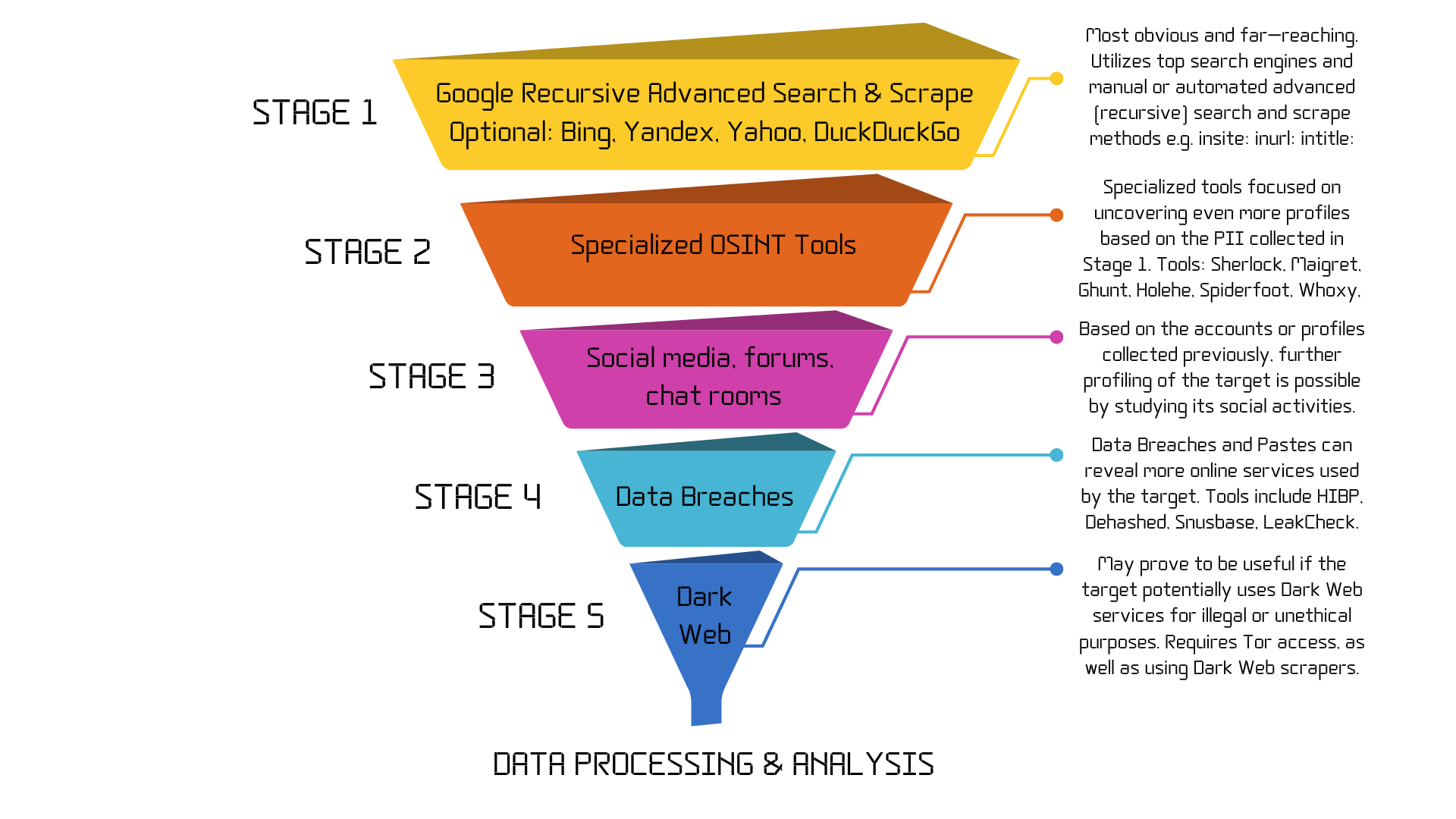
OSINT Funnel Methodology for creating a coherent data collection workflow in person-based investigations.
The main goal of OFM is to provide a clear path for performing the Data Collection phase of an OSINT investigation, so that enough and diverse data can be passed further to the Data Process & Analysis phases. With hundreds of websites, services, and CLI tools available, conducting a coherent research may be overwhelming. For this reason, the OSINTer should have a clear, easy-to-follow plan for collecting data in an organized manner.
- This methodology refers to passive, non-intrusive OSINT tasks.
- The mentioned tools are just examples, not an exhaustive list.
- The OFM methodology only addresses the Data Collection phase.
- The OFM best fits OSINT investigations related to individuals.
- Any OSINT investigations should be preceded by proper OpSec.
OFM is meant to be followed in a top-down approach, starting with the widest types and methods of searching for data and gradually implementing increasingly specialized tools and techniques. In the end, all the collected data is funneled into the Data Process & Analysis phase.
-
The main goal of this stage is to collect more PII (Personal Identifiable Information, e.g., email addresses and/or usernames) about the target. The discovery of new PII is useful both for recursively searching the web for more data on the target, as well as feeding this PII to specialized OSINT tools during Stages 2-5.
-
This stage may sometimes collect the most amount of data, although this data may be quite scattered and raw in the absence of any kind of automation or filtering algorithm.
-
For each search engine, manual or automated (API-based) advanced search and scrape methods can be applied to filter the results via built-in operators or patterns, and also to organize the data in structured formats e.g., JSON.
-
Furthermore, recursive searching and scraping should be applied for each piece of PII collected during previous searches. This can be done best by using an automated tool.
-
The tools used in this stage are the most well-known search engines, either queried manually or programmatically:
-
Automated OSINT Tool:
-
After the first wave of (more or less) relevant data has been collected and filtered from search engines, the next step is to use specialized OSINT tools on the most relevant bits of data that have been collected during Stage 1 (usernames, email addresses, phone numbers, profile URLs, etc.).
-
These tools are meant as additional filters for the OSINT investigation; however, they can also provide new insights and leads on the target's online presence. Combining these tools with the advanced searches from the previous stage may already build a significant portion of the target's digital footprint.
-
Some of the tools used in this stage are:
-
Username search:
-
Email search:
-
Phone Number search:
-
- The information collected in the previous two steps may point to one or more social media profiles that the target is using. These profiles may include, but not be limited to, well-known social media services such as Facebook, Instagram, TikTok, X, or Reddit, secondary or emerging social networks such as Bluesky or Truth Social, blogs, forums, or chat rooms such as Telegram, Discord, Slack, etc.
- Any of these avenues can lead to discovering more information about the target, either personal (age, birthday, photos, workplace, locations, friends) or ideological such as political, cultural, religious, or sexual preferences, among others. Any such lead can further unravel a suite of pathways to explore, and can also help paint a better picture of the target. This stage is partly manual, however the tools below may provide additional or faster insights.
🍀 NOTE: There are hundreds of social media OSINT (SOCMINT) tools than have been developed over the years. Few of them still work (fully or partially) to this day, however most of them have not been maintained for years mostly because social media platforms have become more restrictive when it comes to their search functionality, API access and privacy measures. Therefore, any attempt to list all of these tools would be futile. Recently, more and more specialized (paid) tools emerged in the OSINT community and, even though some of them may not be affordable for most users, professional OSINT investigators will rely more and more on these solutions.
🍀 NOTE: In the age of information and speed, real OSINT investigators would rather have a handful of (paid) specialized tools to rely on anytime, in combination with other tools and APIs mentioned throughout this methodology, than spend hours or days scouring through GitHub, Reddit or other places in search of a functional tool to do their job. The purpose of the OFM is to provide a pragmatic and useful path for conducting OSINT investigations, not to blindly list every available tool out there.
-
Below you can find some general SOCMINT search tools that are free or partially free, as well as a list of paid tools which is going to be updated periodically.
-
General search tools (Free):
- IntelTechniques Facebook Search
- IntelTechniques Twitter Search
- IntelTechniques Instagram Search
- IntelTechniques LinkedIn Search
- IntelTechniques Communities (Reddit, TikTok, etc.)
- Bellingcat Facebook Tools
- Bellingcat Twitter Tools
- Bellingcat Instagram Tools
- Bellingcat LinkedIn Tools
- Bellingcat Discord Tools
- Bellingcat Telegram Tools
- Bellingcat Reddit Tools
- Bellingcat TikTok Tools
- Bellingcat VKontakte Tools
- Bellingcat YouTube Tools
- Bellingcat Other Networks
-
Specialized SOCMINT tools (Paid):
-
-
Websites and APIs providing information and search capabilities on data breaches and pastes can sometimes prove to be extremely rewarding, especially if the previous steps have not provided a great deal of data about the target. Finding breaches that the target's username or email address has been a part of can provide crucial clues on some of the platforms where the target has (or at least had) accounts or profiles. Furthermore, this type of search can easily be automated via Python scripts and libraries, at very low API costs. Of course, this can again lead to manual research once one or more pieces of data have been found.
-
Typical tools in this step are:
-
Finally, in some cases there may be a need to touch the dark web, especially if the target potentially uses this environment for unethical or illegal activities. Most of the time, tapping into the rabbit holes of the dark web is unnecessary since 99% of the data resides on the clear web. This type of research is mostly manual, it's done through the Tor network and can expose the investigator to various risks if proper security measures are not implemented.
-
Most common Dark Web OSINT tools include:
- The OFM may get updated over time due to a rapidly-changing online landscape and the emergence of more sophisticated tools.
- Tools, websites, or services that are not actively maintained (2yrs+) will be gradually removed, and new ones will be added.
- Version v1.1.0 added browser bookmarks containing all the tools organized by stages, as well as a few additional OSINT tools - see the bookmarks folder.
- Version v1.1.1 added a report template file containing a sample page of an OFM-based report generated during OSINT investigations - see the template folder.
- In the context of this methodology, OSINT refers to passive, non-intrusive open-source intelligence.
- Tool mentions are not endorsements. I am in no way affiliated with any of these tools or services.
- Not every tool mentioned here has been tested by the author of OFM. Do your own due diligence!
- Keep in mind that any illegal or unethical use of this information is solely your responsibility.
-
Email Address:
Please direct your inquiries to sintr.0@pm.me. -
Important Guidelines:
- Use a professional email or a ProtonMail address.
- Keep your message concise and written in English.
-
Security Notice:
Emails with links or attachments will be ignored for security reasons.