NOTE: All tools should be run from ISE as administorator unless otherwise noted.
Kindly be advised that this code is being offered as-is and Dell will not provide any support in using these tools. However, if you encounter any issues, we would appreciate it if you could submit them under the "Issues" section.
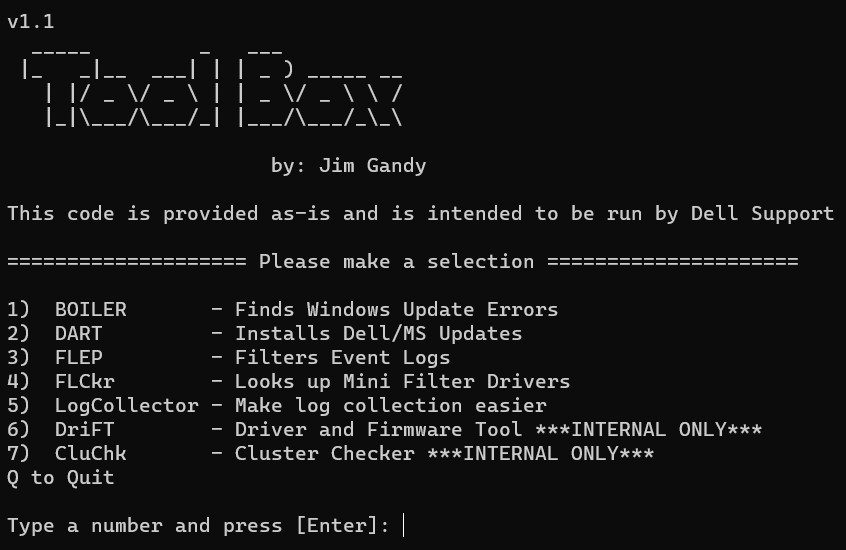
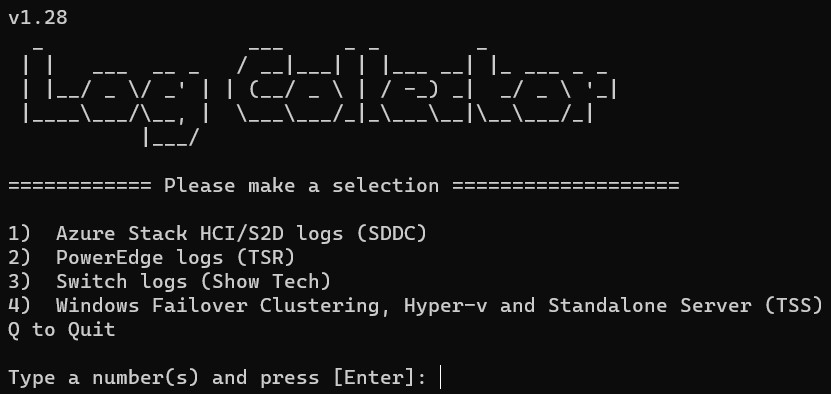
Tool Box is a menu of all the tools to run them from one place
Copy the below powershell code and paste into PowerShell
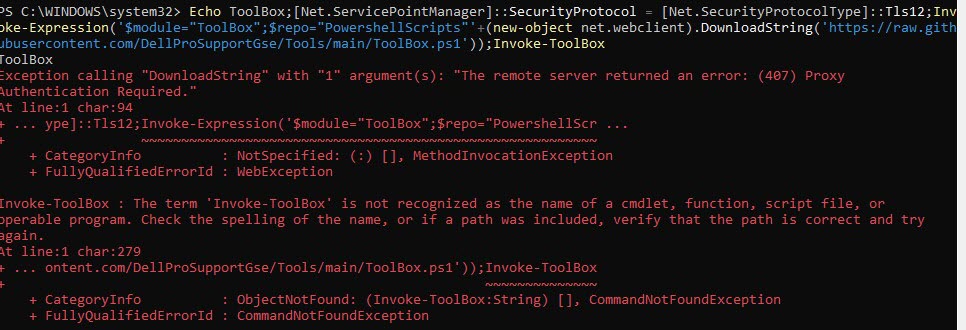
Echo ToolBox;[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="ToolBox";$repo="PowershellScripts"'+(new-object net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/ToolBox.ps1'));Invoke-ToolBox$browser = New-Object System.Net.WebClient
$browser.Proxy.Credentials =[System.Net.CredentialCache]::DefaultNetworkCredentials
This script checks the URLs that the Azure Stack HCI operating system may need to access as per Microsoft Doc: https://docs.microsoft.com/en-us/azure-stack/hci/concepts/firewall-requirements
Copy the below powershell code and paste into PowerShell
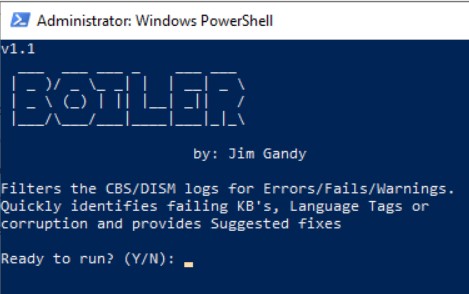
Echo AzHCIUrlChecker;[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="AzHCIUrlChecker";$repo="PowershellScripts"'+(new-object net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/AzHCIUrlChecker.ps1'));Invoke-AzHCIUrlCheckerFilters the CBS/DISM logs for Errors/Fails/Warnings to quickly identify failing KB's, Language Tags or corruption plus, it provides Suggested fixes.
1. Copy/Paste PowerShell code below
2. Answer the Rady to run? Y/N
3. Provide the log to analize in the popup
- Supports running locally or remotly by feeding it a ZIP file of the logs or just log file.
4. Review the output for the finds and suggested fixes
- Failing KBs
Shows any KBs that are failing to install, provides the link to download them if available and the how to DISM install it for best success.
- Failing Language Packs
Shows any language tag that is failing with the process to download and install to repair it
- Corruption identified by the log
Show any corruption identified in the log and the steps to restore health with eval ISO
- Display Errors, Fails and Warnings
If no other scenario is found but we still see Errors, Fails and Warnings then they are displayed
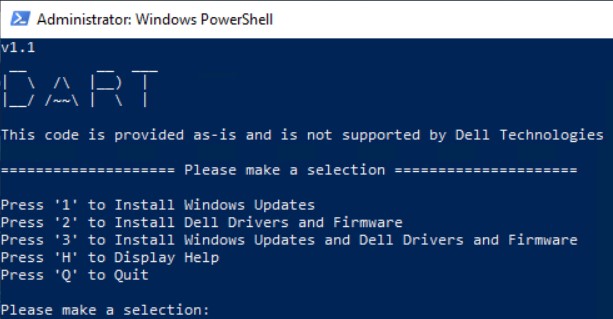
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="BOILER";$repo="PowershellScripts"'+(new-object net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/BOILER.ps1'));Invoke-BOILERDell Automated seRver updaTer is a Windows Failover Cluster and HCI/S2D aware tool that will automatically download and install Windows Updates, Drivers/Firmware on Dell Servers.
How To Use: From PowerShell as admin execute the following:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="DART";$repo="PowershellScripts"'+(new-object net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/DART.ps1'));Invoke-DART- Checks to make sure your running on a Dell server
- Checks to see if have the latest Dell System Update is installed
- If not then it downloads and installs the latest version of DSU
- Is Azure Stack HCI (Storage Spaces Direct Ready Node or AX node)
- We download and extract the AZHCI-Catalog to use with DSU
- We Pause & Drain the node and Enable Storage Maintenance Mode
- Installs Windows Updates
- Runs DSU
- No reboot required: We resume the node, disable Storage Maintenance Mode and show Installation Report
- Reboot Required: We setup a logon task that will resume the node and disable Storage Maintenance Mode after the reboot and logon
- Failed Update: We show you the failed update and exit so we can look into the errors and decide how to proceed.
- Is Cluster member
- We Pause & Drain the node and Enable Storage Maintenance Mode
- Installs Windows Updates
- Runs DSU
- No reboot required: We resume the node and show Installation Report
- Reboot Required: We setup a logon task that will resume the node after the reboot and logon
- Failed Update: We show you the failed update and exit so we can look into the errors and decide how to proceed.
- Is Regular Power Edge Server
- Installs Windows Updates
- Runs DSU
- No reboot required: Show Installation Report
- Failed Update: We show you the failed update and exit so we can look into the errors and decide how to proceed.
Transcript Logging: C:\ProgramData\Dell\DART
Use -IgnoreChecks:$True to install updates without suspending cluster node or enabling storage maintenance mode for Azure Stack HCI
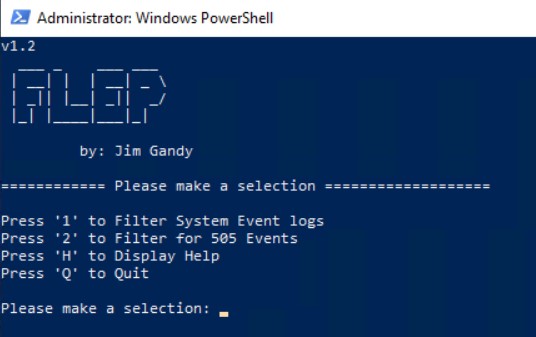
This tool is used to filter Windows event logs.
1 Filter System Event logs
Filters the system event log for the 24 most common events 13,20,28,41,57,129,153,134,301,1001,1017,1018,1135,5120,6003-6009
2 Filter for 505 Events
Filters the Microsoft-Windows-Storage-Storport/Operational event logs for event id 505 to be able to see S2D/HCI storage latancy buckets
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="FLEP";$repo="PowershellScripts"'+(new-object net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/FLEP.ps1'));Invoke-FLEPThis tool is used to collect all the logs Switches, Servers and OS
How To Use: From PowerShell as admin execute the following and follow the prompts:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="LogCollector";$repo="PowershellScripts"'+(new-object System.net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/LogCollector.ps1'));Invoke-LogCollectorThis tool is used to collect Dell switch logs
How To Use: From PowerShell as admin execute the following and follow the prompts:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="GetShowTech";$repo="PowershellScripts"'+(new-object System.net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/GetShowTech.ps1'));Invoke-GetShowTechHow To Use: From ISE or PowerShell as admin execute the following:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="SDDC";$repo="PowershellScripts"'+(new-object net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/RunSDDC.ps1'));Invoke-RunSDDC- From a machine that has Internet access, download the SDDC master file from here: https://github.com/DellProSupportGse/PrivateCloud.DiagnosticInfo/archive/master.zip
- Right click and copy the downloaded file.
- Connect to a node of the cluster using RDP.
- If Sconfig launches, select option 15 to exit to Powershell.
- Type notepad at the prompt to launch Notepad.
- From the File menu, select Save As.
- Browse to the folder where you wish to save the master.zip file and type Ctrl-V to paste it into the folder.
- Return to the machine with Internet access and browse to https://github.com/DellProSupportGse/Tools.
- Click SDDCOffline.ps1.
- Near the upper-right corner of the code window, click Raw to view only the PowerShell code.
- Type Ctrl-A to select the complete PowerShell script, then Ctrl-C to copy it.
- Return to the RDP session on the cluster node and paste the copied text directly into PowerShell.
- Press Enter to begin running the script.
- Type y at the Ready to run? prompt.
- Any previous versions of the SDDC tool will be removed automatically.
- Type y again when asked if the SDDC has been copied locally.
- Browse to the C:\Dell folder and select the zipped SDDC master file. Click Open.
- The offline SDDC tool will be extracted to all nodes, and data collection will begin. This will take several minutes.
- When prompted, type y to remove the downloaded SDDC master file or n to retain it.
- The zipped output file will be located in C:\users<current user>\ and will have a name that begins with HealthTest.
- From a machine that has Internet access, download the SDDC master file from here: https://github.com/DellProSupportGse/PrivateCloud.DiagnosticInfo/archive/master.zip
- Right click and copy the downloaded file.
- Connect to a node of the cluster using RDP.
- If Sconfig launches, select option 15 to exit to Powershell.
- Type notepad at the prompt to launch Notepad.
- From the File menu, select Save As.
- Browse to the folder where you wish to save the master.zip file and type Ctrl-V to paste it into the folder.
- Return to the machine with Internet access and browse to https://github.com/DellProSupportGse/Tools.
- Click SDDCOffline.ps1.
- Near the upper-right corner of the code window, click Raw to view only the PowerShell code.
- Type Ctrl-A to select the complete PowerShell script, then Ctrl-C to copy it.
- Return to the RDP session on the cluster node and paste the copied text directly into PowerShell.
- Press Enter to begin running the script.
- Type y at the Ready to run? prompt.
- Any previous versions of the SDDC tool will be removed automatically.
- Type y again when asked if the SDDC has been copied locally.
- Browse to the C:\Dell folder and select the zipped SDDC master file. Click Open.
- The offline SDDC tool will be extracted to all nodes, and data collection will begin. This will take several minutes.
- When prompted, type y to remove the downloaded SDDC master file or n to retain it.
- The zipped output file will be located in C:\users<current user>\ and will have a name that begins with HealthTest.
This tool is used to collect TSRs from all nodes in a cluster"
How To Use: From ISE or PowerShell as admin execute the following:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="TSRCollector";$repo="PowershellScripts"'+(new-object net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/TSRCollector.ps1'));Invoke-TSRCollectorFLtmc Checker This tool lookups up filter drivers in Microsoft's known good list URL: https://raw.githubusercontent.com/MicrosoftDocs/windows-driver-docs/staging/windows-driver-docs-pr/ifs/allocated-altitudes.md
How To Use: From ISE or PowerShell as admin execute the following and follow the prompts:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="FLCkr";$repo="PowershellScripts"'+(new-object System.net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/FLCkr.ps1'));Invoke-FLCkrConvert ETL network traces to PCap for use with WireShark
Copy the below powershell code and paste into PowerShell
Echo ToolBox;[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="Convert-Etl2Pcap";$repo="PowershellScripts"'+(new-object net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/Convert-Etl2Pcap.ps1'));Invoke-ETL2PCAPConvert a folder to ISO
Copy the below powershell code and paste into PowerShell
Echo MakeIso;[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-Expression('$module="MakeIso";$repo="PowershellScripts"'+(new-object net.webclient).DownloadString('https://raw.githubusercontent.com/DellProSupportGse/Tools/main/isomaker.ps1'));Invoke-MakeISOIf you run into any problems or would like to provide feedback, please open an issue here https://github.com/DellProSupportGse/Tools/issues