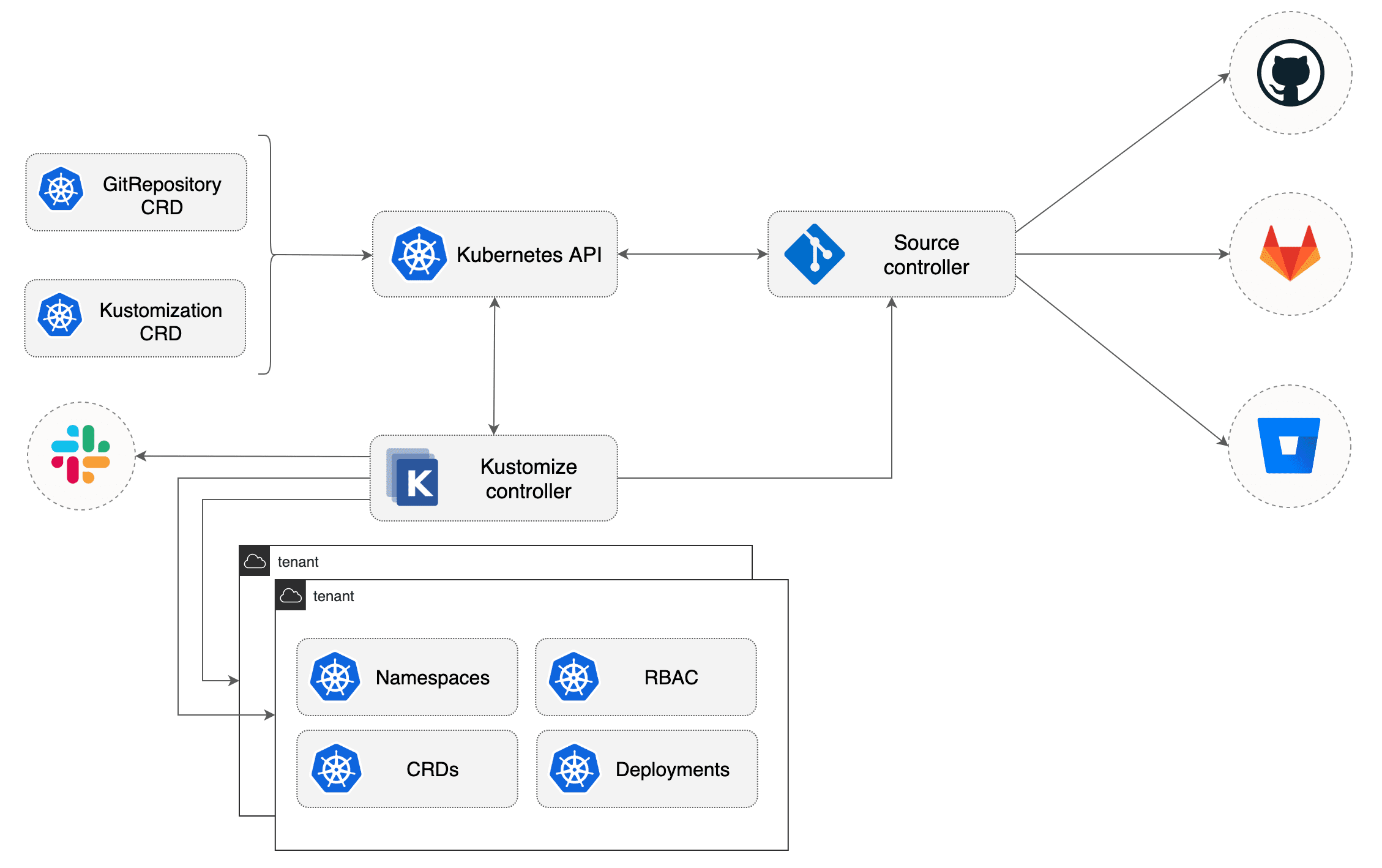
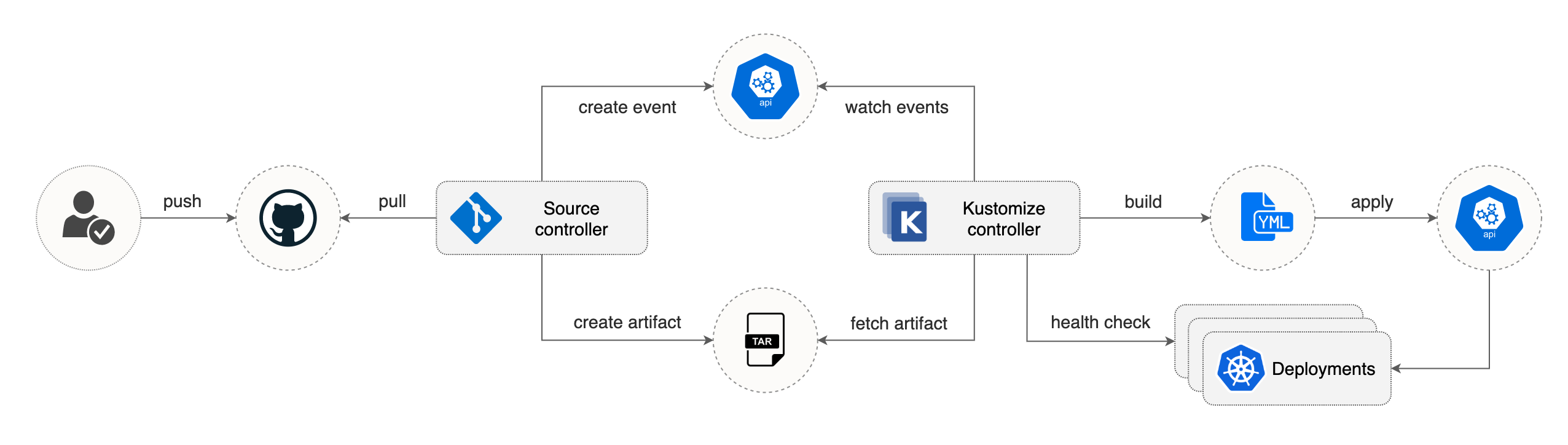
The kustomize-controller is a Kubernetes operator, specialized in running continuous delivery pipelines for infrastructure and workloads defined with Kubernetes manifests and assembled with Kustomize.
Features:
- watches for
Kustomizationobjects - fetches artifacts produced by source-controller from
Sourceobjects - watches
Sourceobjects for revision changes - generates the
kustomization.yamlfile if needed - generates Kubernetes manifests with kustomize build
- validates the build output with client-side or APIServer dry-run
- applies the generated manifests on the cluster
- prunes the Kubernetes objects removed from source
- checks the health of the deployed workloads
- runs
Kustomizationsin a specific order, taking into account the depends-on relationship - notifies whenever a
Kustomizationstatus changes
Specifications:
The kustomize-controller is part of a composable GitOps toolkit and depends on source-controller to acquire the Kubernetes manifests from Git repositories.
Download the toolkit CLI:
curl -s https://toolkit.fluxcd.io/install.sh | sudo bashInstall the toolkit controllers in the gitops-system namespace:
tk installCreate a source object that points to a Git repository containing Kubernetes and Kustomize manifests:
apiVersion: source.fluxcd.io/v1alpha1
kind: GitRepository
metadata:
name: podinfo
namespace: gitops-system
spec:
interval: 1m
url: https://github.com/stefanprodan/podinfo
ref:
branch: masterFor private repositories, SSH or token based authentication can be configured with Kubernetes secrets.
Save the above file and apply it on the cluster. You can wait for the source controller to assemble an artifact from the head of the repo master branch with:
kubectl -n gitops-system wait gitrepository/podinfo --for=condition=readyThe source controller will check for new commits in the master branch every minute. You can force a git sync with:
kubectl -n gitops-system nnotate --overwrite gitrepository/podinfo fluxcd.io/reconcileAt="$(date +%s)"Create a kustomization object that uses the git repository defined above:
apiVersion: kustomize.fluxcd.io/v1alpha1
kind: Kustomization
metadata:
name: podinfo-dev
namespace: gitops-system
spec:
interval: 5m
path: "./deploy/overlays/dev/"
prune: true
sourceRef:
kind: GitRepository
name: podinfo
validation: client
healthChecks:
- kind: Deployment
name: frontend
namespace: dev
- kind: Deployment
name: backend
namespace: dev
timeout: 80sNote that if your repository contains only plain Kubernetes manifests, the controller will automatically generate a kustomization.yaml file inside the specified path.
A detailed explanation of the Kustomization object and its fields can be found in the specification doc.
Based on the above definition, the kustomize-controller fetches the Git repository content from source-controller,
generates Kubernetes manifests by running kustomize build inside ./deploy/overlays/dev/,
and validates them with a dry-run apply. If the manifests pass validation, the controller will apply them
on the cluster and starts the health assessment of the deployed workload. If the health checks are passing, the
Kustomization object status transitions to a ready state.
You can wait for the kustomize controller to complete the deployment with:
kubectl -n gitops-system wait kustomization/podinfo-dev --for=condition=readyWhen the controller finishes the reconciliation, it will log the applied objects:
kubectl -n gitops-system logs deploy/kustomize-controller | jq .{
"level": "info",
"ts": 1587195448.071468,
"logger": "controllers.Kustomization",
"msg": "Kustomization applied in 1.436096591s",
"kustomization": "gitops-system/podinfo-dev",
"output": {
"namespace/dev": "created",
"service/frontend": "created",
"deployment.apps/frontend": "created",
"horizontalpodautoscaler.autoscaling/frontend": "created",
"service/backend": "created",
"deployment.apps/backend": "created",
"horizontalpodautoscaler.autoscaling/backend": "created"
}
}You can trigger a kustomization reconciliation any time with:
kubectl -n gitops-system annotate --overwrite kustomization/podinfo-dev \
fluxcd.io/reconcileAt="$(date +%s)"When the source controller pulls a new Git revision, the kustomize controller will detect that the source revision changed, and will reconcile those changes right away.
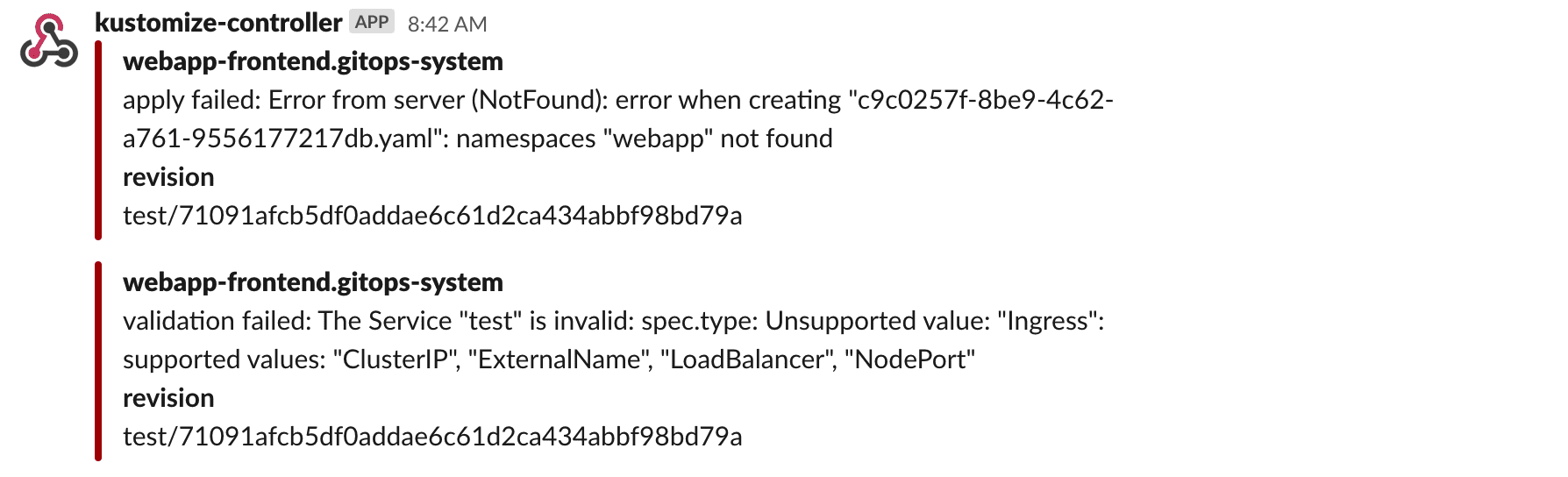
If the kustomization reconciliation fails, the controller sets the ready condition to false and logs the error:
status:
conditions:
- lastTransitionTime: "2020-04-16T07:27:58Z"
message: 'apply failed'
reason: ApplyFailed
status: "False"
type: Ready{
"kustomization": "gitops-system/podinfo-dev",
"error": "Error from server (NotFound): error when creating podinfo-dev.yaml: namespaces dev not found"
}When running a kustomization, you may need to make sure other kustomizations have been
successfully applied beforehand. A kustomization can specify a list of dependencies with spec.dependsOn.
When combined with health assessment, a kustomization will run after all its dependencies health checks are passing.
For example, a service mesh proxy injector should be running before deploying applications inside the mesh:
apiVersion: kustomize.fluxcd.io/v1alpha1
kind: Kustomization
metadata:
name: istio
namespace: gitops-system
spec:
interval: 10m
path: "./istio/system/"
sourceRef:
kind: GitRepository
name: istio
healthChecks:
- kind: Deployment
name: istiod
namespace: istio-system
timeout: 2m
---
apiVersion: kustomize.fluxcd.io/v1alpha1
kind: Kustomization
metadata:
name: podinfo-dev
namespace: gitops-system
spec:
dependsOn:
- istio
interval: 5m
path: "./deploy/overlays/dev/"
prune: true
sourceRef:
kind: GitRepository
name: podinfoFor production deployments, instead of synchronizing with a branch you can use a semver range to target stable releases:
apiVersion: source.fluxcd.io/v1alpha1
kind: GitRepository
metadata:
name: podinfo-releases
namespace: gitops-system
spec:
interval: 5m
url: https://github.com/stefanprodan/podinfo
ref:
semver: ">=4.0.0 <5.0.0"With ref.semver we configure source controller to pull the Git tags and create an artifact from the most recent tag
that matches the semver range.
Create a production kustomization and reference the git source that follows the latest semver release:
apiVersion: kustomize.fluxcd.io/v1alpha1
kind: Kustomization
metadata:
name: podinfo-production
namespace: gitops-system
spec:
interval: 10m
path: "./deploy/overlays/production/"
sourceRef:
kind: GitRepository
name: podinfo-releasesBased on the above definition, the kustomize controller will apply the kustomization that matches the semver range set in the Git repository.
The kustomize controller emits Kubernetes events whenever a kustomization status changes.
You can use the notification-controller to forward these events to Slack, Microsoft Teams, Discord or Rocket chart.
Create a notification provider for Slack:
apiVersion: notification.fluxcd.io/v1alpha1
kind: Provider
metadata:
name: slack
namespace: gitops-system
spec:
type: slack
channel: alerts
secretRef:
name: slack-url
---
apiVersion: v1
kind: Secret
metadata:
name: slack-url
namespace: gitops-system
data:
address: <encoded-url>Create an alert for a list of GitRepositories and Kustomizations:
apiVersion: notification.fluxcd.io/v1alpha1
kind: Alert
metadata:
name: on-call
namespace: gitops-system
spec:
providerRef:
name: slack
eventSeverity: info
eventSources:
- kind: GitRepository
name: podinfo-releases
- kind: Kustomization
name: podinfo-productionMultiple alerts can be used to send notifications to different channels or Slack organizations.
The event severity can be set to info or error.
When the severity is set to error, the controller will alert on any error encountered during the
reconciliation process. This includes kustomize build and validation errors, apply errors and
health check failures.
When the verbosity is set to info, the controller will alert if:
- a Kubernetes object was created, updated or deleted
- heath checks are passing
- a dependency is delaying the execution
- an error occurs