- Cross-account deployment
- Deploy from CI/CD
- Manual approval
AWS_PROFILE=cmdlab-sandpit1 npx cdk bootstrap --toolkit-stack-name gh-deploy --qualifier ghdep aws://[primary-account-id]/ap-southeast-2 --trust-for-lookup [second-account-id] --cloudformation-execution-policies arn:aws:iam::aws:policy/AdministratorAccess
AWS_PROFILE=cmdlab-sandpit2 npx cdk bootstrap --toolkit-stack-name gh-deploy --qualifier ghdep aws://[second-account-id]/ap-southeast-2 --trust [primary-account-id] --cloudformation-execution-policies arn:aws:iam::aws:policy/AdministratorAccess
Add "@aws-cdk/core:bootstrapQualifier": "ghdep", in the context section. The cdk.json file tells the CDK Toolkit how to execute your app.
You only need to create the role in your primary AWS account.
see github-oidc-for-aws for more details.
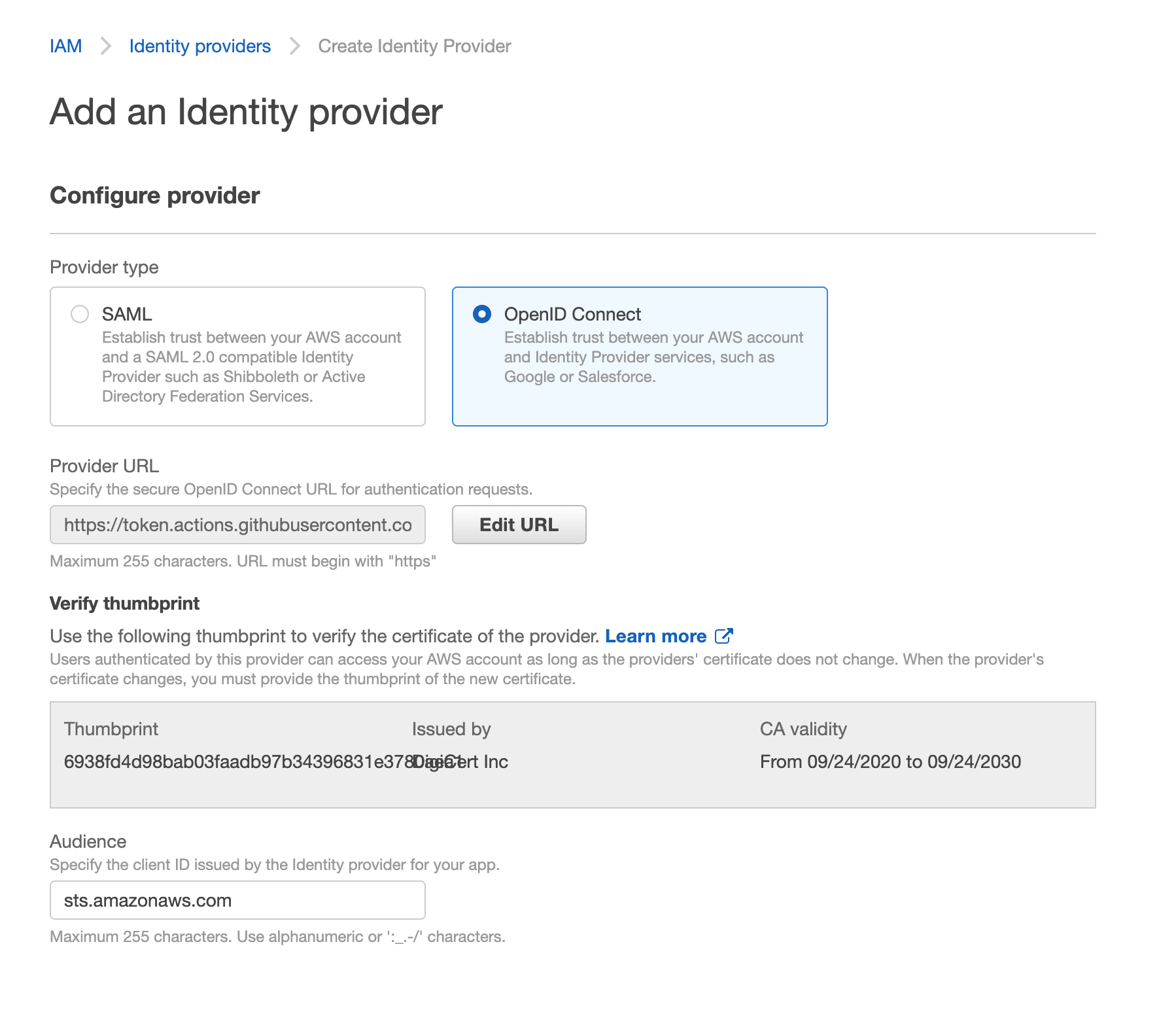
see minimal policies required by cdk-pipelines-github for more details
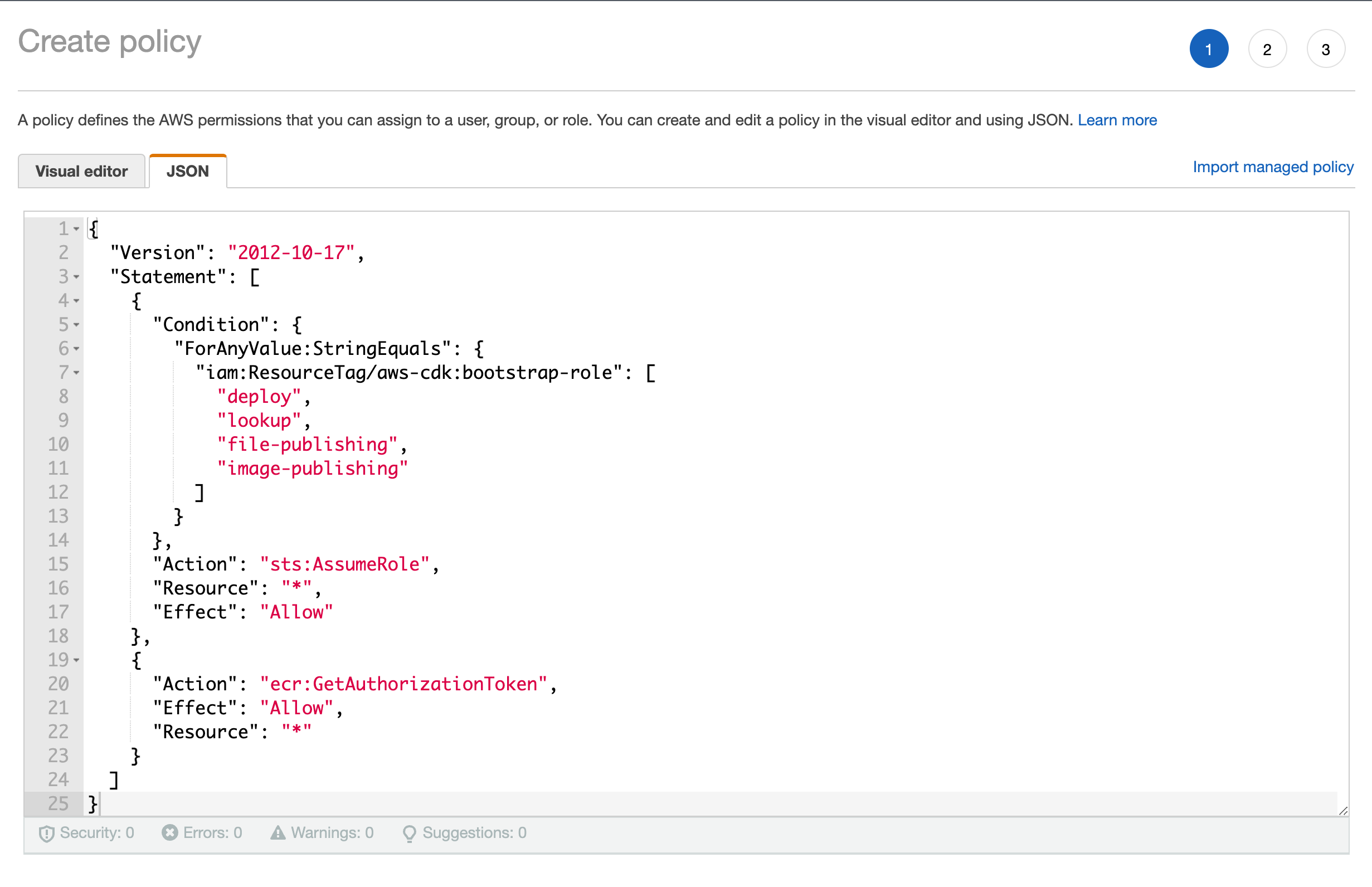
{
"Version": "2012-10-17",
"Statement": [
{
"Condition": {
"ForAnyValue:StringEquals": {
"iam:ResourceTag/aws-cdk:bootstrap-role": [
"deploy",
"lookup",
"file-publishing",
"image-publishing"
]
}
},
"Action": "sts:AssumeRole",
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "ecr:GetAuthorizationToken",
"Effect": "Allow",
"Resource": "*"
}
]
}
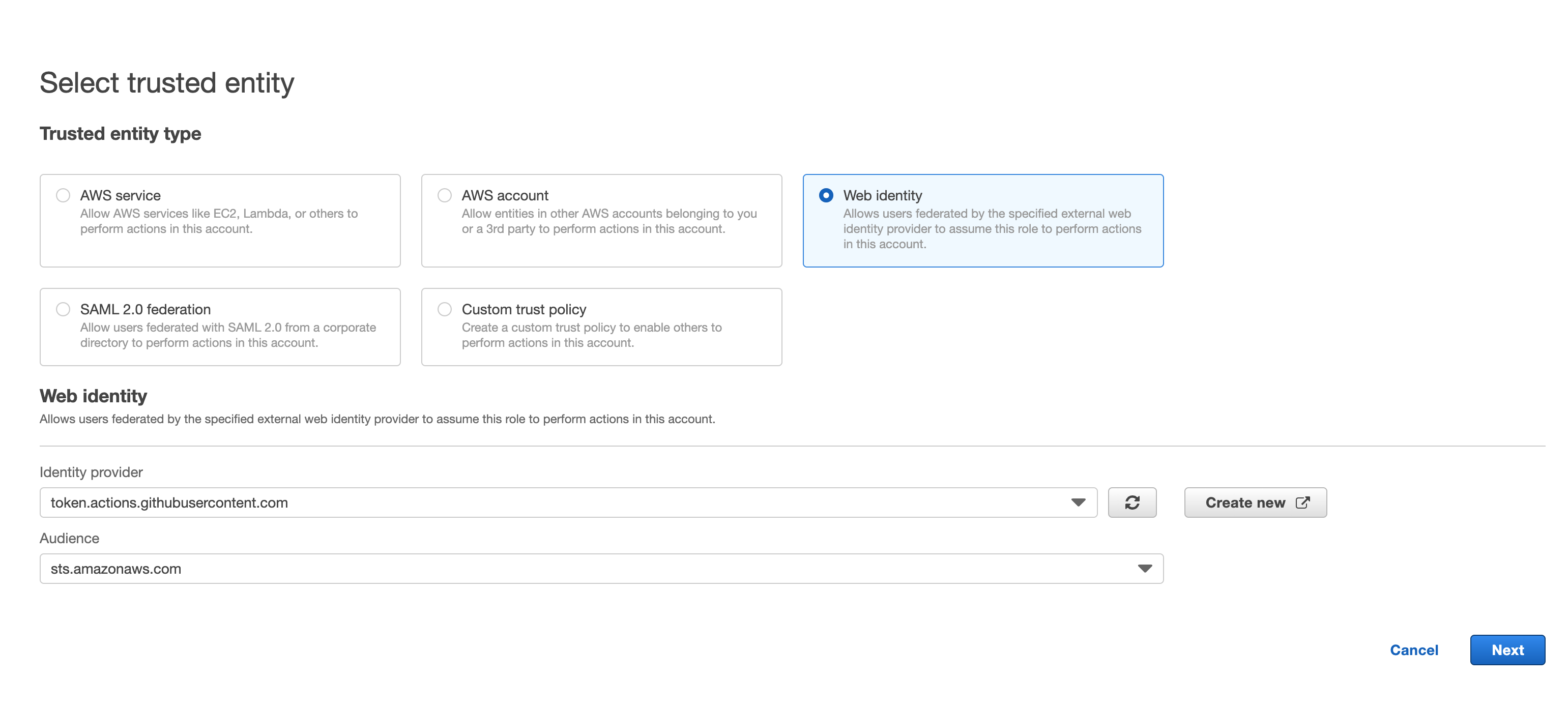
Choose web identity
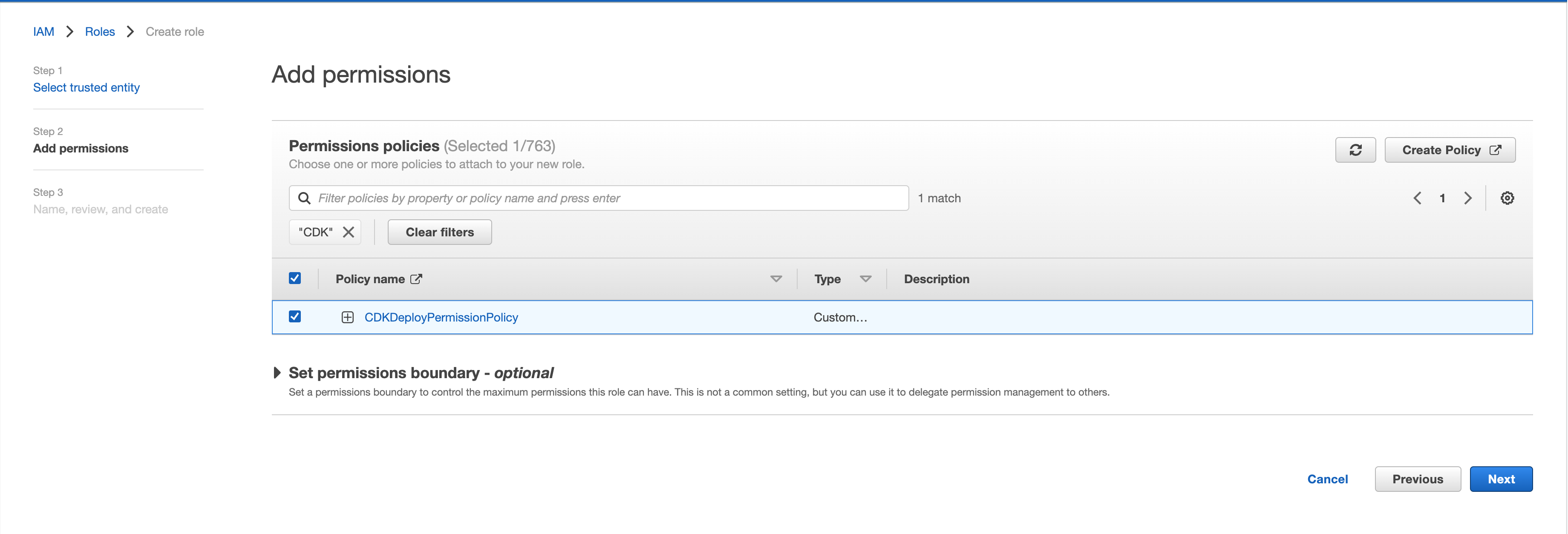
 Attach the policy
Attach the policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::[primary-account-id]:oidc-provider/token.actions.githubusercontent.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"token.actions.githubusercontent.com:aud": "sts.amazonaws.com"
},
"StringLike": {
"token.actions.githubusercontent.com:sub": [
"repo:liweiyi88/*:ref:refs/heads/*",
"repo:liweiyi88/*:environment:*"
]
}
}
}
]
}