An AWS Lambda function that sends data received from Chef Automate Data Tap to AWS Security Hub
Basic flow:
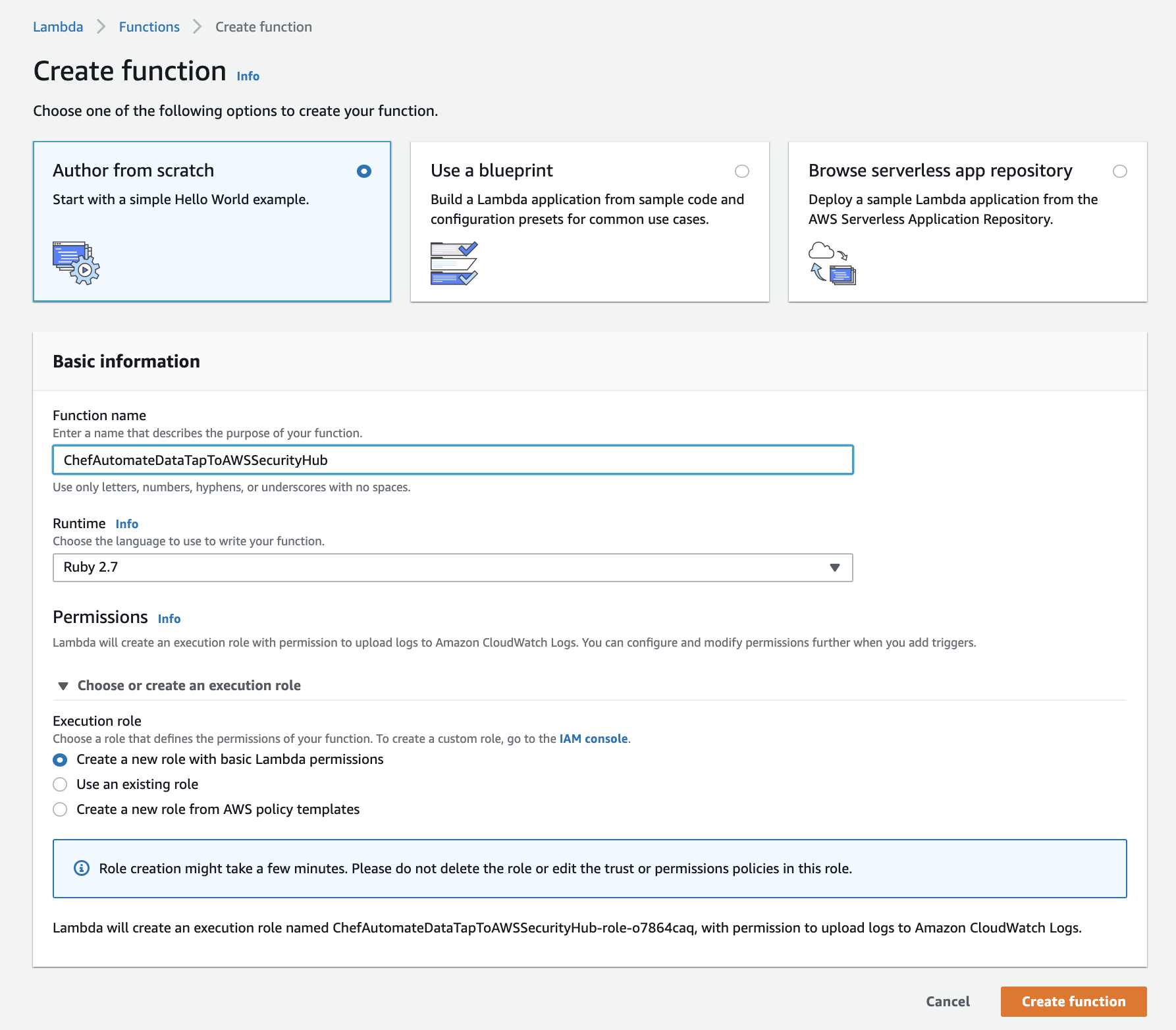
- Create an AWS Lambda function with lambda_function.rb to process Chef Infrastructure and Compliance Data and send it to the AWS Security Hub in the required ASFF format.
- Create an AWS API Gateway and Resouce/Method to connect the Lambda function in (1) to.
- Add the AWS API Gateway URL to a Chef Automate Data Tap.
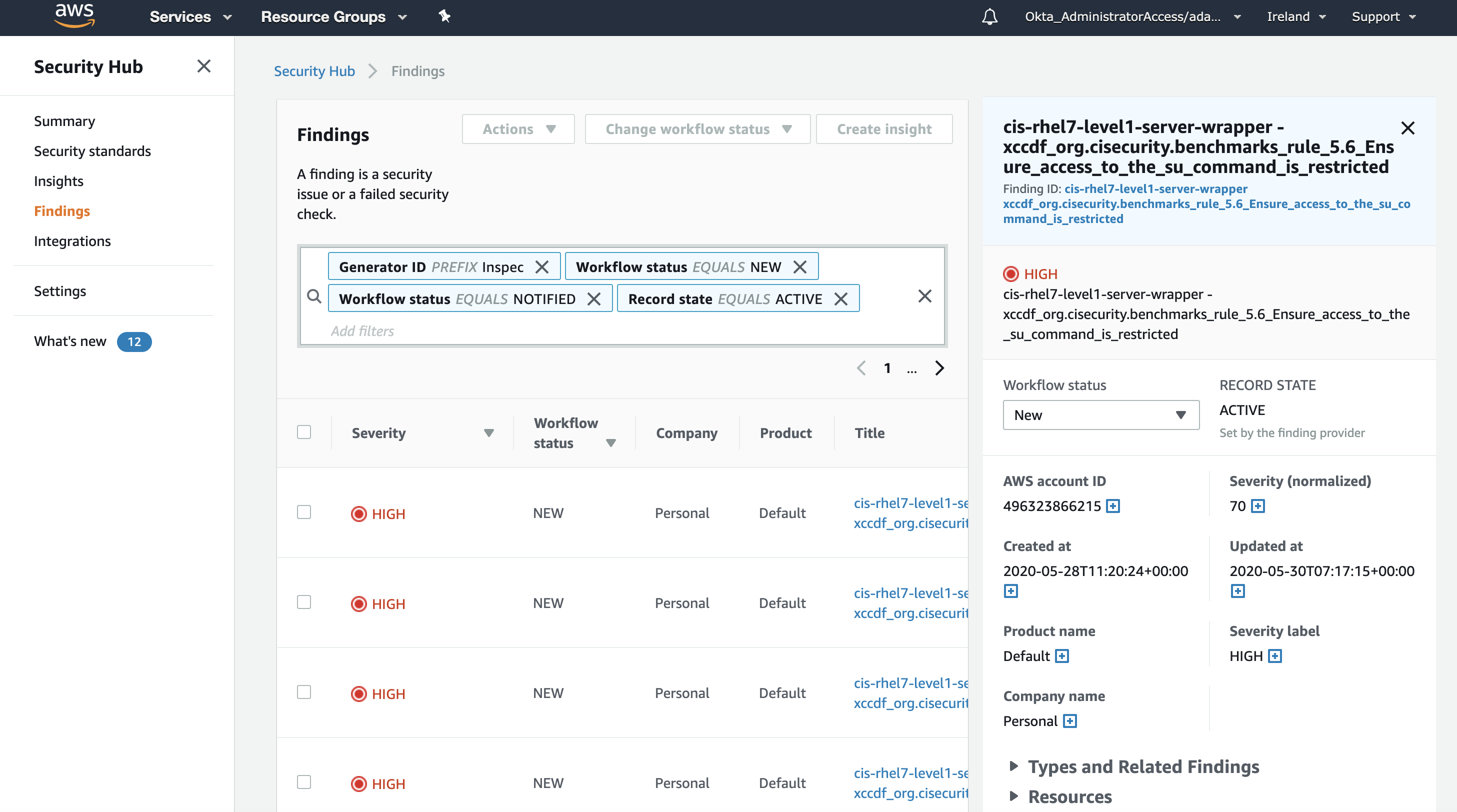
- View the Chef Infrastructure and Compliance Data in the AWS Security Hub.
Detailed Flow:
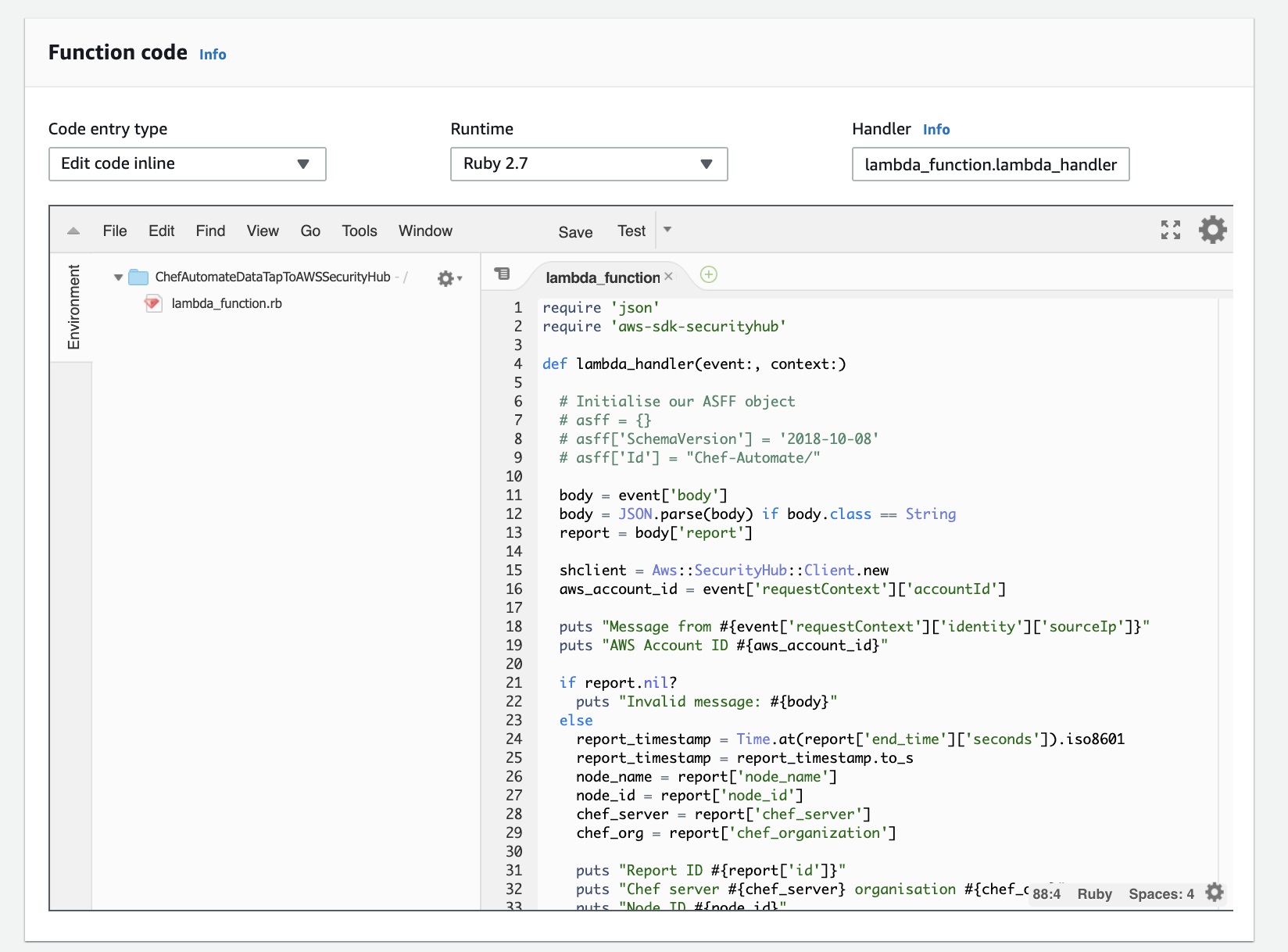
ii. Add the Ruby code (lambda_function.rb) to the function as below:
iii. Add a Policy to the Lambda's role to allow logging and reporting findings to the AWS Security Hub.
Select the Permissions tab and click the existing link under role name.
Click Attach policies Button, then Create policy
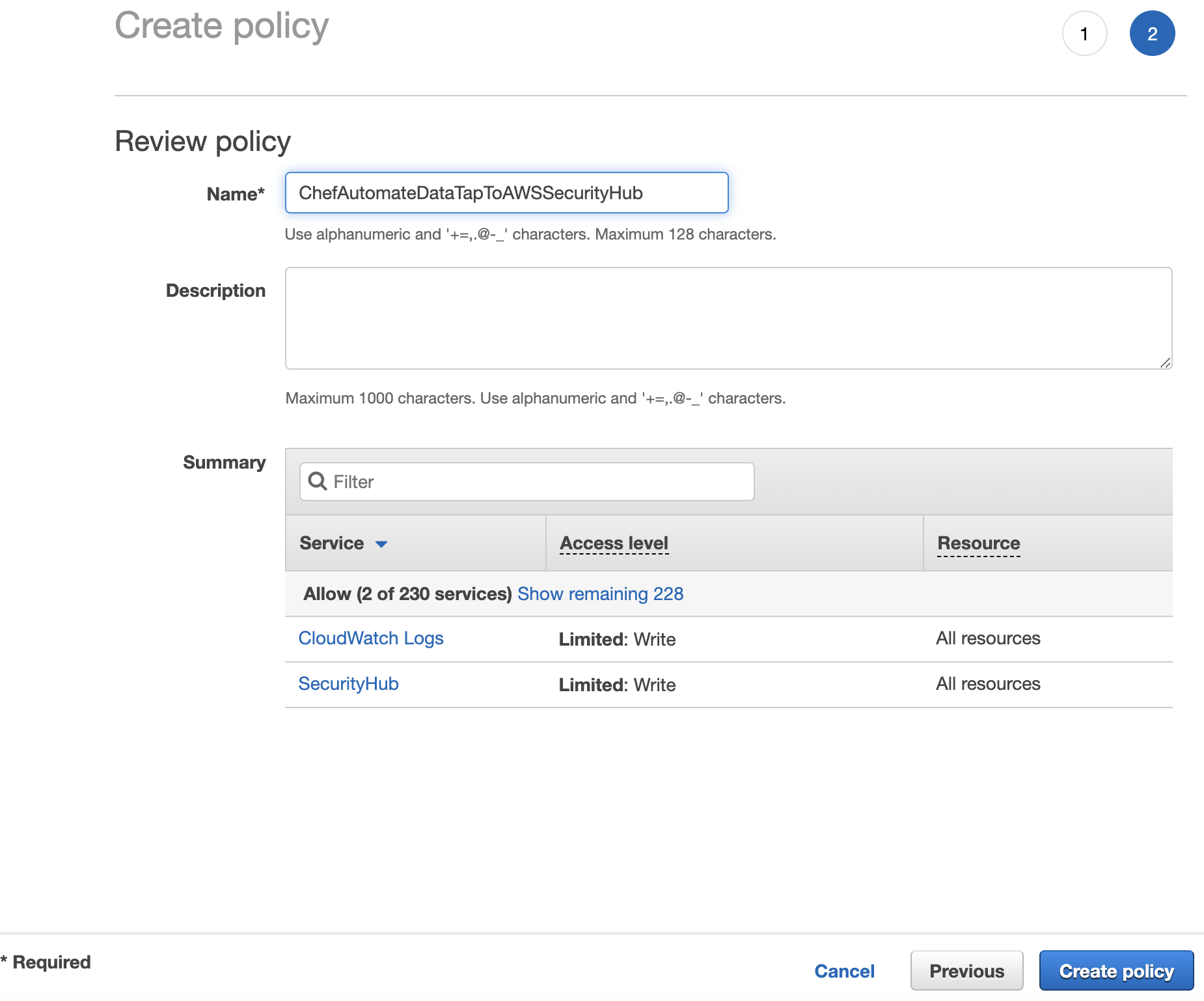
Add the policy below using the json editor
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:CreateLogStream",
"logs:CreateLogGroup",
"logs:PutLogEvents",
"securityhub:BatchImportFindings"
],
"Resource": "*"
}
]
}
Click Review policy
Click Create policy
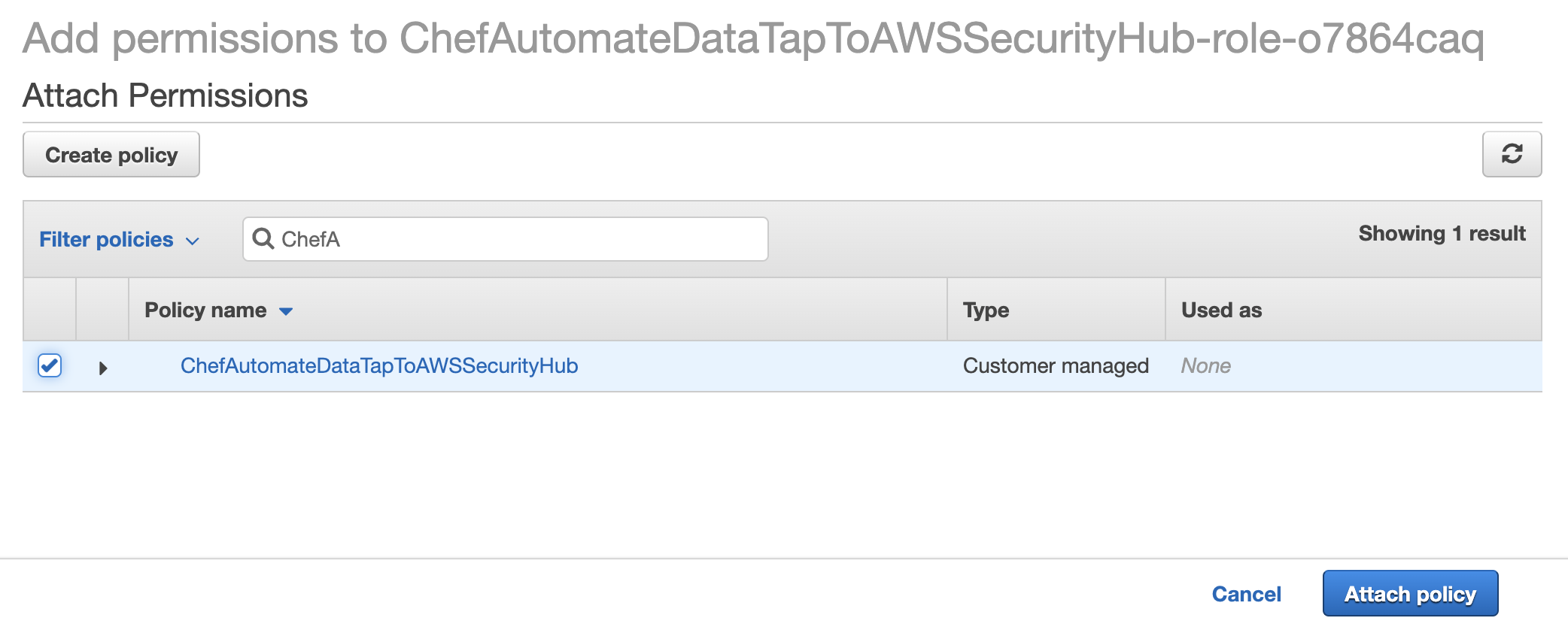
Search for your newly created policy attach it to your role
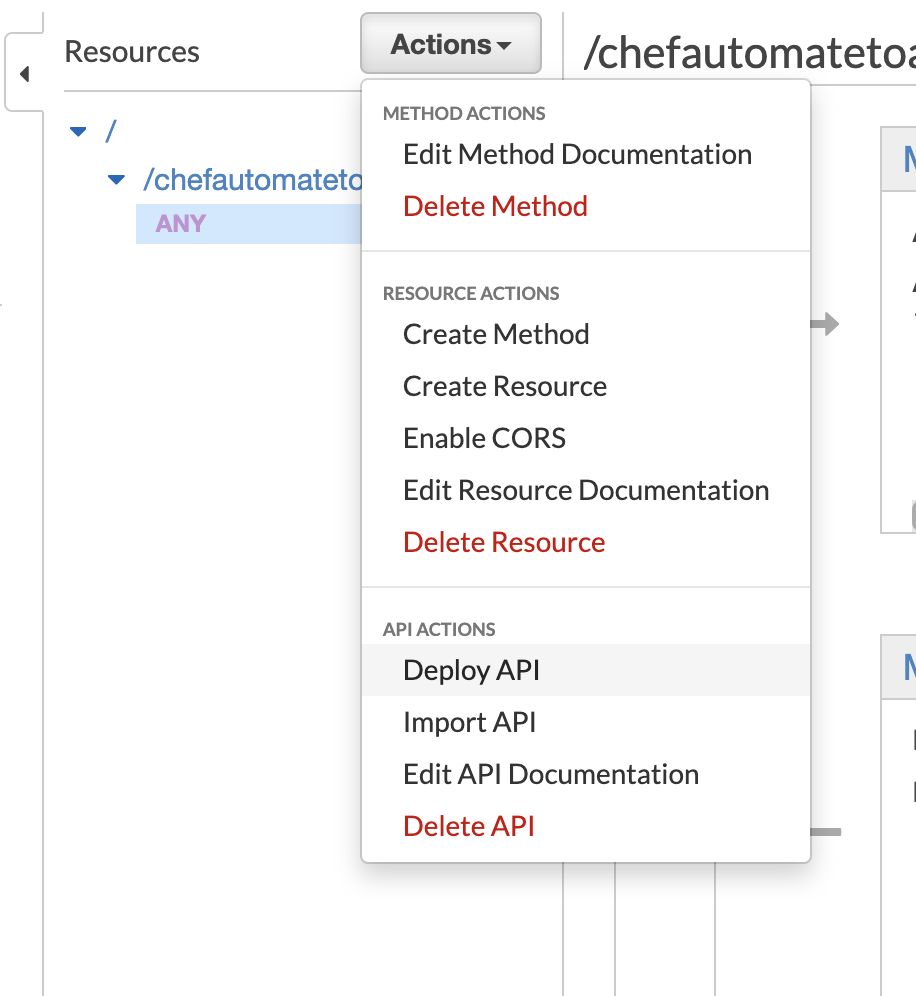
- Create an AWS API Gateway Configuration.
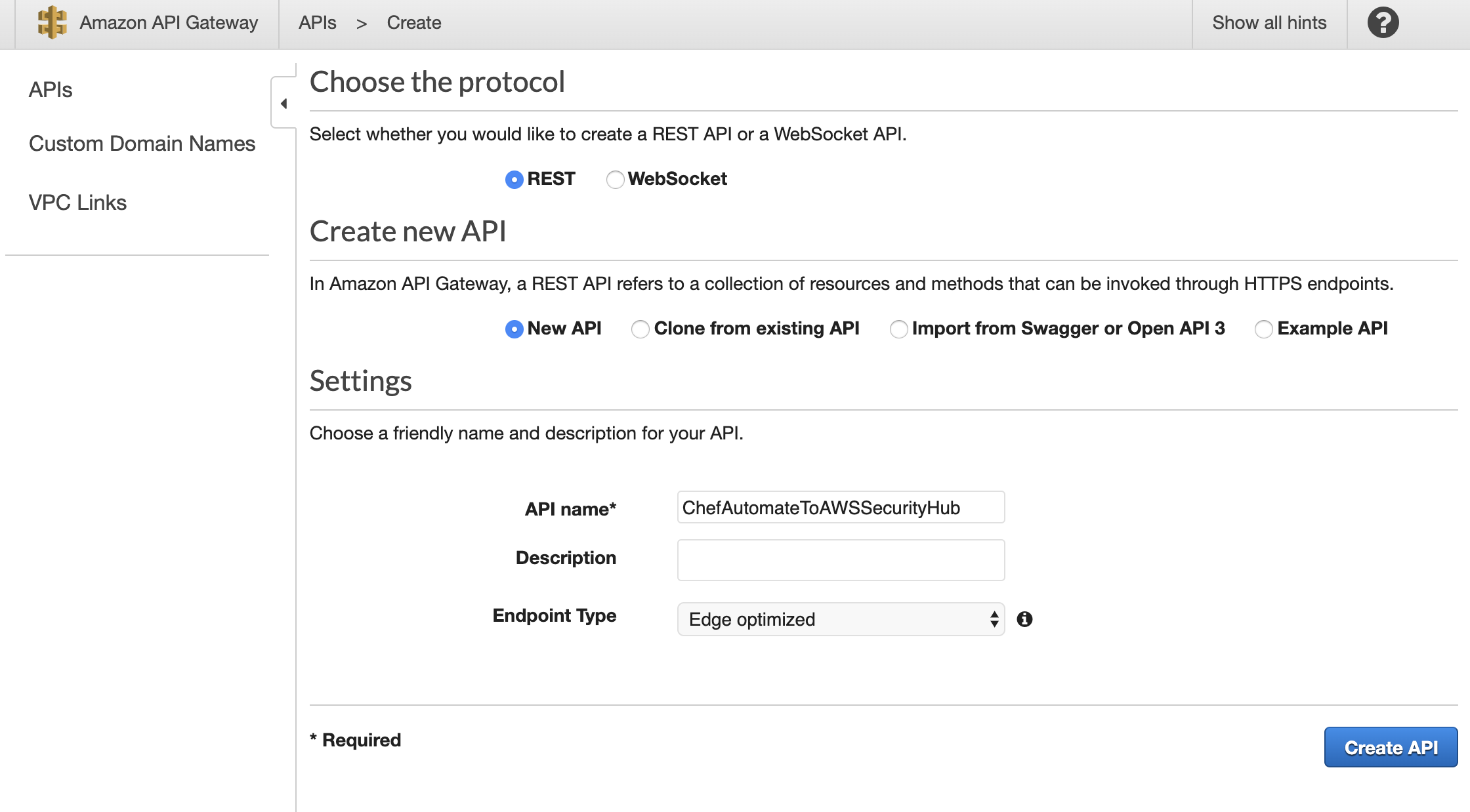
i. Create new API Gateway
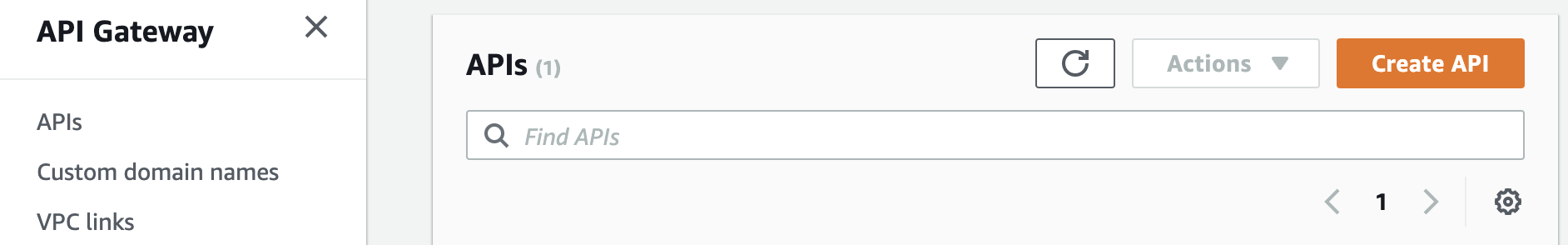
Select a Rest API and build.
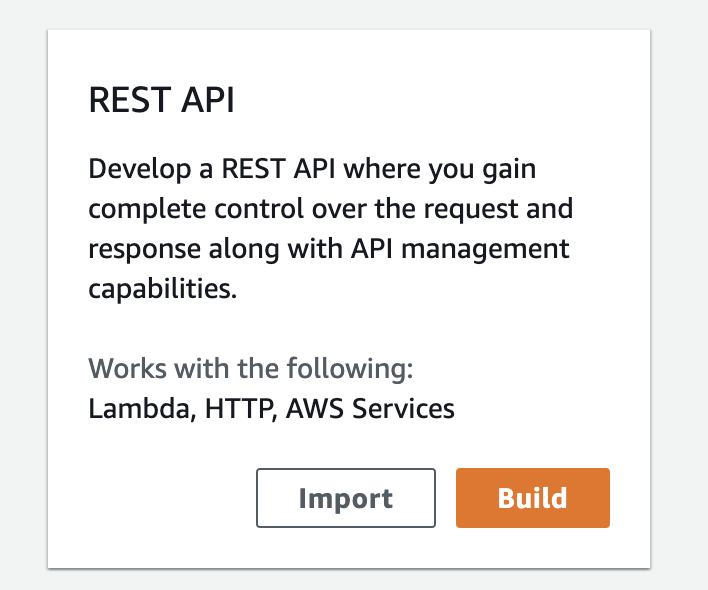
Configure as shown below and click Create API
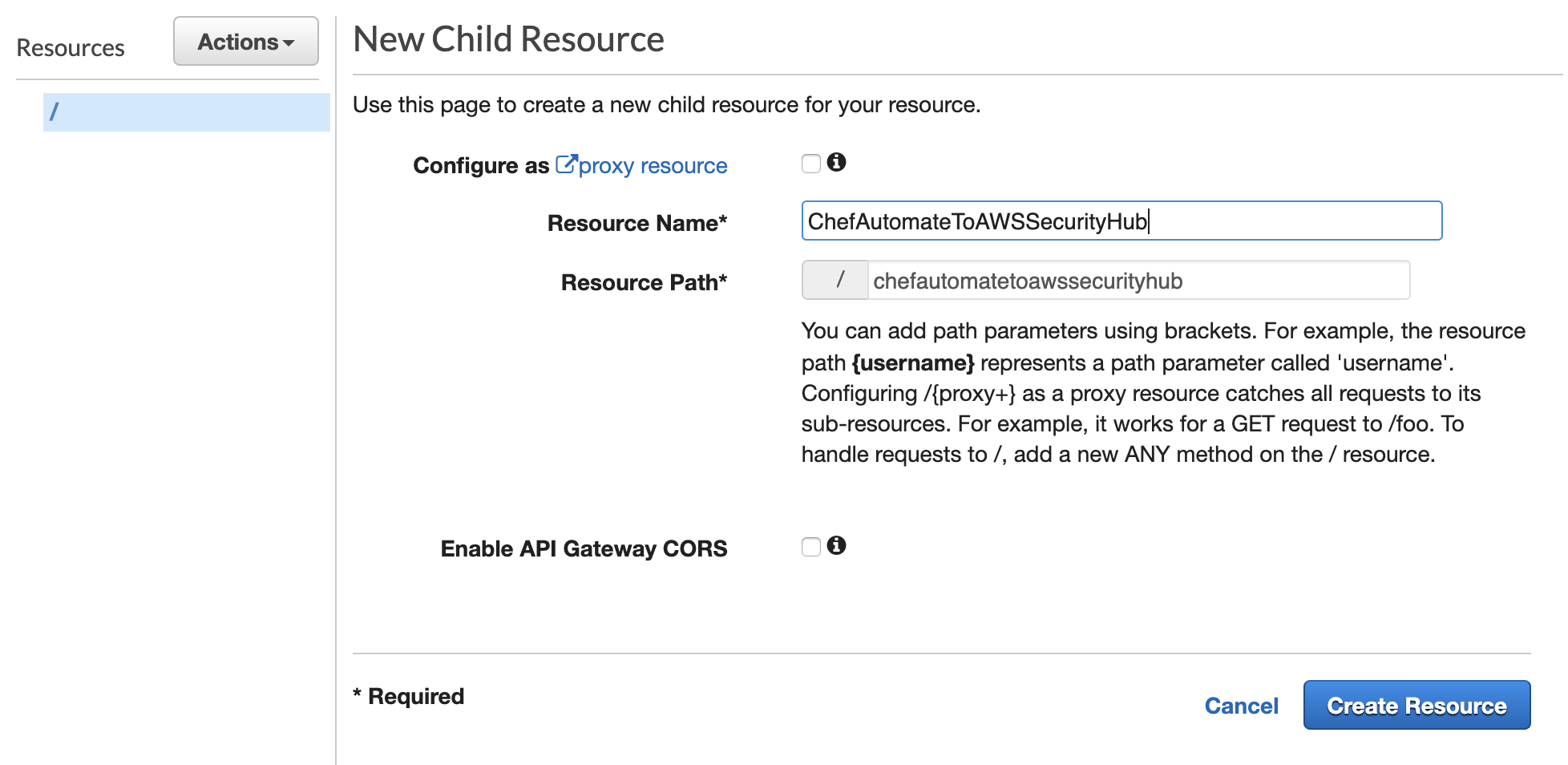
Select Actions, then Create Resource as below, click Create Resource
With the resource selected create a new method, select ANY and then tick the tick, as below:
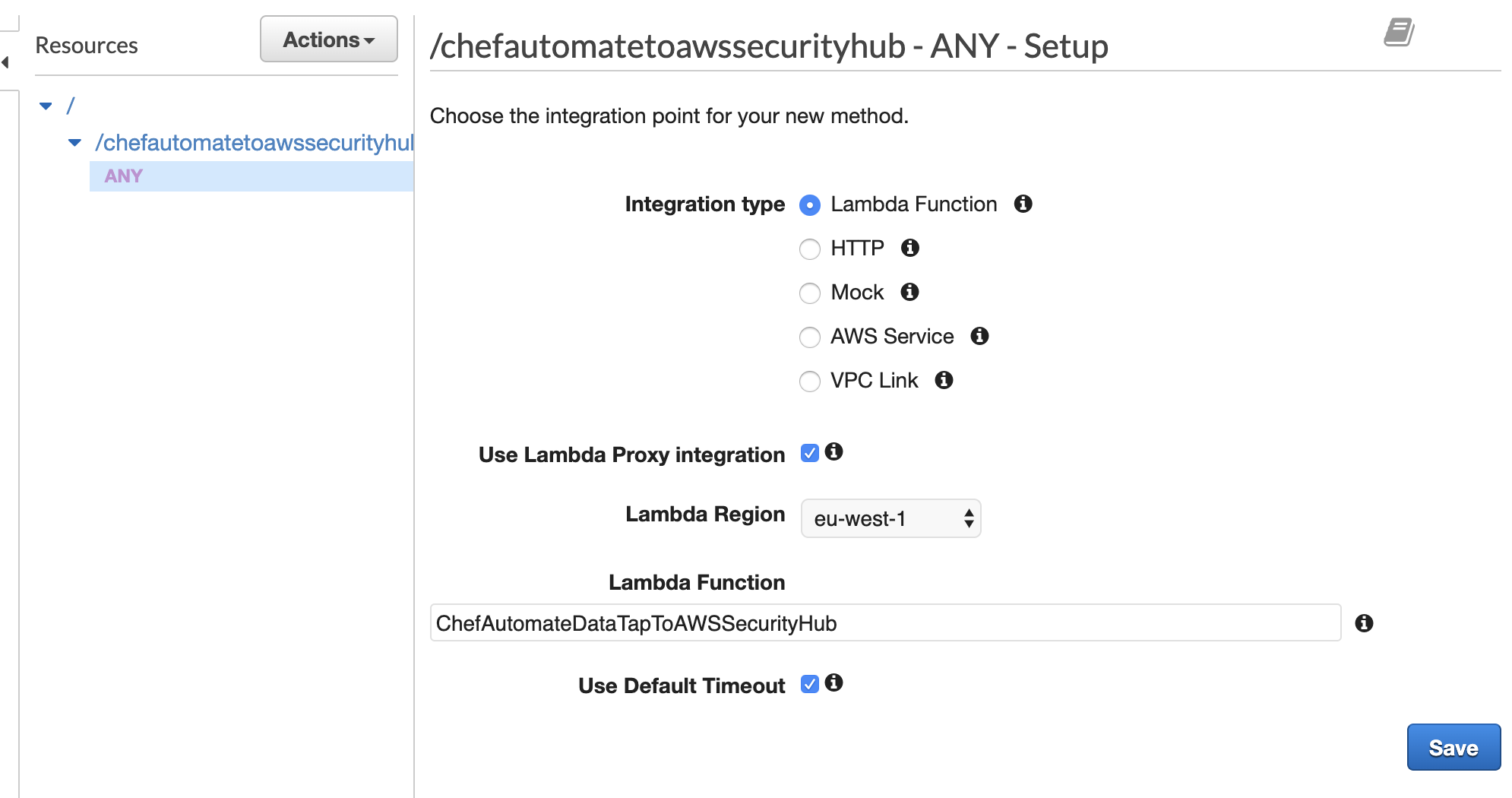
Fill in the Lambda details and hit save:
Say Ok to allow the gateway to have the permission to call your Lambda function.
Test your method if you want, you will see an error from the Lambda code, that is expected as there is no input data to work on, we will supply that later.
Create a new Deploy stage:
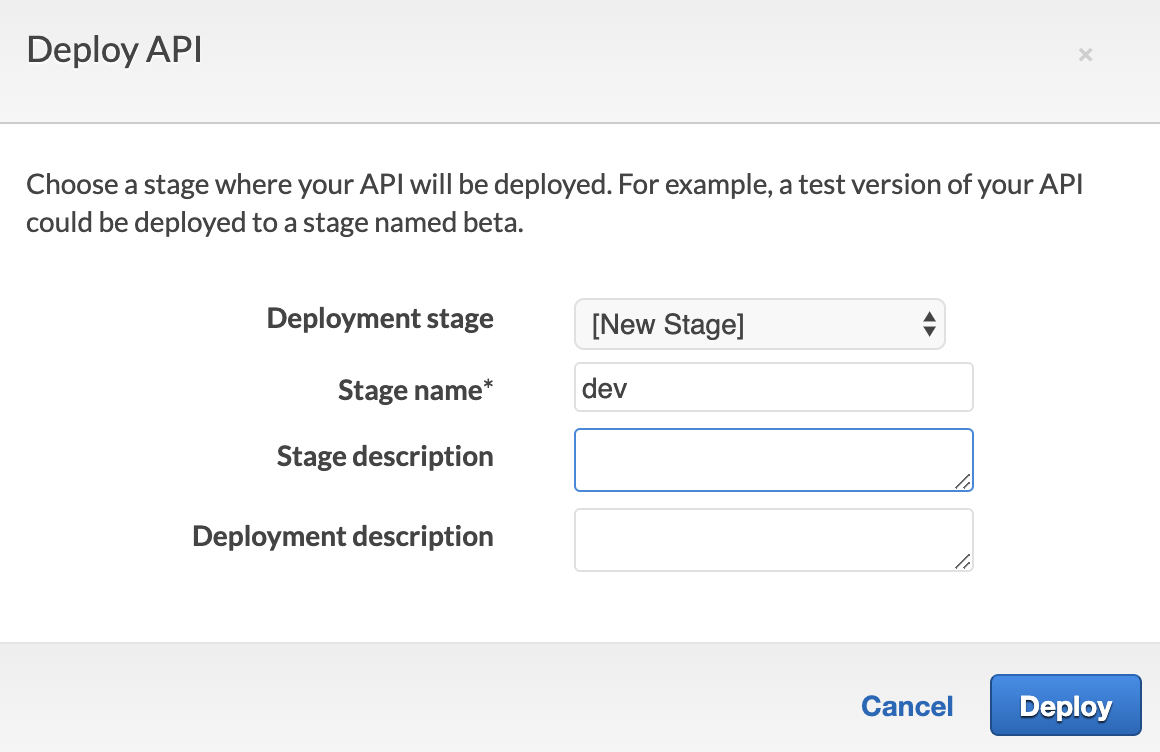
 Call it
Call it dev and hit Deploy
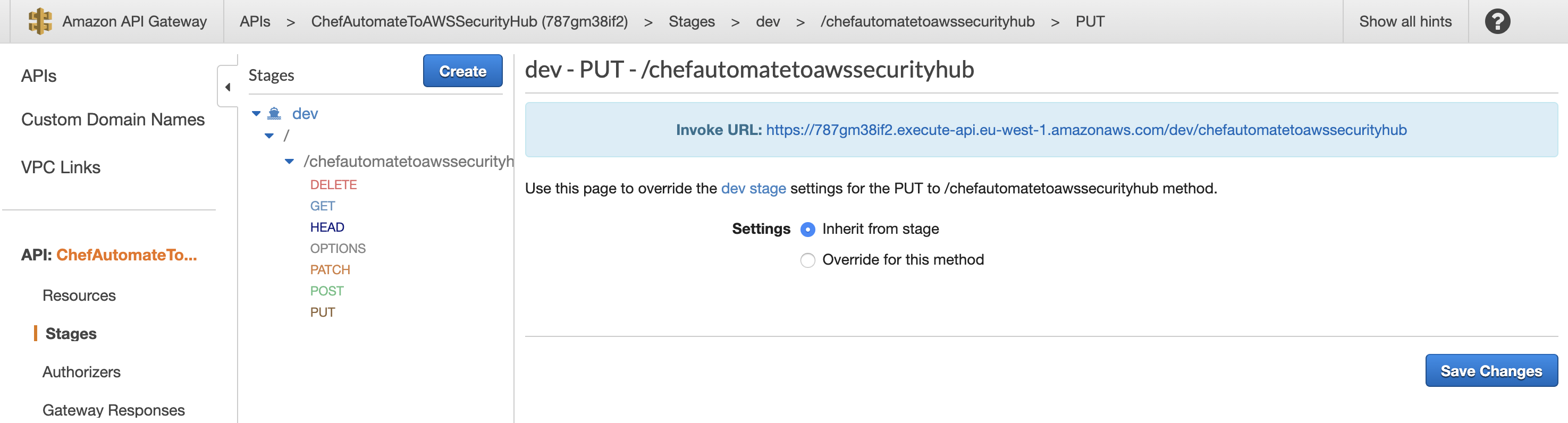
Select your stage and your resource and any of the methods (we choose to support ANY method to call our Lambda function in our setup).
You can see the URL required to invoke the API, make a copy ot it.
- Create a Data Tap in Chef Automate
i. Open your browser up and go to Chef Automate and select the settings tab -> Data Feeds. (If the menu item is not there then you may be using the beta version, type beta in the browser window and turn the Data Feed on, refresh the browser).
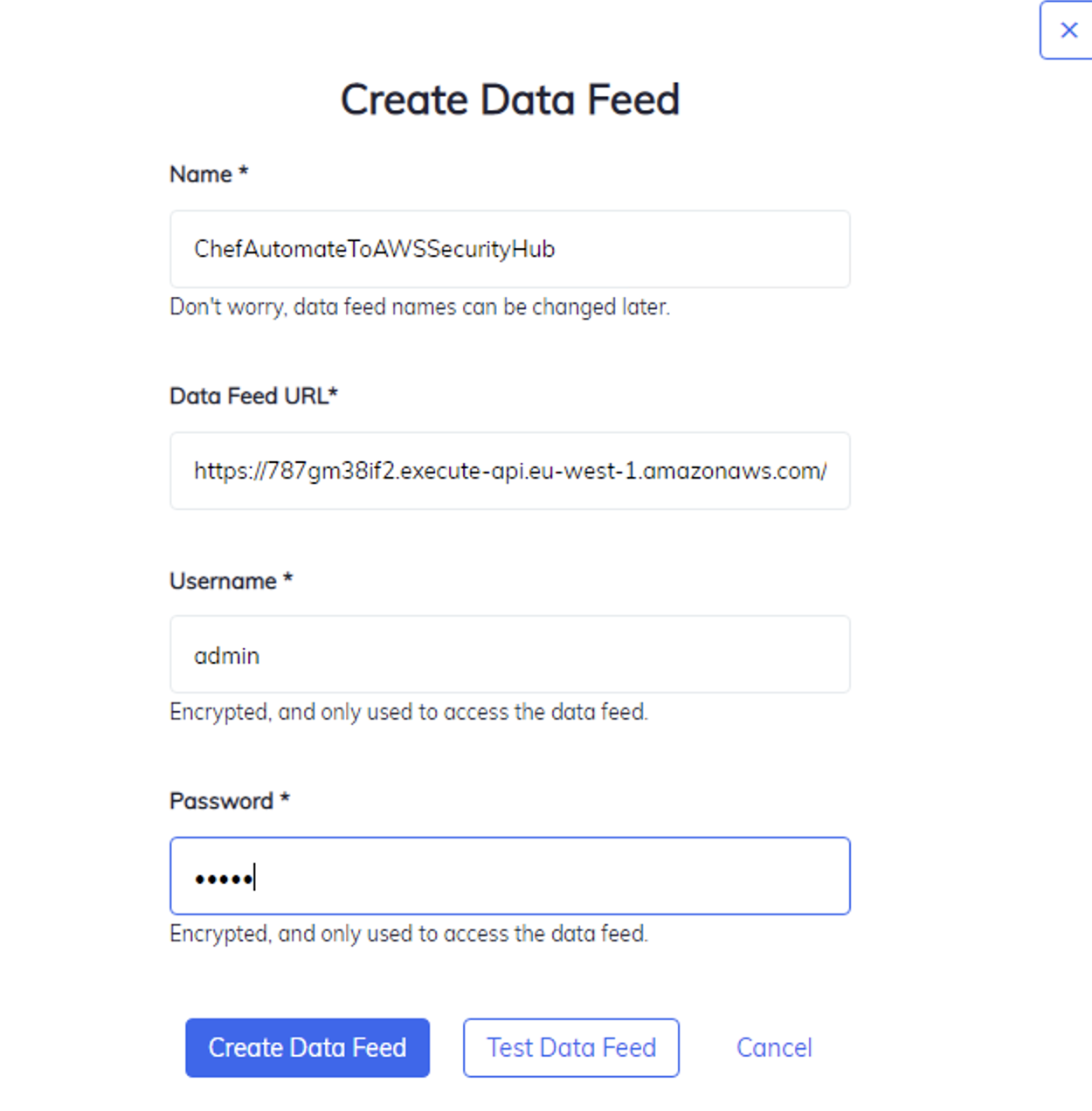
ii. Click Create Data Feed and fill in as below. You can put random stuff in the Username and Password fields, the Lambda function could be extended in the future to use them.
Click Create Data Feed
iii. Test your data feed, you should get a postive reply if all is set up properly
iv. Speed up the data interval and adjust the amount of node data sent.
ssh on to your Chef Automate machine and alter the config of the data feed.
Edit /hab/pkgs/chef/data-feed-service/1.0.0/20200506151626/default.toml.
Your version numbers may be different. Speed up the feed_interval and change the node_batch_size to 1
[service]
host = "localhost"
port = 14001
feed_interval = "3m"
asset_page_size = 100
reports_page_size = 1000
node_batch_size = 1
updated_nodes_only = false
disable_cidr_filter = true
cidr_filter = "0.0.0.0/0"
[tls]
key_contents =""
cert_contents = ""
root_cert_contents = ""
[mlsa]
accept = false
[log]
format = "text"
level = "info"
[storage]
database = "data_feed_service"
Stop the data_feed service (it will auto restart)
hab svc stop chef/data-feed-service
hab svc status
Note in future versios of Chef Automate you will be able to adust the Chef Automate config to set this.