Table of Contents generated with DocToc
A mobile-friendly web application that serves KeePass database on a web frontend.
Written in Rust and JavaScript.
- Doesn't save master password/keyfile, uses a new and unique encryption key to cache the database
- Encryption key is stored securely in the kernel keyring
- Server revokes encryption keys after a configurable user idle time, effectively removing access to the cached database
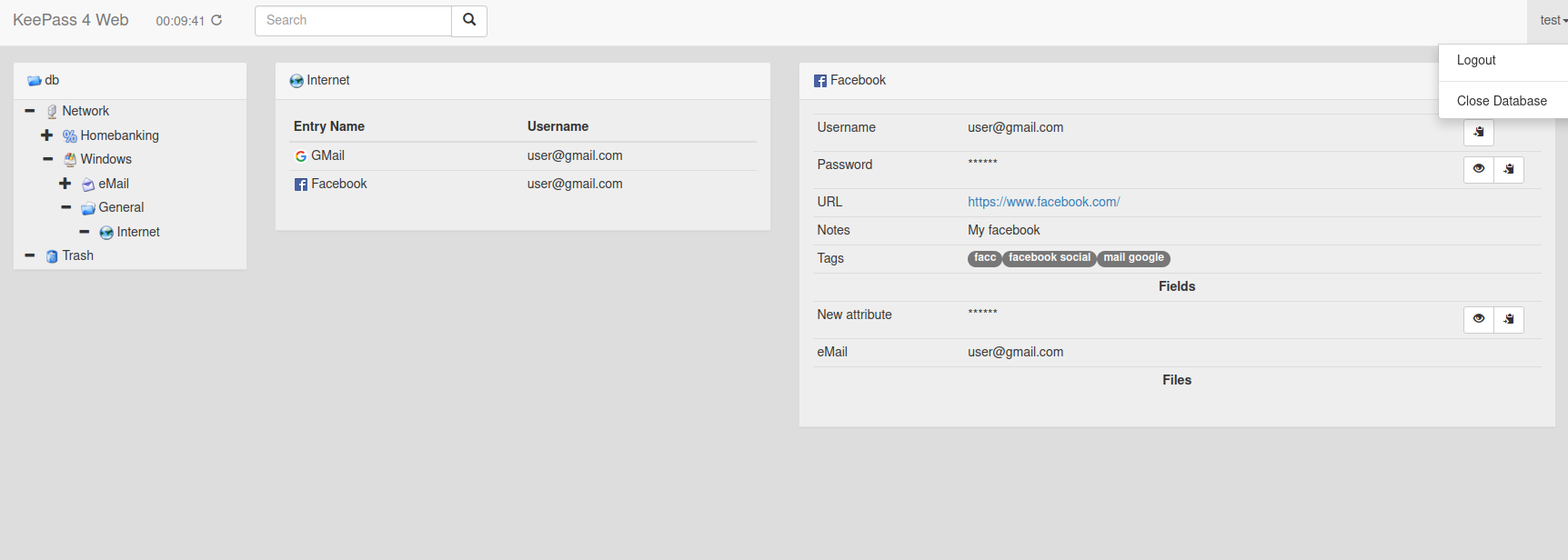
- Web interface offers entry search and access to files stored inside the database. Also displays custom entry icons
-
From container image: See DEPLOYMENT
-
From source:
-
Clone the repo to some dir
cd keepass4web-rs
-
Follow BUILD FRONTEND, DEPLOYMENT in that order
-
The minified, bundled file will be written to public/scripts/bundle.js
-
Install Node/npm, e.g. for Ubuntu
sudo apt-get install npm
-
Install js modules
npm install
-
Copy bootstrap font files
cp node_modules/bootstrap/fonts/* public/fonts/
-
Build js bundle
npm run build
-
For a non-uglified version you can run
npm run dev
- See
config.yml
See GitHub Packages
The image ships with the default config in /conf/config.yml, which should be overwritten with a mount/volume.
The app makes use of the Linux kernel keyring.
The keyring is currently not namespaced, hence container tooling deactivate the specific syscalls by default. To make the app run you will need to activate the syscalls by creating a custom seccomp profile and passing the path to the container runtime:
A base file for extension can be found here,
see the syscalls section.
The required syscalls are:
- keyctl
- add_key
- request_key
There's an example seccomp profile seccomp/keyring.json in the repo.
Make sure no other containers are running under the same user, or they will be able to access keys stored for keepass4web.
This is best achieved by running rootless containers with a dedicated user for keepass4web.
Example:
docker run \
-p 8080:8080 -v ./config.yml:/conf/config.yml \
-v ./tests/test.kdbx:/db.kdbx \
--security-opt seccomp=seccomp/keyring.json \
ghcr.io/lixmal/keepass4web-rs:master
(master password: test)
This requires rust installed, compile the binary:
export RUSTFLAGS="-Ctarget-cpu=sandybridge -Ctarget-feature=+aes,+sse2,+sse4.1,+ssse3"
cargo build --bins --release --target-dir release
Run the binary:
target/release/keepass4web-rs
-
Htpasswd
- Authenticates users against a
.htpasswdfile.
- Authenticates users against a
-
LDAP
- Authenticates against external LDAP servers (Microsoft AD, OpenLDAP, etc.)
- Provides customizable search filters, attribute mapping, and secure binding.
-
OIDC
- Authenticates users with a compatible OpenID Connect provider.
- Retrieves user information, supports customizable scopes, CSRF protection, and logout functionality.
-
Filesystem
- Retrieves KeePass databases from the local filesystem.
- Can fetch database and keyfile locations from authentication backend or configuration.
-
HTTP
- Fetches KeePass databases over HTTP/HTTPS.
- Supports basic authentication and bearer token mechanisms.
-
Show kernel keyrings in use (as root)
sudo cat /proc/keys
sudo cat /proc/key-users
- KeePass databases are read-only
- Limits of kernel keyring apply
Client Server
Load website /
request KeePass tree
-------------------->
Check sesssion
not authenticated
<--------------------
Redirect to /user_login
Show credentials dialog
user credentials
-------------------->
User auth (LDAP, SQL, ...)
login OK
<--------------------
Redirect to /backend_login
Show backend login dialog
backend credentials
-------------------->
Init DB backend / receive backend token
login OK
<--------------------
Redirect to /db_login
Show KeePass password dialog
KeePass credentials
-------------------->
Get KeePass database from backend
Decrypt KeePass database with master key + key file
Encrypt serialised string with newly generated key
Put encryption key into kernel keyring
Write keyring key id to session
Place encrypted database into cache
decryption OK
<--------------------
Redirect to /
request KeePass tree
-------------------->
Get database from cach
Get keyring key id from session
Get encryption key from kernel keyring
Decrypt database with key
Send KeePass tree
<--------------------
Show KeePass tree
...
Password request by user
Request pw entry
-------------------->
Get keyring key id from session
Get encryption key from kernel keyring
Get database from cache
Decrypt database
Decrypt requested password
Send pw entry
<--------------------
Show cleartext pw
This software is copyright (c) by Viktor Liu. It is released under the terms of the GPL version 3.
Most of the icons in the public/img/icons directory are released under the LGPL version 2, the licence can be found in
the same directory.
The remaining icons are public domain.
As these icons are the same as the ones used by the original KeePass software, you can refer to the info
there: Icon Acknowledgements.