_K8S_20=I don't care about Privilege Escalation :-O
checkov.io/skip2: CKV_K8S_14
checkov.io/skip3: CKV_K8S_11=I have not set CPU limits as I want BestEffort QoS
spec:
containers:
...Logging
For detailed logging to stdout setup the environment variable LOG_LEVEL to DEBUG.
Default is LOG_LEVEL=WARNING.
Skipping directories
To skip a whole directory, use the environment variable CKV_IGNORED_DIRECTORIES.
Default is CKV_IGNORED_DIRECTORIES=node_modules,.terraform,.serverless
Alternatives
For Terraform compliance scanners check out tfsec, Terrascan and Terraform AWS Secure Baseline.
For CloudFormation scanning check out cfripper and cfn_nag.
For Kubernetes scanning check out kube-scan and Polaris.
Contributing
Contribution is welcomed!
Start by reviewing the contribution guidelines. After that, take a look at a good first issue.
Looking to contribute new checks? Learn how to write a new check (AKA policy) here.
Disclaimer
checkov does not save, publish or share with anyone any identifiable customer information.
No identifiable customer information is used to query Bridgecrew's publicly accessible guides.
checkov uses Bridgecrew's API to enrich the results with links to remediation guides.
To skip this API call use the flag --no-guide.
Support
Bridgecrew builds and maintains Checkov to make policy-as-code simple and accessible.
Start with our Documentation for quick tutorials and examples.
If you need direct support you can contact us at info@bridgecrew.io .