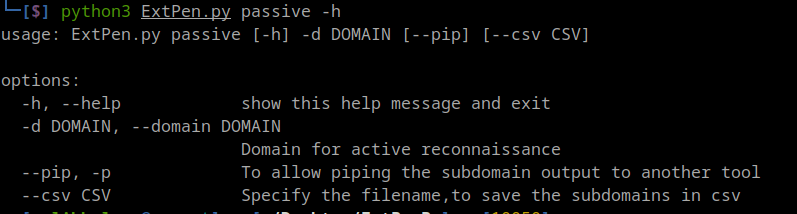
- Passive:
- Collecting Subdomains (without brute forcing)
- Whois database check
- Zone Transfer
- DNS records check
- Reverse DNS Lookup
- IP addresses range
- Regex to Google Dork
- Active:
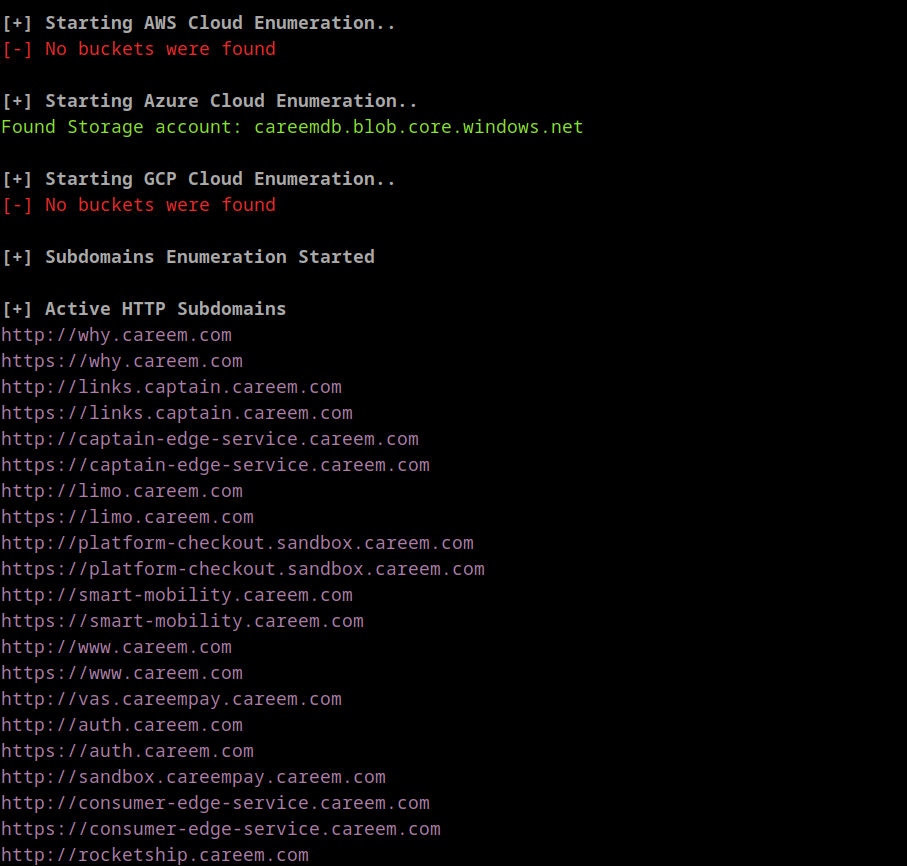
- Cloud storage enumeration
- Identifying known paths (.git, .htaccess, etc)
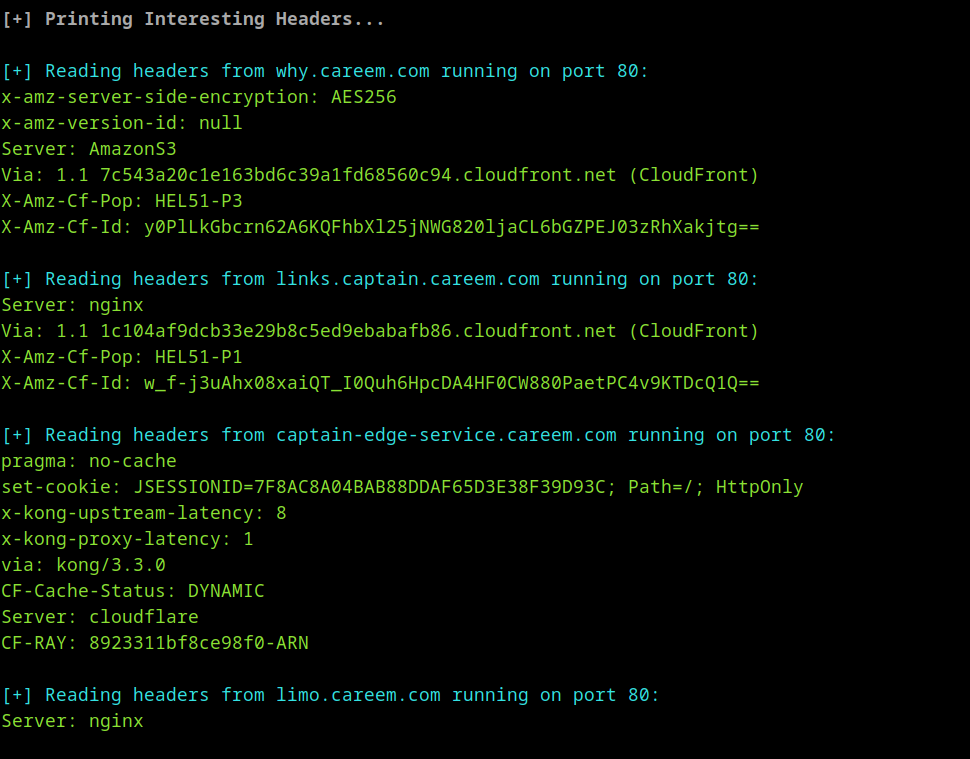
- Intersting Headers
- Taking screenshots of validated subdomains
- All the passive stuff
- Validating hosts running HTTP[S]
- Gathering included paths (without bruteforcing)
- Collecting subdomains (with brute forcing)
- APK:
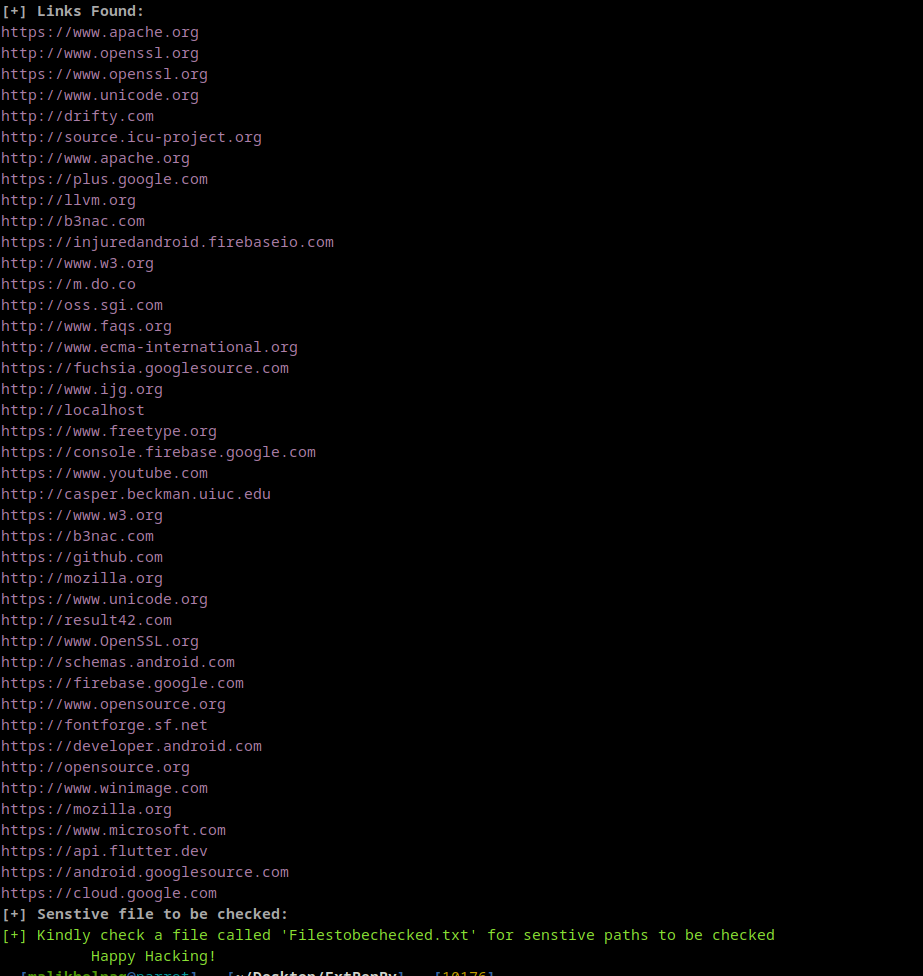
- Collecting URL"s
- Root Detection Check
- SDK Version Check
- Decompiling APK to smali and java
- Extracting Sensitive information like API keys, passwords, etc..
- Debuggable mode Check
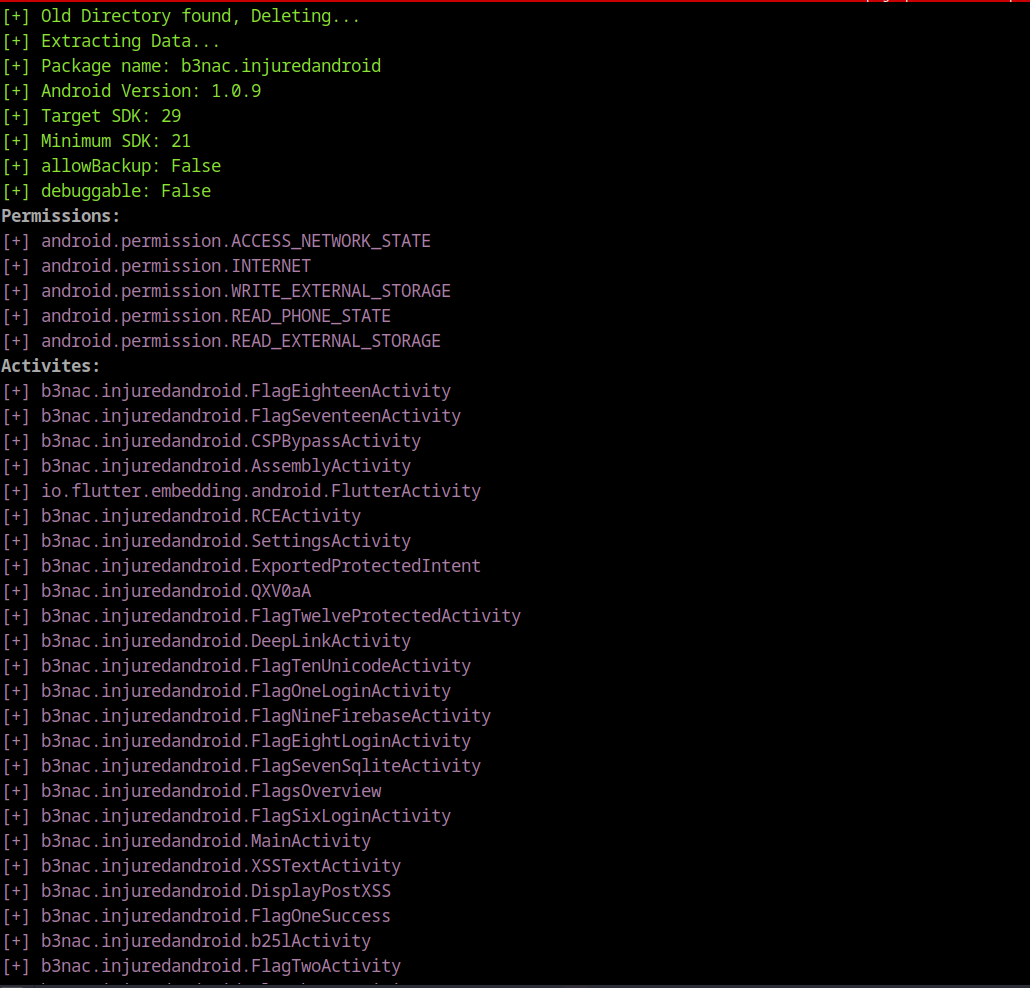
- Checking permissions
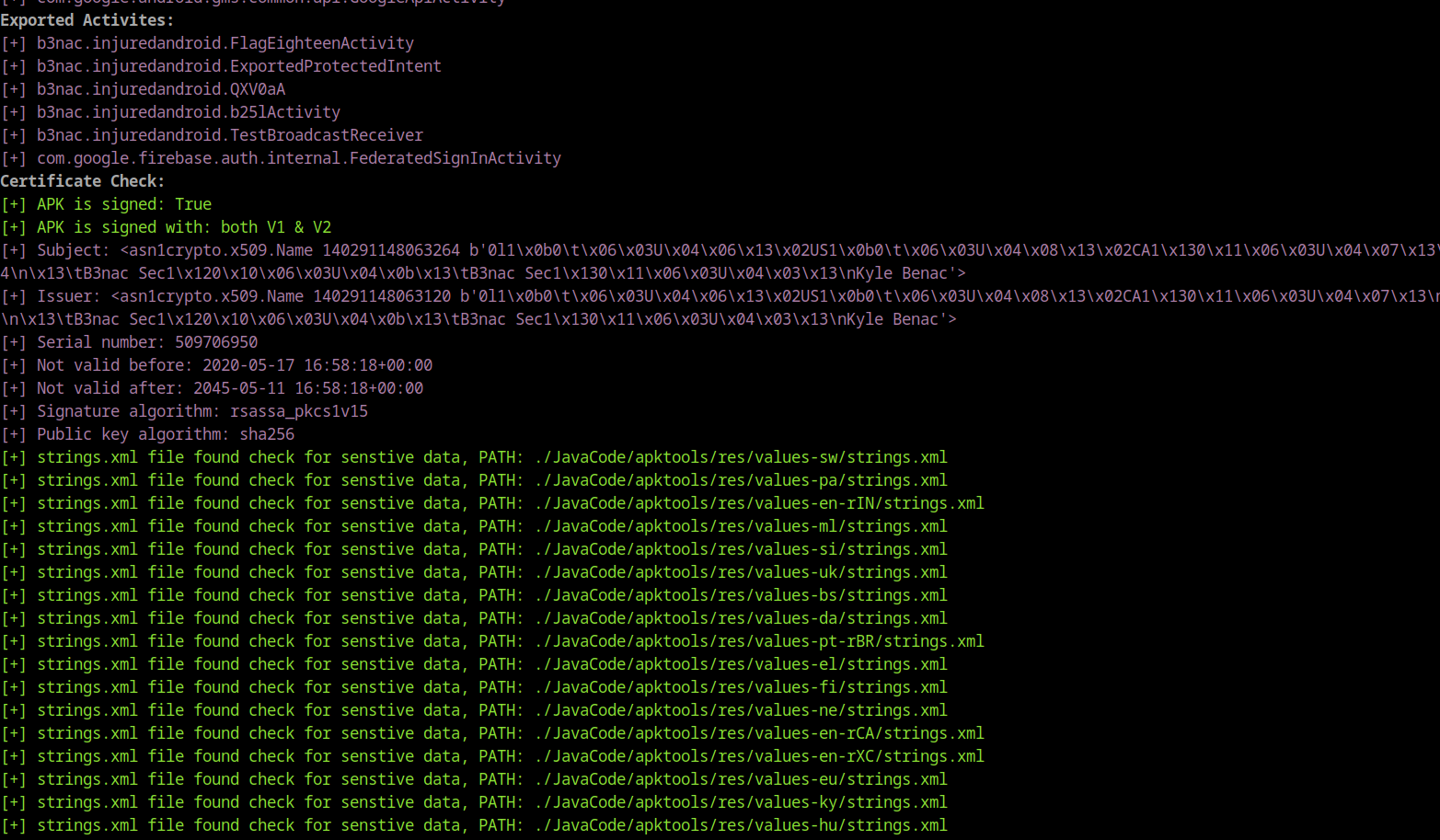
- Checking activities and (Exported Activities)
- Check if backup is allowed
- collecting strings.xml files
Sample_run.mp4
wget https://dl.google.com/linux/direct/google-chrome-stable_current_amd64.deb
sudo dpkg -i ./google-chrome-stable_current_amd64.debpip3 install pipx
pipx install extpenpy==1.3git clone https://github.com/maliktawfiq/ExtPenPy.git
cd ExtPenPy
pip install -r requierments.txt
sudo apt install apktool
python3 ExtPen.py -hgit clone https://github.com/maliktawfiq/ExtPenPy.git
cd ExtPenPy
docker build -t extpenpy .
#linux
docker run -it -v $PWD:/app extpenpy -h
#windows
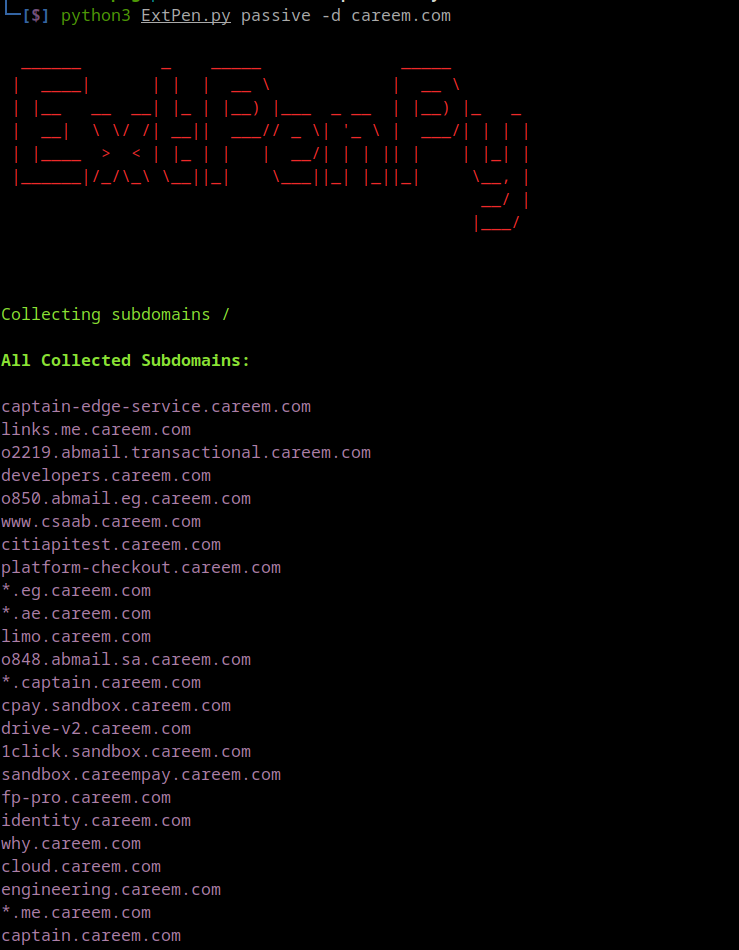
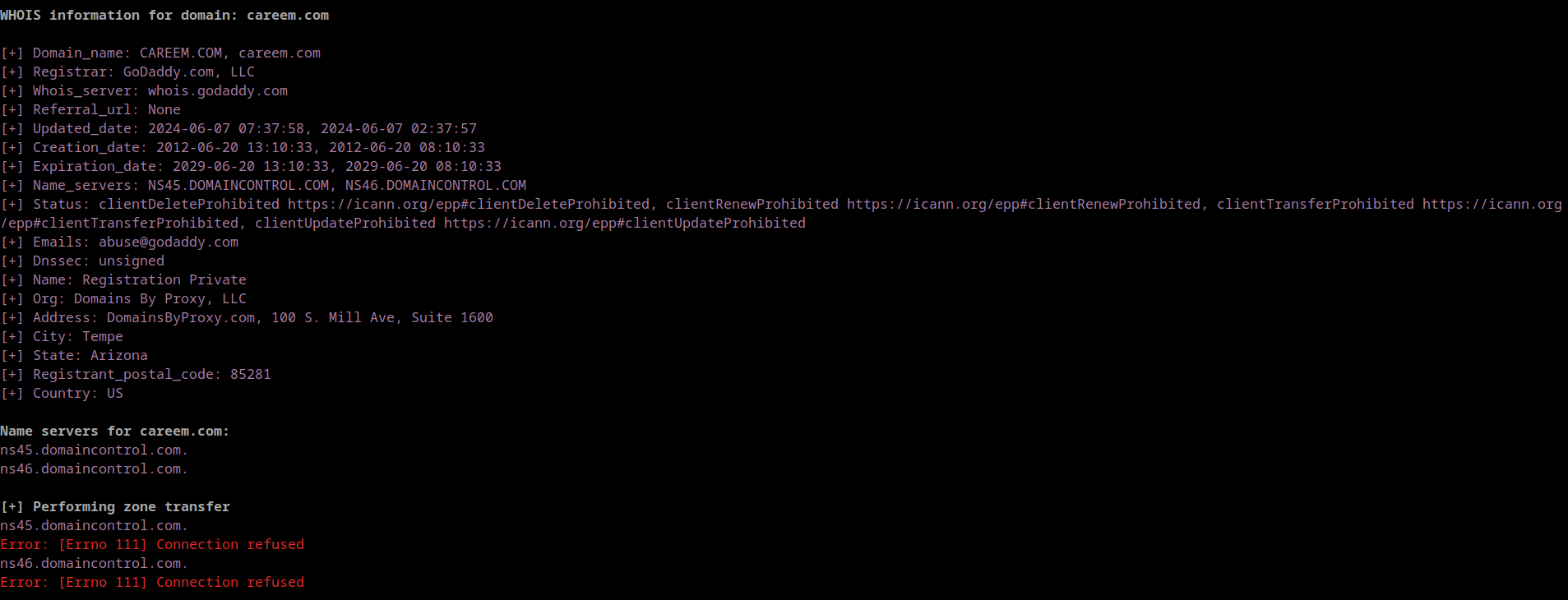
docker run -it -v "%cd%":/app extpenpy -hpython3 ExtPenPy -hpython3 ExtPenPy passive -d careem.com- Whois databse and zone trasfer attempt
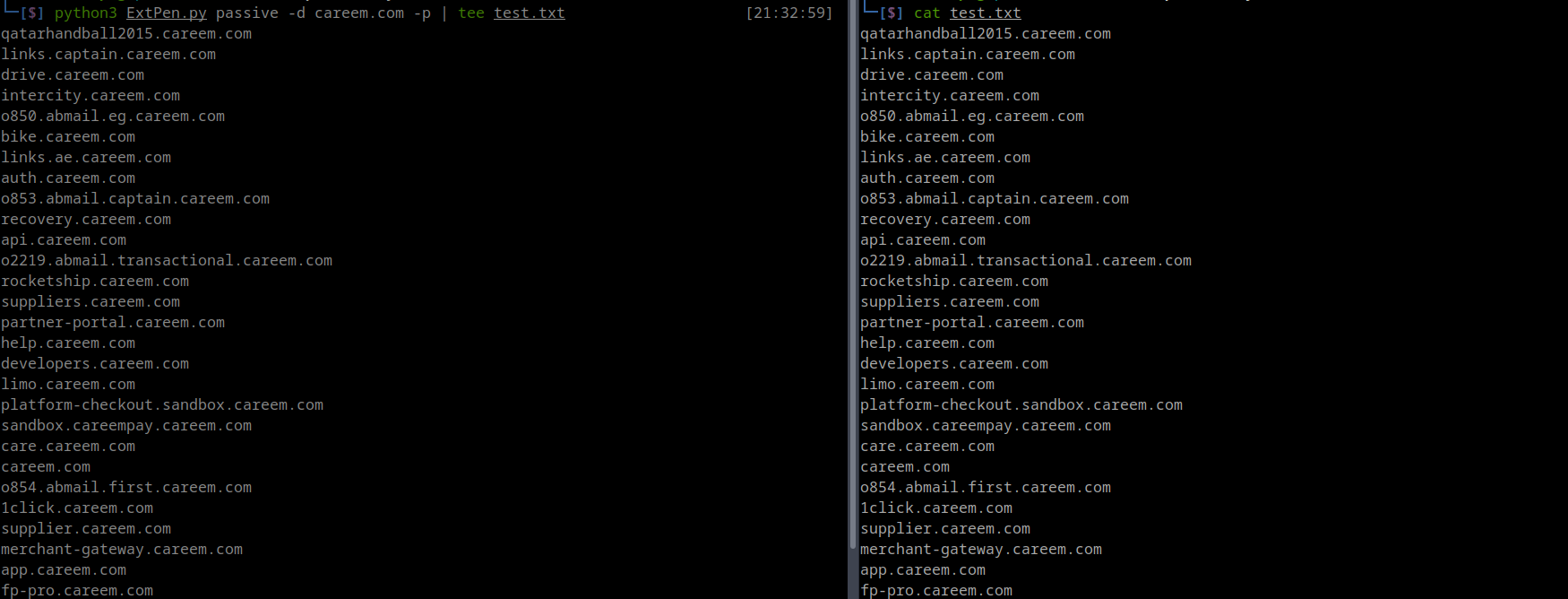
- -p or —pip allows piping the subdomain output to a file, tool..etc as shown below
python3 ExtPen.py passive -d $Domain -p | tee test.txt- you can add —csv to save the subdomains in csv file.
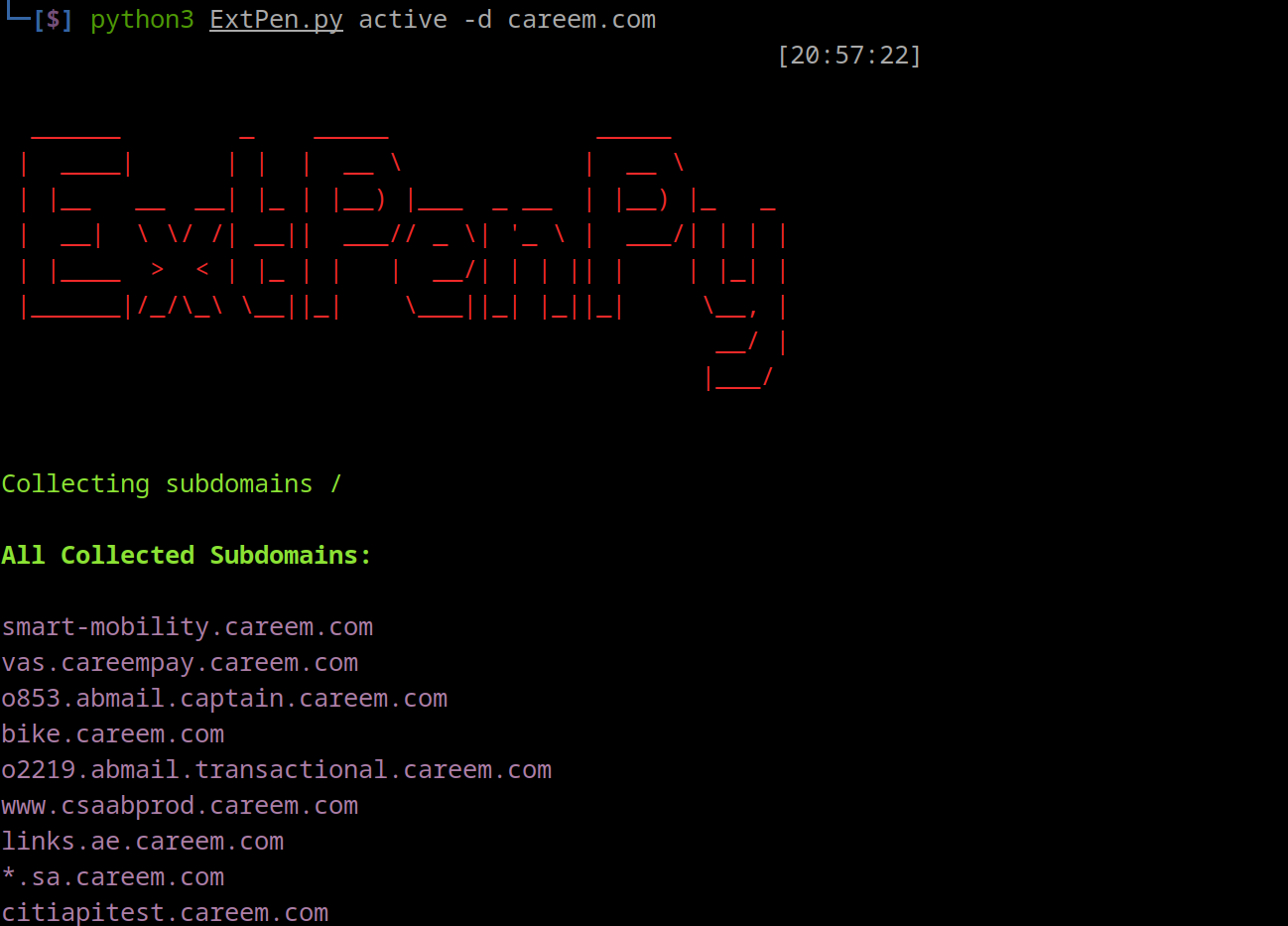
python3 passive -d $domain --csv ./subdomainspython3 ExtPen.py active --helppython3 ExtPen.py active -d $domain- Example of cloud storage enumeration
- Example of web enumeration
After running the APK analysis two directories will be created.
- Javacode: which will contain the decompiled code
- apk_decomiled: which holds the data before decompiling
python3 ExtPen.py apk -h- The activities and the permissions the applications uses
- Certificate check and identifying sensitive strings found
- Exporting links found in the APK
ExtPenPy was made to help security researchers speed up the reconnaissance phase, it is intended for legal and ethical penetration testing only. Unauthorized use is prohibited and may be illegal. Users must ensure compliance with all relevant laws and regulations. The developers are not liable for any misuse or damages.