Table of Contents
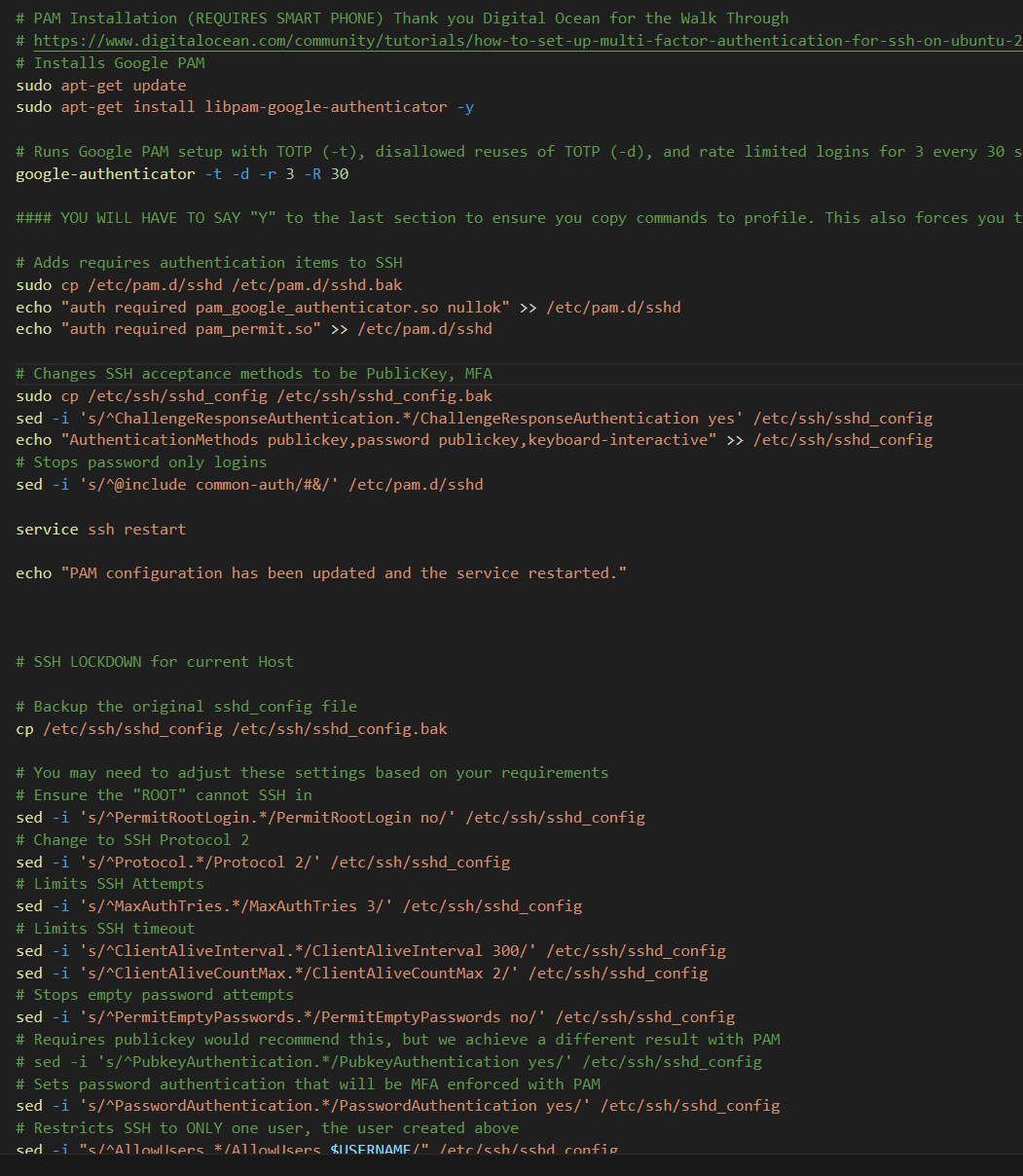
As I have build, rebuilt, and expanded my homelab, I always wanted a better way to monitor SSH traffic and restrict it. So I built these bastion host SSH script. You have 3 different scripts, the first will create a new user of your choice on your bastion host, install Google PAM for MFA, and then lockdown SSH to that user. The second script is the SSH lockdown for the remote host. The last one will be added to the ~/.bashrc at the end to restrict the terminal access
- Bash
Download the git project.
This is an example of how to list things you need to use the software and how to install them.
- bash
git clone https://github.com/m1cypher/bastion_host.git
- Modify permissions for the scripts
chmod +x new_user.sh
chmod +x ssh_lockdown_remote.shUse this space to show useful examples of how a project can be used. Additional screenshots, code examples and demos work well in this space. You may also link to more resources.
For more examples, please refer to the Documentation
- Add Auditing
- Export of Auditing Logs
- Bruteforce auto ban (DenyHost or Fail2Ban)
- PortKnocking Option
See the open issues for a full list of proposed features (and known issues).
Contributions are what make the open source community such an amazing place to learn, inspire, and create. Any contributions you make are greatly appreciated.
If you have a suggestion that would make this better, please fork the repo and create a pull request. You can also simply open an issue with the tag "enhancement". Don't forget to give the project a star! Thanks again!
- Fork the Project
- Create your Feature Branch (
git checkout -b feature/AmazingFeature) - Commit your Changes (
git commit -m 'Add some AmazingFeature') - Push to the Branch (
git push origin feature/AmazingFeature) - Open a Pull Request
Distributed under the MIT License. See LICENSE.txt for more information.
Your Name - @mimircyber - info@mimircyber.com
Project Link: https://github.com/m1cypher/bastion_host