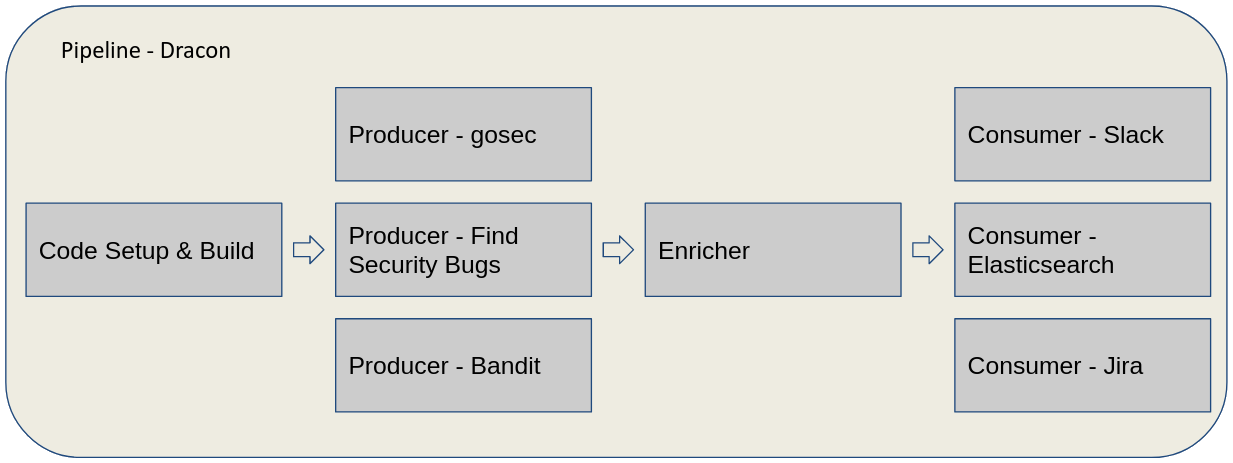
Security pipelines on Kubernetes. The purpose of this project is to provide a scalable and flexible tool to execute arbitrary tools on arbitrary code while processing the results in a flexible way.
The Getting started in Minikube tutorial explains how to install, configure, and run Dracon.
Other tutorials are also available:
| Name | Description |
|---|---|
| Getting started in Minikube | Beginner guide on how to get started with Dracon |
| Running our demo pipeline | End to end demo of running an example pipeline |
| Example of using a public git repo | Example of running Dracon against a public git repository |
| Example of using a private git repo | Example of running Dracon against a private git repository |
| Creating your own pipeline | WIP: How to create your own custom dracon pipeline |
| Creating your own producer | WIP: Extending Dracon by creating your own custom producer |
| Creating your own consumer | WIP: Extending Dracon by creating your own custom consumer |
We have compiled binaries for dracon in under GitHub releases. dracon can quickly be installed into your home directory by executing:
bash <(curl -s https://raw.githubusercontent.com/thought-machine/dracon/master/scripts/install.sh)Dracon was announced at OWASP Appsec Amsterdam in 2019. Check out the slides from the presentation.
If you have questions, reach out to us by opening a new issue on Github.
Contributions are welcome, see the developing and releasing guides on how to get started.
Dracon is under the Apache 2.0 license. See the LICENSE file for details.