Disassemble ANY files including android shared libraries (aka .so files) (NDK, JNI), windows PE files(EXE, DLLs, SYSs, etc..), linux executables, object files, ANY files you want like pictures, audios, etc(for fun) entirely on Android. Capstone-based disassembler application on android.
Version 1.6.0 pre-release!
- Shows details of elf files.
- Shows symbol table(functions or objects' ,... names) of elf files.
- Disassembles the code sections.
- Has various export options of the disassembly. (Reloadable raw file, compilable txt file, analytic text files, json, and reloadable database)
- Supports projects.
- Supports directly launching from file browsers.
- Supports many ABIs(arm,x86,x64,MIPS,PowerPC,...)
- Jump to address by symbols' names, or a hex address.
- Syntax colorizing.
- Support PE and other bin formats.
- Sort symbols if needed.
- No need to press
Disassemblebutton! - Colorize PUSH/POP instructions.
- Colorize ARM arch instructions better.
- Added Follow Jump menu for jump instructions.(With BackStack)
- Can override auto parse setup
- You can copy an instruction to the clipboard.
- It now parses IAT, EAT of PE headers.
- You can now choose the columns to view.
- Supports analyzing system files(which are not accessible without root permission) for rooted phones.
- Friendlier message for non-parsable files.
- The storage chooser now retains the session, so that it remembers the last browsed folder.
- Added Hex View and utility calculator.
- Theme installation is automated.
- Choose which binary to analyze when the zip/apk has multiple binaries.
- Choose APK from installed
- Search for strings in the binary (Unfortunately only for ascii characters)
- Bytewise analysis (mean, hashes, entropy, g-test, chi-test, autocorrelation) to help determine if the file is encrypted
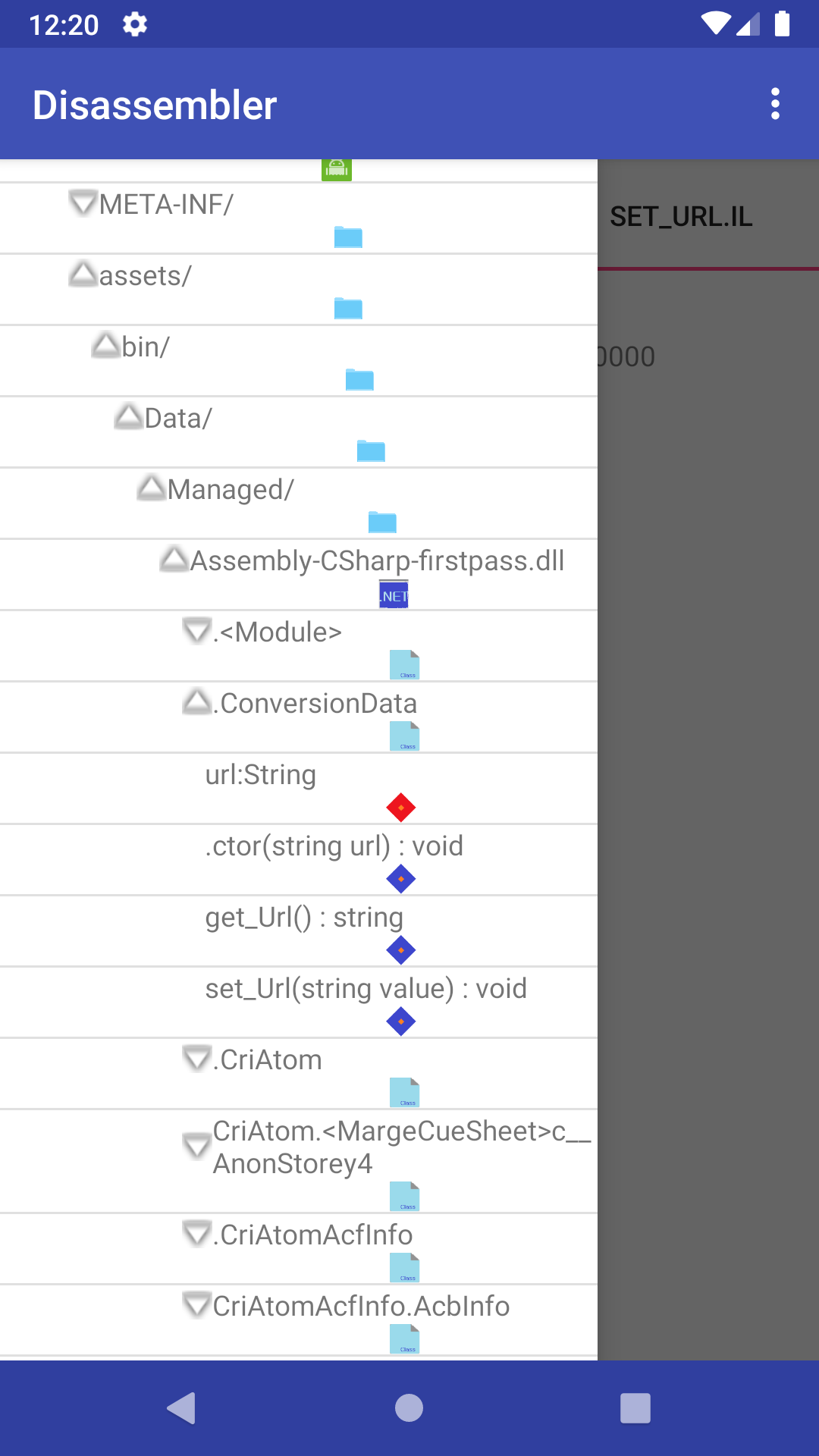
- Support .NET assemblies
- Support dex files
Good themes usually help you recognize some important instructions easily.
-
Browse to a file to analyze.
The app automatically digs into
.zip, .apk, .dexand.NET assemblyfiles! -
You can just click to see the disassembled
.smalifiles. -
Just by opening a .NET file like a folder, you can browse the symbols and methods defined.
-
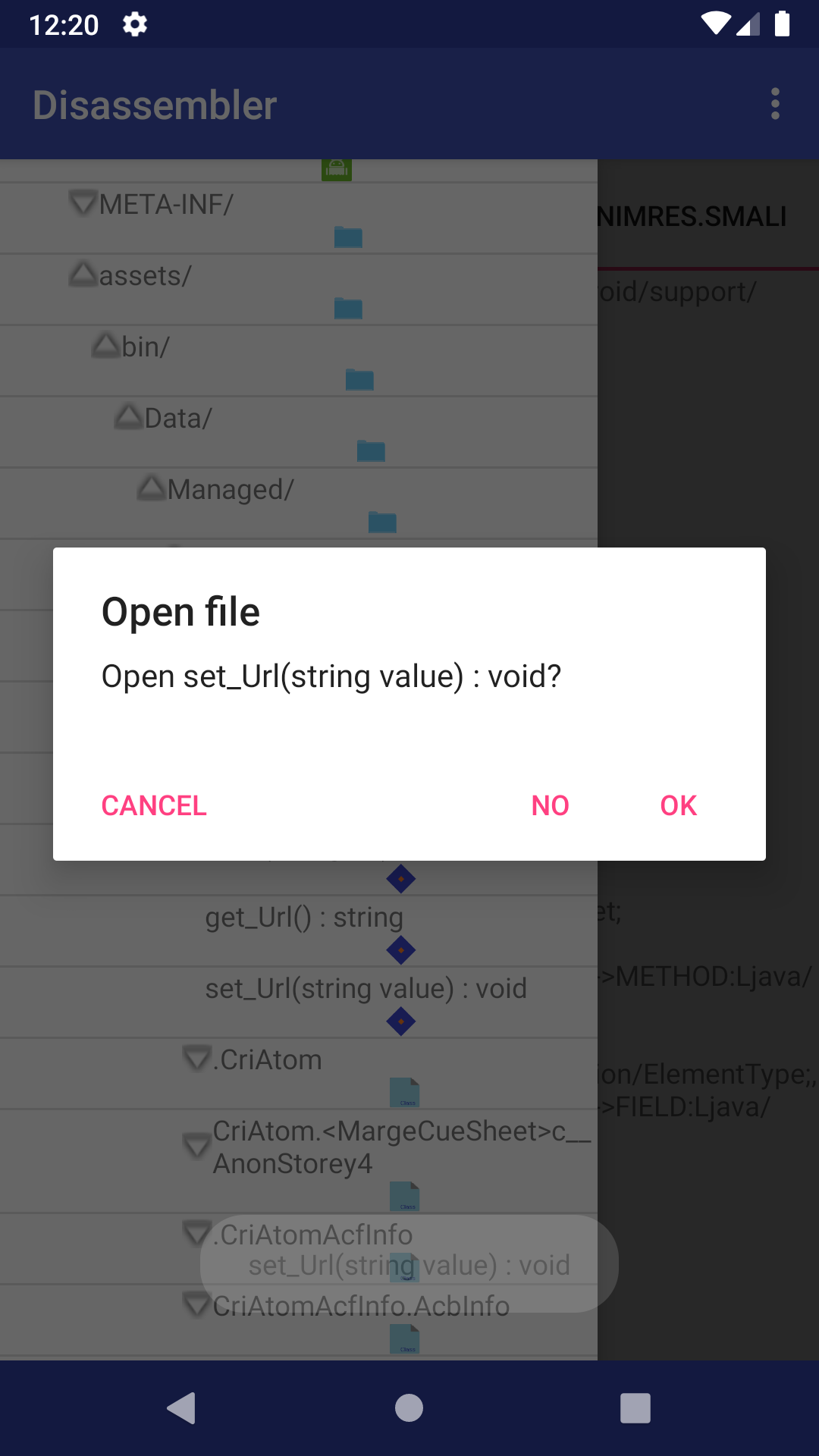
You can view the decompiled
.smalior.ilfiles by clicking the method name.
- To change chooser, go to settings and change.
- Go to details tab.
- Press
Show detailsbutton to see details. (ELF)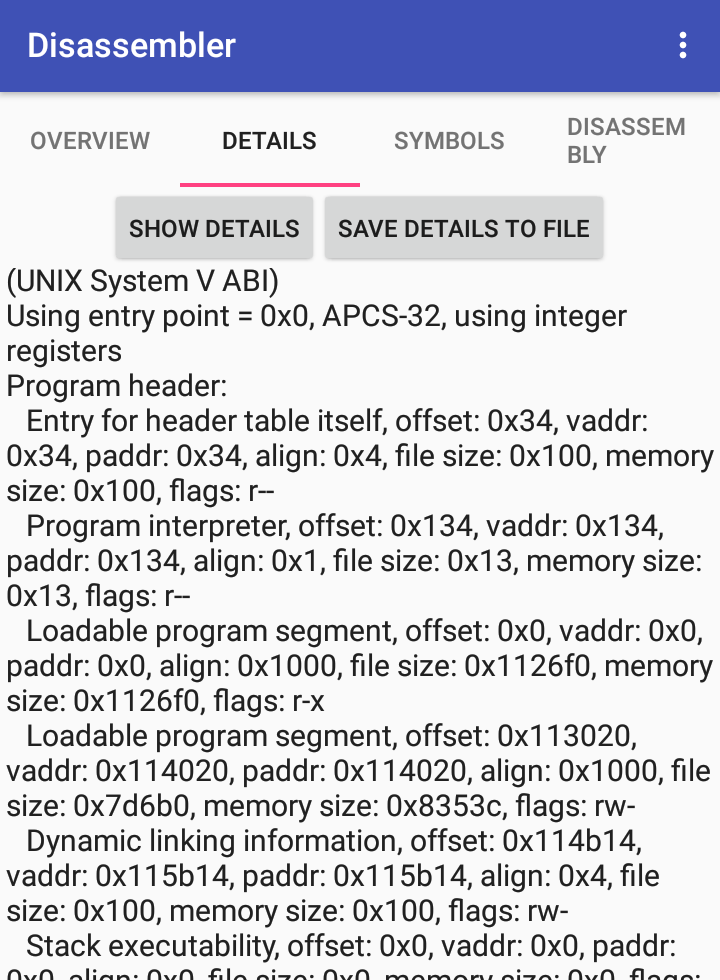 (PE)
(PE)
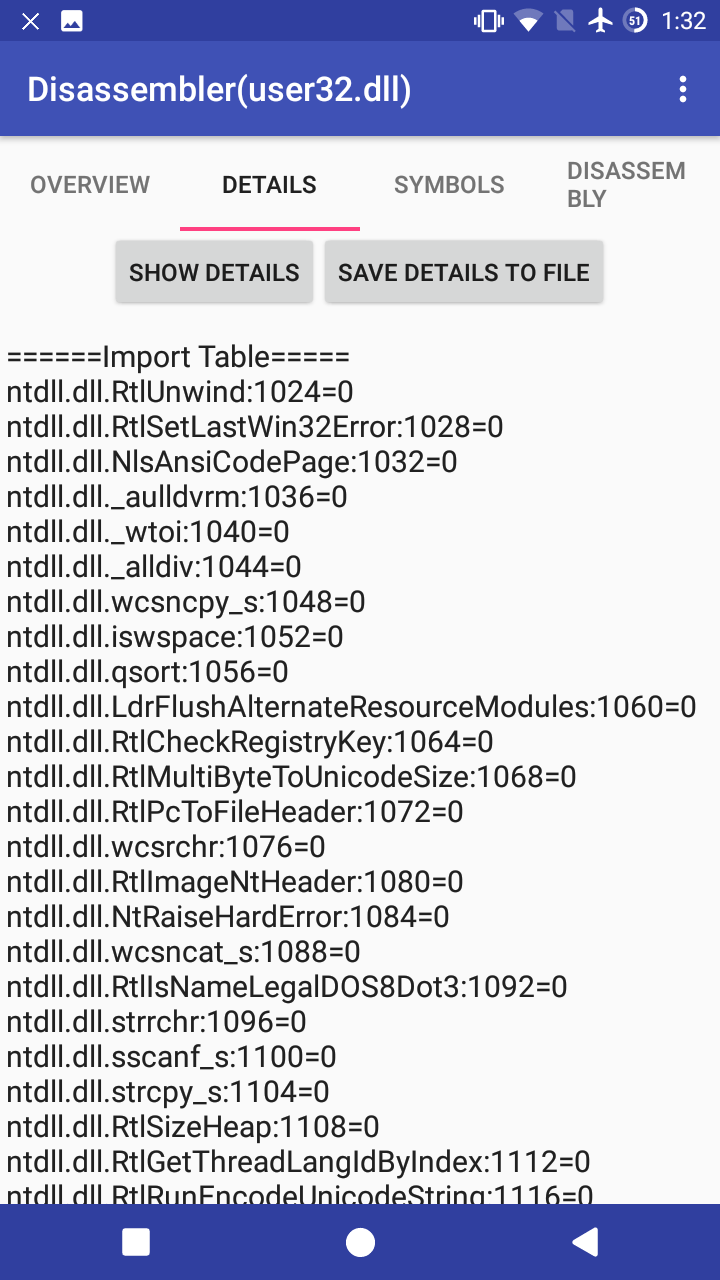
- Press
Save to filebutton to save it. - Go to Symbols tab.
- You can see symbols found in the elf file, their demangled names(if they exist), addresses, and their properties.
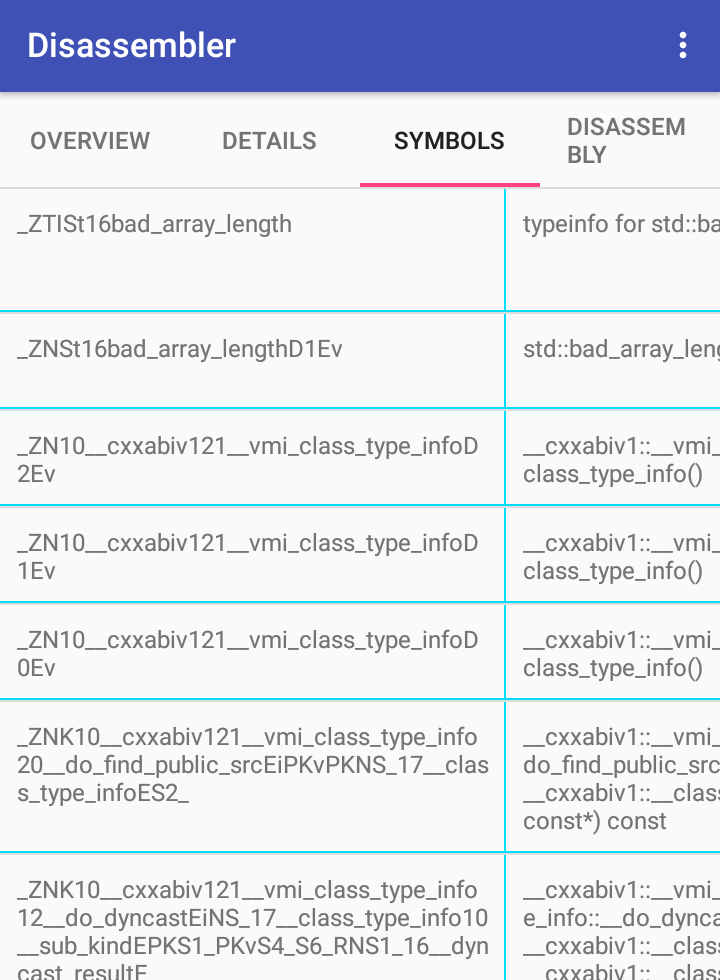
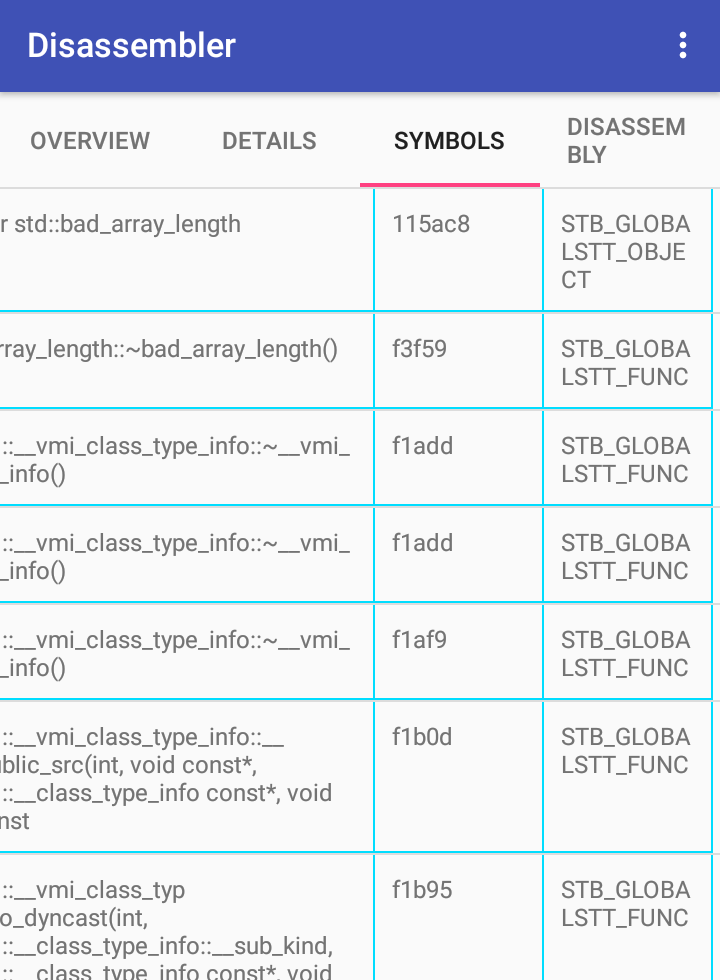
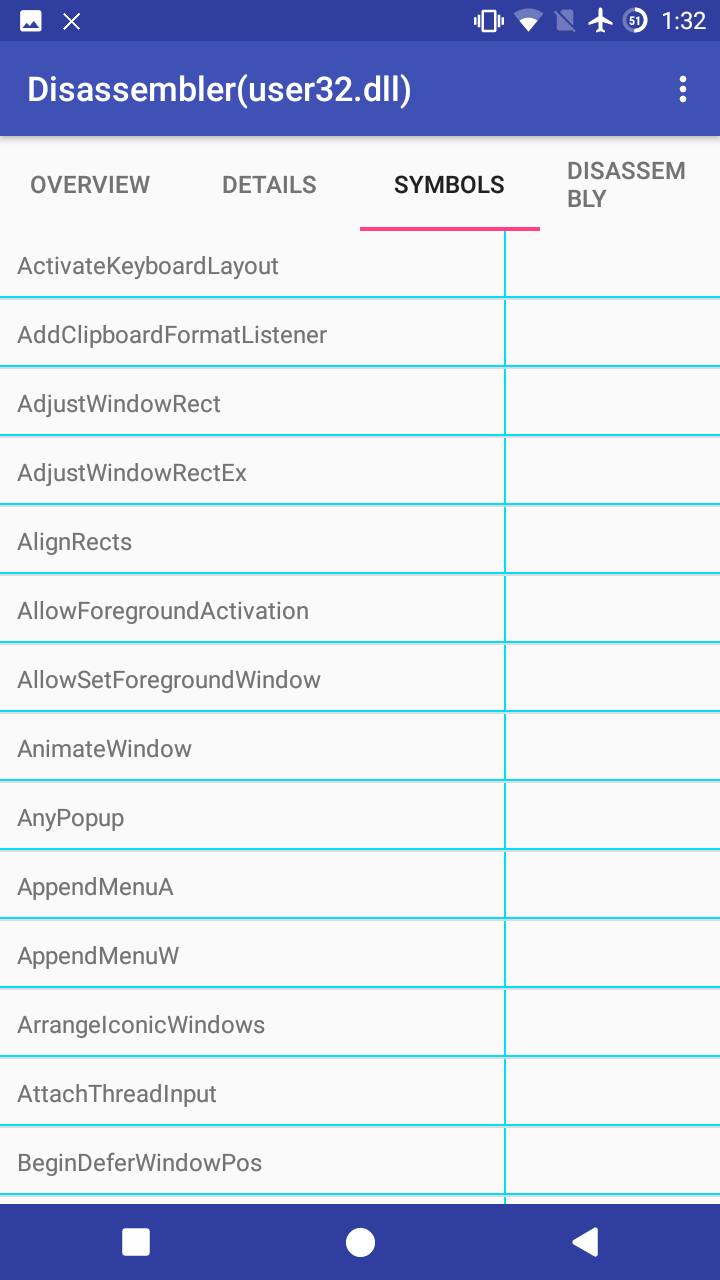
- Go to disassembly tab.
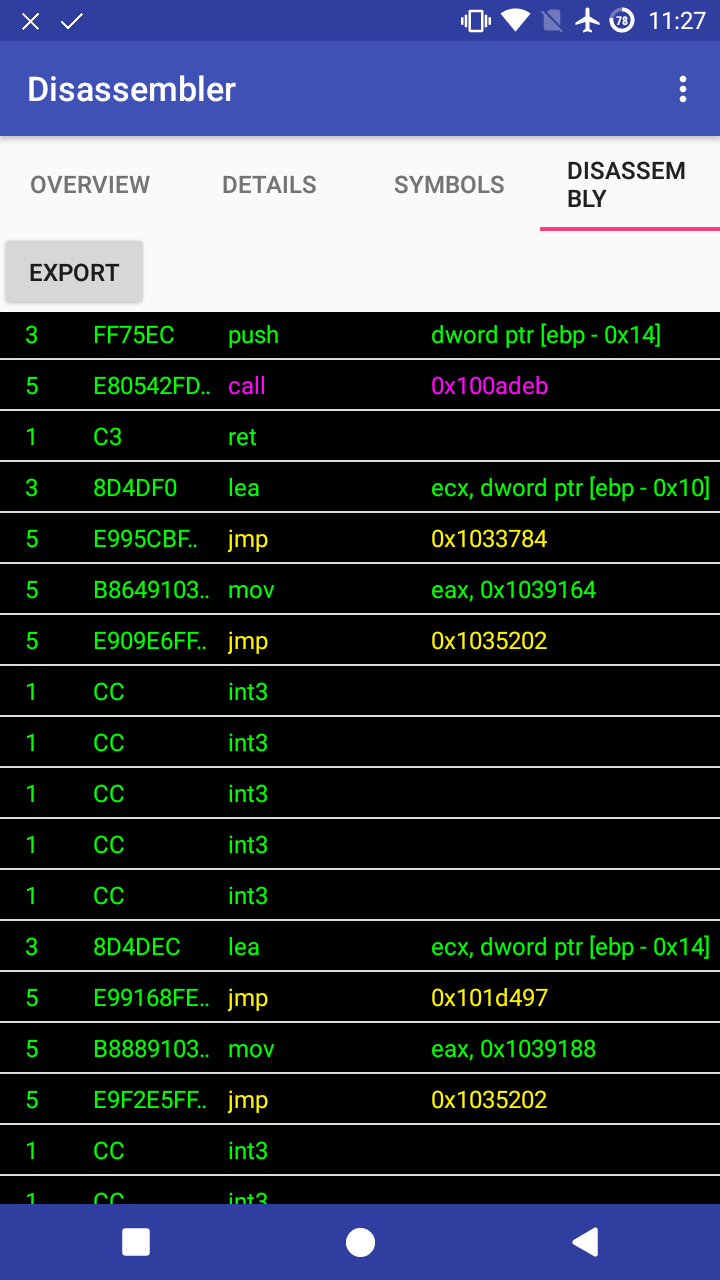
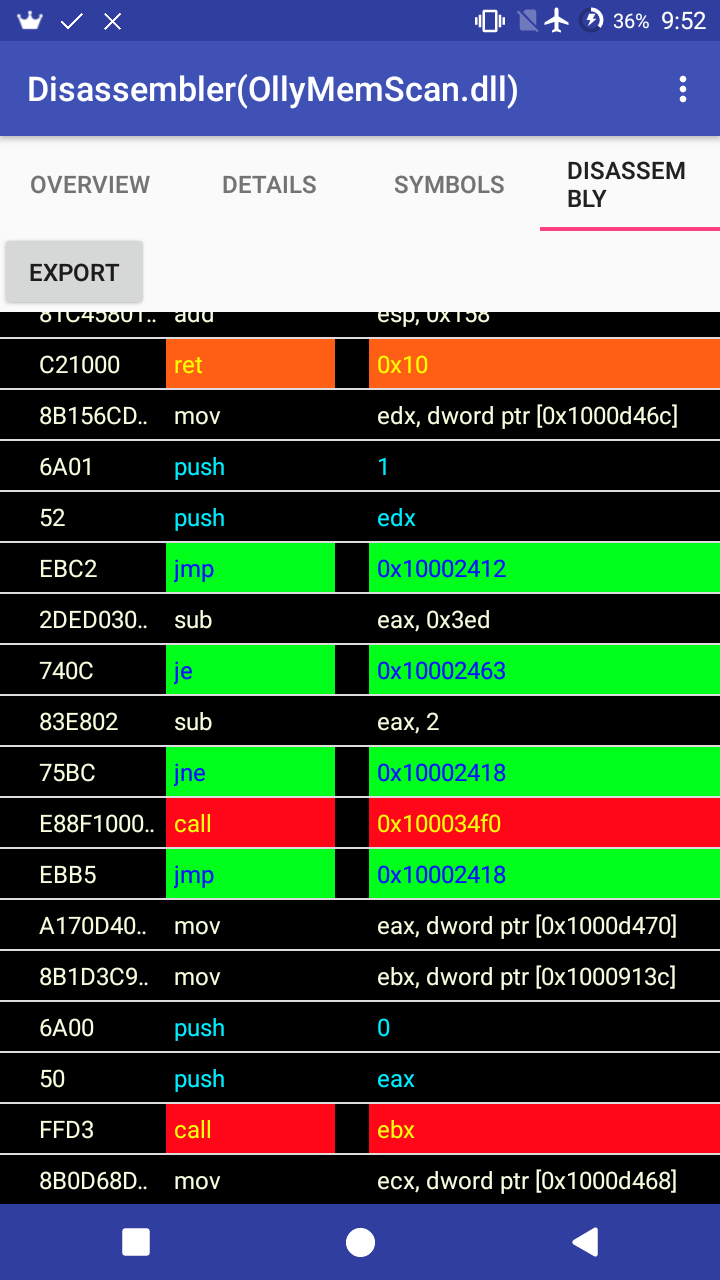
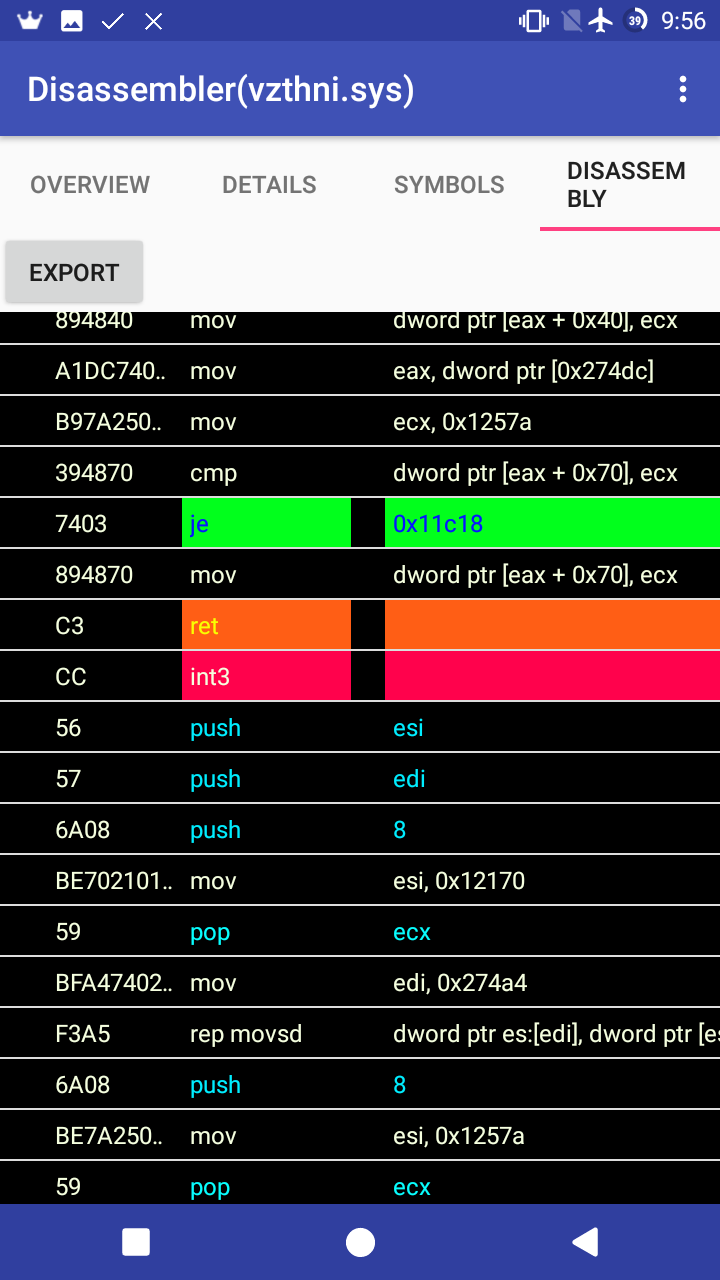
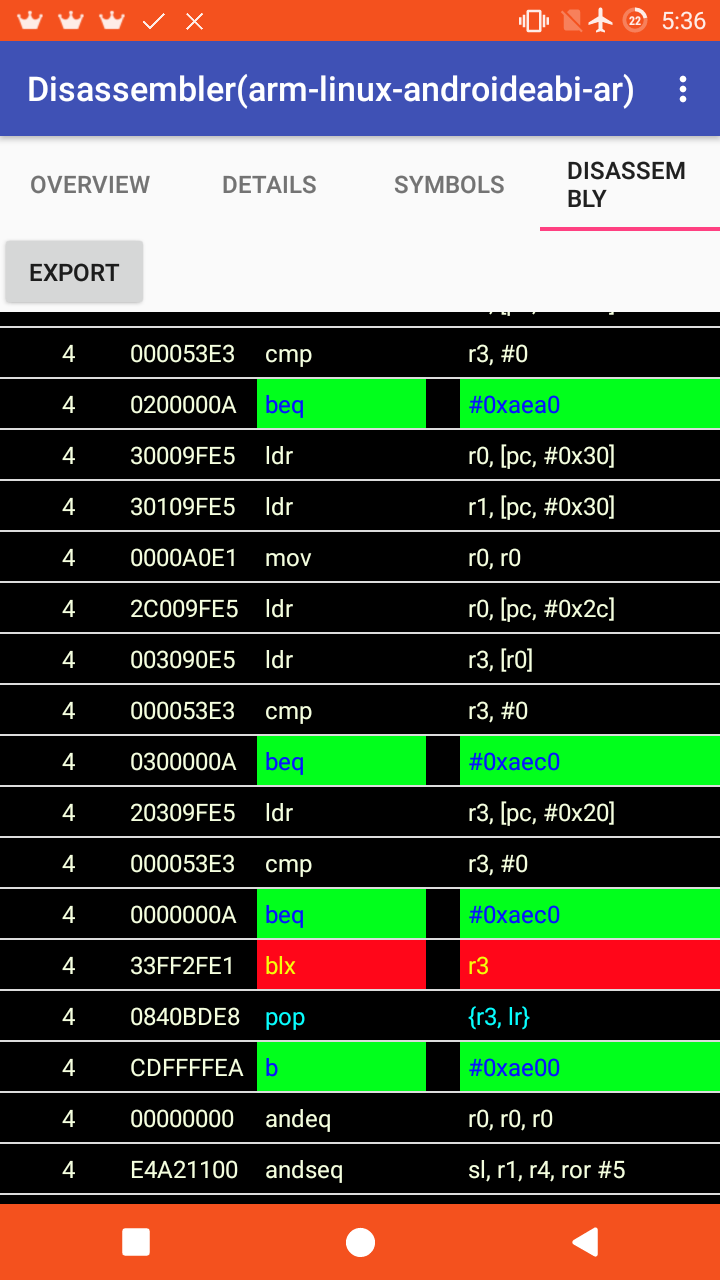
- To export the disassembly, press
Exportbutton and choose the option.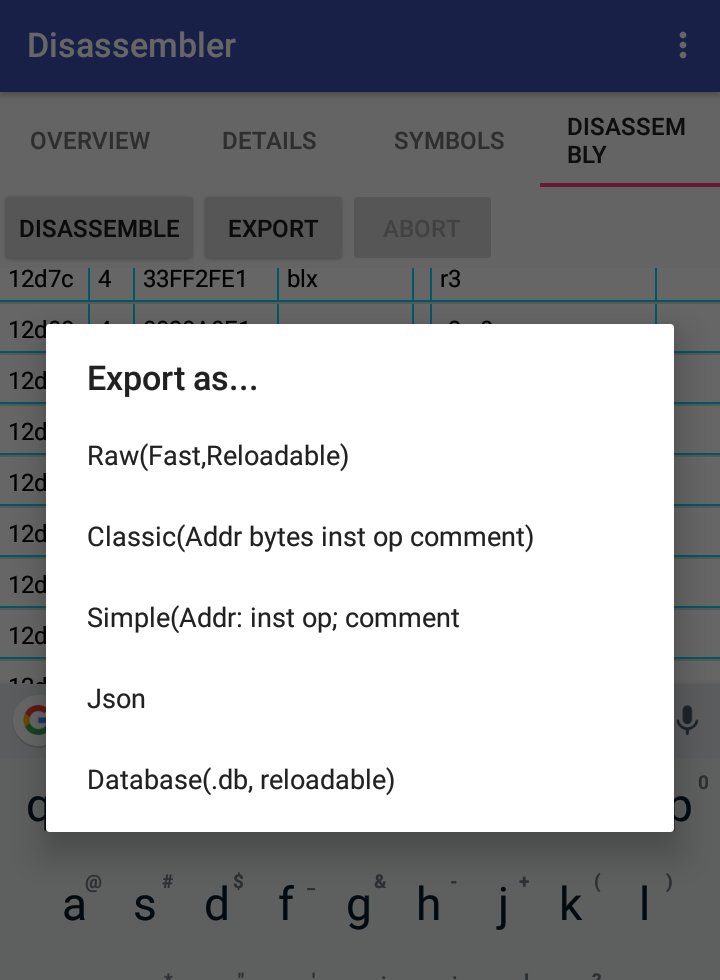
- Raw Uses java's intrinsic serialization, and super fast.
- Classic Pretty!
- Simple Can be directly pasted as code!
- Json It can be loaded again to analyze again(though reloading is not implemented yet - Sorry.)
- Database Slow. Not recommended.
Here are some common issues and some solutons for them.
-
The app crashes!
Sorry for inconvenience, please send an error report as an issue. If you can't wait for the next stable version, please check / grant the read/write permission to the app.
-
NotThisFormatException
Is it a well known executable file? (ELF:
.so, .o, .lib, .a, etc.., PE:.exe, .dll, .sys, ...) Then please report me with the file you tried to disassemble. If not, you need to pressOKand setup manually.
You can download the theme.zip here.
- Unzip it to
/storage/emulated/0/themes/or/sdcard/themes. - Done. You can now use this in settings menu(in app)
- To rename/remove themes, just rename/remove the files.
- Use Android studio.
- Any improvements are welcomed!
This app used
- Capstone
- Storage-Chooser
- Colorpickerview
- Java-binutils
- PECOFF4J.
- Root File Chooser
- PhotoView
- Multi-level-Listview
- Facile-api
- plthook
- Show prototypes of NDK/C standard APIs in the symbols tab.
- More sophisticated colorizing
- Generate more useful comments
- Provide assembly tutorials.
- Fix symbols bug.
- Add pseudo-virtual machine to debug.
- Allow users to analyze active processes.
- Add arrow beside the disassembly.
- Row selection
- Better support for thumb assemblies
- Add compatibility for OllyDbg's
.udd/.bakfiles - Add compatibility for IDA's produce files.
- About to add other utilities.
- Add android resource analyzer
- Don't the symbols' names look odd?
https://reverseengineering.stackexchange.com/a/20124/23870
https://reverseengineering.stackexchange.com/a/18203/23870
I think I have to notice you that:
- When the crash report with types such as
FileCorruptedExceptionis sent, the file you are analyzing may be attached to the bug report email, and be uploaded to the repository ingithub.com.