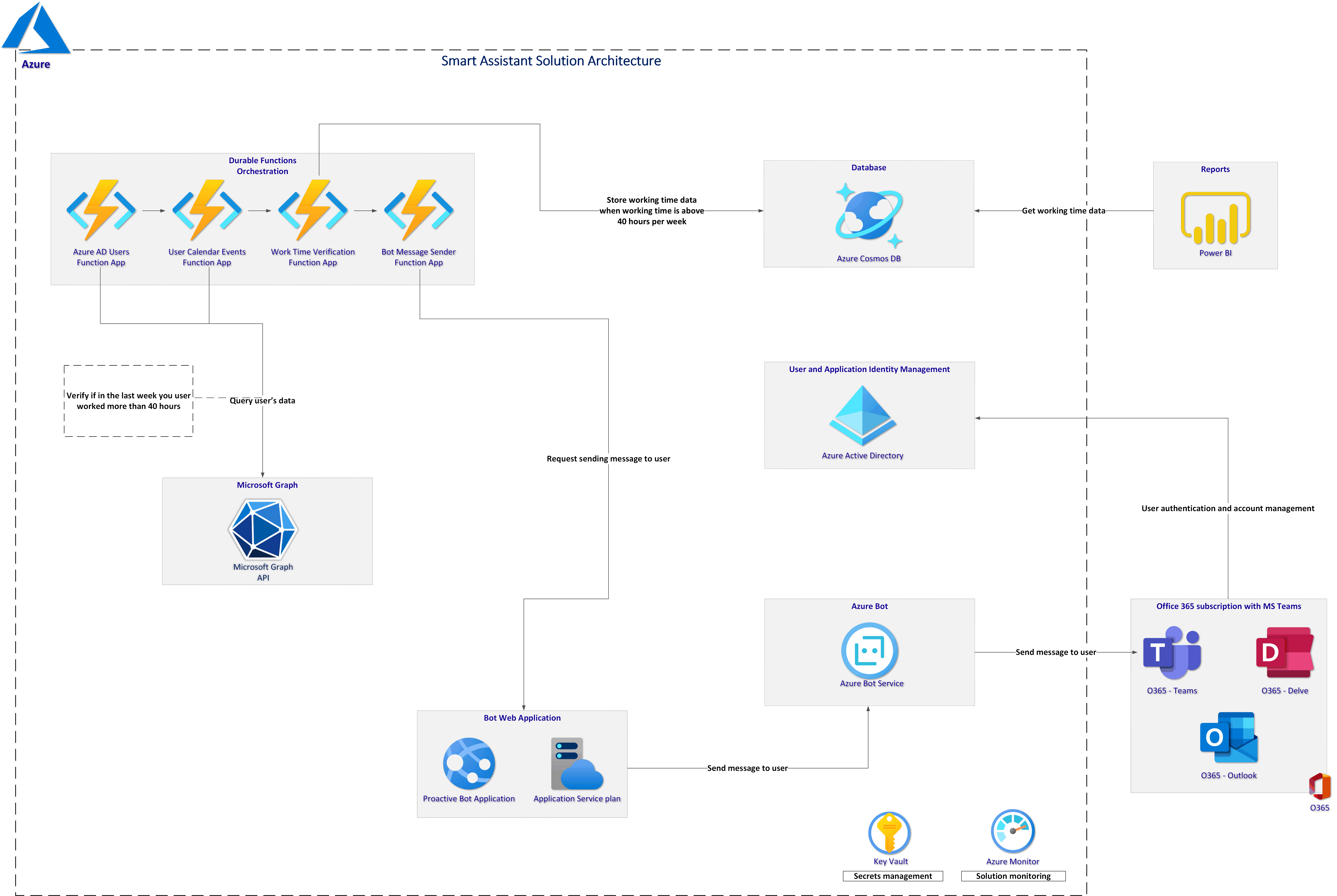
This repository contains source code for the smart Azure Bot which is responsible for verifying employee's working time and notifying them when they work more than 40 hours per week.
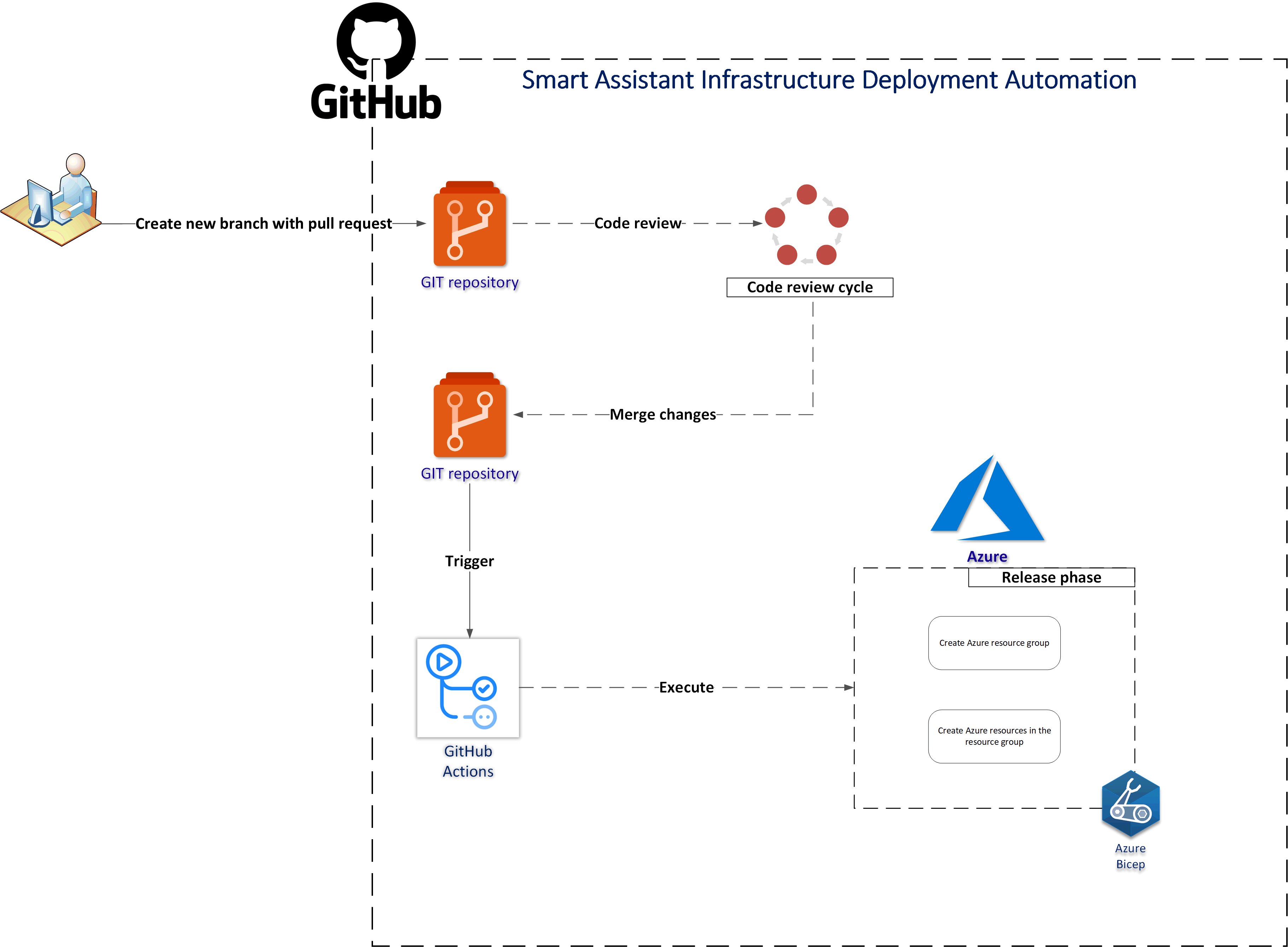
This section contains details about infrastructure setup and configuration.
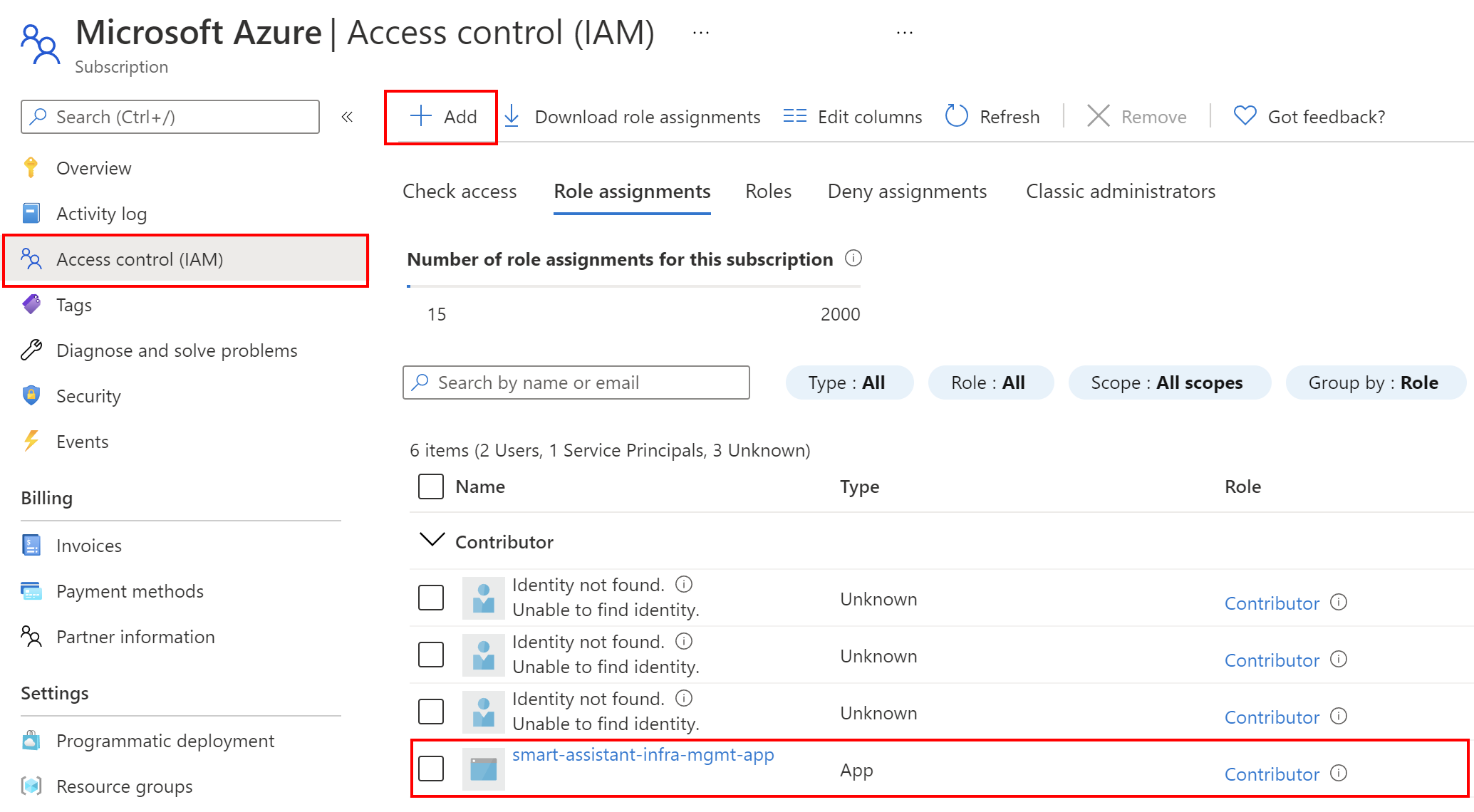
Create a new application int the Azure Active Directory related to Azure subscription, where resources must be created, and assign Contributor role to it on the subscription level:
Then, fill out the below JSON:
{
"clientId": "<GUID>",
"clientSecret": "<GUID>",
"subscriptionId": "<GUID>",
"tenantId": "<GUID>"
}- clientId - ID of the registered application in the Azure AD
- clientSecret - generated secret for the registered application under Certificates & secrets tab
- subscriptionId - ID of the subscription
- tenantId - ID of Azure AD tenant related to Azure subscription (can be found under Overview tab of the Azure AD service)
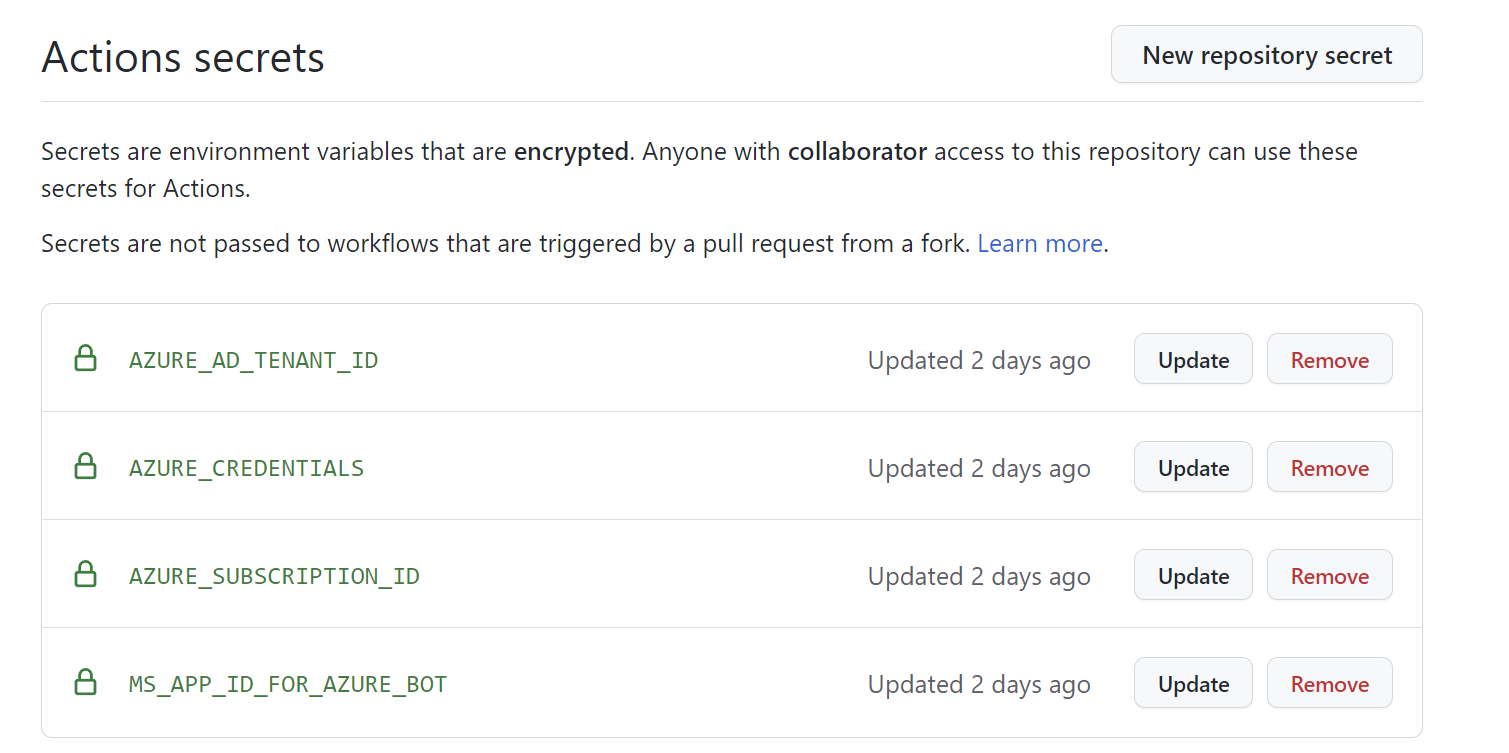
Copy above value. Open the GitHub secrets section in the project settings and paste the above JSON result. The name of the secret should be: AZURE_CREDENTIALS.
Create two additional secrets:
- AZURE_AD_TENANT_ID - with the ID of your Azure Active Directory tenant ID (can be found under Overview tab in the Azure AD blade in Azure portal)
- AZURE_SUBSCRIPTION_ID - ID of your Azure subscription where you will deploy Azure resources
In the Visual Studio code, sign in to your Azure tenant using az login command.
az account set --subscription <<subscription ID>>
az group create --location westeurope --name rg-smart-assistant-dev
Create smart-assistant-infrastructure.bicep file:
today=$(date +"%d-%b-%Y")
DeploymentName="deployment-"$today
az deployment group create \
--name $DeploymentName \
--resource-group rg-smart-assistant-dev \
--template-file smart-assistant-infrastructure.bicep \
--parameters location=westeurope tenantId=your-tenant-id
In the repository you can also find the source code for the bot web application under this link.
To access the endpoint which sends messages to Teams, we have to secure this endpoint with Azure AD to make sure that anonymous access is not allowed.
In the Azure AD we have to register a new app which will represent our Bot Web Application:
It is important to add role in the app manifest:
"appRoles": [
{
"allowedMemberTypes": [
"Application"
],
"description": "Access bot using client credentials flow",
"displayName": "Access bot using client credentials flow",
"id": "bc3b46b8-22ab-4868-8136-573a1a38233a",
"isEnabled": true,
"lang": null,
"origin": "Application",
"value": "access:bot"
}
],We need this role because we will obtain access token for the Azure Functions to call Bot Web App using client credentials flow.
Azure Durable Functions are used to communicate with Microsoft Graph to:
- Get all users (employees) from the organization's Azure AD tenant
- Query user's (employees) calendars to obain information about meetings and events
- Calculate working hours from the last week
- Send proactive message on Teams from the Azure bot
Authentication is required to obtain access tokens to securely communicate with Microsoft Graph API. Let's open existing application from the Azure AD so bot-smart-assistant-func-app. Three parameters are required:
- Client ID
- Tenant ID
- Client Secret
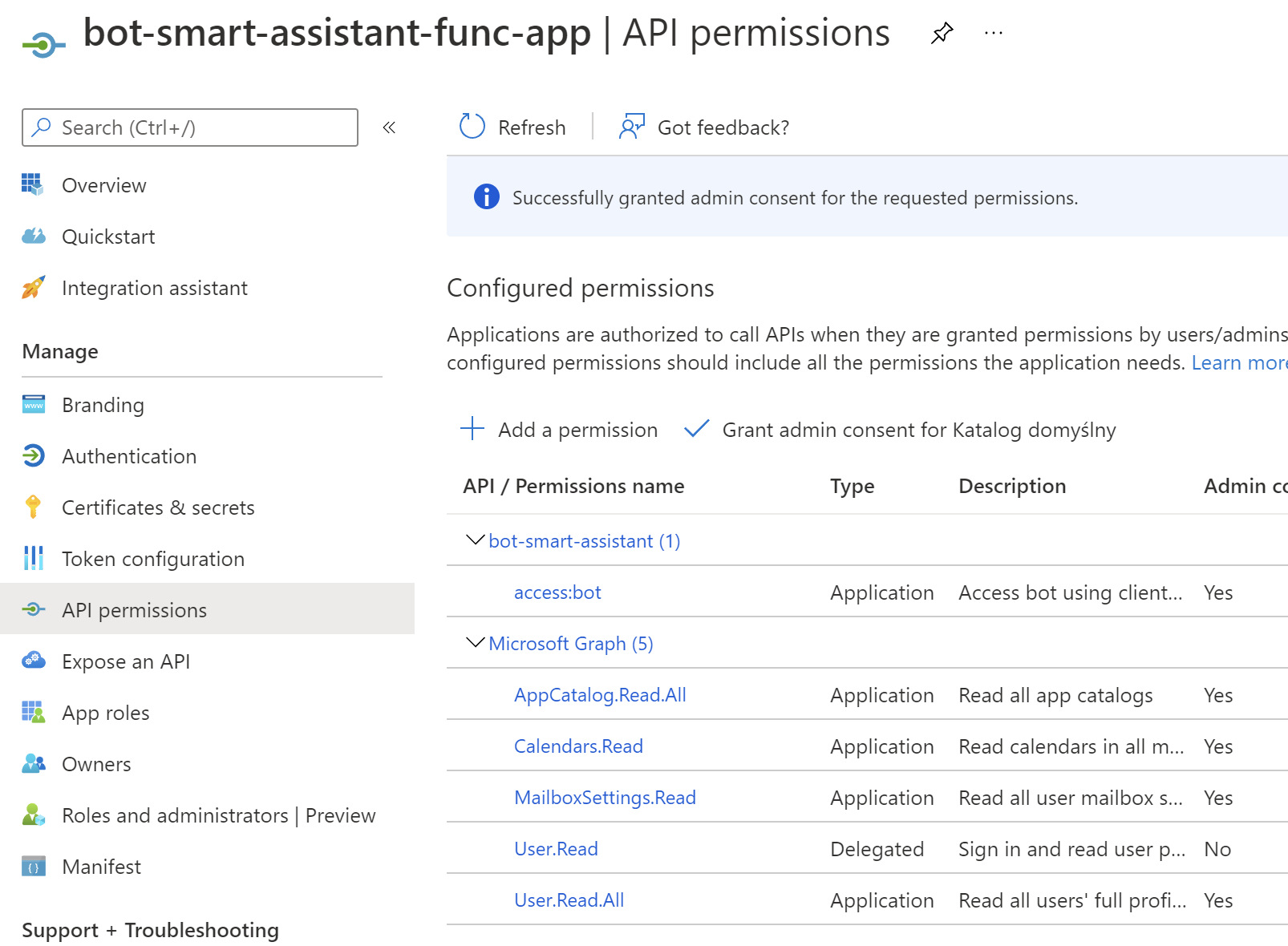
We have to add three more permissions for the application:
- Listing all users from the Azure AD tenant
- Listing events from the user's calendar
- Getting mailbox settings to detect if user has Exchange mailbox enabled
There is also one more permission to obtain an access token to call Bot Web App: access:bot which we configured in the previous step for Bot Web App.
This section contains details about Microsoft Teams App creation with Azure Bot capability.
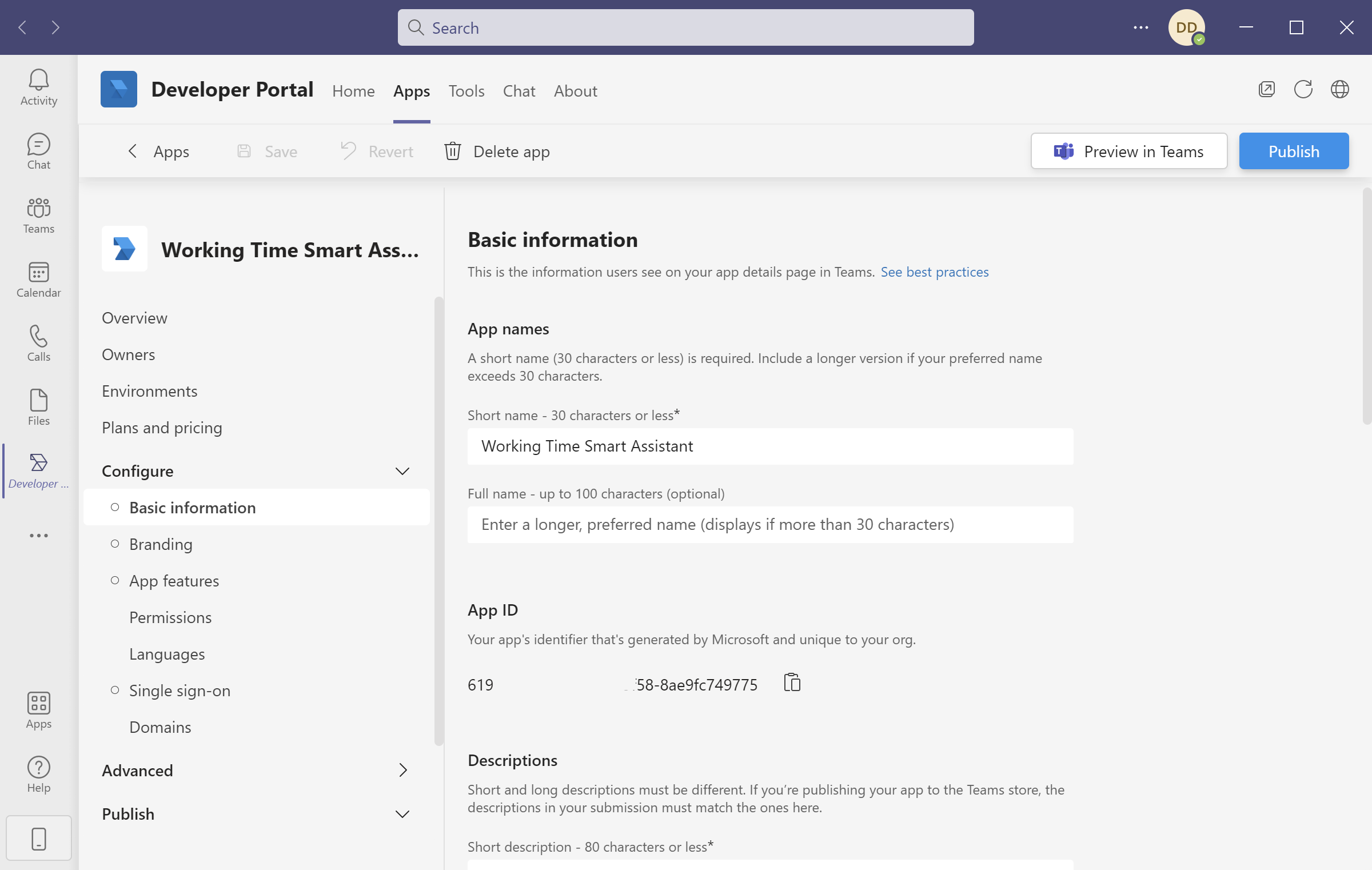
Microsoft Teams application can be created quickly using Developer Portal application available in the MS Teams.
You have to fill out required fields like long and short description or organization website:
To make it easier, I exported the application manifest so you can import the app without the need to fill in each detail. It is available in the repo under this link.
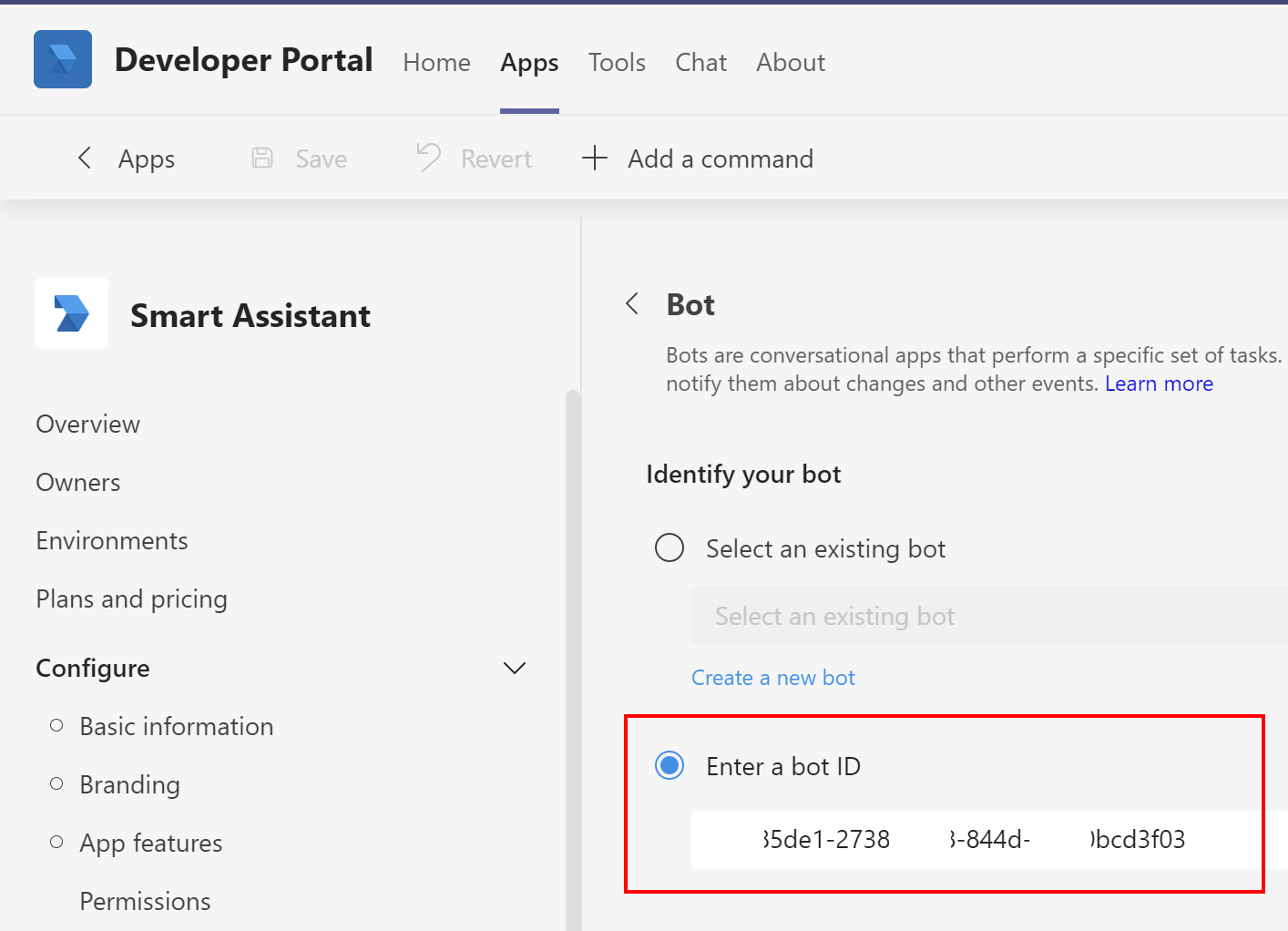
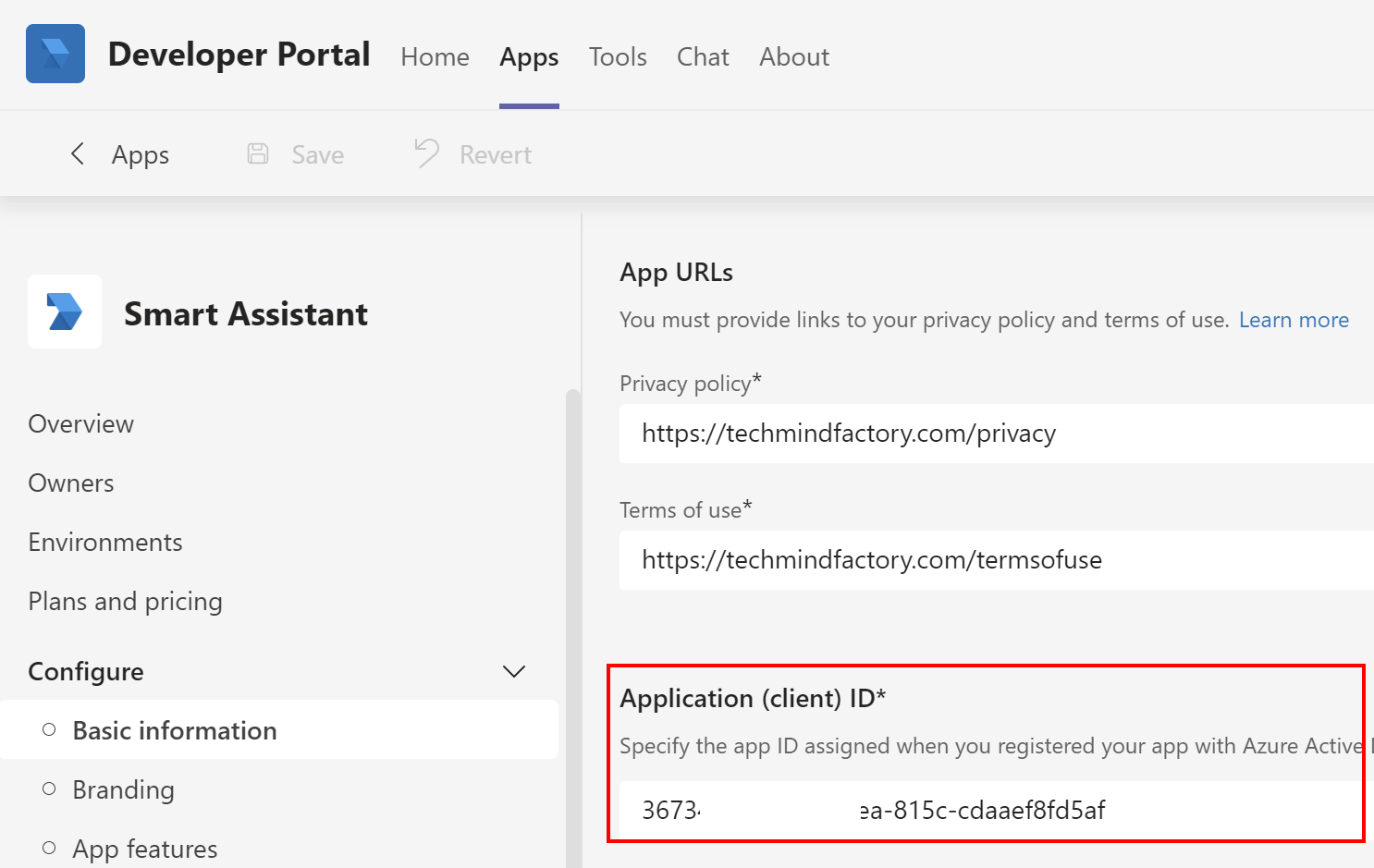
We have to provide our Azure Bot Application ID from the Azure AD where we registered the application for the bot to make it possible for bot to send messages through our MS Teams app:
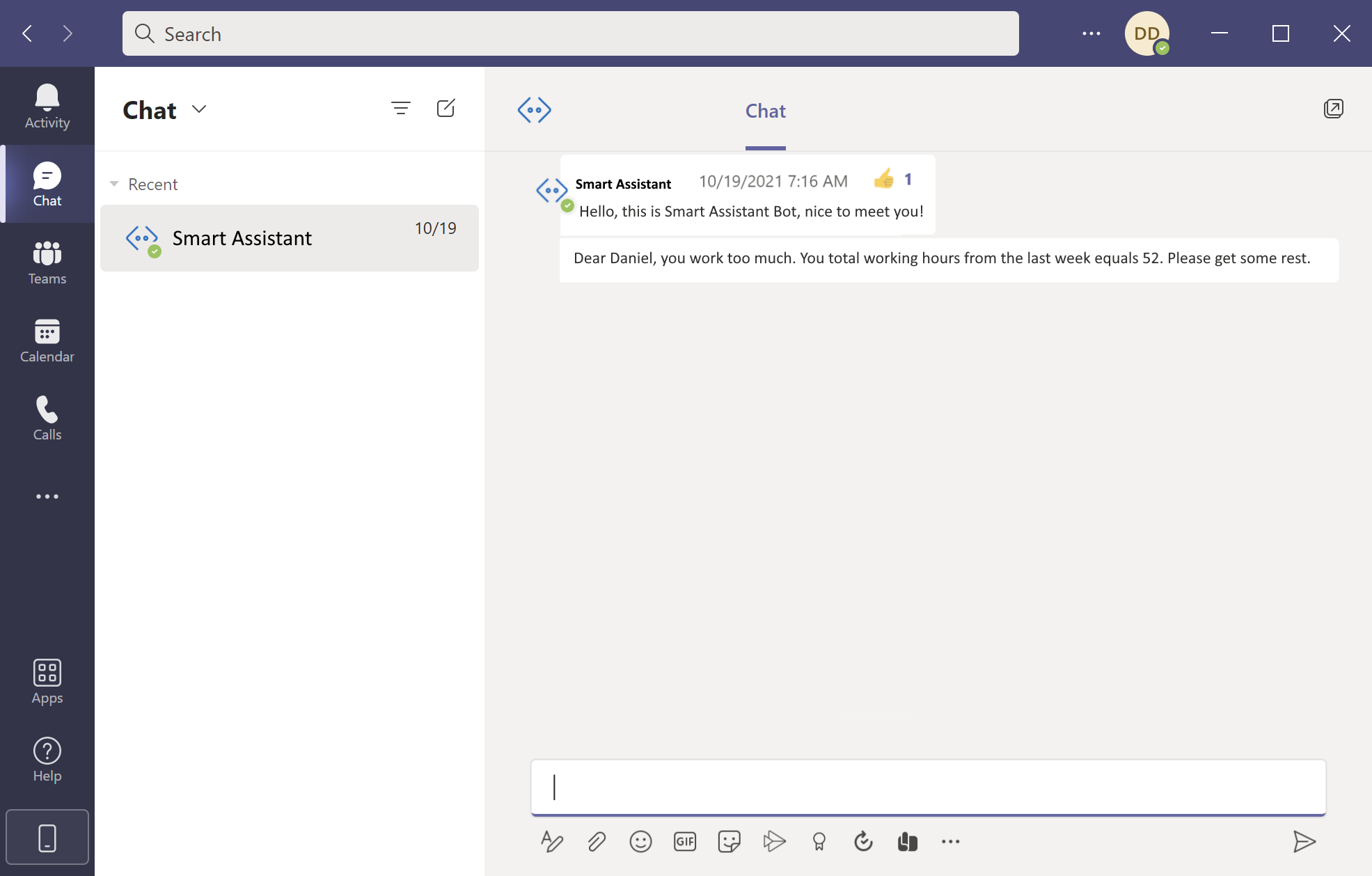
We want our bot to proactively send messages to these employees who worked too much, so more than 40 hours per week. This requires two steps:
- Installing Smart Assistant MS Teams app for specific user
- Sending a proactive message on MS Teams once the application is installed
For this kind of scenario we use Proactive installation of apps using Graph API to send messages.
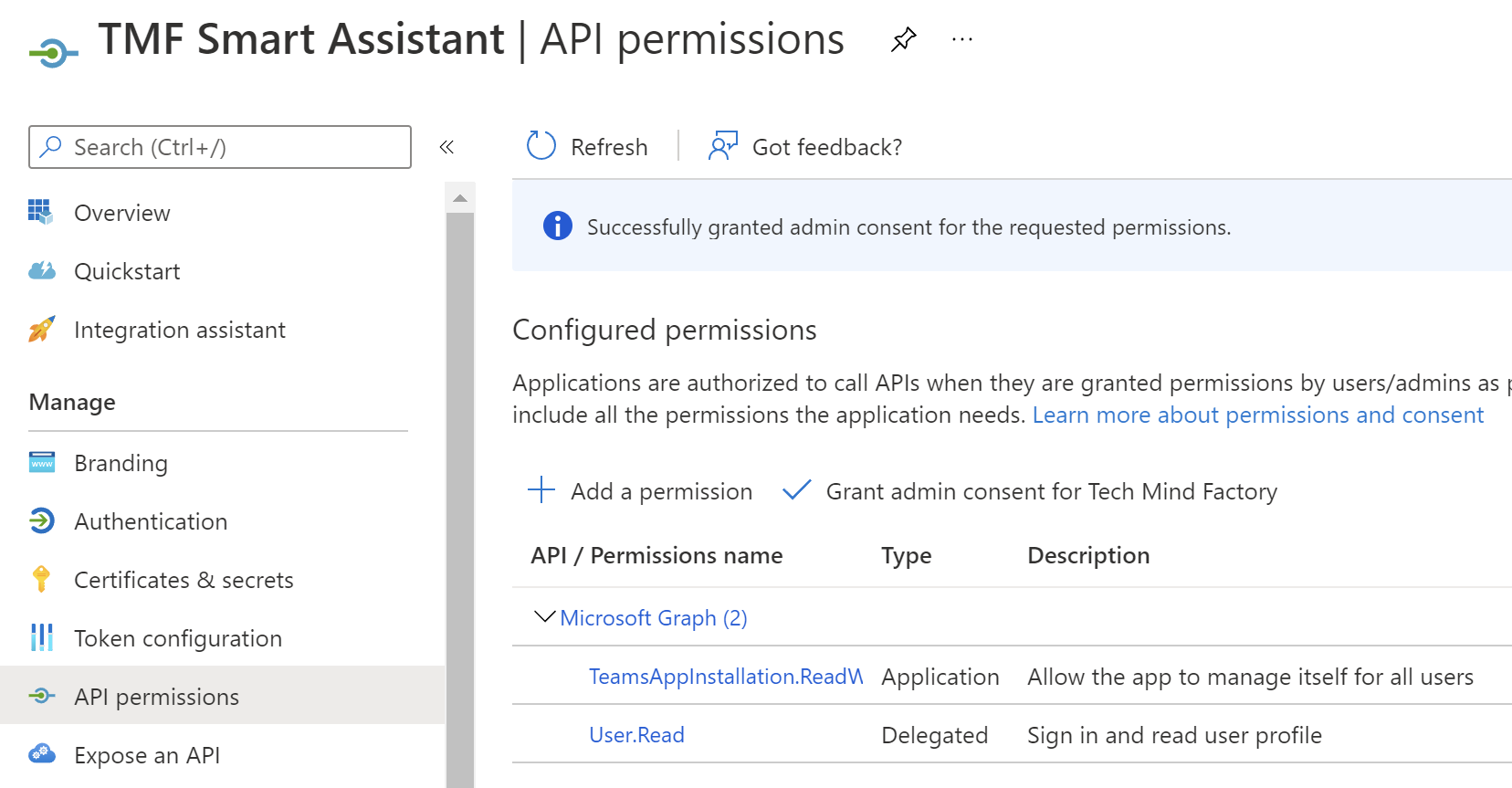
Application which we will register in the Azure AD tenant of our organization must have TeamsAppInstallation.ReadWriteSelfForUser.All permission assigned.
In the Azure AD management blade, we have to register new application with TeamsAppInstallation.ReadWriteSelfForUser.All permission:
We have to also fill Application ID with the value of client ID of the app we registered above:
Once app is ready, we can publish it to our organization:
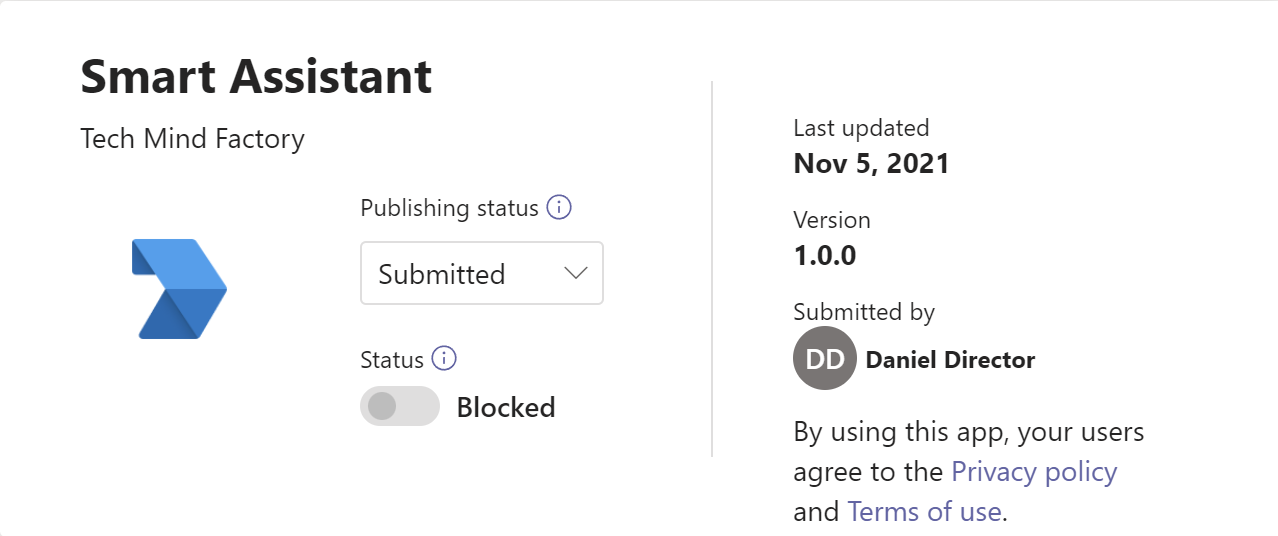
Before app can be used it has to be accepted by Teams administrator in the administrator portal. Publishing status has to be set to Published:
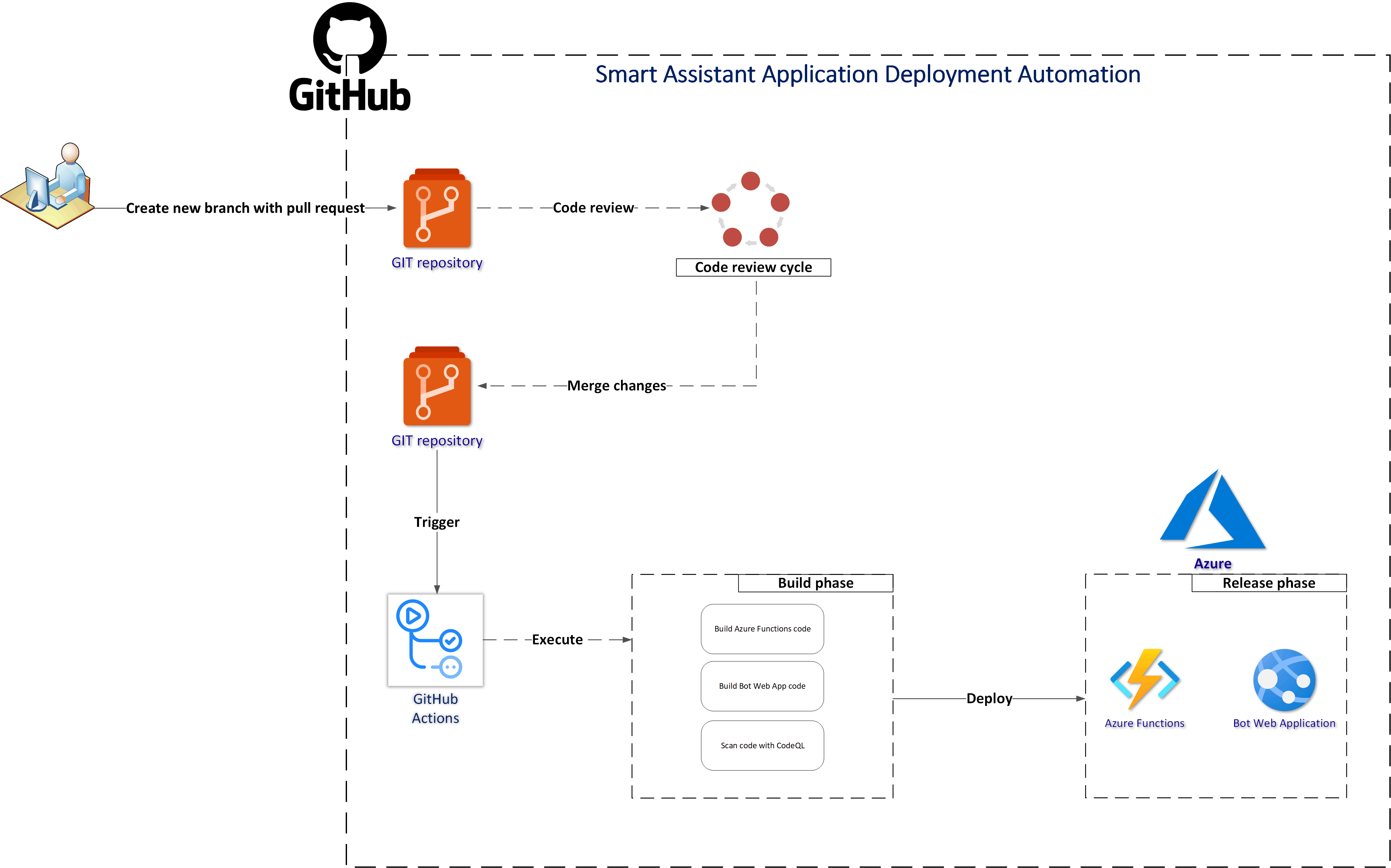
Under workflows folder you can find GitHub Actions script to build and deploy Azure Functions and Bot Web App.
Manage custom app policies and settings in Microsoft Teams
Build your first bot for Microsoft Teams
Debug a bot from any channel using ngrok
Send proactive messages tutorial
Installing app for specific users using Graph API
Proactive installation of apps using Graph API to send messages
Proactive Installation Sample App